Gaming and the Darknet
July 08, 2024
In celebration of National Video Game Day on July 8th, this blog examines the intersection between gaming and darknet communities, notably instances of criminal activity targeting gamers or carried out by gamers themselves. This blog will highlight the prevalence of hacking in gaming communities—stolen accounts, pirated games, leaked data, etc.—as well as the infiltration of violent extremist ideologies into certain gaming communities. Our previous blog looking at the intersection of streaming, gaming, and the darknet can be found here.

Hacking: “Cracked” Accounts, Pirated Games, and Gaming Leaks
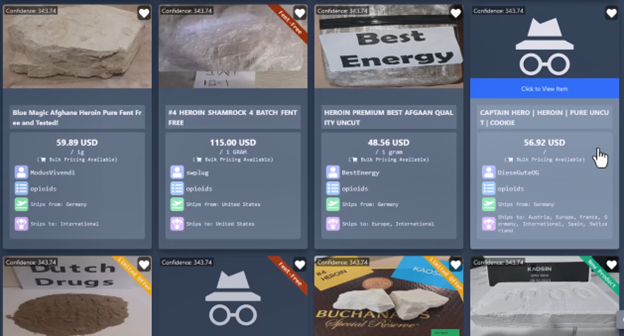
Open-source research reveals an extensive game-hacking community on the deep and dark web. The community consists of individuals on forums, channels, servers, and marketplaces that target gamers and gaming software to gain unauthorized access to systems and accounts. The targets of these hacking efforts most often include user accounts on a variety of online games, notably League of Legends, Minecraft, Fortnite, and Roblox. Hackers may “crack” accounts by utilizing usernames and passwords previously leaked in data breaches or by targeting young or naïve players through chat features. These “cracked” accounts are subsequently sold on the darknet, where their prices are determined by factors such as account level, collection of rare characters, amount of in-game currency, or inventory of in-game items (such as collectable character “skins”).

Figure 1: Genshin Impact account for sale; Source: DarkOwl Vision
Recent data points to an increase in compromised accounts over the past few years across several games. Figures released in 2024 revealed that Roblox, one of the most targeted online games, saw a 231% increase in hacked accounts in 2023 compared to 2021. In addition to the games themselves, gaming platforms such as Steam have also been increasingly targeted; these accounts are often even more appealing to hackers as they may be linked to credit cards and can thus allow for real-money theft as well as in-game currency theft.
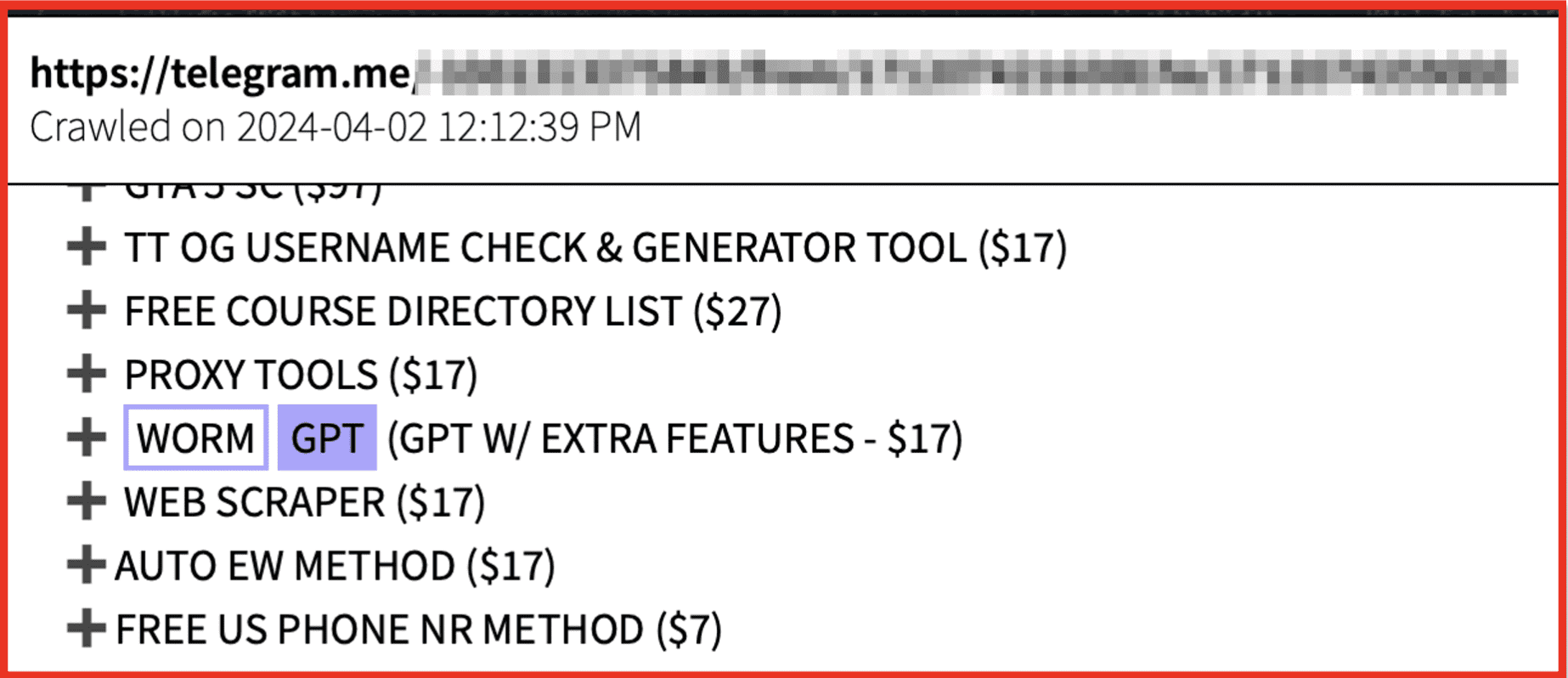
