Cyber Weapons on Darknet Marketplaces and Forums
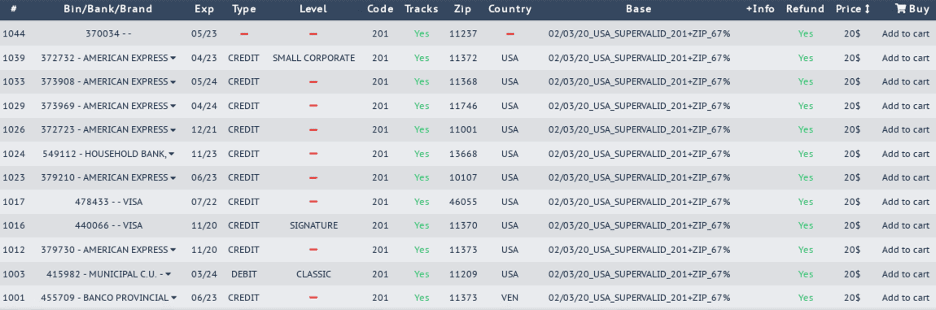
Underground markets of the darknet provide an extensive inventory of illegal goods for sale, including and certainly not limited to drugs, weapons, hackers and assassins for hire. In the “Digital Goods” section of most marketplaces, one will find an array of malware, bots, and services for conducting offensive information operations against a victim network or targeted information system.
While many of these are tools are considered ‘commercially’ available products and services for any interested anonymous darknet buyer with the cryptocurrency to purchase in hand, nation state-level cyber threat actors are certainly one potential consumer for any of these products with the intent to add these digital weapons to their repository of cyber tools.
[Quick Read: Darknet posts show SolarWinds has been a target, and has open servers that trace back to Russia]
As we’ve recently reported in our findings regarding the SolarWinds hack, monitoring the darknet for these types of tools and malicious discussions enables organizations to understand when and if they’re a target, and prepare accordingly.
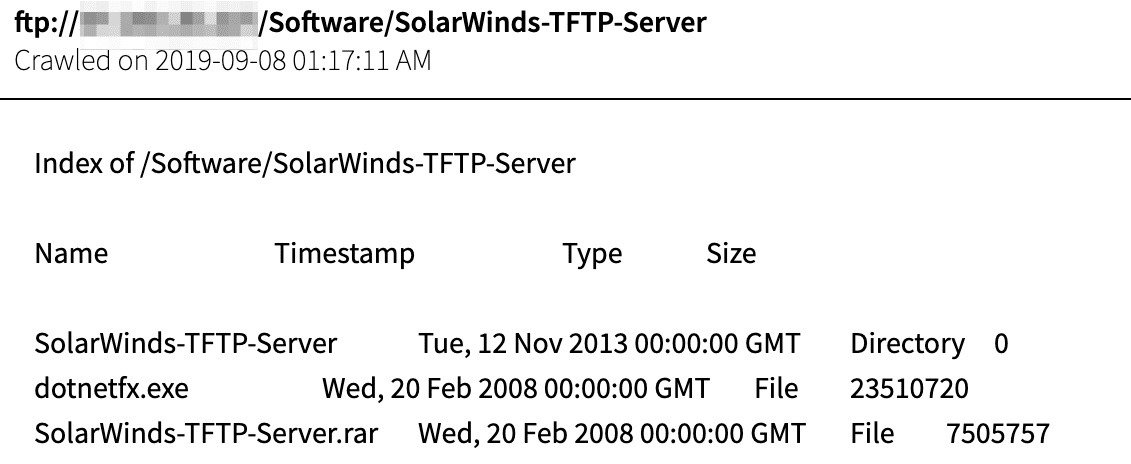
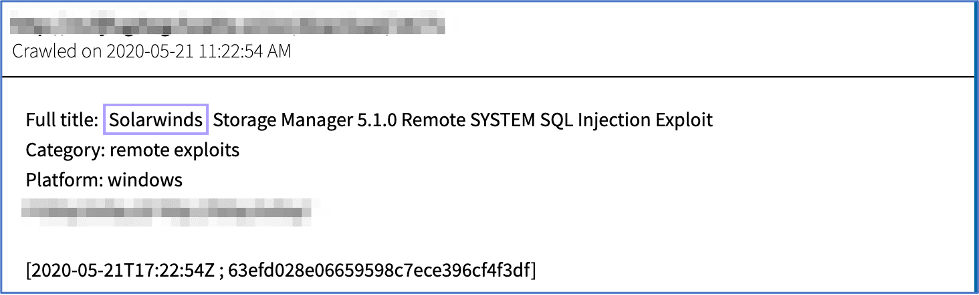
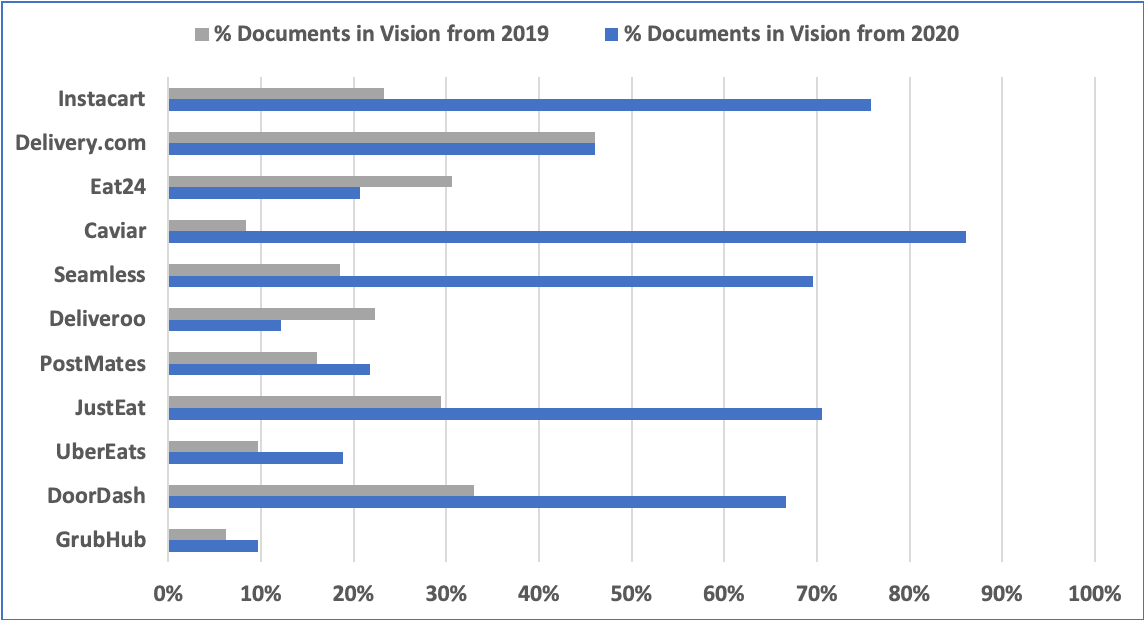
For example, in the case of SolarWinds, we have evidence that they have been a target by hackers for a number of years. A few searches in DarkOwl Vision’s database of darknet content reveal glaring potential indicators of compromise that, when taken seriously, could have been leveraged by their customers as a cue to safeguard themselves against what ultimately resulted in the devastating hack that transpired this year.
