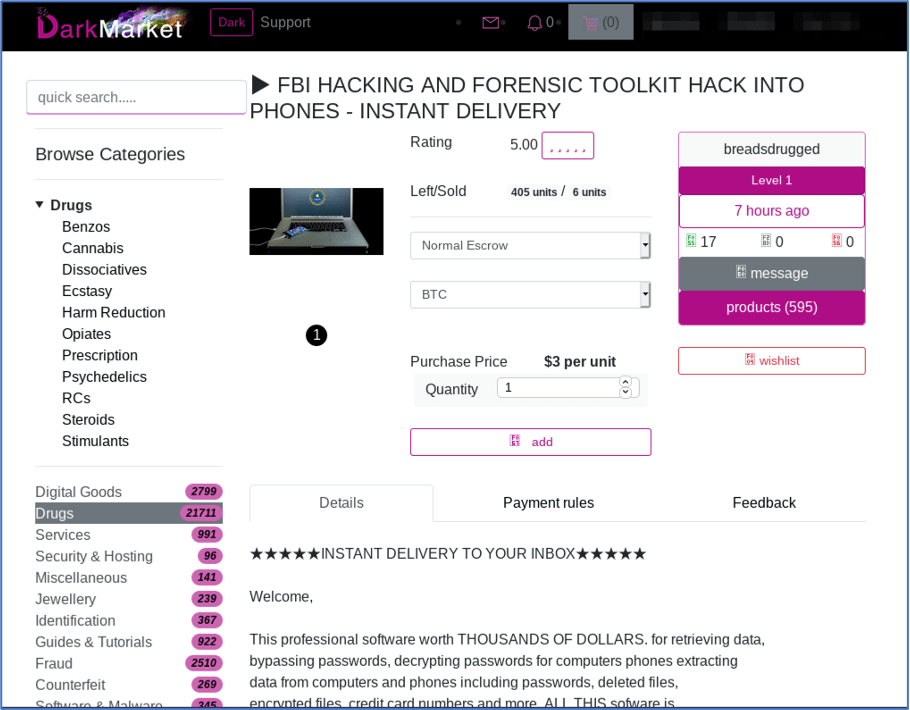
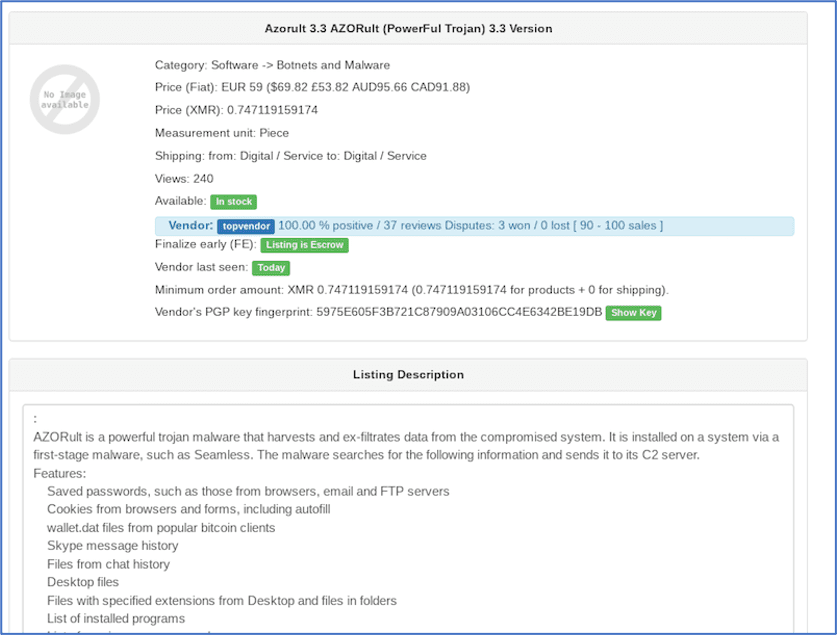
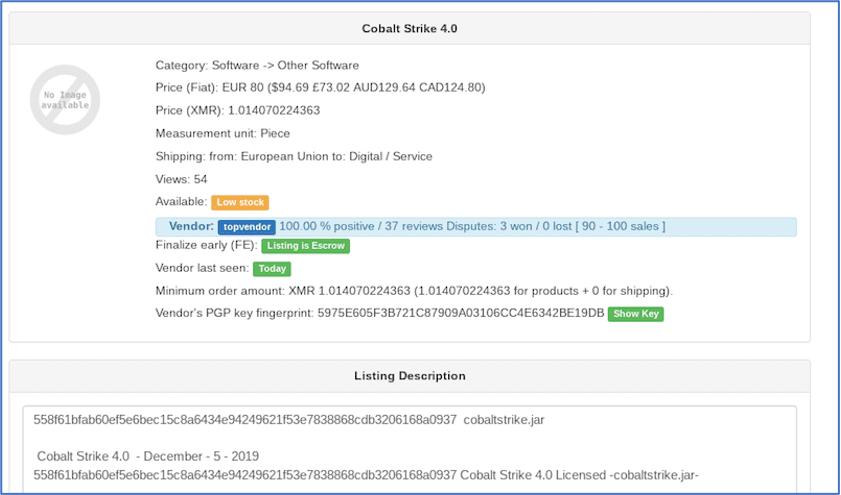
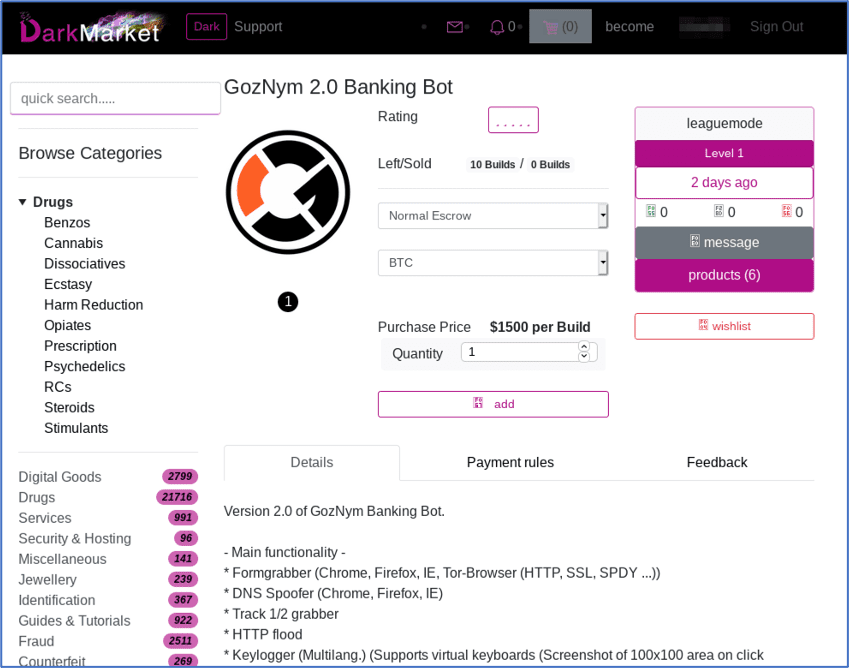
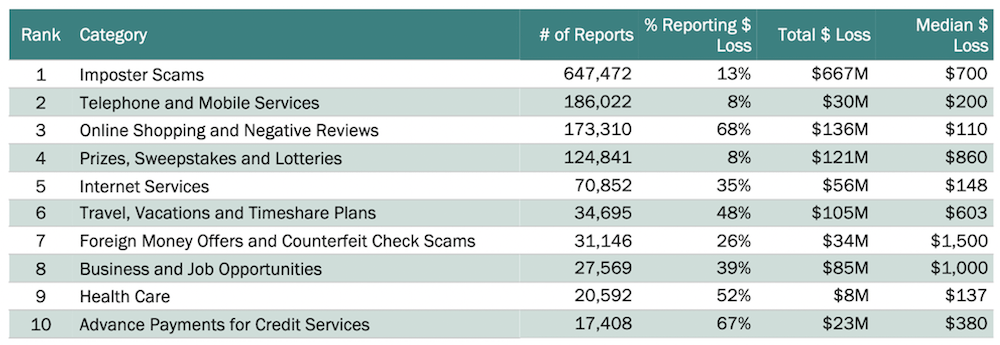
Unemployment Fraud on the Darknet
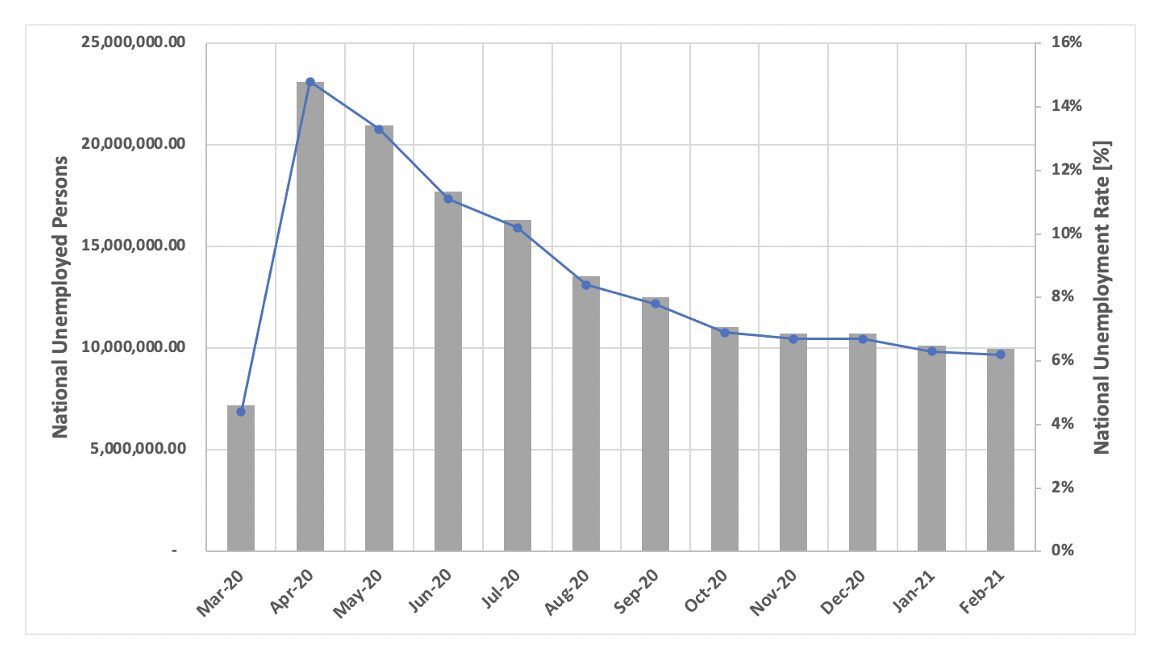
In April 2020, within weeks of widespread lockdown and quarantine caused by the coronavirus or COVID-19 pandemic, the U.S. Bureau of Labor and Statistics reported that over 23.1 million people were unemployed across the United States. This surge in out-of-work adults caused record spikes in unemployment claims across state benefits systems, many of them unable to accommodate the increased demands in benefit requests.