In addition to hacking users’ gaming accounts and selling them on the dark web, hackers also target the games themselves. “Cracked” or pirated games are frequently distributed by hackers on the darknet either for free or at a reduced cost. Not all games, however, are hacked with the intention of distributing pirated software; malicious actors also target game servers in the interest of leaking data. In June of 2023, for instance, hackers carried out a cyberattack against GSC Game World—the Ukrainian video game developer behind S.T.A.L.K.E.R 2: Heart of Chernobyl—and leaked builds from the game online. GSC Game World was also targeted by Russian hacktivists earlier that year, who threatened to release game data if their demands were not met by the developer. It’s worth noting that the malicious actors who engage in these leaks are not always hacktivists. Most recently, in June of 2024, Disney’s Confluence server was hacked by individuals believed to be fans of the massively multiplayer online game (MMO) Club Penguin. The hackers stole 415 MB of Club Penguin data from the server and the data was subsequently shared on 4chan.

Figure 2: Cracked Gaming Websites; Source: Dark Owl Vision
Unfortunately, game leaks are not always limited to game data. While the Club Penguin fans targeted data related to the game, they also stole and leaked internal, business-related Disney data. There have been other instances in which hackers have stolen and leaked not only the targeted company’s business data, but also its employees’ personal information. In 2023, the ransomware group “Rhysida” leaked 1.67 TB of data stolen from Insomniac Games, which—in addition to footage and images from the upcoming Wolverine game—also included employees’ personal information. Specifically, the leak included passport scans and HR files, thereby resulting in the doxing of more than 400 Insomniac Game employees.
Infiltration of Violent Groups into Games and Gaming Platforms
In addition to continued hacking efforts, online gaming communities have been increasingly targeted and infiltrated by violent groups and individuals seeking to harass, extort, radicalize, promote hate, and inspire acts of violence. These violent extremist groups have successfully co-opted gaming aesthetics and features—such as leaderboards and livestreams—in an effort to gain supporters. For instance, the white supremacist “Terrorgram” network on Telegram consistently posts “Saints Calendars” and “Saints Cards” meant to commemorate individuals—dubbed “saints”—who have carried out far-right attacks. The militant accelerationist group engages in the gamification of violence by releasing saint cards in the style of trading cards and including details such as “kill counts.” The more victims a terrorist claims in an attack, the more “points” they receive and the more likely they are to receive the “saint” title.