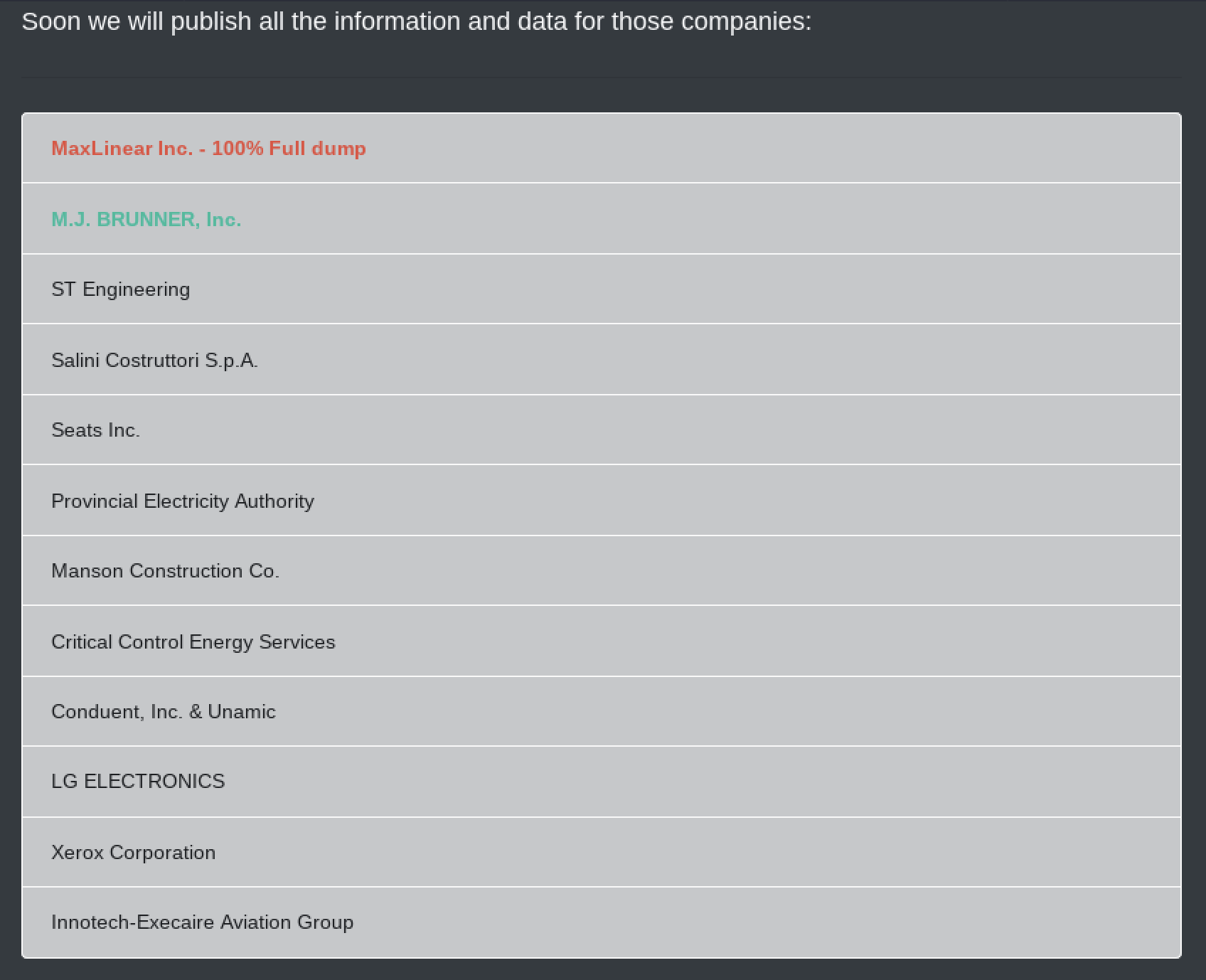
There are many more cyber weapons at Nation-State threat actors’ disposal on the darknet
The digital goods section of most darknet marketplaces are broad in their offerings, suggesting that a ‘digital good’ consists of any product or service delivered virtually, unlike the purchase of an illegal weapon or illicit drugs that are delivered to a physical address. As such, the digital goods section of many marketplaces includes Adobe PDF files guides, lifetime website memberships and subscriptions, and digitized programming books with little to no value to a sophisticated nation state cyber actor. Most of these are innocuous instructions for the most novice to the underground criminal operations, such as carding, identity fraud, basic social engineering, and technical ‘hacking’ manuals covering basic network penetration.
Basic Network Exploitation Tools
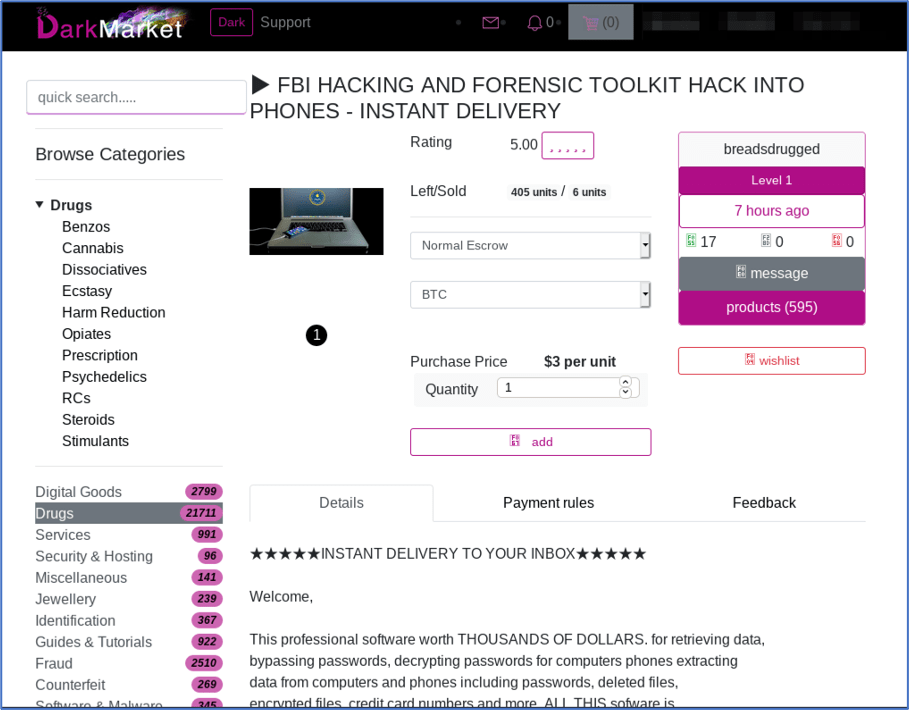
A darknet marketplace consumer can also purchase any number of basic network protocols and tools for maintaining anonymity such as anonymous servers, VPNs and bulk proxies. It is unlikely a foreign nation will need such simplified tools; however, there are also vendors selling more advanced versions of the same type of tools, in packages such as KeyLogger Script Collections and CIA forensics expert tool – Magnet IEF on White House Market, or the FBI Hacking and Forensic Toolkit for exploiting mobile phones for sale by the vendor breadsdrugged on DarkMarket. This package is advertised to include KONBOOT authentication bypass, Oxygen Forensics which retrieves deleted texts and extracts data from all the popular mobile-phone cloud providers.