Figure 1: Chart Derived from U.S. Bureau of Labor and Statistics (Source – Courtesy of Department of Numbers)
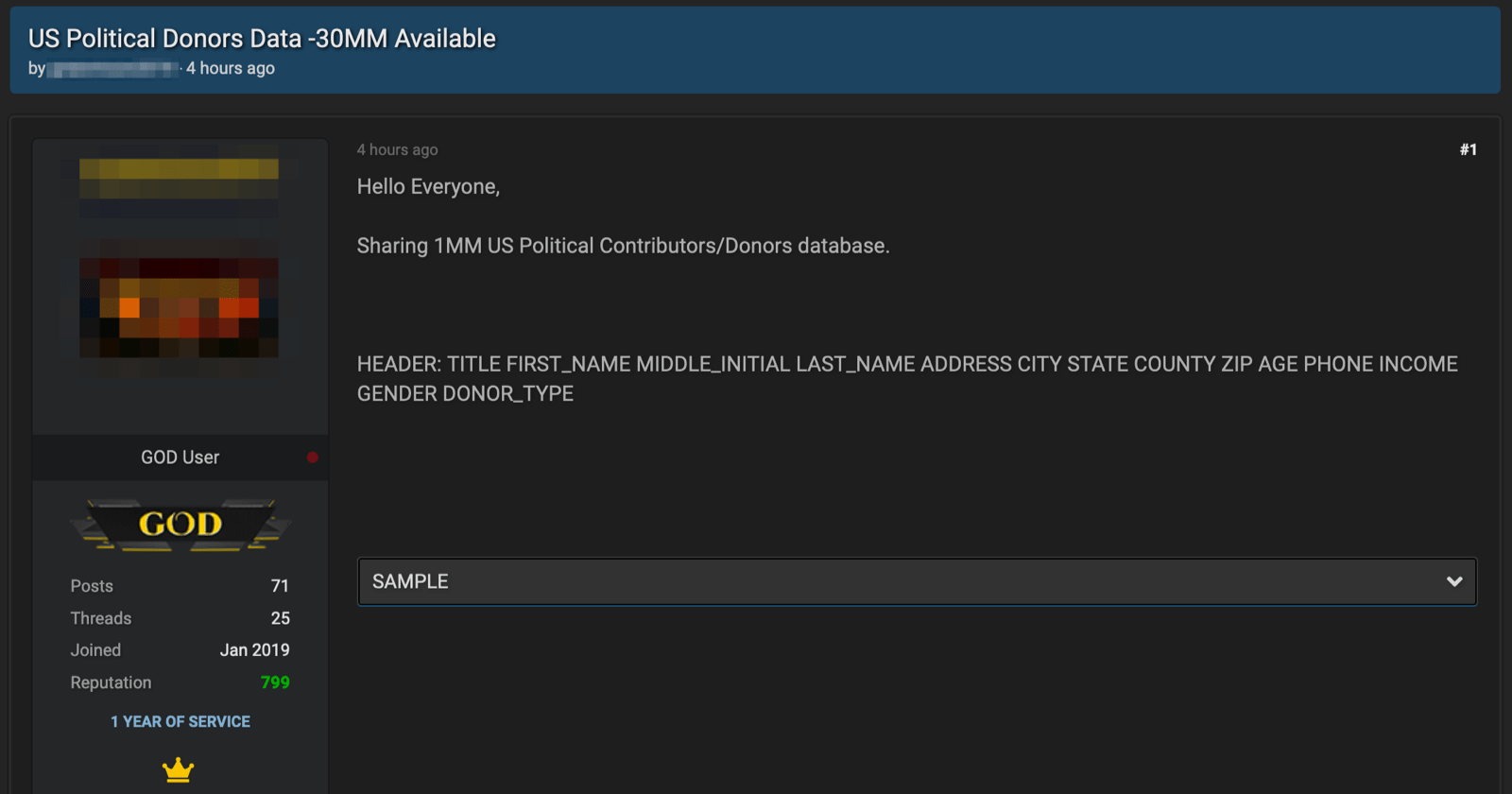
As a result, fraudsters on the darknet and deep web quickly capitalized on flaws in the state-run unemployment benefits systems, directly compromising claimant accounts to redirect unemployment payments, submitting false unemployment claims using illegally obtained personally identifiable information (PII).
Aiding in the exploitation of these programs are the plethora of available detailed step-by-step instructions known as ‘methods’ or ‘sauce’ that are readily available for purchase across the darknet.
Serious fraud yields serious capital for cyber criminals
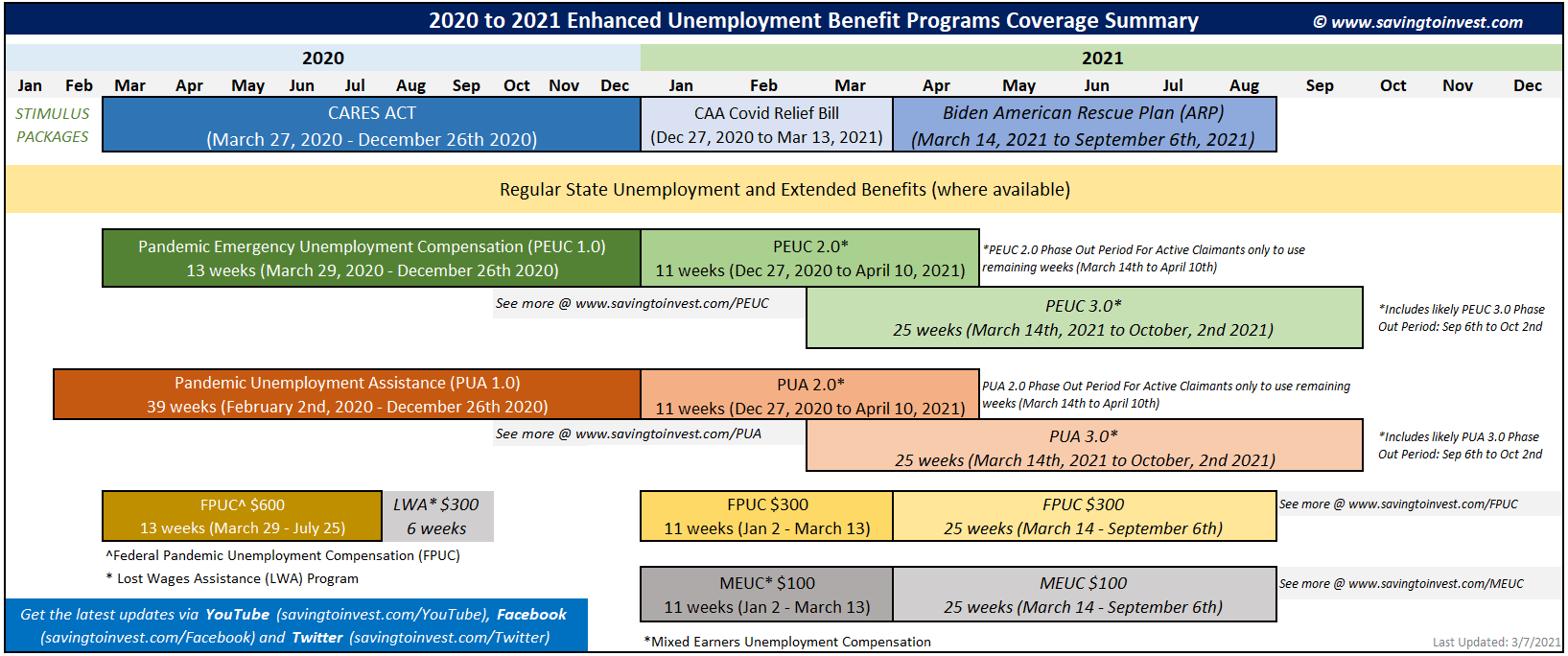
With record numbers of persons unemployed comes record financial programs to cover these claims. The Coronavirus Aid, Relief and Economic Security (CARES) Act, signed into law in March, 2020 at $2.2 trillion USD, provided multiple lines of funding for unemployed U.S. workers including $260 billion USD in direct funding for expanded unemployment insurance.
-
The original unemployment supplemental was known as the Federal Pandemic Unemployment Compensation (FPUC) program. This program provided an extra $600 per week for individuals who already qualified for state unemployment compensation from late January 2020 through July 31, 2020.