Moreover, as highlighted in a 2023 Global Network on Extremism & Technology (GNET) report, this gamification is further achieved by the repeated live streaming of mass shootings, which allows viewers to experience the attack from a first-person shooter (FPS) perspective often utilized in games. This visual choice—as seen with the 2019 Christchurch attacks—can facilitate viewers’ identification with the perpetrator while simultaneously emotionally distancing them from the victims. The sheer reach of livestreamed attacks (the 2022 Buffalo shooting was viewed “more than 600,000 times in less than 24 hours”), combined with their ability to generate a connection between perpetrator and viewer, threatens to radicalize more individuals and inspire similar attacks.
Apart from the adoption of gaming aesthetics and features, the gamification of violent extremism is made even more apparent by the actual creation of new or “modified” violent games by extremist groups and individuals. Open-source research on the deep and dark web reveals a slew of video games created since the early 2000s which allow players to target at-risk communities. Targeted groups most often include the Jewish and LGBTQ+ communities, with the 2002 anti-semitic video game Ethnic Cleansing being one of the notorious. Many of these games also recreate previous attacks—including the Christchurch shootings and the Pittsburgh synagogue shooting—in existing games like Roblox. Such modifications of existing games are referred to as “mods.” Other than white supremacist groups and individuals, Foreign Terrorist Organizations (FTOs) including ISIS and Hezbollah have also created extremist video games meant to radicalize and inspire. While it is believed that the vast majority of these games reach a self-selected audience with an existing interest in violent extremism, they may nonetheless play a key part in further radicalizing individuals and bringing them closer to carrying out attacks in the real world.

Figure 3: Antisemitic Video Game; Source: Dark Owl Vision
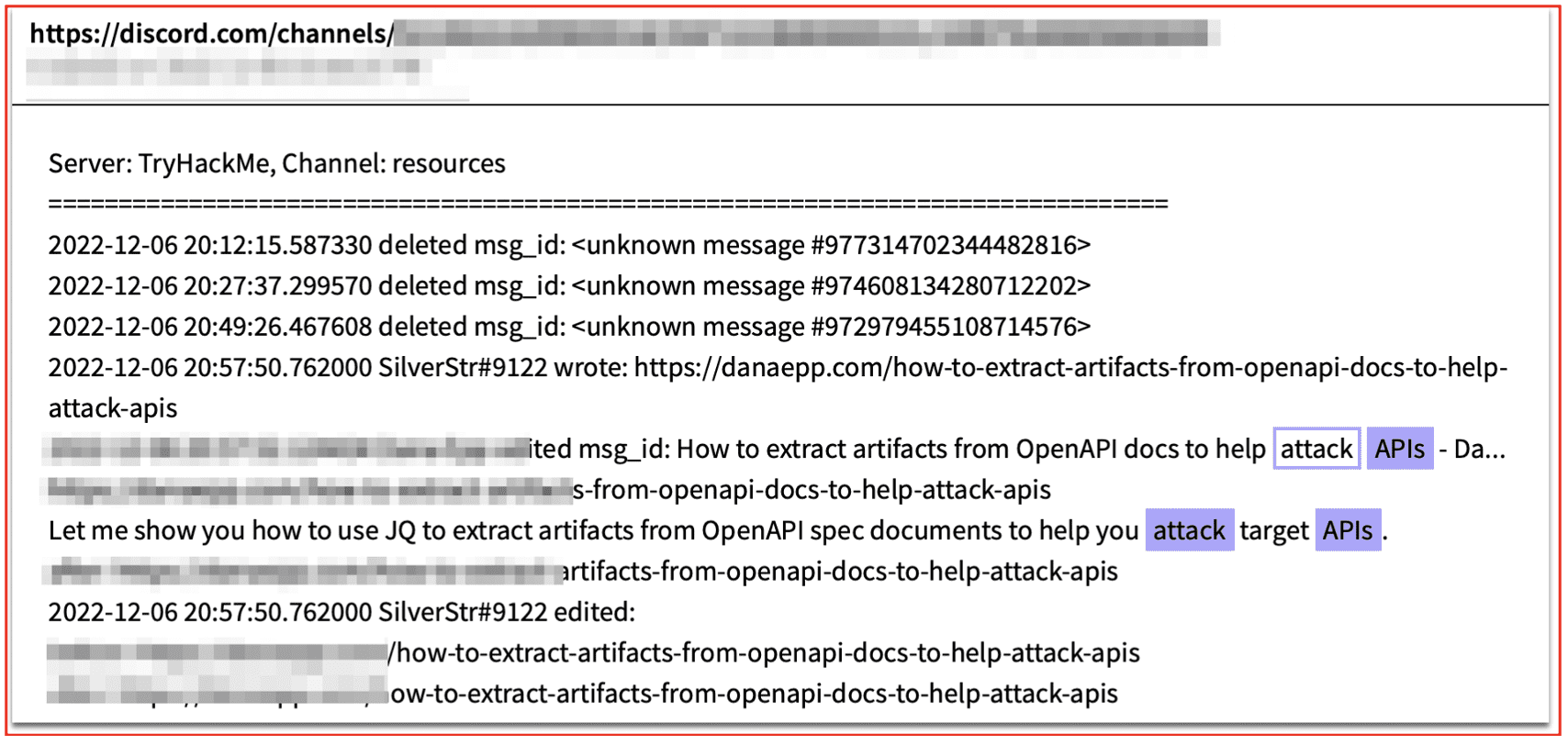
In addition to the creation of extremist video games, gaming platforms used by gamers to communicate have also been infiltrated by individuals seeking to identify targets for radicalization and exploitation. This targeting is particularly prevalent on the darknet adjacent platform Discord, where there have been numerous instances of children being groomed for violence and/or sexual exploitation. Among these violent groups is the notorious web of Discord servers originating from, or affiliated with, the group “764,” which has become increasingly