DarkOwl 2025 Recap: A Quick Reflection & Updates
December 30, 2025
As 2025 draws to a close, as we do every year, our content and marketing teams are taking a moment to reflect on the exciting events, trends, and changes the DarkOwl team experienced throughout the year. From major product advancements to strategic partnerships and thought leadership in the darknet intelligence space, this year has been marked by progress and momentum. We’re grateful to our customers, partners, and community for your continued engagement and support — and we look forward to building on these successes in 2026!
We hope you continue to find the topics we explore valuable, enlightening, and engaging. One final marketing reminder for the year: be sure to sign up for our weekly newsletter to stay updated on the latest insights from our research and content teams!
Around the World & Across the Industry
In 2025, DarkOwl continued its commitment to engaging with the global cybersecurity community. The team was active at leading industry events, including the RSA Conference in San Francisco, where we showcased our platform capabilities and met with peers and customers to discuss the evolving threat landscape. Check out where we will be in 2026 and request time to meet here.
Beyond trade shows, DarkOwl shared insights through webinars and blog posts on cutting-edge topics — from artificial intelligence’s role in threat intelligence to emerging darknet trends — providing thought leadership to practitioners and analysts worldwide.
And don’t worry! The team also made time for some fun. This summer, in our annual company get-together, we got to meet our adopted owl. 3 years ago, we adopted an owl! He jumped early from his Michigan nest in 2015 and fractured his right wing in two places and was on the ground for about a week next to a barn before he was picked up by the landowners and brought to a rehabilitation center. He was sent to the Raptor Education Foundation in Denver in August, 2016 where he now lives. You can learn more about him on his dedicated adoption page.

RSA Conference in San Francisco, CA