-
The Pandemic Emergency Unemployment Compensation (PEUC) funding program provided an extended benefit period to individuals who have exhausted their unemployment benefits under existing state or federal law, have no right to regular unemployment benefits under any state law or other compensation under any federal law.
-
The Pandemic Unemployment Assistance (PUA) program was setup to provide unemployment compensation to individuals who would not ordinarily qualify for unemployment such as: gig workers and freelancers, independent contractors and self-employed persons, or those who have exhausted all other rights to state or federal unemployment (including PEUC). Qualifying individuals were eligible to receive up to 39 weeks of benefits for being unemployed between January 27, 2020 and December 31, 2020.
The difference between PEUC and PUA is that the PEUC essentially extends benefits by up to 13 weeks for individuals otherwise qualified to receive regular unemployment, but who have exhausted those benefits. DarkOwl has observed both programs mentioned extensively across the fraud community in the darknet and deep web.
In December 2020, the U.S. Government passed the Continued Assistance Act (CAA), totaling $900 billion, which extended the federal benefits of the CARES Act from December 27, 2020 to March 13, 2021. The CAA extended the benefits for an additional 11 weeks, and also provides an extra $300 per week for all benefits recipients.
This act also included a new supplemental known as Mixed Earners Unemployment Compensation (MEUC) program intended to address gaps in the original stimulus package penalizing with those mixed income from multiple sources who receive lower unemployment benefits because they were only deemed eligible for regular state unemployment or PEUC due to their wage-based income.
The MEUC program is subject to state discretion and very few states have adopted the new payment terms of providing mixed income earners an extra $100 USD per week.
Figure 2: 2020 to 2021 Enhanced Unemployment Benefit Programs Coverage Summary (Source)
Overview: Pandemic-related unemployment fraud on the darknet
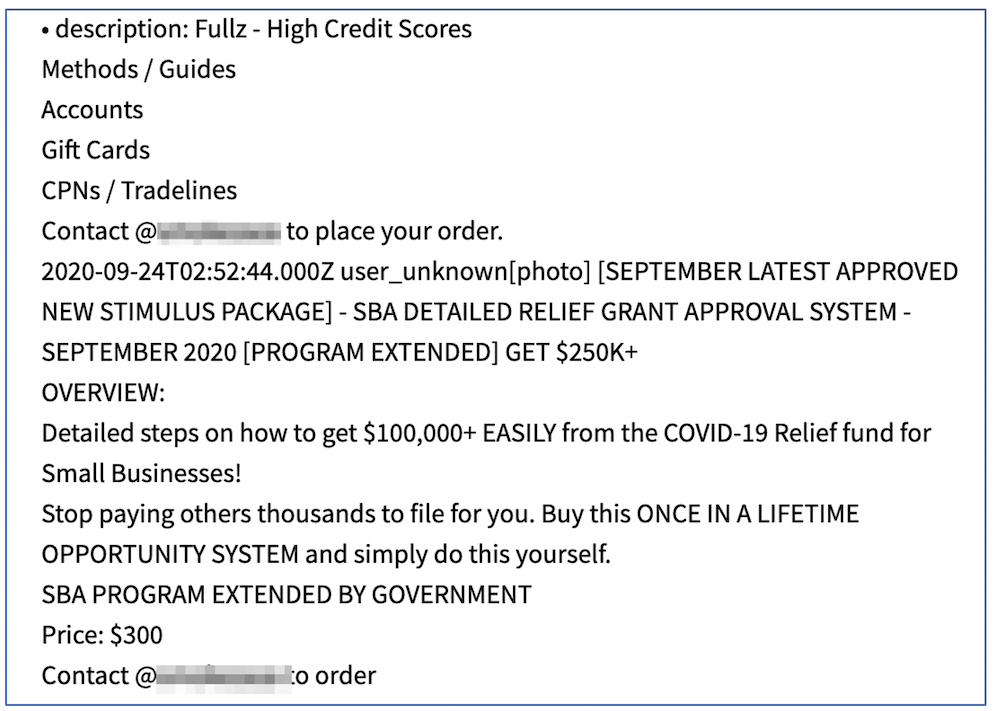
“Sauce” for sale
On the darknet, fraudsters and cybercriminals have become intimately familiar with these programs offering elaborate guides and tutorials detailing how to fraudulently make claims against the different financial unemployment assistance programs. Described as “sauce,” fraudsters offer the methods for sale on darknet marketplaces, in private and public chatrooms, and on social media.
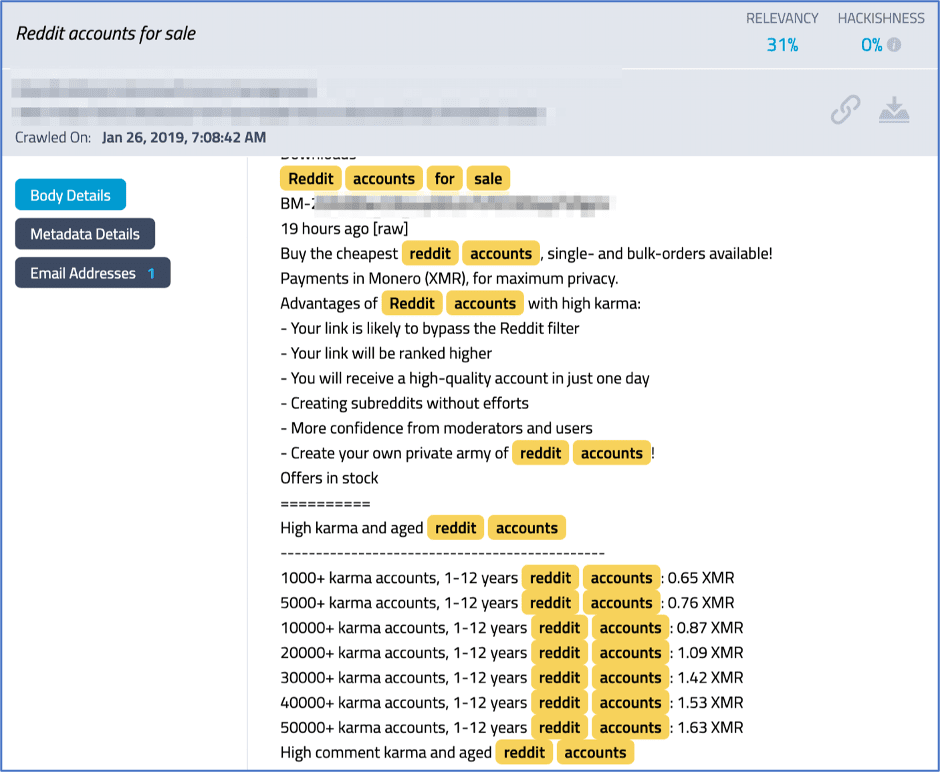
The going rate for a detailed unemployment fraud method varies between $200 and $300 USD and offered specifically by state, suggesting that different state unemployment systems may require unique techniques for direct exploitation.