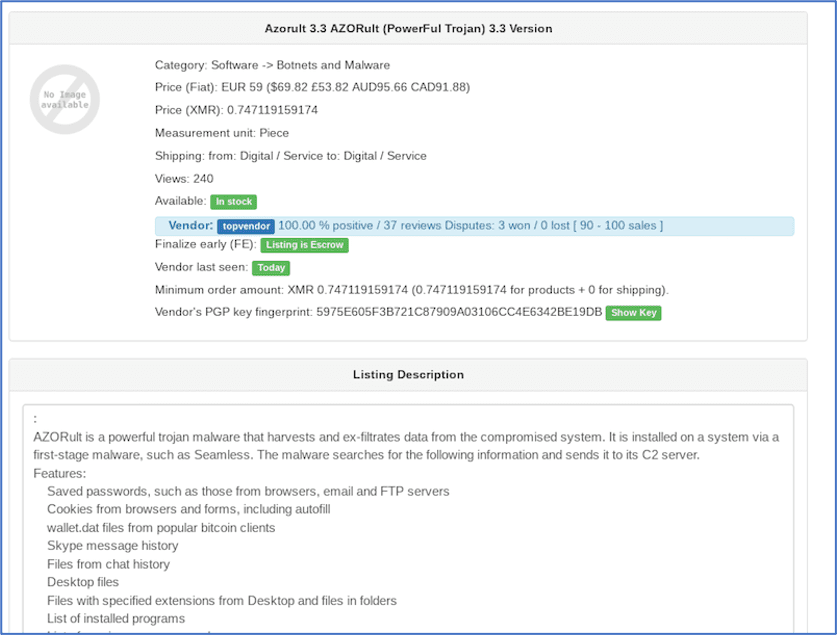
Then, there are also commercially available remote access trojans and bots that nation states could leverage for more sophisticated attacks and espionage. The Anubis Bot, Azorult 3.3 AZORult Trojan (Version 3.3), and Spy MAX v1.0 – Android RAT are all currently available for sale across many darknet marketplaces and accessible via instant download link delivered upon purchase.
Historically, nation states readily target mobile phones for espionage and intelligence collection. This was publicly revealed when the Kingdom of Saudi Arabia’s (KSA) intelligence and government officials were caught using the Pegasus malware against WhatsApp and iPhone messaging platforms, developed by an Israeli security firm, to target dissident journalists. Recent reporting from Toronto’s Citizen’s Lab details how the Saudi government targeted 36 journalists from Al Jazeera earlier this year.
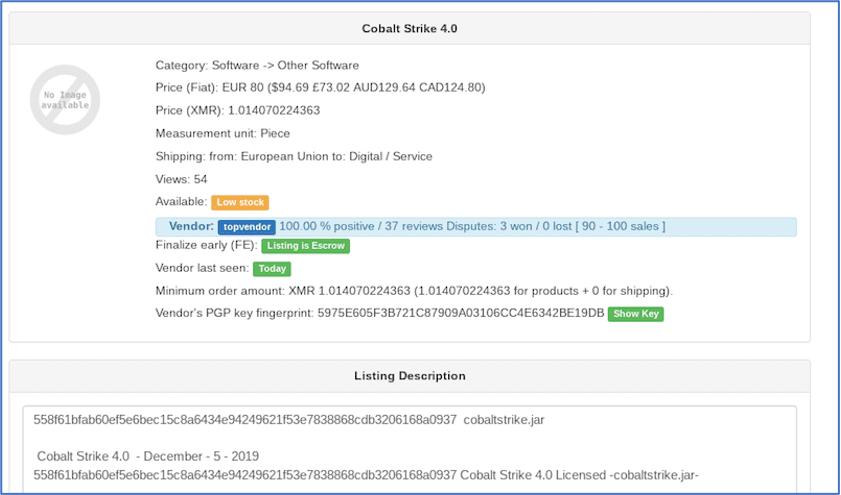
Cobalt Strike is a popular software emulation environment designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors and readily for sale on the darknet. Recent open source reporting suggests Chinese hackers sponsored by the Chinese government have been actively using Cobalt Strike to enable backdoor access to a number of compromised networks and information systems for the deployment of additional tools on the network in the future.
Banking Malware for Large Scale Financial Industry Attacks
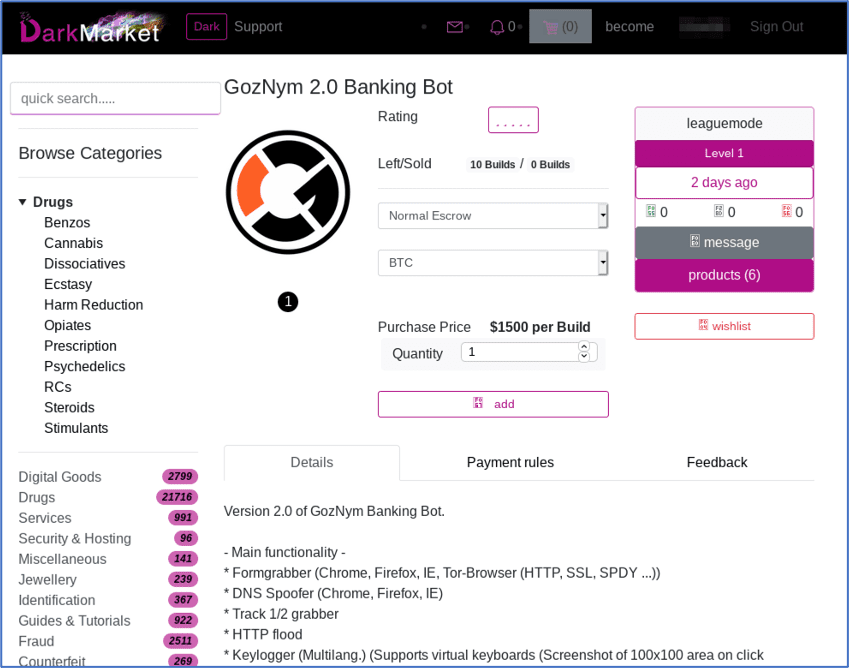
Some nation states, such as North Korea have been known to leverage banking malware for cyber-operations to recoup financial gain from the economic impact of international sanctions. Vendor leaguemode on DarkMarket offers the GozNym 2.0 banking bot for purchase for $1500 USD per build. The same vendor also sells ATM malware that is deployed via EMV (Europay, Mastercard, and Visa, i.e. “chipped”) debit cards on the same market for $1,000 USD per card.
Tools to support the targeted phishing of international banks based in North America, such as CHASE and CIBC of Canada is also currently available for sale on darknet markets. The digital good includes the HTML and CSS for scam websites for a number of prominent banks, including detailed administrator panels. These websites could be used by nation states to conduct targeted attacks against financial institutions.
Ransomware for Offensive Cyber Operations
One information operations technique nation states could employ is simply shutting down critical operations of a competitor country’s critical corporations and industries. WannaCry (aka GonnaCry) ransomware successfully crippled the UK’s National Health System and is currently for sale on White House Market for $150 USD.
The source code for another effective ransomware, known as KingLocker, is also available for purchase and could be customized by a nation state to conduct a large scale campaign against a target industry or country.
The ransomware could be coupled with country-specific business directories, also for sale on darknet marketplaces for targeted in-country deployment. Multiple vendors on White House Market sale leaked databases, such as Dubai’s enterprises and UAE business directory costs as little as $129 USD. Meanwhile, Russia’s industry data with business names, domains, and contact information is only slightly more at $160 USD.
Targeted Phishing and Disinformation Campaigns – Credentials and PII
In the same way leaked organizational information for sale on the darknet could be instrumental for launching ransomware attacks, other critical country-specific information could be leveraged for targeted phishing and disinformation campaigns.