The team at HQ in Denver, CO

ISS World Europe in Prague, Czech Republic
We love our #Pets!
Gotta show some pet love as well from our Pets Slack Channel (the best channel).😻



Yearly reminder: DarkOwl analysts and their pets recommend you never use your pet’s name in any password combination as it is a popular term for threat actors using brute force attacks.
Product Enhancements & Platform Innovations
Throughout 2025, our Product Team rolled out significant updates designed to empower analysts and security teams with deeper, more actionable darknet intelligence:
- Enhanced Case Management: Vision UI now supports improved team workflows and collaboration with enhanced Case Findings features that include inline annotation and visual summary dashboards.
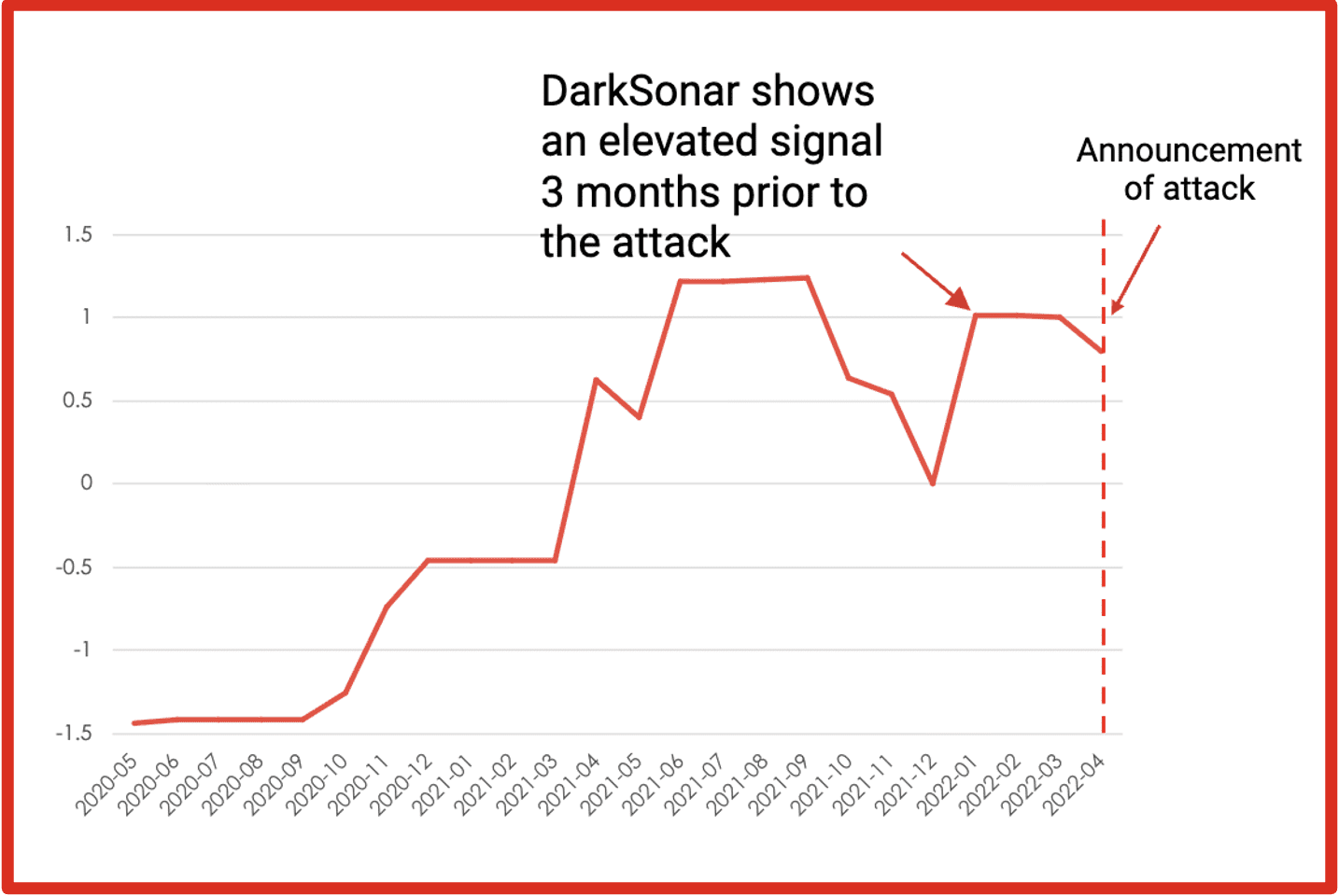
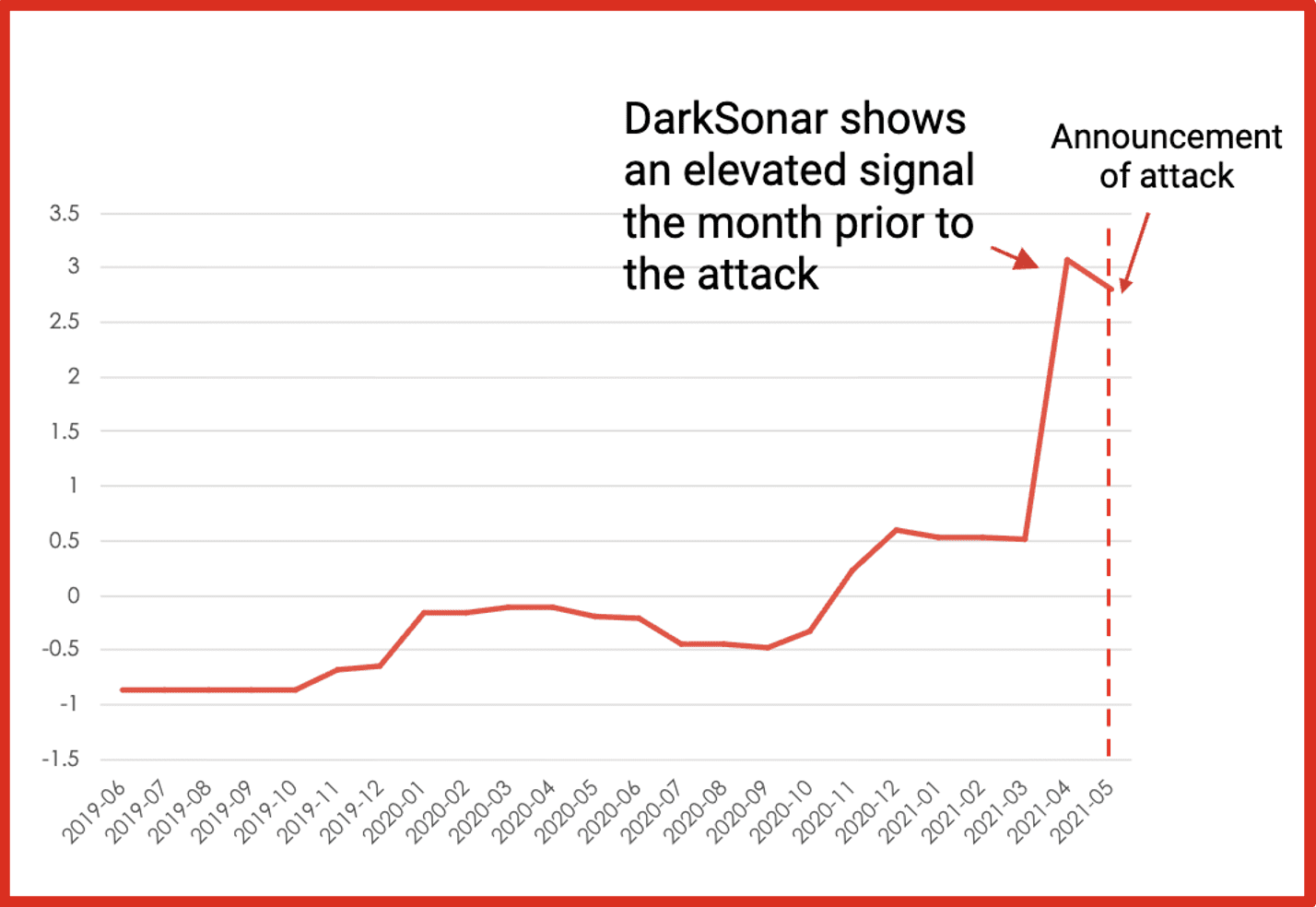
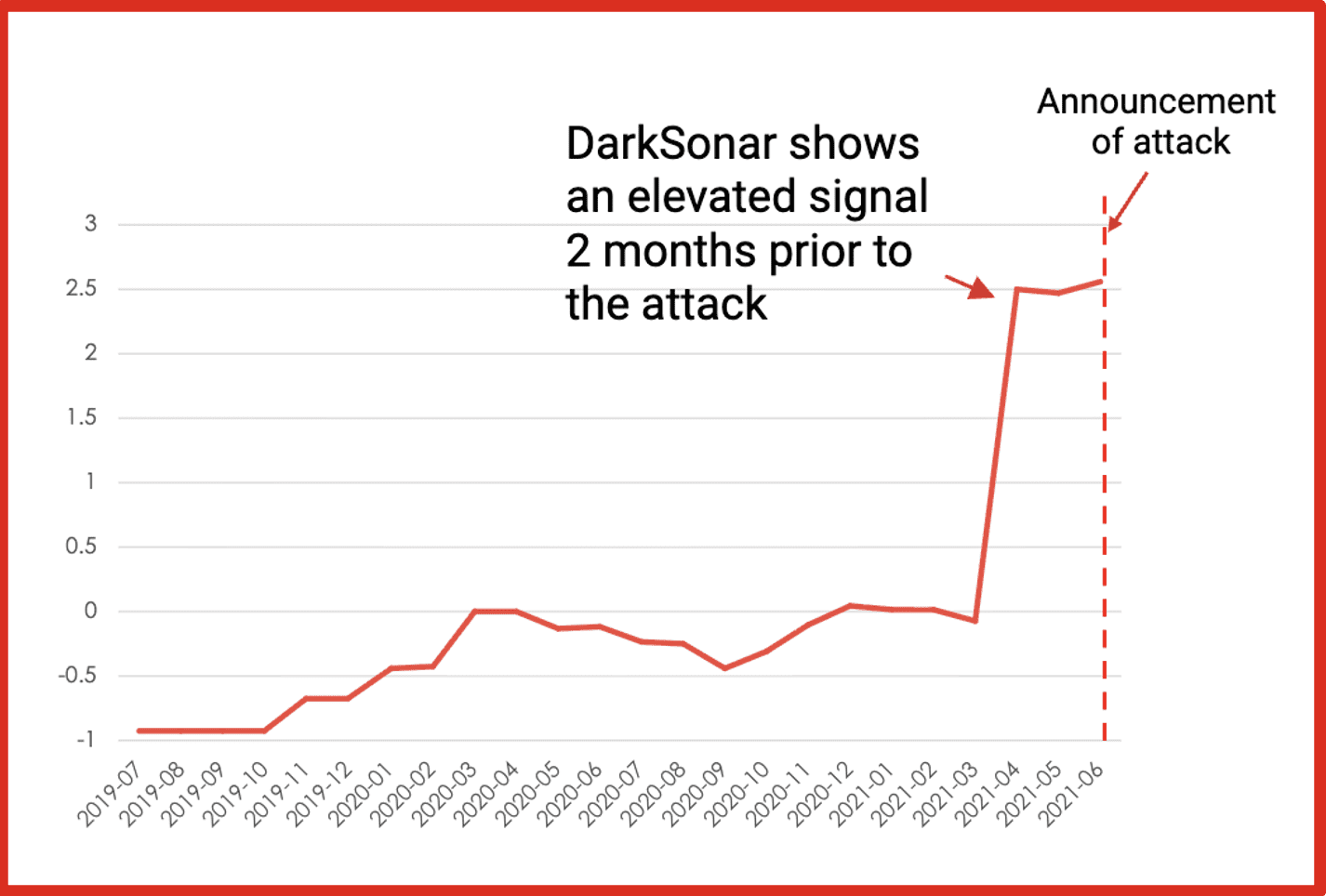
- Leak Visualizations & Timeline Analytics: New visualizations help users grasp leak compositions and alert trends over time — enabling richer analysis and faster decision making.