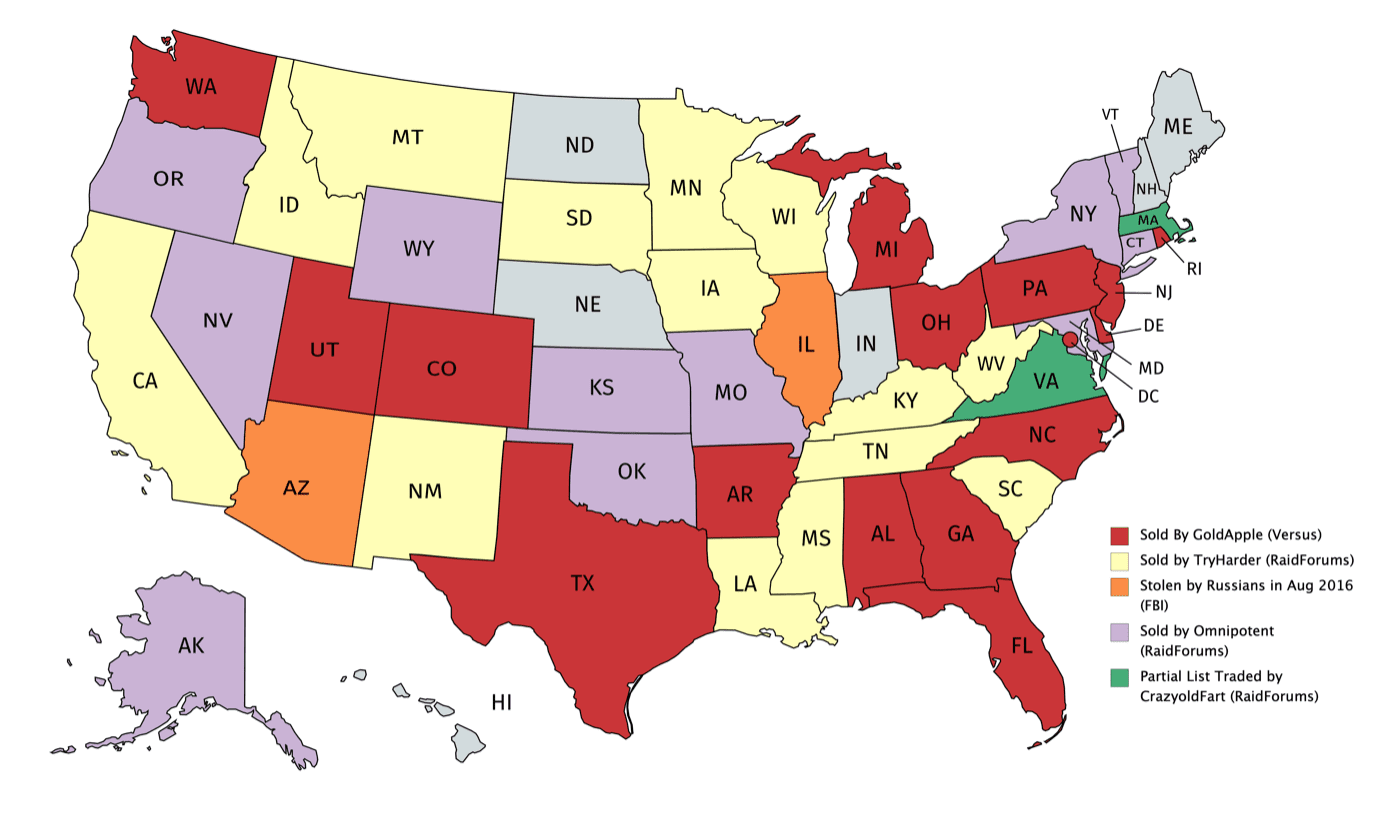
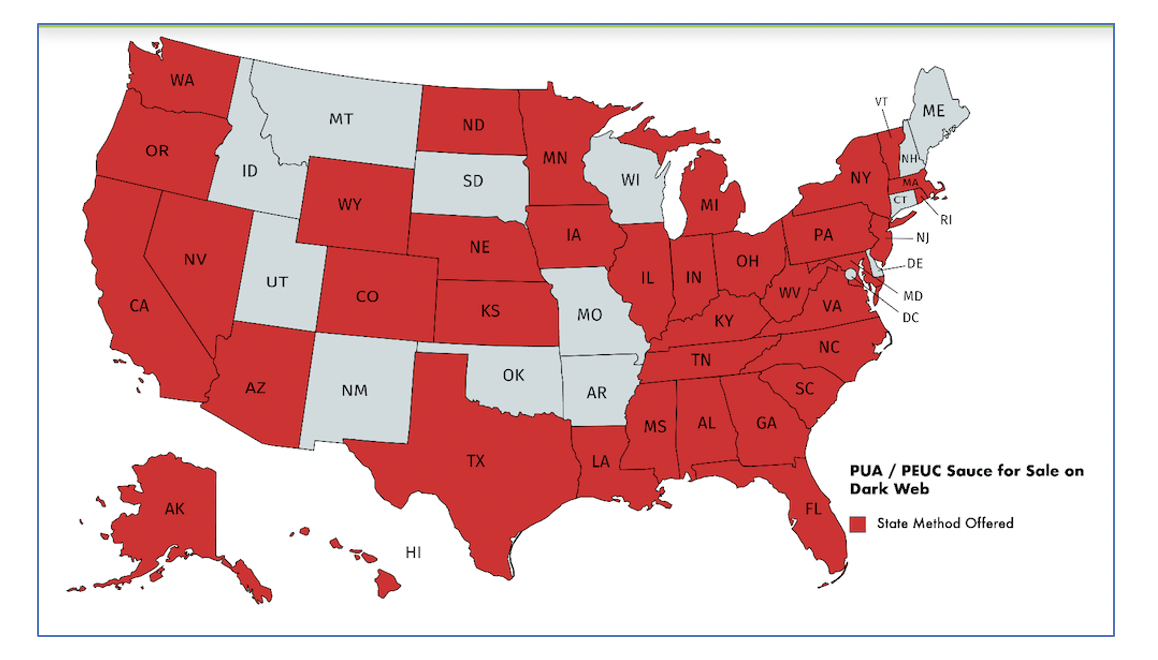
According to DarkOwl Vision, PUA is mentioned more often than PEUC, likely cause there is fewer historical work data reporting requirements for freelancers and sole proprietors covered by the PUA method and thus easier to defraud. DarkOwl has observed the PUA “sauce” for sale for the specific states listed below – with over 75% of the United States mentioned in offers across the darknet and deep web. This does not indicate that only these states have been exploited, but merely that these are the states observed advertised in the darknet communities DarkOwl has access to over the last year.
Pandemic Unemployment Assistance exploitation “how-to” guides are being sold for the following states:
AlabamaAlaskaArizonaArkansasCaliforniaColoradoFlorida GeorgiaHawaiiIllinois Indiana Iowa Kansas KentuckyLouisiana Maryland Massachusetts Michigan Minnesota MississippiNebraska Nevada New Jersey New York North Carolina North Dakota OhioOregonPennsylvaniaRhode IslandSouth CarolinaTennesseeTexasVermontVirginiaWashingtonWest Virginia WyomingFigure 3: Users on the darknet are selling PUA “sauce”, or how-to guides for exploiting unemployment programs, for the states colored in red above
Fraudsters selling PUA and PEUC methods are highly adaptive and acutely aware of security methods states are implementing to combat fraud, often updating the “sauce” frequently with the latest and greatest information. This includes new offers of “backpay sauce” opportunities with the latest relief funding being approved for states that ran out of unemployment relief funds.
According to the most recent fraud group chatter, Ohio has been mentioned more frequently with the phrase “Ohio is lit and still paying” acknowledging that some states’ anti-fraud methods are not as effective as others.
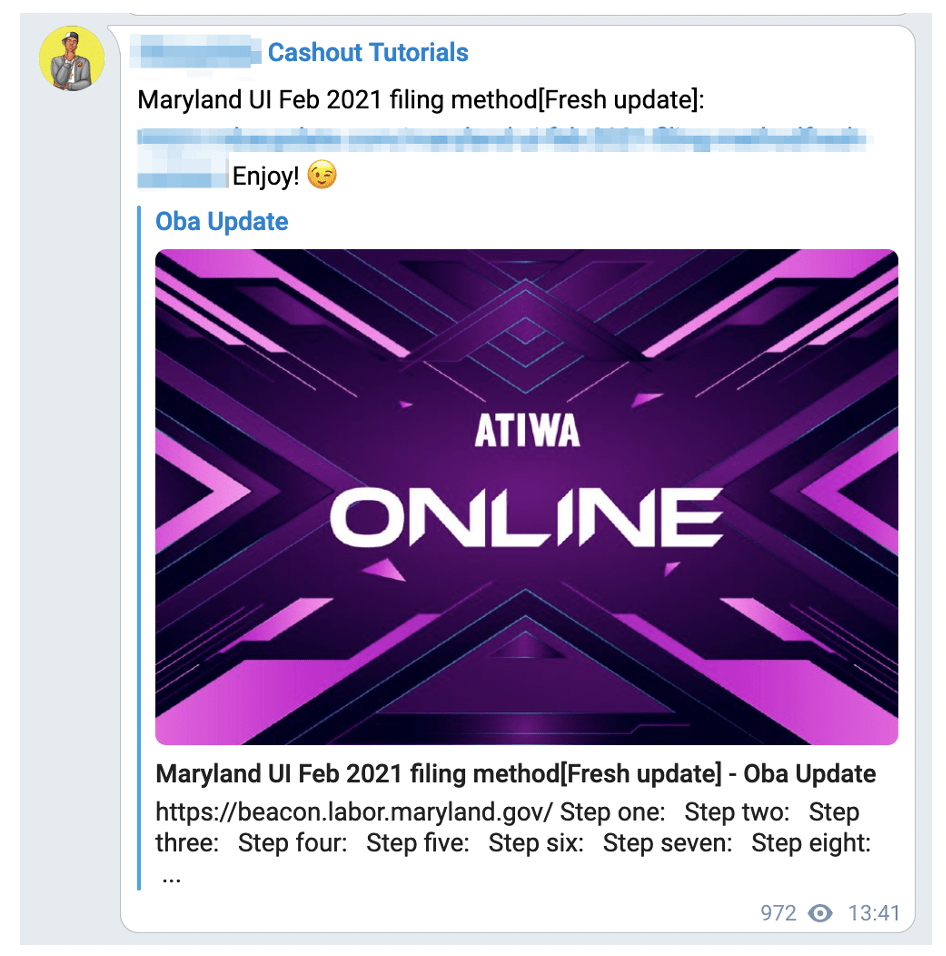
Figure 4: Step by step guide to fraudulently file for benefits in Maryland (Source – Twitter)
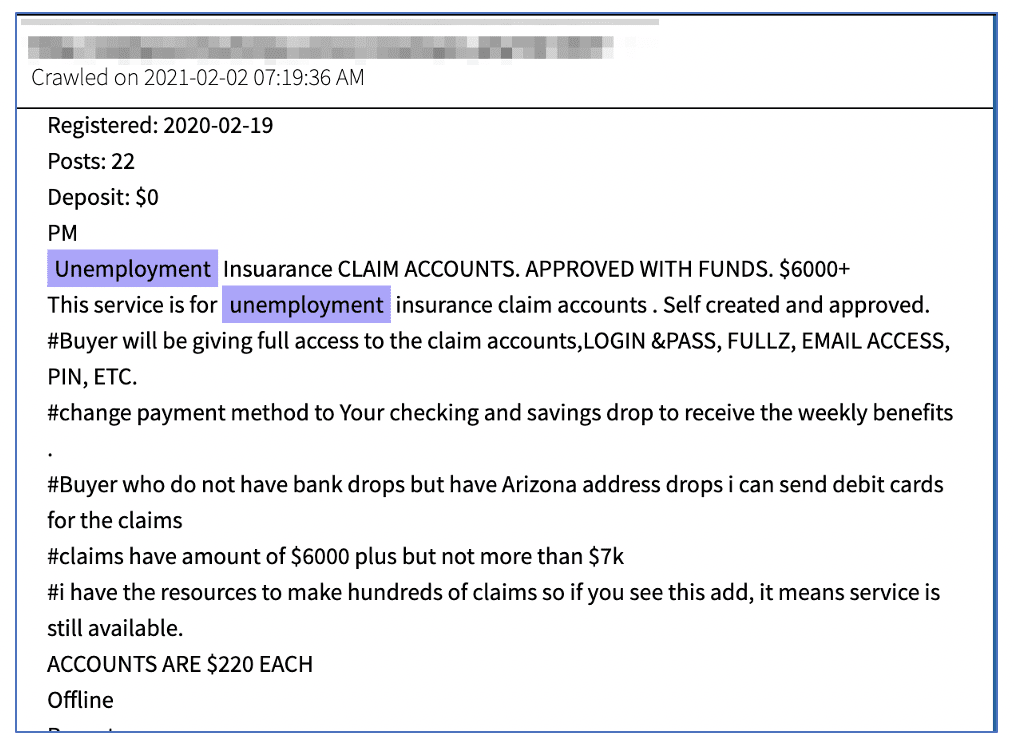
Figure 5: Advertisement on darknet forum for unemployment insurance claim services (Source – DarkOwl Vision)
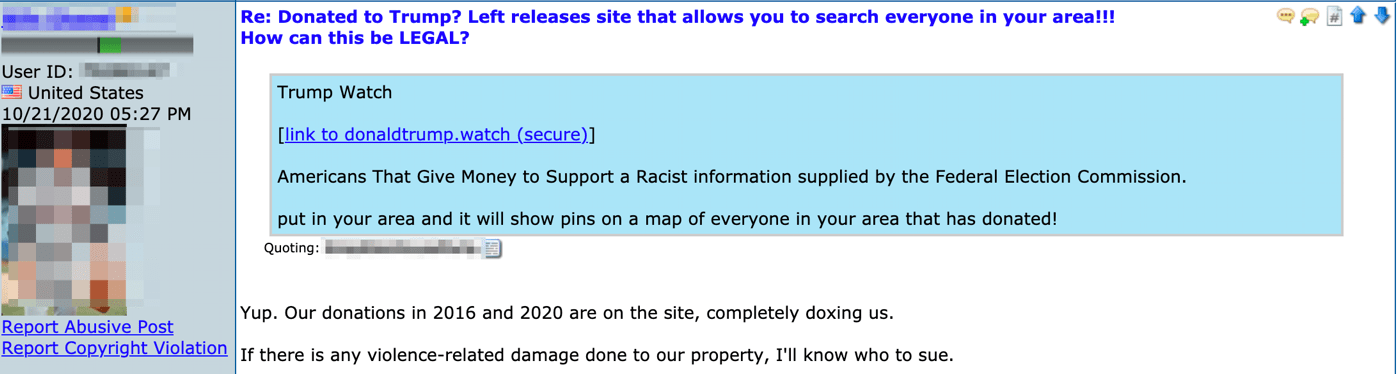
Telegram and Social Media are playing a large part in the spread of this type of fraud