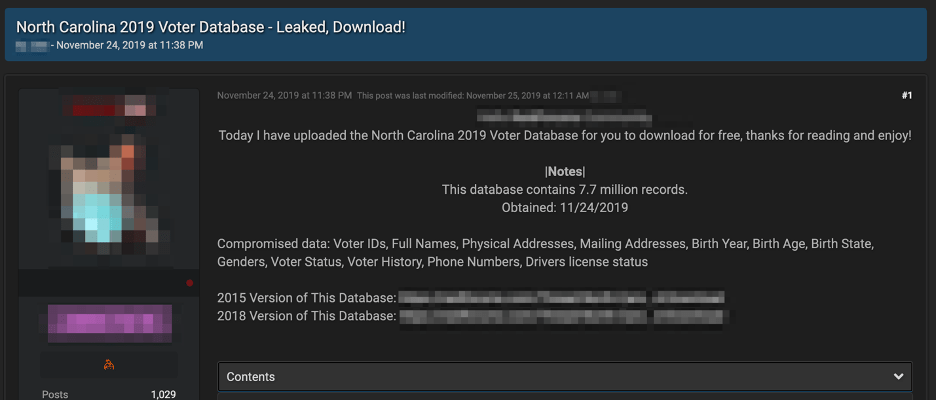
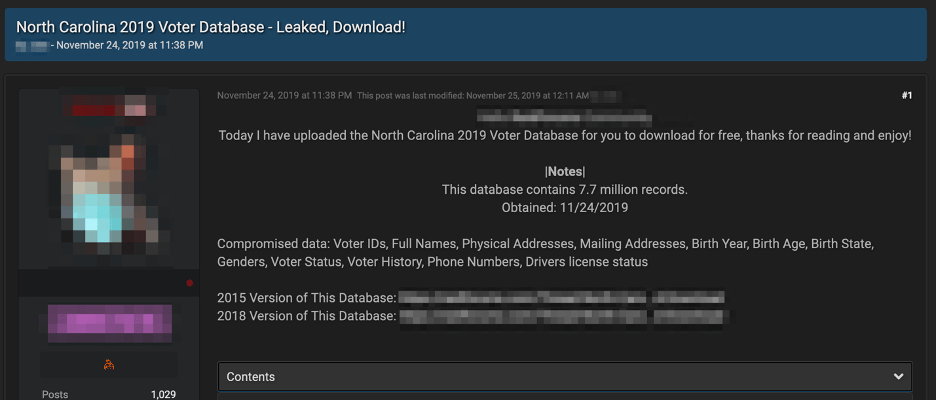
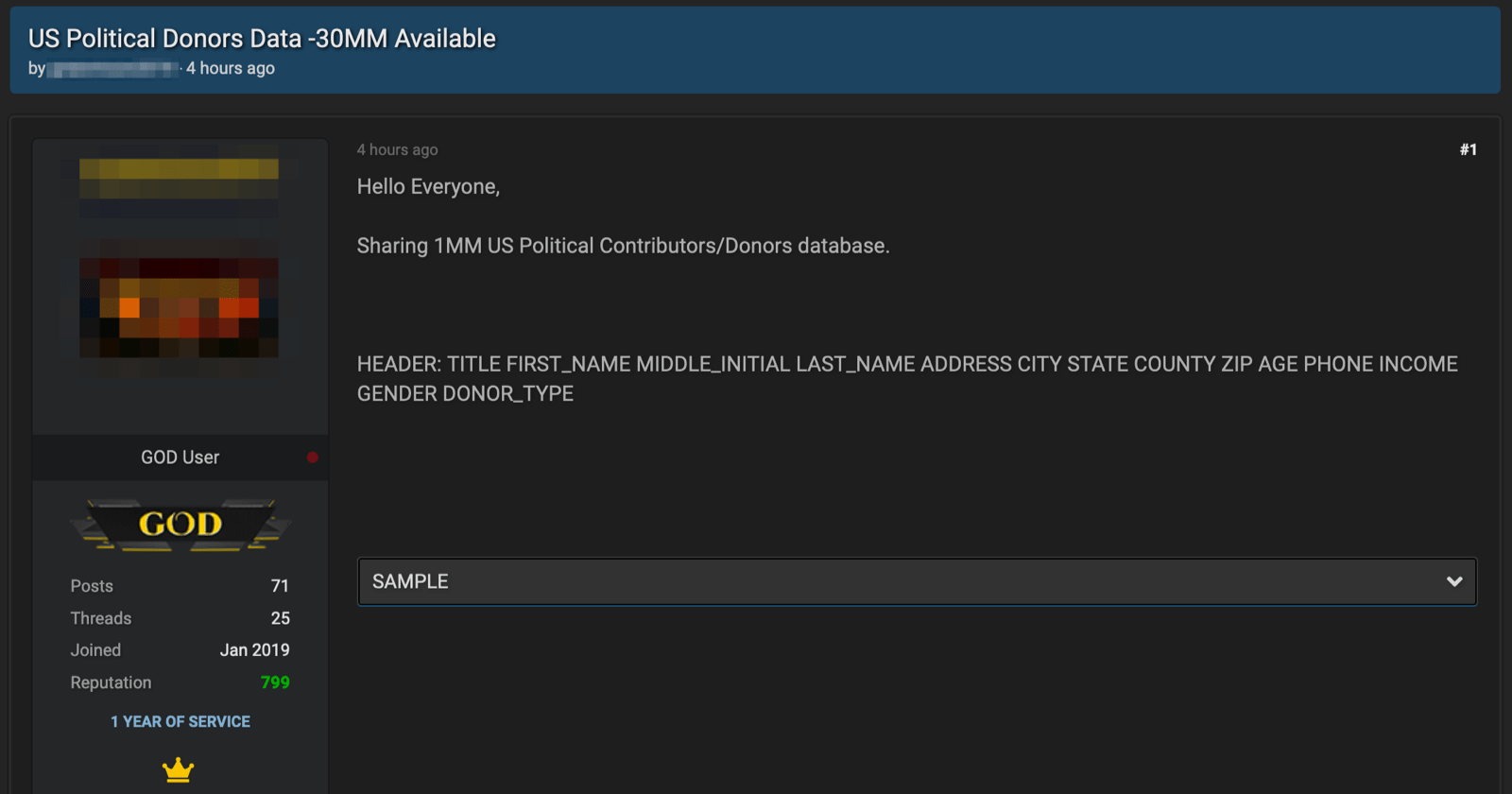
On DarkFox, the vendor GoldApple on DarkFox sells numerous combo lists and US-state level voter registration data. The same vendor offers over 570,0000 (0.57 Million) emails from Japanese citizens for as little as $10 USD that could be for targeted attacks and disinformation campaigns.
One vendor offers a list of millions of US mobile phone customers personal information, including social security numbers and carrier that could be used for spamming and disinformation for $229 USD. The same vendor also has another 8 million Chinese phone numbers for only $200 USD.
Another vendor offers Taiwan’s Ministry of Civil Service database of employees which could be used for targeted phishing to infect government networks for espionage for €69 EUR.
A database containing information for a US Intelligence agency is advertised for sale on White House Market for a mere $100 USD. According to the advertisement and the hackers who obtained this information, it was stolen from a cloud server owned by the US government. The database contains thousands of records of critical detailed information associated with the vendors providing goods and services to the agency. This information could be invaluable for a targeted information operations attack by a nation-state.