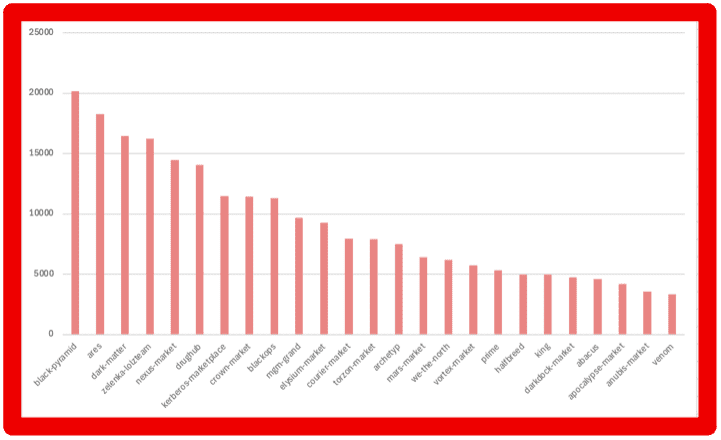
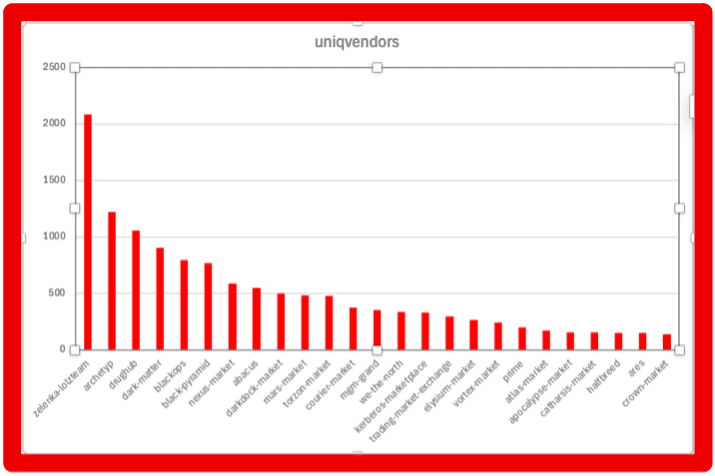
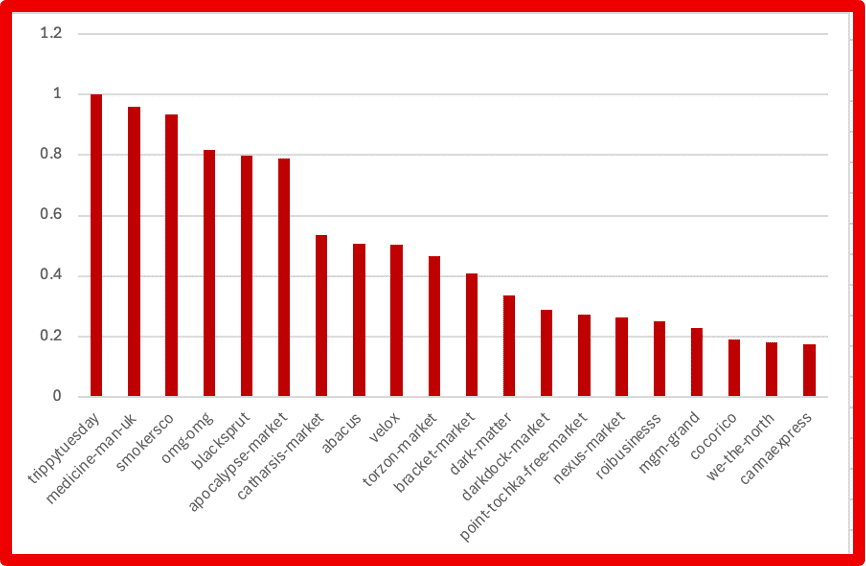
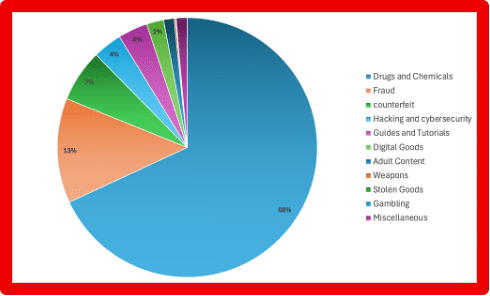
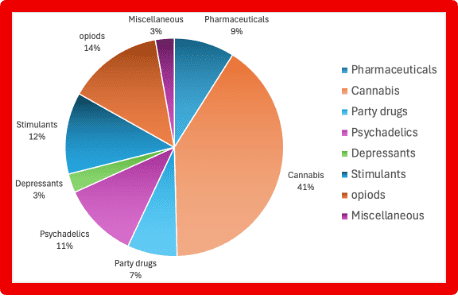
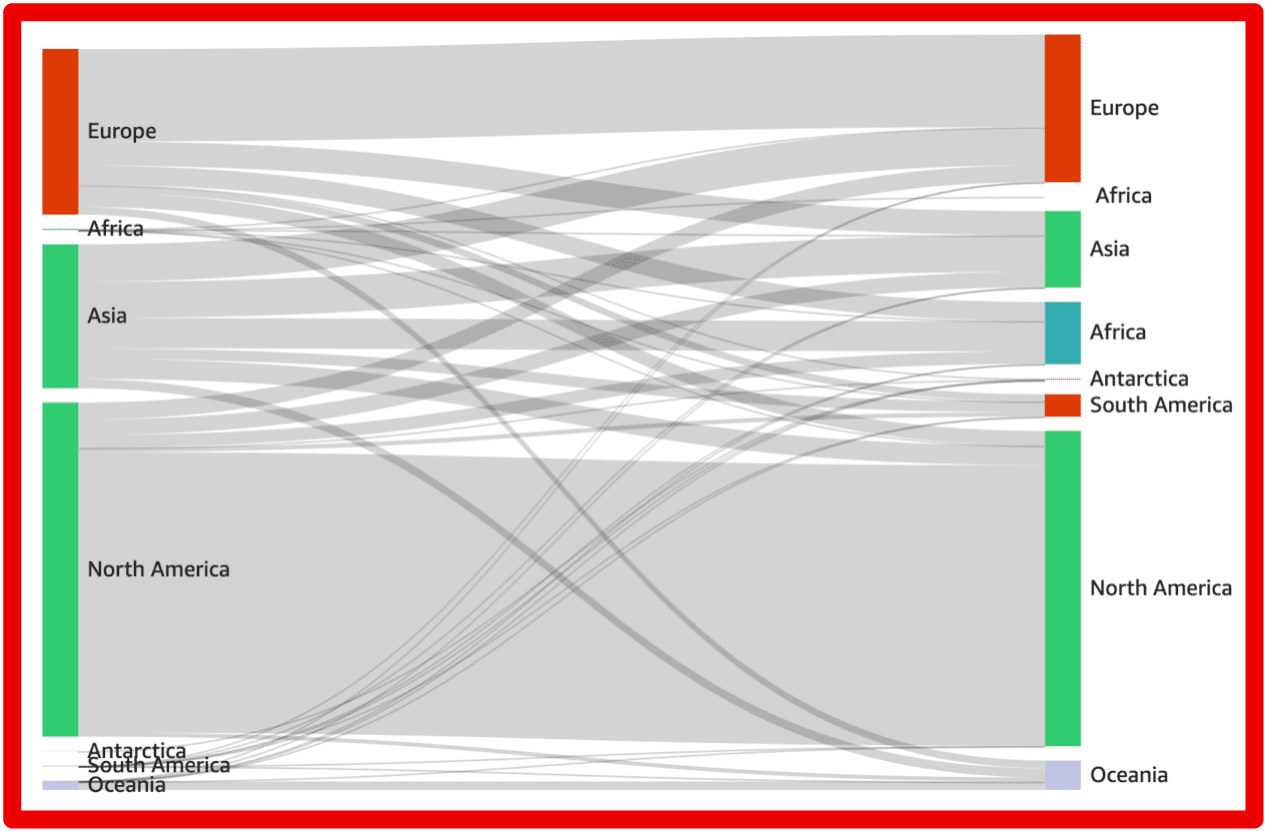
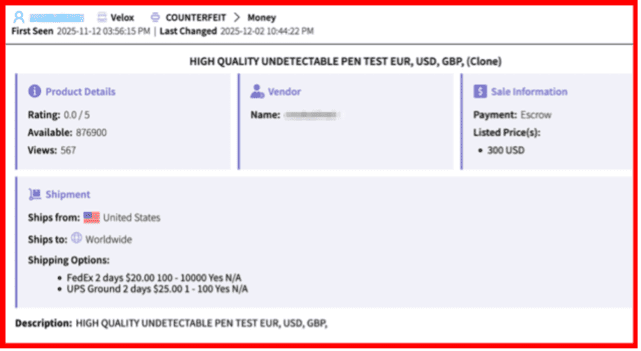
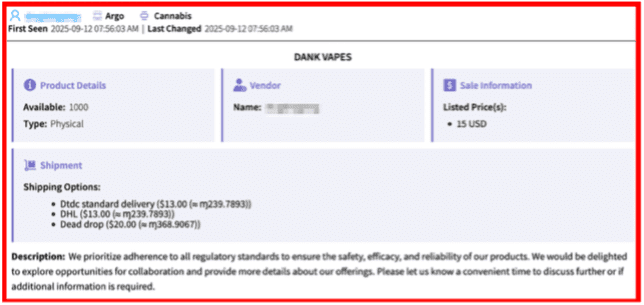
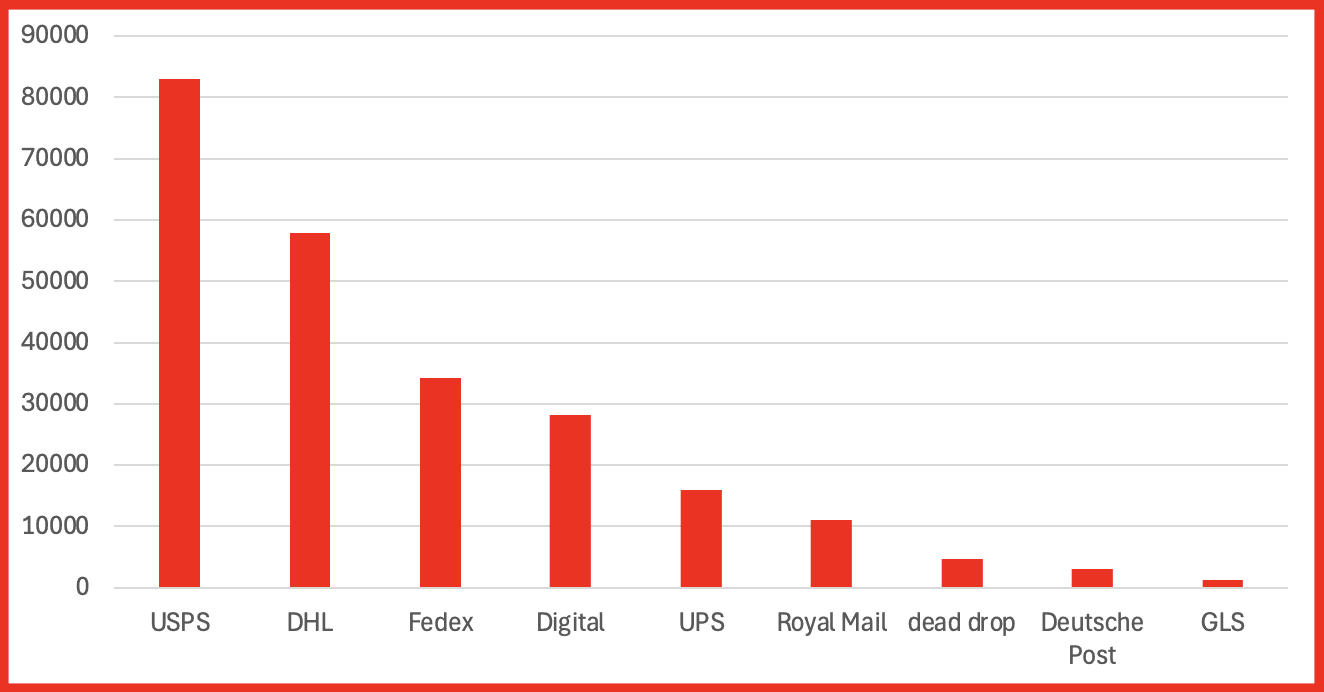
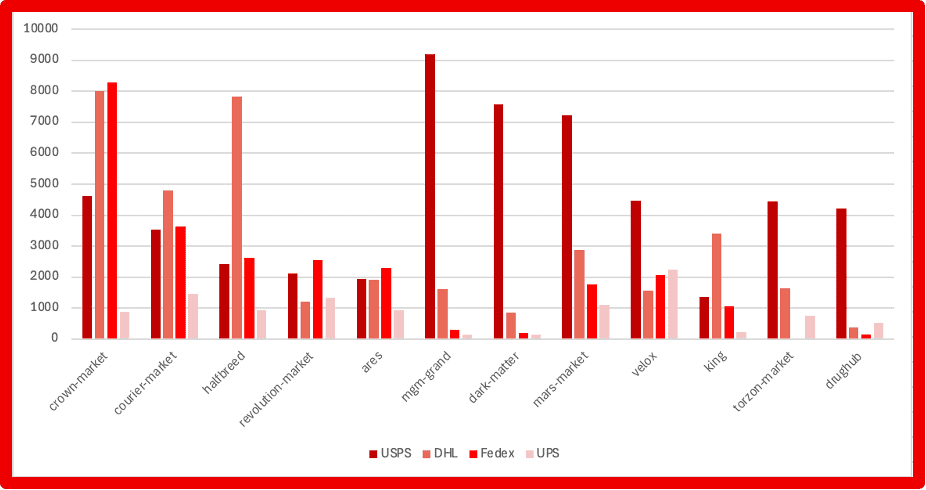
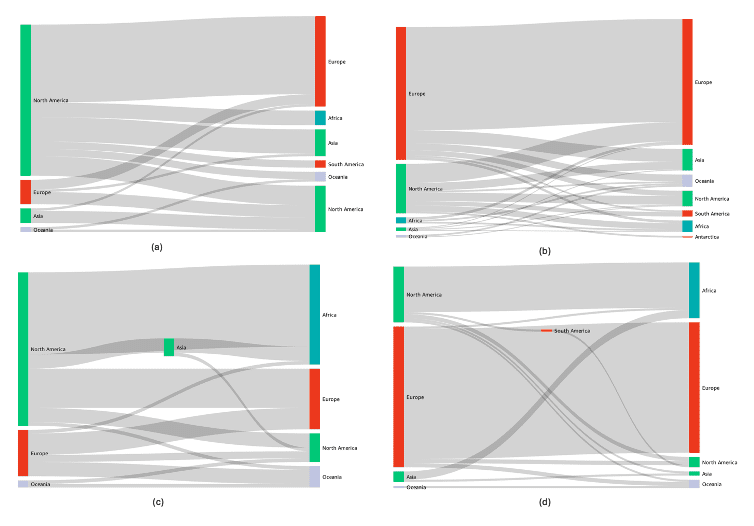
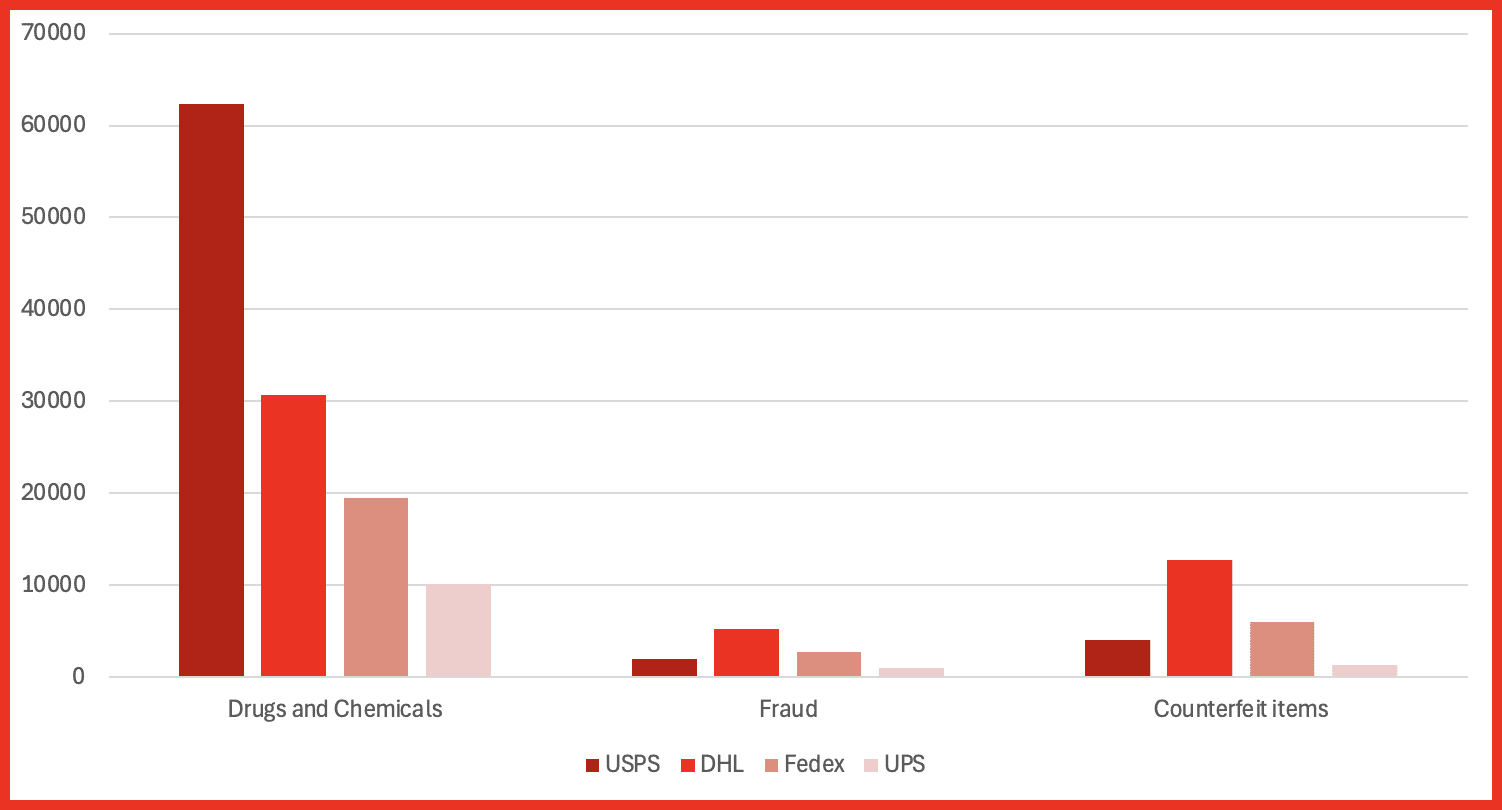
- Marketplace Intelligence: A major expansion of darknet marketplace capabilities incorporates rich structured data across dozens of fields — from vendor info to pricing and shipping — directly in Vision UI and API.