While the fraud community continues to thrive on Tor, many threat actors are active on chat platforms such as Telegram as well. Many popular fraud channels and supergroups contain users selling the latest sauce and new exploitation methods, including large Telegram communities with upwards of 100,000 members.
Fraudsters are also increasingly utilizing social media platforms like YouTube and Instagram. where they share videos detailing a variety of fraud related guides and topics. Many of these posts relay methods by which one could commit fraud and take a variety of formats, including:
a) personally narrating the steps in a video – which often entails revealing their voice,
b) sharing a video of a method written out in text with suggestions to ‘pause the video and read’
c) demonstrating the technique via captured video of their computer screen while candidly committing the fraud.
As can be seen in the YouTube video included above, these content providers often successfully navigate possible YouTube take-downs by stating the video is “for educational purposes only.”
Unemployment fraud methods: How criminals are accessing and exploiting state unemployment systems
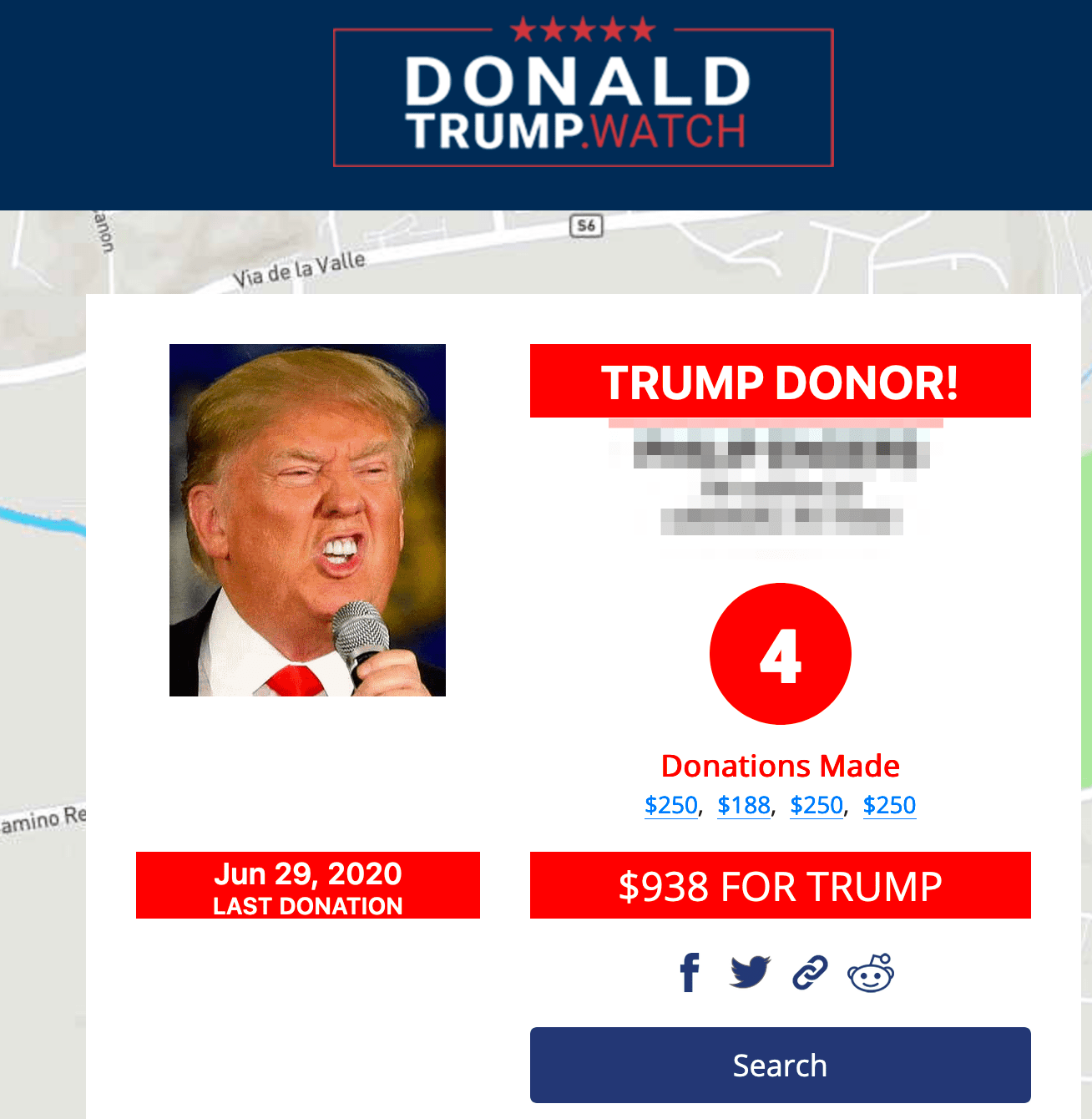
Hijacking the account of existing claimants using compromised commercial authentication data such as email addresses and passwords
Many fraudsters exploit individuals who have already submitted a claim, but this method may often require access to the email address associated with the unemployment claimant’s account for successfully changing the password and personal information for the claimant account. Many PEUC claimants register for their unemployment benefits then do not regularly visit the web portal to access their account.
Claimant victims might be tipped that their account has been compromised if they receive a password change notification from the system via email (for the states with such a system) but even those noticed may be overlooked. Once the criminal successfully gains access to the account, then they will quickly change the name and mailing address associated with the account along with the bank information where the existing claims are being paid.