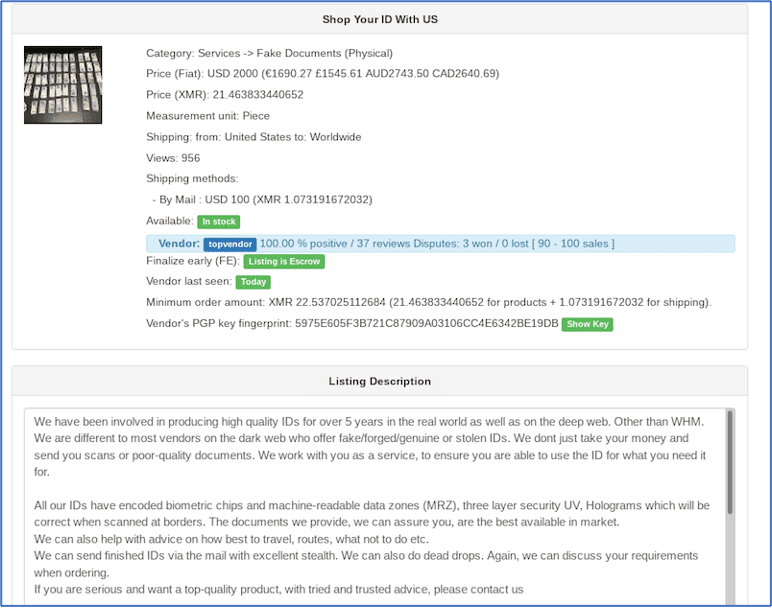
Most nation-state sponsored human intelligence operations require fake identification and passports. Vendors on the darknet offer fake US passports with biometric data for sale for a starting price of $2,000 USD. The advertisement, sold by vendor topvendor on White House Market states that all their identifications have machine-readable data zones, three layer security UV hologram which will readout correctly when scanned at borders. The vendor also offers detailed advice on travel routes and social engineering methodologies for interacting with customs officials.
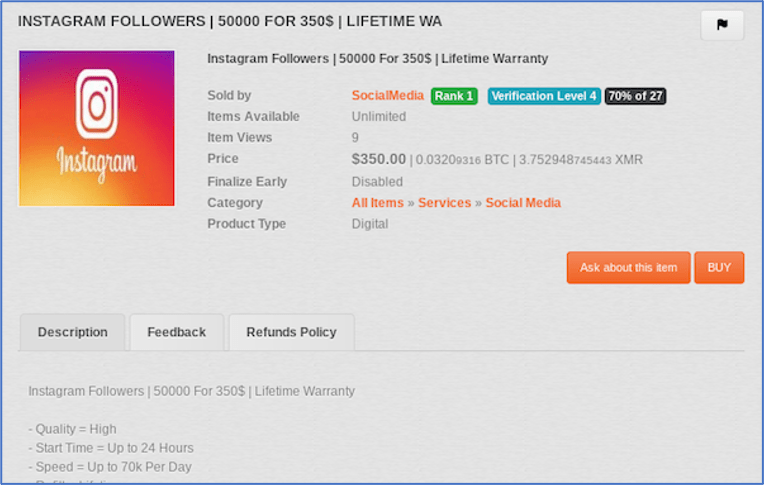
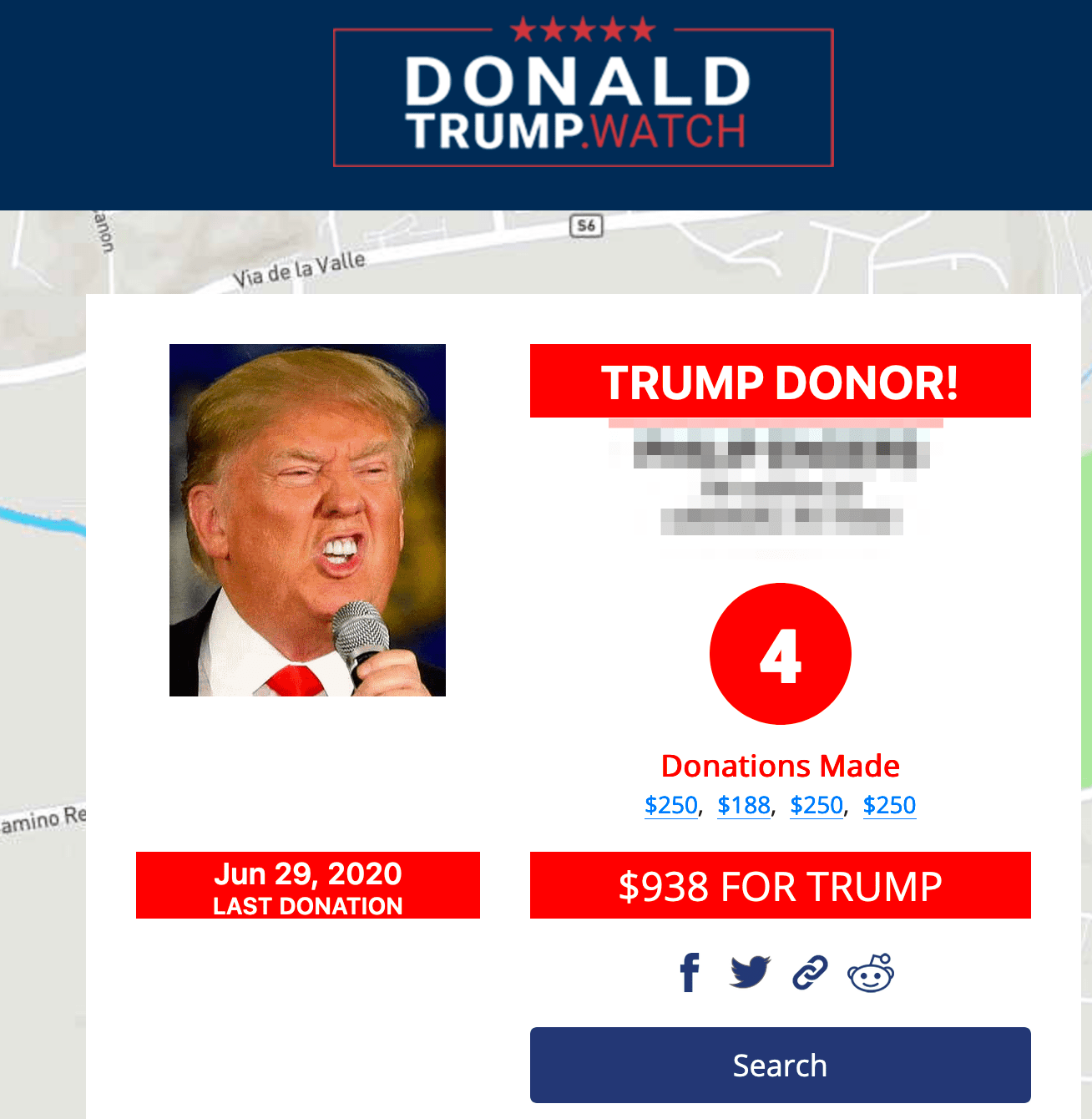
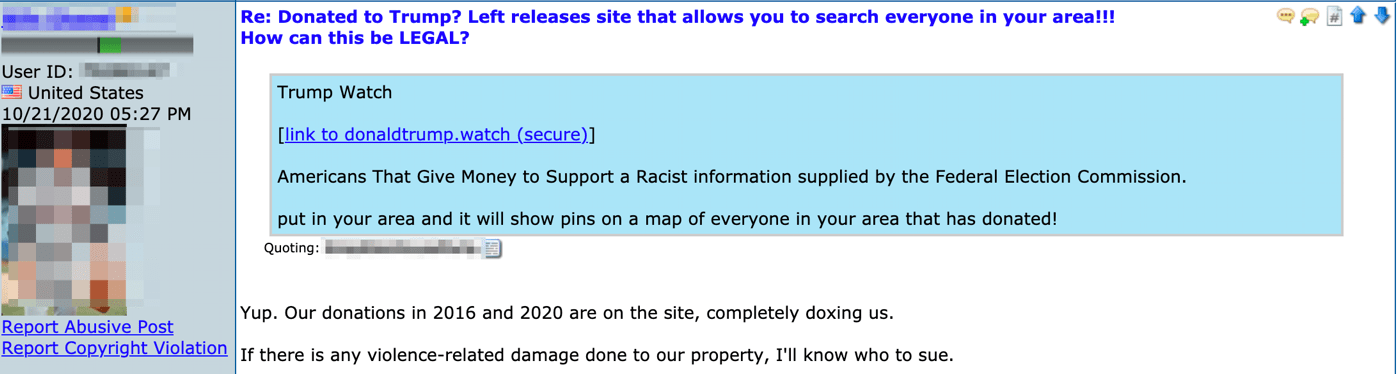
As we reported earlier this year, social media manipulation is an increasingly popular trend by nation state actors to conduct disinformation and propaganda campaigns against their adversaries. Accounts on most all prominent social media platforms are readily available for sale across most darknet marketplaces with digital goods. Long-term established accounts with more ‘followers’ and historical influence are more coveted. One can purchase 1,000 LinkedIn followers for as little as $15 USD on ToRReZ, which could be essential for a nation-state level social engineering or espionage attack, while 50,000 Instagram followers cost upwards of $350 USD. A Facebook campaign to disseminate a particular propaganda agenda is also available for as little as $380 USD from the vendor, etimbuk on the ToRReZ market.