active since late 2023. The 764 network overlaps with violent extremist and militant accelerationist movements—notably the Satanist, neo-Nazi group Order of the Nine Angles (O9A). In September of 2023, the Federal Bureau of Investigation released a Public Service Announcement warning of the 764 network’s ability to use “extortion and blackmail tactics, such as threatening to SWAT or DOX the minor victims […] [to] manipulate and extort minors.” Victims are often pressured to engage in self-harm and animal cruelty, share sexually explicit images or videos, and commit suicide. Members of affiliated Discord servers and Telegram channels have also been observed engaging in mass swatting and doxing efforts, most often targeting one another.
Conclusion
Open-source research reveals overlap between gaming communities and criminal activity on the deep and dark web. Instances of hacked gaming systems and accounts remain prevalent, with recent figures highlighting an increase in hacked gaming accounts over the past few years. Gaming platforms have proven to be desirable targets for hackers seeking to sell cracked accounts and engage in real-money theft. Hackers also continue to successfully carry out cyberattacks against video game developers, often releasing company data and employees’ personally identifying information (PII) in ensuing leaks. As such, it is recommended that organizations be on alert for any possible leaks affecting their data.
Research also points to a persistent infiltration of violent extremist ideologies into gaming platforms. Many gaming communities have become hotbeds for violent extremist groups and individuals, who utilize chat-enabled online spaces to promote violent narratives and radicalize users. Young gamers are particularly vulnerable to radicalization and recruitment efforts, as evidenced by numerous instances of teenagers being groomed for violence and sexual exploitation across multiple platforms. Continued reports of harmful and criminal activities carried out by individuals in the gaming space signals a need to address the rampant exploitation of gaming by criminals. It is critical to emphasize that these activities do not represent the entire gaming space: for many, gaming is a key source not only of enjoyment, but of community. In an interconnected world, online games have the ability to bring together individuals from around the world and foster a sense of belonging. So, rather than vilifying gaming communities, it is vital that steps are taken to address the infiltration of criminal activities, hate, and violence in order to combat the victimization of gamers.