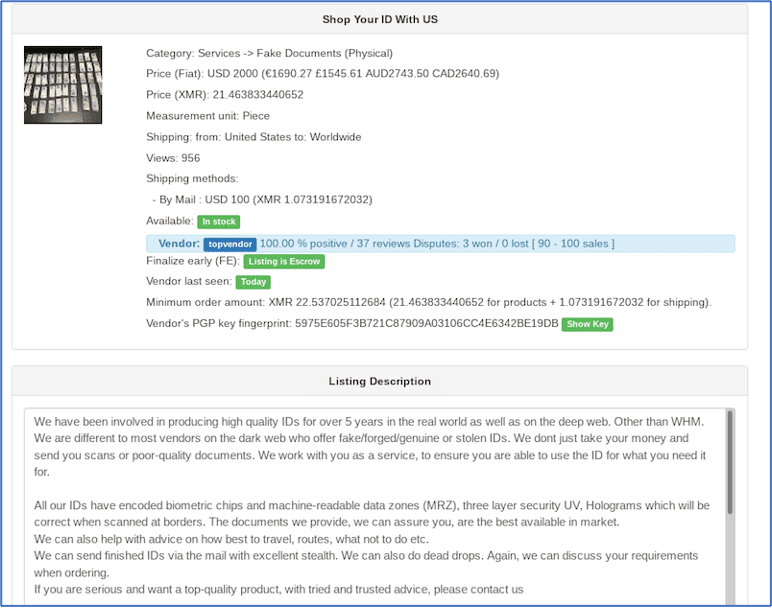
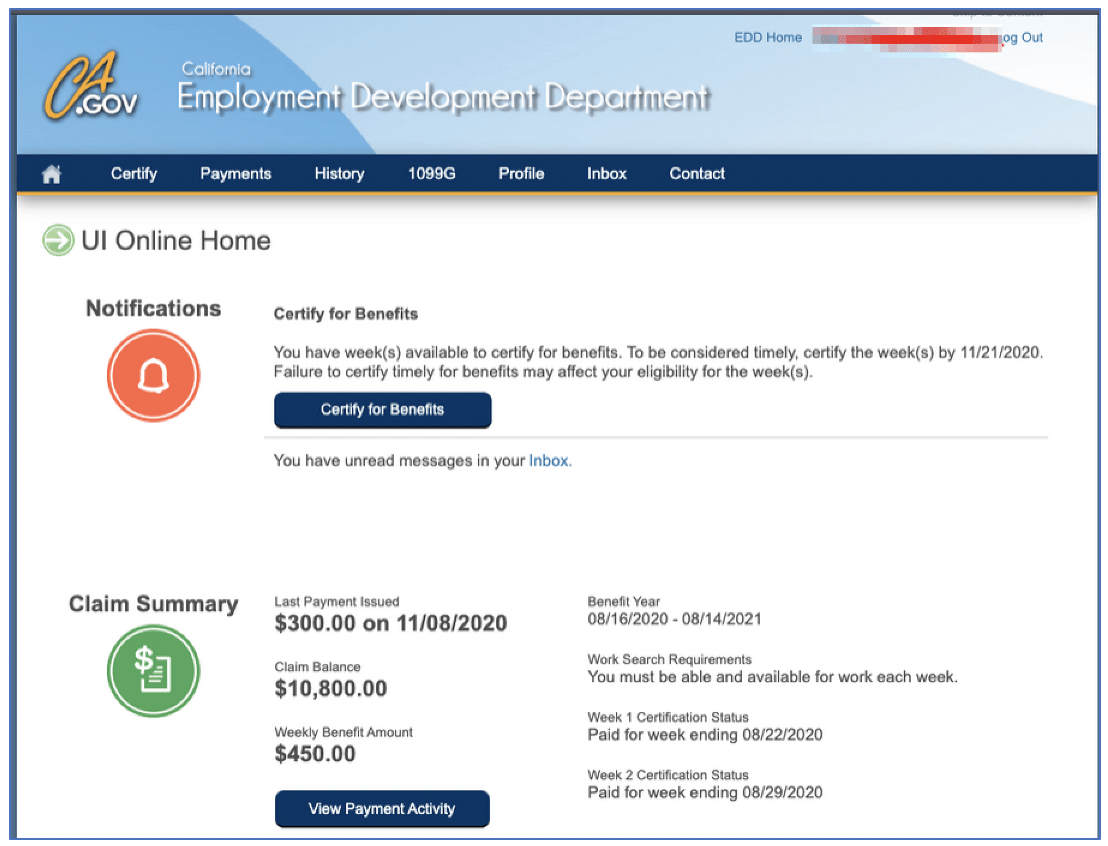
Figure 6: Screenshot provided as proof from fraudster claiming they had access to California’s EDD claimant accounts with outstanding balance for purchase.
Some criminals will foolishly attempt to use the exploited claimant account to extend benefits or submit new claims using the fraudulently information without the victim’s knowledge. This method often triggers most states fraud activity flags, which forces the account and payments into a hold state until the victim (or a fraudster) can verify their information and activity by calling the unemployment office directly.
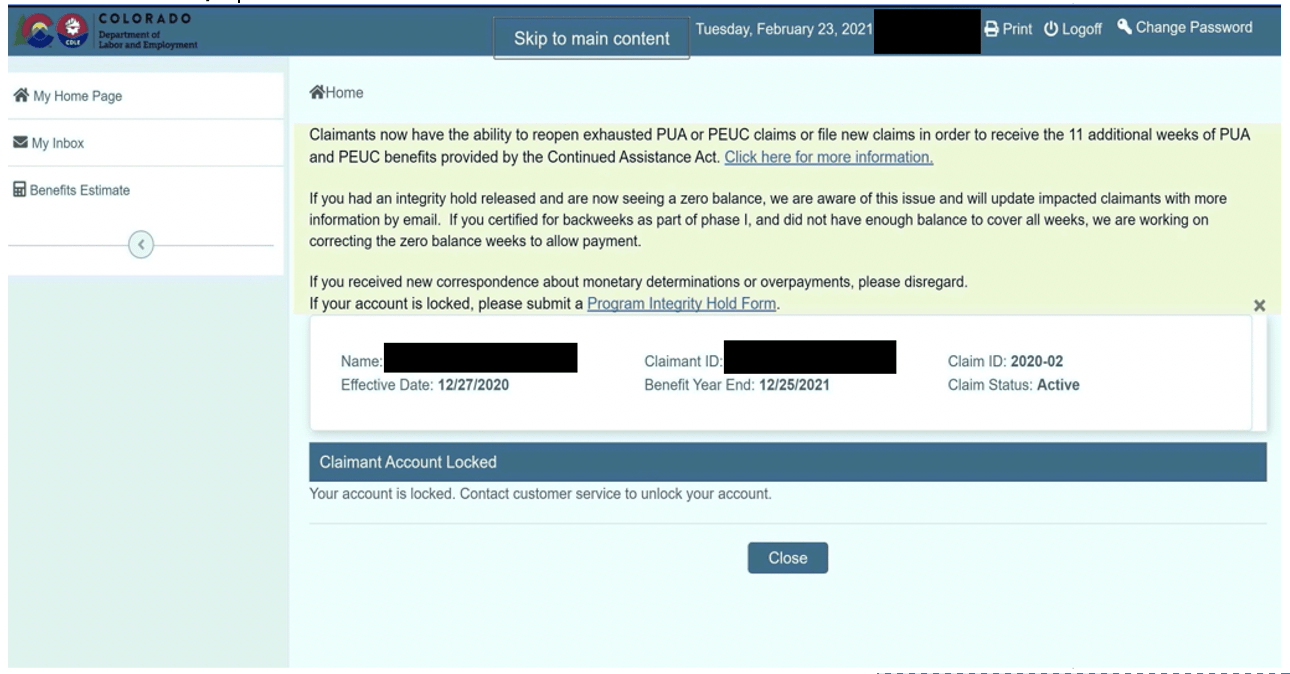
Figure 7: Screenshot from Colorado Unemployment Benefits Website with Account Locked
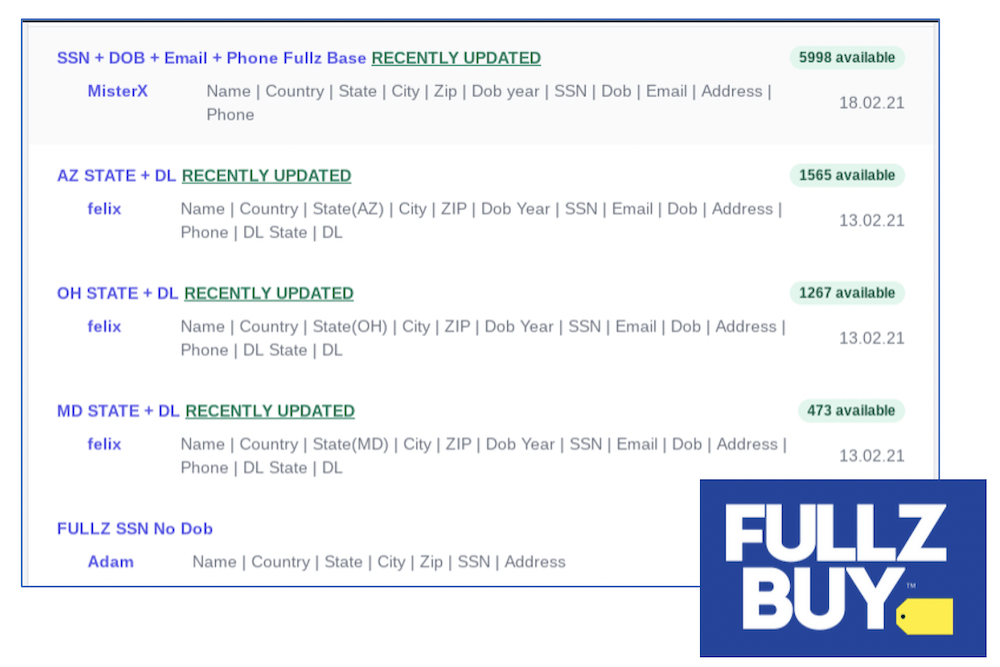
Initiating new unemployment benefit claims using compromised fullz data of persons gainfully employed purchased from the deep web and darknet
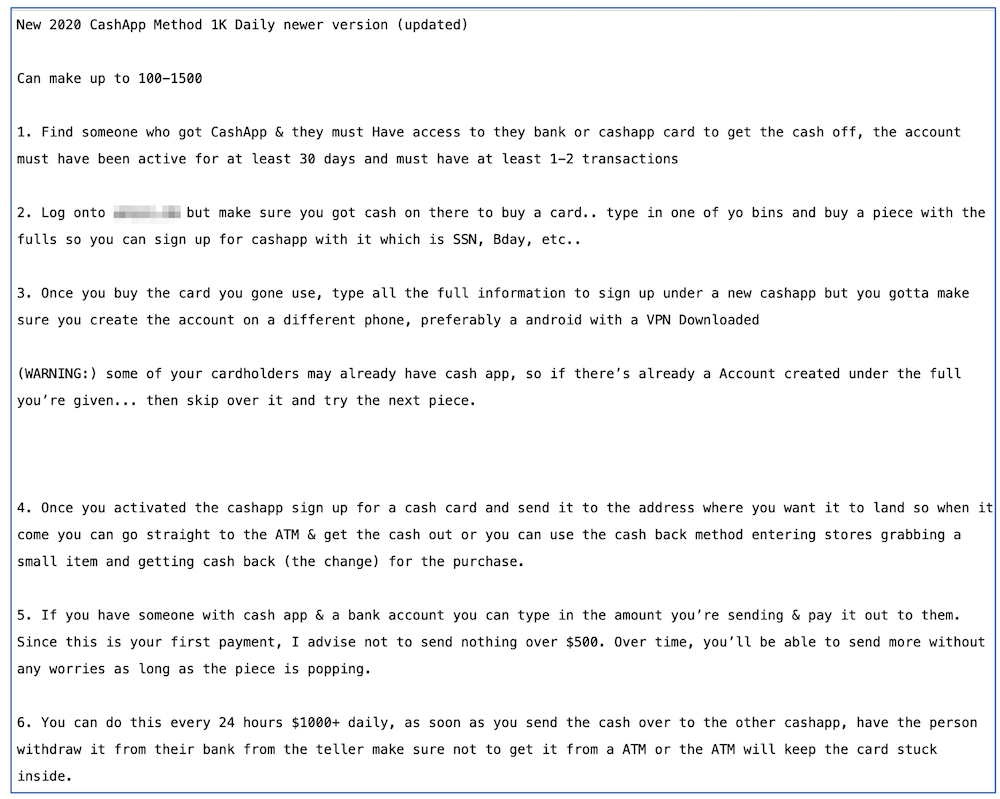
Initiating new claims using fullz data is the most frequently mentioned method of committing unemployment fraud. In the latest tutorials fraudsters have shared on social media, the cybercriminals are very specific in their method, such as selecting fullz from key states that have the highest probability of paying the benefit.