Unique Exploits for Field Operations
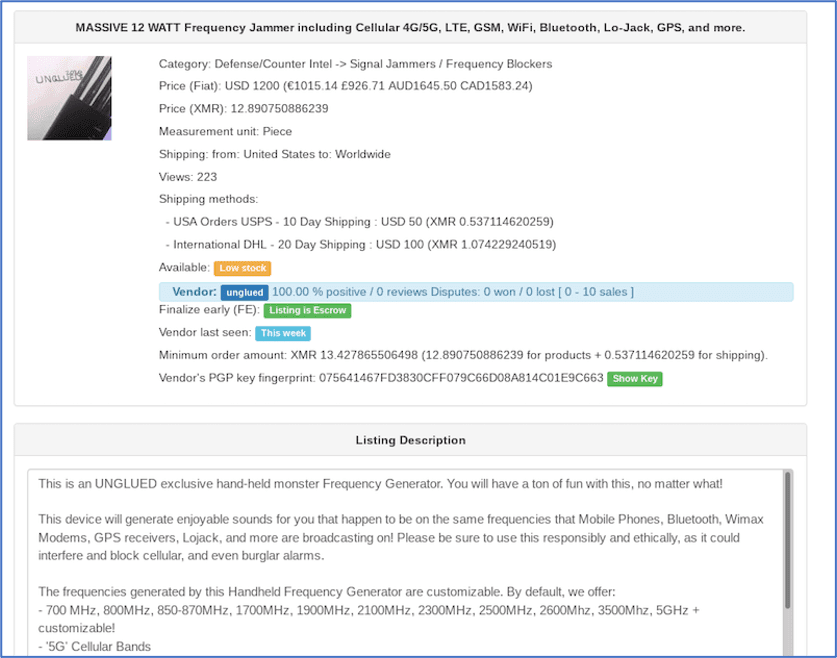
One vendor on White House Market using the pseudonym unglued, recently posted a 12-Watt Frequency Generator for sale on the marketplace. The hand-held device could be utilized by a threat actor to jam and potentially interfere with the operation of a wide range of frequencies including those used by mobile phones, Bluetooth devices, and GPS receivers. Nation-states wanting to conduct in-field operations could greatly benefit from such a device. The unit sells for $1,200 USD.
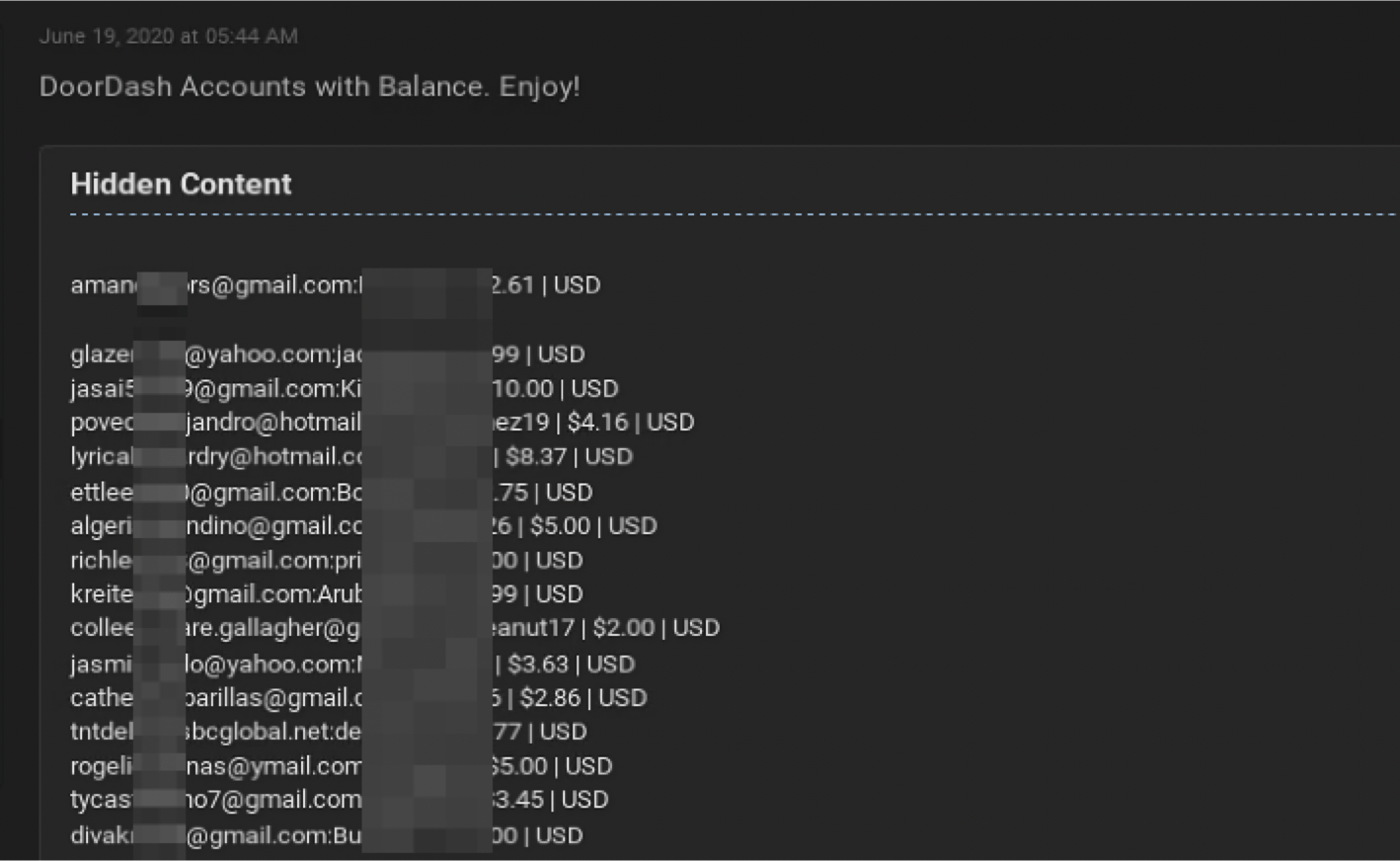
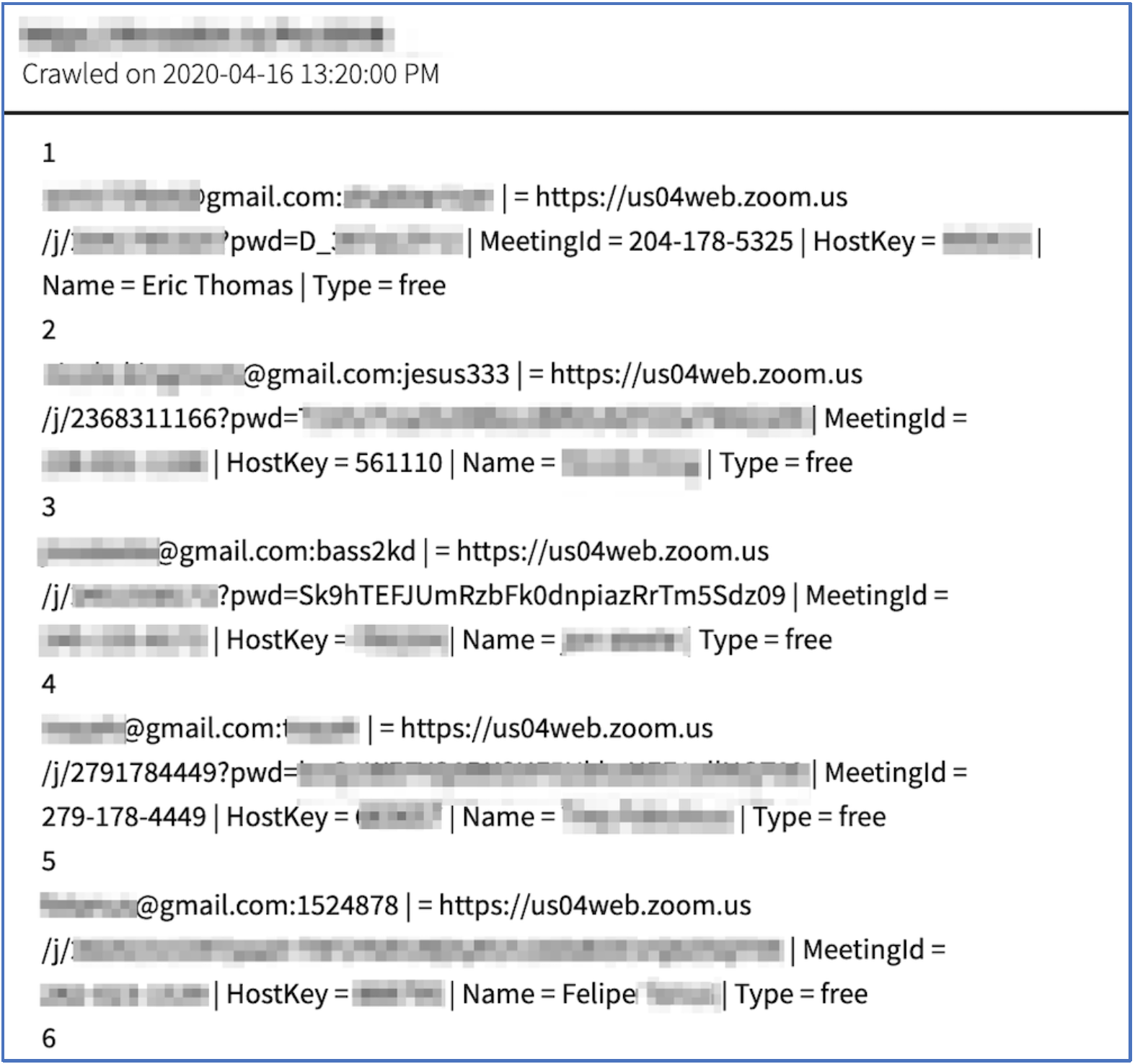
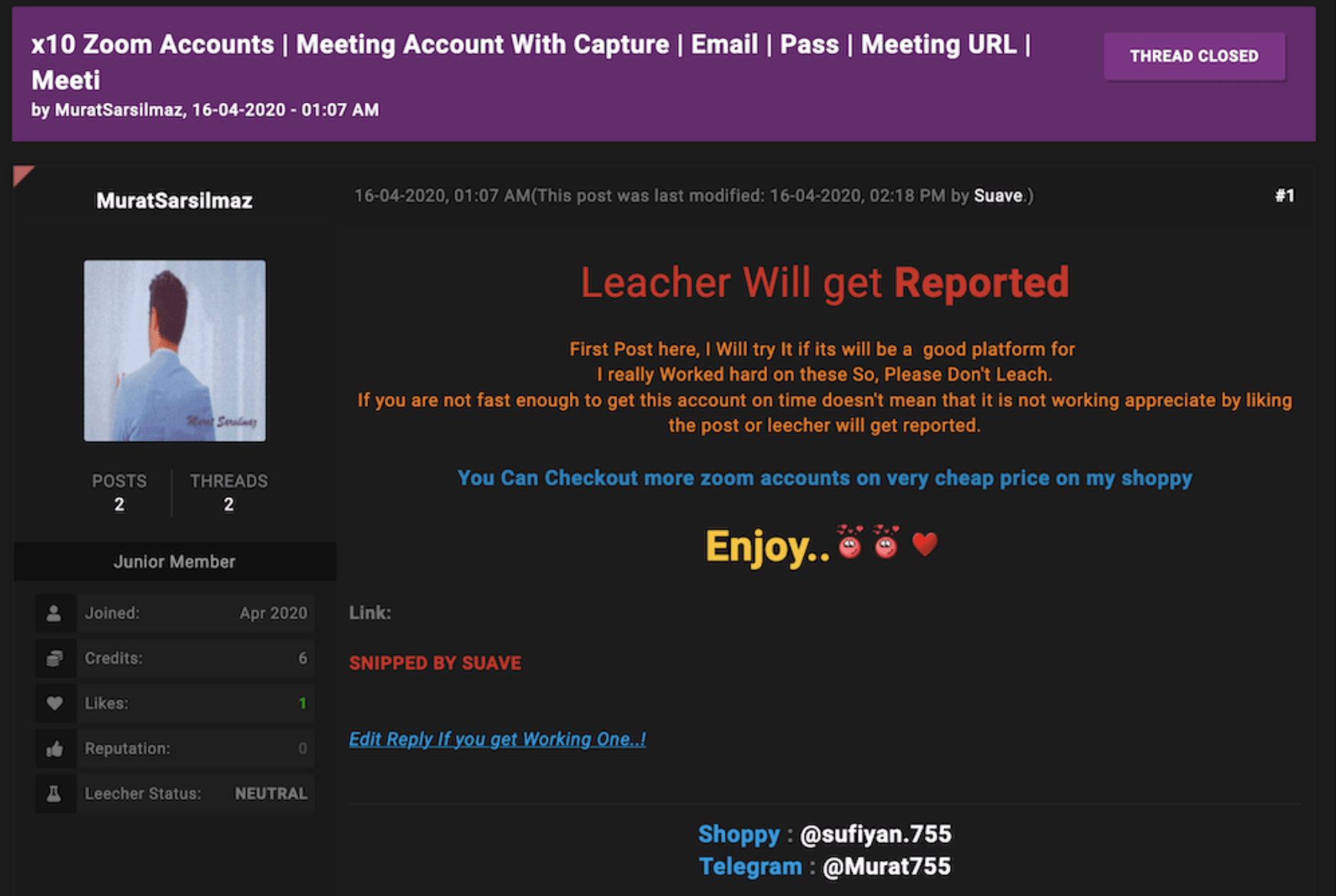
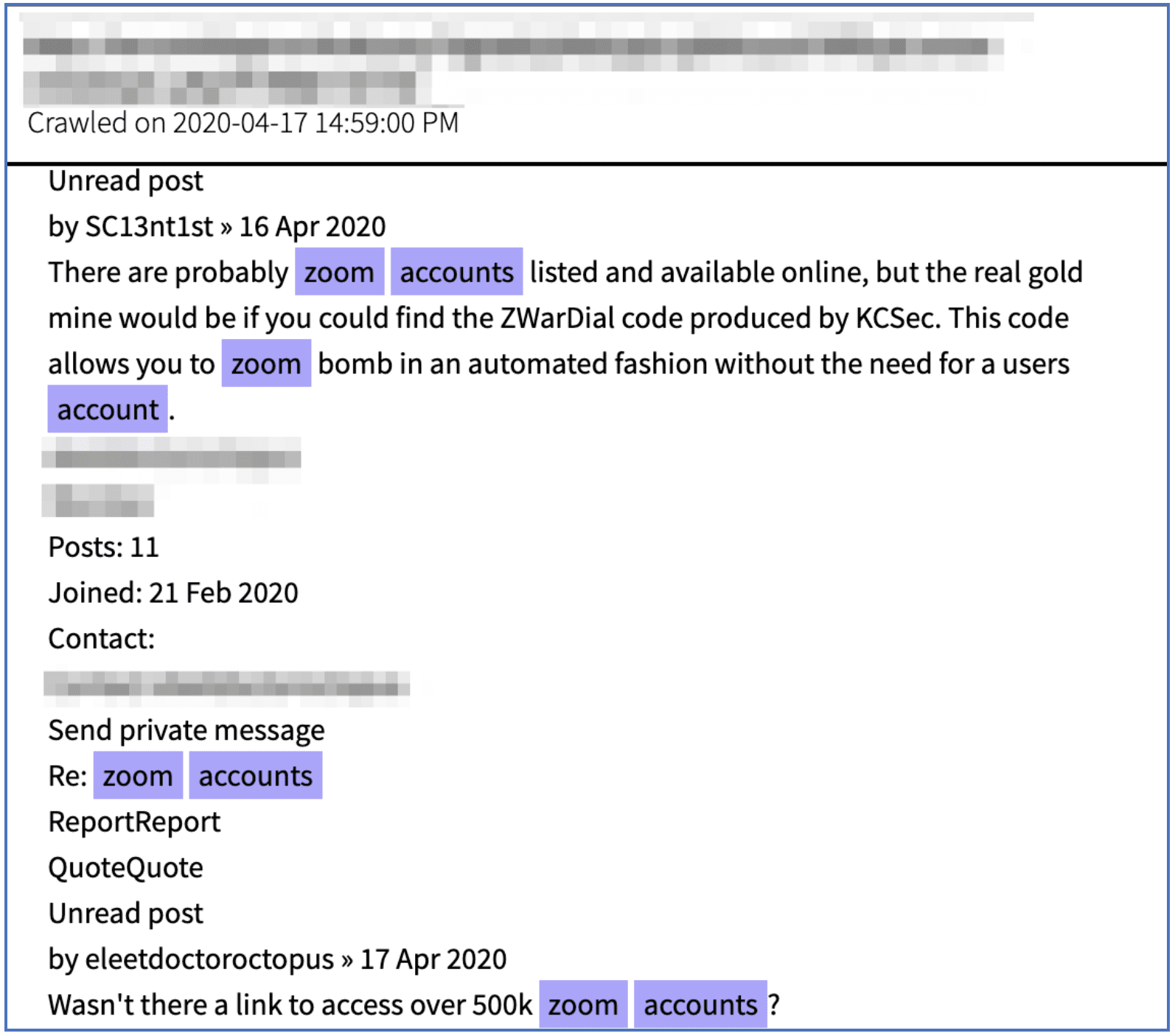
Still the most prevalent cyber weapon: credentials