- Universal Phone Query Builder & Export Flexibility: We introduced a Universal Phone Number Builder and expanded reporting formats — including Word export — to support a variety of operational needs.
These enhancements reflect our ongoing commitment to refining workflows, increasing visibility into complex data, and enabling faster, smarter insights for our users. These are just a few of the product updates made throughout the year! You can check out more in our quarterly blogs, starting here.
Community & Education: Sharing Knowledge
DarkOwl’s blog continued to be a hub for expert analysis on darknet intelligence, cyber threats, and cybersecurity trends. Notable posts from late 2025 included practical guides on cyber hygiene, explorations of how threat actors operate, and even insights into unique aspects of darknet ecosystems like vendor shipping choices.
In addition, DarkOwl was selected as the darknet technology of choice for Channel 4’s series Hunted, offering real-world demonstrations of how darknet intelligence supports investigative work.

Partnerships & Strategic Collaborations
2025 saw DarkOwl strengthen its global reach through a series of partnerships aimed at bringing darknet intelligence to more organizations:
- Strategic Alliance with Ticura: A collaboration to simplify dark web monitoring workflows and broaden operational accessibility for security teams and MSSPs alike.
- 8com GmbH & Co. KG Partnership: 8com integrated DarkOwl’s Vision UI and Search API into its SOC workflows to enhance early detection of compromised data and proactive defense measures.
- Global Reseller Partnerships: Authorized reseller agreements — including with Hottolink in Japan — expanded access to DarkOwl’s threat intelligence solutions across international markets.



These collaborations underline DarkOwl’s role as a trusted provider of darknet intelligence to enterprises, security practitioners, and service providers around the globe.
Looking Ahead to 2026
As we close out 2025, we are energized by the rapid evolution of both cybersecurity challenges and the tools needed to address them. DarkOwl is committed to pushing the frontier of darknet intelligence — delivering deeper insights, smarter workflows, and stronger partnerships that equip our customers to stay ahead of threats.
Thank you for being part of our 2025 journey. Stay connected by subscribing to our newsletter, engaging with our content, and joining us at events in the year ahead!