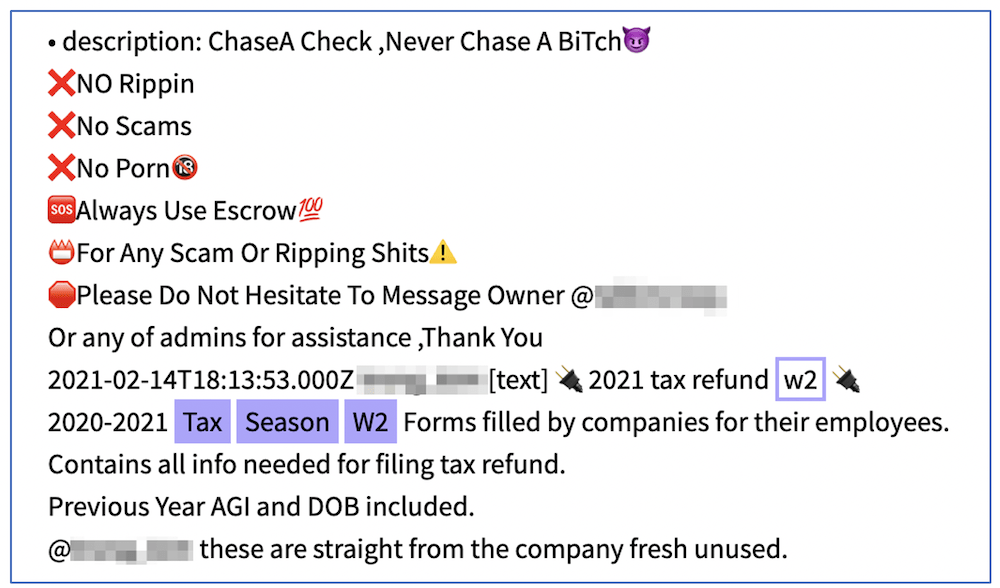
Other advanced fraudsters leverage social engineering to research additional data on person behind the fullz they are intending to use like extracting their employer information (via targeted LinkedIn search) in order to append falsified historical w2 forms in attempts to validate the account’s legitimacy. Many victims are only discovering their information was compromised upon receiving a 1099-G tax form in their physical mailbox in January for taxes owed on benefit compensation they never received.
Initiating new unemployment benefits claims using deceased fullz data purchased from the darknet and deep web
Many family and friends of the deceased do not monitor the financial status of their departed loved one, even often forgetting to cancel the credit cards for the deceased. With the fullz data of the deceased, this is usually enough to initiate a new unemployment benefit claim registered to bank account controlled by the fraudster and start receiving the $600 per week within days of the registration completion.
A U.S. Department of Labor report from the Assistant Inspector General in late February reported that over 91,000 social security numbers of deceased persons accounted for $58.7 million USD in unemployment insurance claims in 2020.
Compromising the state unemployment system via blackhat ‘hacking’ techniques or exploiting vulnerabilities of the benefit system and modifying claimant account information in the system database
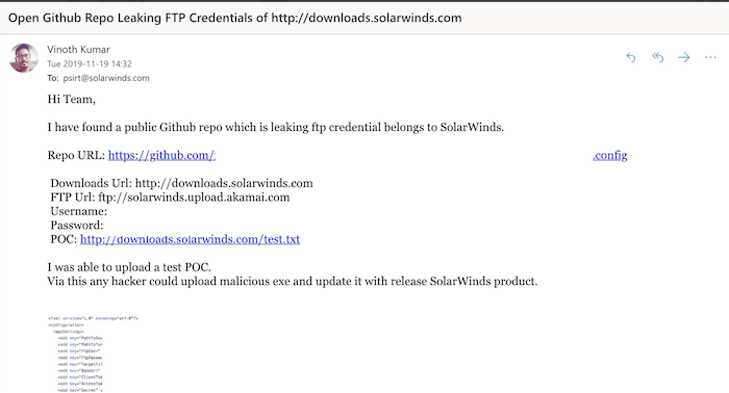
DarkOwl has observed criminal sources alluding to this method in chatter on the darknet in recent months. In July 2019, Maryland’s Department of Labor reported cybercriminals breached their agency’s unemployment database resulting in the potential compromise of over 78,000 claimant’s personal information including full names, social security numbers, dates of birth, and city or county of residence.
Earlier this year, Washington state reported that in December the State Auditor discovered a vulnerability in its unemployment benefit system computer file-transfer service used by the auditor’s office that allowed unknown “persons” to access to data from over a million residents of Washington that submitted claims in 2020. The exposed information included claimant’s social security numbers, driver’s license numbers, bank account numbers and employment information, essentially comprehensive fullz data a cybercriminal could leverage to steal someone’s identity.
The critical vulnerability discovered was later reported to be associated with a third-party service provider, specifically Accellion’s File Transfer Application (FTA). In recent weeks, FTA’s critical vulnerability has been assessed as the behind a string of cyber attacks against corporations, governments, and universities around the globe and linked to the CL0P ransomware gang from the darknet.
Most of the fraudsters are not bold enough to use their own personal accounts, but instead utilize online banking applications such as Venmo and Bluevine. Others use prepaid debit cards like Netspend or an account owned by a trusted money mule to receive the unemployment funds.
Remediation is an ongoing, near-daily process
Many of the state systems are identifying weaknesses in their unemployment benefits systems and implementing more rigorous identity protection measures. Many states now require claimants submit an identity authorization form including photograph of the person and official identification such as a passport or driver’s license. With the Colorado Department of Labor & Employment such steps have not previously been required prior to and in the early phases of the pandemic, but in recent weeks Colorado mandated every claimant (active or on hold) verify their identity with their “Program Identity Hold” system with their partner ID.me to help mitigate fraudulent claim activity by evaluating 50 different potential triggers.
According to recent reporting, Colorado has experienced inordinate volumes of fraudulent claims with over 1 million claims flagged for fraud – about 90% of their PUA claims – resulting in $7 billion in potential fraud payouts.
Figure 8: Source – DarkOwl Vision
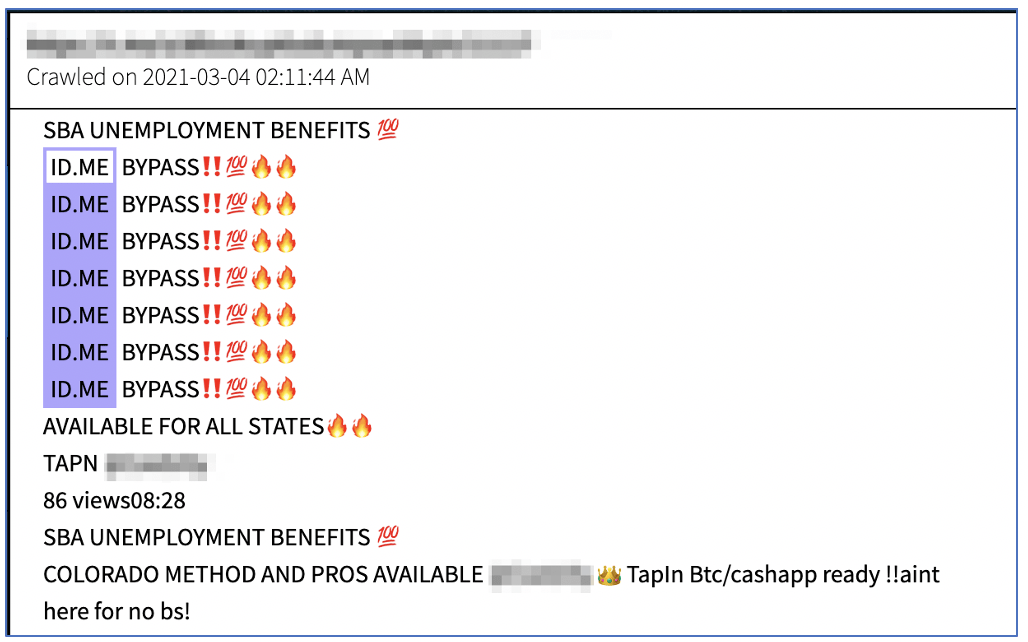
Unfortunately, DarkOwl analysts have witnessed fraudsters in Telegram conversations offer “ID.me” bypass methods for sale, demonstrating how the cyber threat continues to evolve in a continuous cat and mouse game. This offer was shared in a popular fraud supergroup as recently as early March, 2021.