Exposed credentials will continue to be one of the most prominent threat attack vector for organizational networks by cyber campaign operators, large and small.
According to recent Wall Street Journal reporting, the initial compromise to FireEye was through employee VPN credentials and luckily, the employee alerted IT security when their account had been accessed via an unrecognized device which kickstarted the SolarWinds investigation.
“Hours later, the National Security Agency, America’s top cyberspy organization, issued a broader warning to defense agencies and contractors about vulnerabilities such as those exposed by the SolarWinds attack. Hackers, it said, were finding ways to forge computer credentials to gain wider access across networks and steal protected data stored on in-house servers and cloud data centers. The approach, the NSA said, may have been used in an attack on VMware Inc. software used in national security circles that the spy agency warned about earlier this month.” – Wall Street Journal
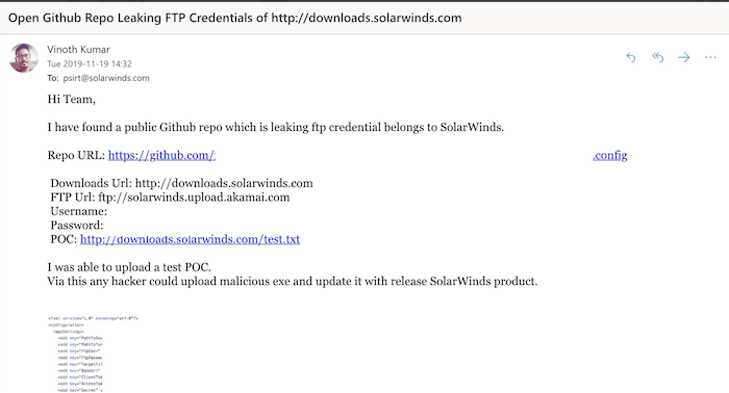
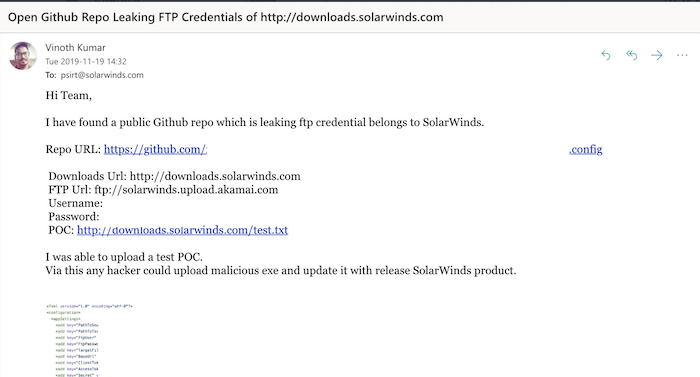
DarkOwl also discovered darknet users talking about key open source reporting regarding the attack, more specifically, Vinoth Kumar posted to social media that he found a public Github repo leaking credentials belonging to SolarWinds since June 2018.
Leveraging vulnerabilities uncovered in the Microsoft platform, nation-state hackers behind the SolarWinds attack also accessed key leadership emails at U.S. Treasury Department and other critical U.S. government agencies.
DarkOwl Vision has indexed over 6,100 documents containing compromised e-mail addresses and passwords for federal employees using the treasury.gov email domain.