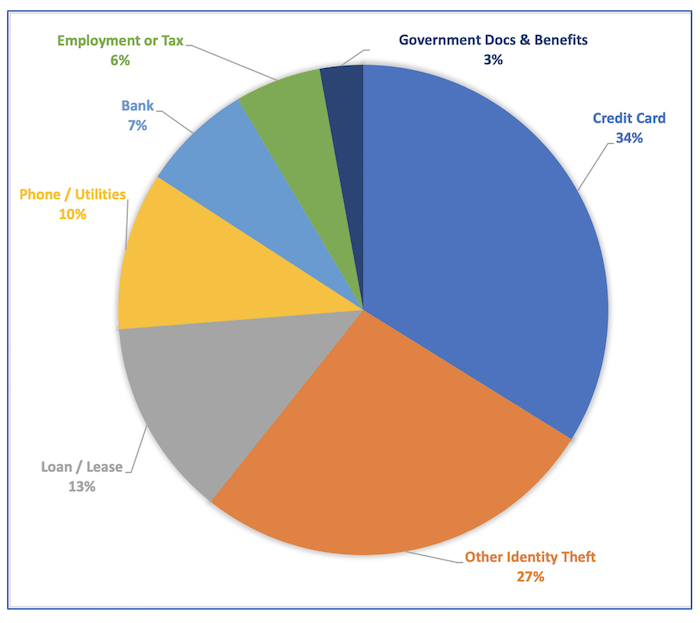
DarkOwl has also observed some recent fraudsters suggest they have “fullz with id” meaning they have a photograph of the victim’s driver’s license to potentially satiate identity authorization requirements. This demonstrates that driver’s license information alone is insufficient for identity verification. It is reasonable to assume that even DMV drivers’ license database for some states could be compromised in the near future. California reported a data breach of their internal DMV data management system with 38 million database records of vehicle registration information stolen in early 2020.
Per the recent passing of the $1.9 trillion dollar stimulus package, the primary unemployment financial assistance programs are likely to continue well into 2021, with PUA and PEUC ending in early October 2021 and FPUC and MEUC continuing through early September, 2021. The continued money flow will inevitably mean continued fraud of the programs on the darknet, with new methods of committing these acts almost certain to emerge.


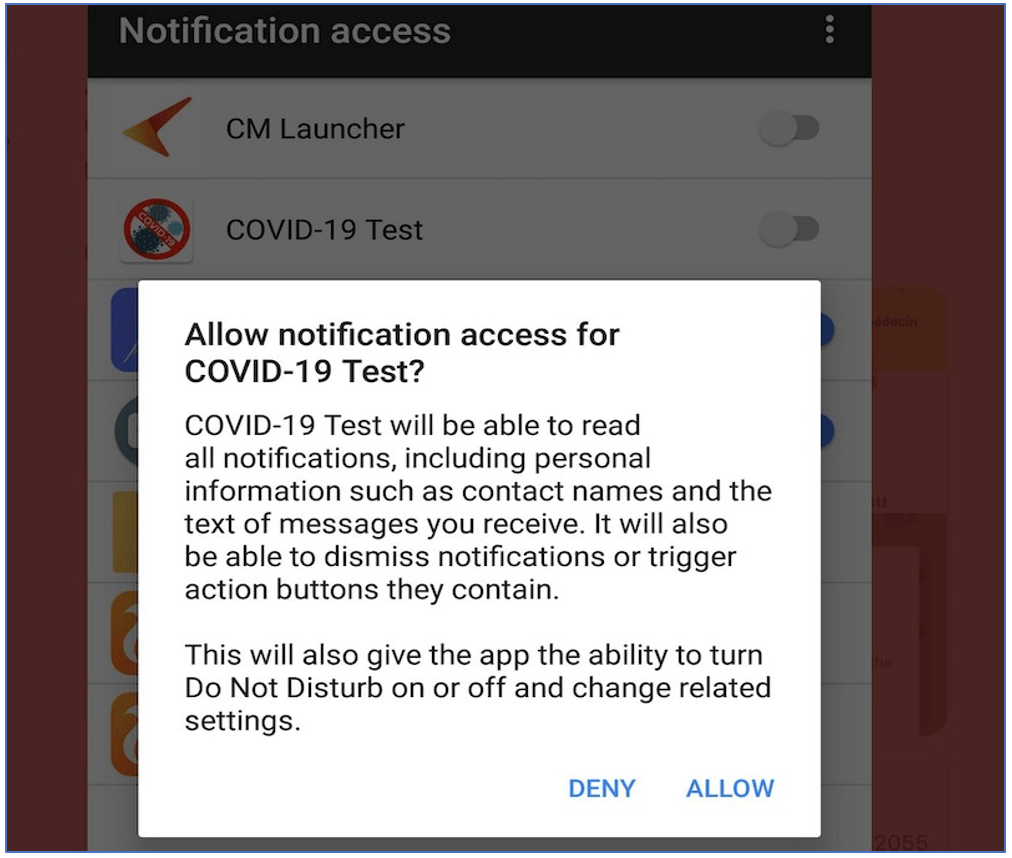

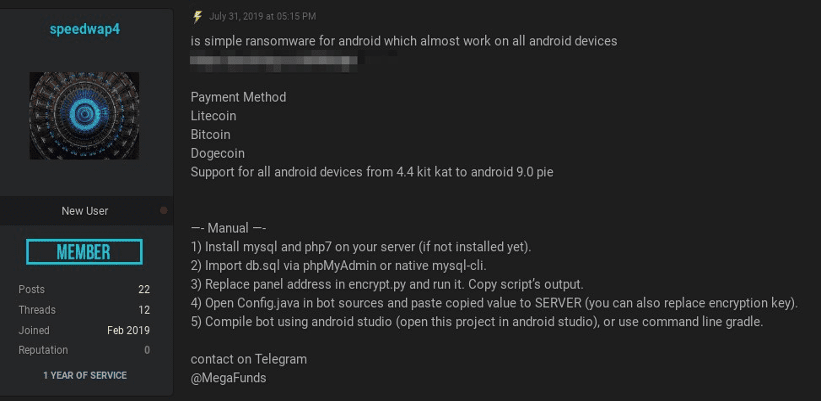
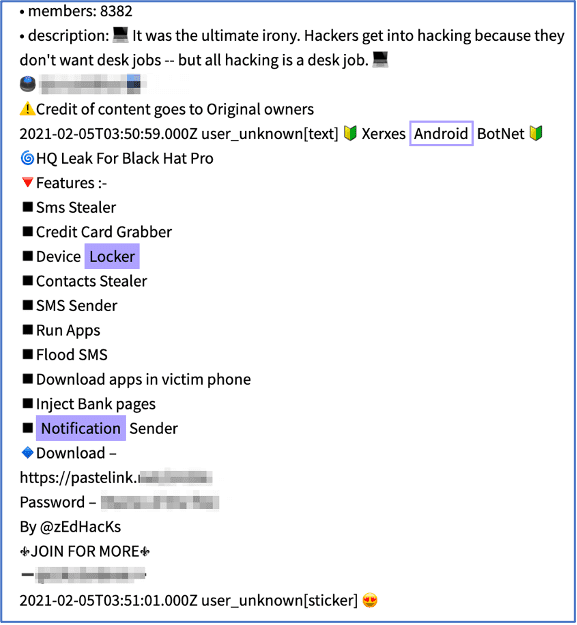
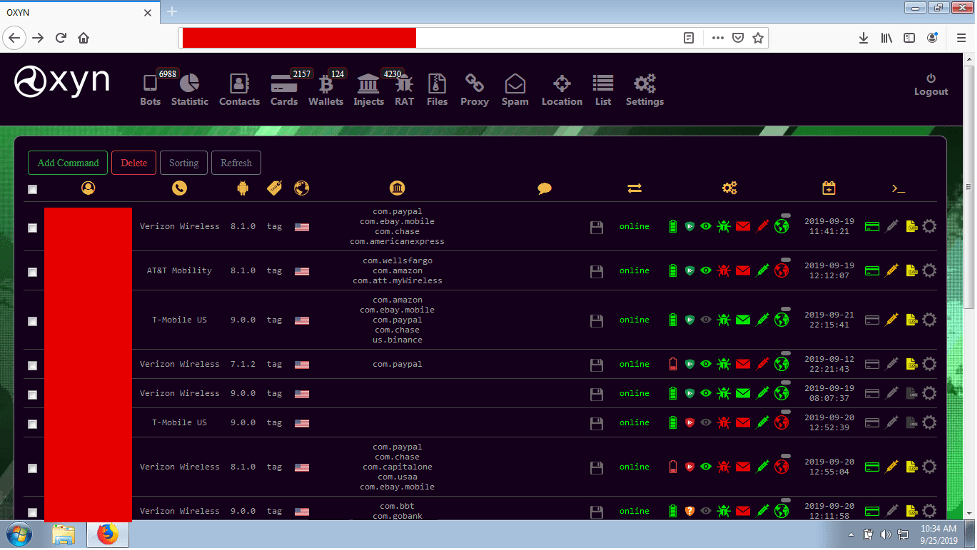
![Figure 11: “[Fud]APK Crypter” for sale (Source -DarkOwl Vision)](https://www.darkowl.com/wp-content/uploads/2021/12/mw11.jpg)