[Presentation Transcription] Importance of Darknet Data in OSINT Investigations
July 09, 2024
The KeyNorth Group hosted DarkOwl’s Director of Intelligence and Collections for an exclusive community webinar in May. We are excited to share the transcription of the presentation below.
The internet is a vast realm that extends far beyond the surface web we commonly explore. Beneath the surface lies the darknet, a hidden network that poses significant challenges but also holds immense potential for open-source intelligence (OSINT) investigations. Join DarkOwl’s Director of Intelligence to learn how the darknet expands the scope of information available to researchers and analysts.
In this session, Erin covers how darknet data:
- Enhances OSINT investigations by unveiling hidden information
- Strengthens our ability to combat cybercrime and protect individuals and organizations
- Enhances threat intelligence and helps maintain a safer digital ecosystem
- Is utilized in identity theft, fraud, compromised accounts and other real-world examples
Lorena Rivera (KeyNorth Group): I’m pretty sure you all recognize DarkOwl as a worldwide provider of darknet data. Some of you know they’re working, providing data for government agencies as well. So today we are really happy to have Erin, Director of Intelligence and Collections at DarkOwl. Erin has more than 10 years of experience working in intelligence and conducting closed-source and open-source investigations. So, without further ado, please join me in welcoming Erin.
Erin (DarkOwl): Thank you. And so, thank you everybody for joining today. I really appreciate you taking time out of your day to learn a little bit more about the dark web. What I’m gonna cover in the session today is a bit of the background on of what is the dark web? And why is it important? And then I’m gonna go through some use cases and real world examples.
As Lorena said, if anyone has any questions throughout, please add them in the chat and I will be more than happy to answer them as I go along.
I’m the Director of Collections and Intelligence at DarkOwl, and I’ve been an intelligence analyst for over 12 years. I worked for the UK Government before working for a number of other companies doing OSINT investigations.
Just to give you a bit of background before we dive into the dark web information, I just wanted to give you a little bit of information about DarkOwl. We are a dark web company and our primary goal is to collect as much darknet data as possible that is relevant to use cases of criminal activity and make that available to individuals through our Vision platform and our APIs. We’ve been around since 2012 and pioneered that darknet collection, so we have a lot of historical data as well as the most recent data that’s available and you can view that through our Vision platform and also through APIs and datafeeds. If anyone would like to know more about DarkOwl again, please add it into the chat and we’d be more than happy to talk you through that.
Jumping into the main event of what we’re talking about, let’s start with what is the darknet and how is that different to the surface web and other things that we’re able to to view? So, no OSINT presentation is complete, I feel, without showing some kind of an iceberg. I feel like everyone does that these days, but it really does demonstrate the different levels of the Internet and the different areas that we can kind of examine.

The surfacenet is websites that we use on a daily basis, they’re indexed by search engines, and you know you can go to Google, you can go to Bing and search for something, and that information will appear for you. So, it’s very easy to access. And the deep net is content that is accessed via a login or behind some kind of wall. So, its credential protected or it’s a database, so it’s not commonly indexed by those search engines. And then the darknet is a hidden service where you need to download software in order to be able to access it and it’s not indexed. It’s a lot more difficult to find URLs. URLs are a random string of characters and numbers, and therefore it’s not an intuitive process to search through it. Although we are a darknet company and that is our primary focus, we do actually collect data from across these three areas and as long as they are relevant in terms of treat actors are accessing them or nefarious activity is taking place.
So with that said, let’s delve into the dark web and what can be found there. So, this gives you a brief history.

And so, the dark web has been around since the early 2000s. It was actually created as a project by the US government in order to share information in an anonymous and secure fashion, but it was released to the public in around 2006 through the TOR project. The TOR project is a not-for-profit organization that manages Tor or the Onion router. It manages the software, and it creates a tunnel for individuals and to access and remain as unknown as possible. The way tool works is it goes through three relays and so you will start on your computer. You’ll type in a message, it will go through three different relays and come out at where you’re attempting to go. So it makes it a lot more difficult to track that traffic.
It is worth noting, and I’d like to point out, that although there is a lot of nefarious activity on the dark web, there are also legitimate uses for it. A lot of individuals that are in countries where their internet access is restricted and the types of sources they’re able to access is restricted, can view some of those things through the dark web. You know, there are news organizations and social media platforms that do have websites on the dark web that people can access, but it is also, as you know, we all know and why we’re here, a place where nefarious activity does take place.
And in the mid 2000s, that was when we started to see marketplaces emerging with cryptocurrency being created that gave people a more anonymous way to transact on the dark web. We’ve started to see data breaches and information being shared there and we can see certain groups not just kind of criminal activity but extremist activity and terrorism activity taking place on there as well.
But law enforcement have started to crack down on this and have been able to and see some of the sights, starting with Silk Road and Alpha Bay. And you know, as recently as two weeks ago, BreachForums were seized. So there’s a lot of information that’s gone. This only shows up to 2020, but obviously you know it’s still a very active place.
So, what can actually be found there? So, I kind of already mentioned, information and social media is available on the dark web, but the things that we’re probably more familiar with people talking about and more relevant to us are things like dark web marketplaces, where drugs, counterfeit goods, data is freely available and for sale. We have forums and where threat actors are discussing and talking about things and usually also selling goods. We see a lot of data leaks and ransomware sites on the dark web, so ransomware walls of shame, we should say, and are available in dark web. And then there’s also a lot of cryptocurrency activity on there. So, things like mixers and tumblers, which help users to obfuscate and their cryptocurrency more so, although there are still ways that you are able to kind of follow that money.
So, to show you some examples of what this actually looks like here are some things that I found on the dark web just kind of give you a flavor of what it looks like.

You can see, even though it’s not indexed and it’s more difficult to find, there are websites that are set up like any other websites that you would see on the surface web. They have reviews, they have payment systems, they have login information and captchas, etcetera. So, here you can see we’ve got a site that’s selling human organs, which I like to think is not real, but it definitely exists out there. We have people selling drugs. We can see people selling and IDs and counterfeit documents as well as selling cash payments and things like that and then going on to the next one.

These are what some of the marketplace homepages look like. So, you see a lot of advertisements. You can see the different types of cryptocurrency Minero, Bitcoin, Dutch, White Coin that are being affected. They do accept a wide range of cryptocurrencies, although Bitcoin is still the dominant currency of choice. You can see credit cards, counterfeit money, and data being shared on all of these sites. So, there’s a huge amount of information out there and it is kind of set up in a way that people can go in and select what they want. You can see the different categories there and how many listings there are for those different categories, and then you can go in and purchase that information and they do tend to ship worldwide.
As well as those specific dark web sites and forums that you get on TOR and Onion, we do also look at dark web adjacent sites. They are the sites we refer to and which are not on the dark web themselves, but they are still being used by the same individuals and in the same nefarious ways. So, looking at things like messaging apps and Telegram is obviously huge at the moment, but we also see things like ICQ, jabber, matrix, element, rocket chat where we’re seeing extremist activity being discussed and criminal networks are operating in announcing activities. That’s also true of some gaming app. So, while there’s a legitimate purpose for that and you know we do see information being shared on things like Discord and Twitch. Obviously, famously, government U.S. was leaked on Discord, so they do try to clamp down on that activity since that happened.
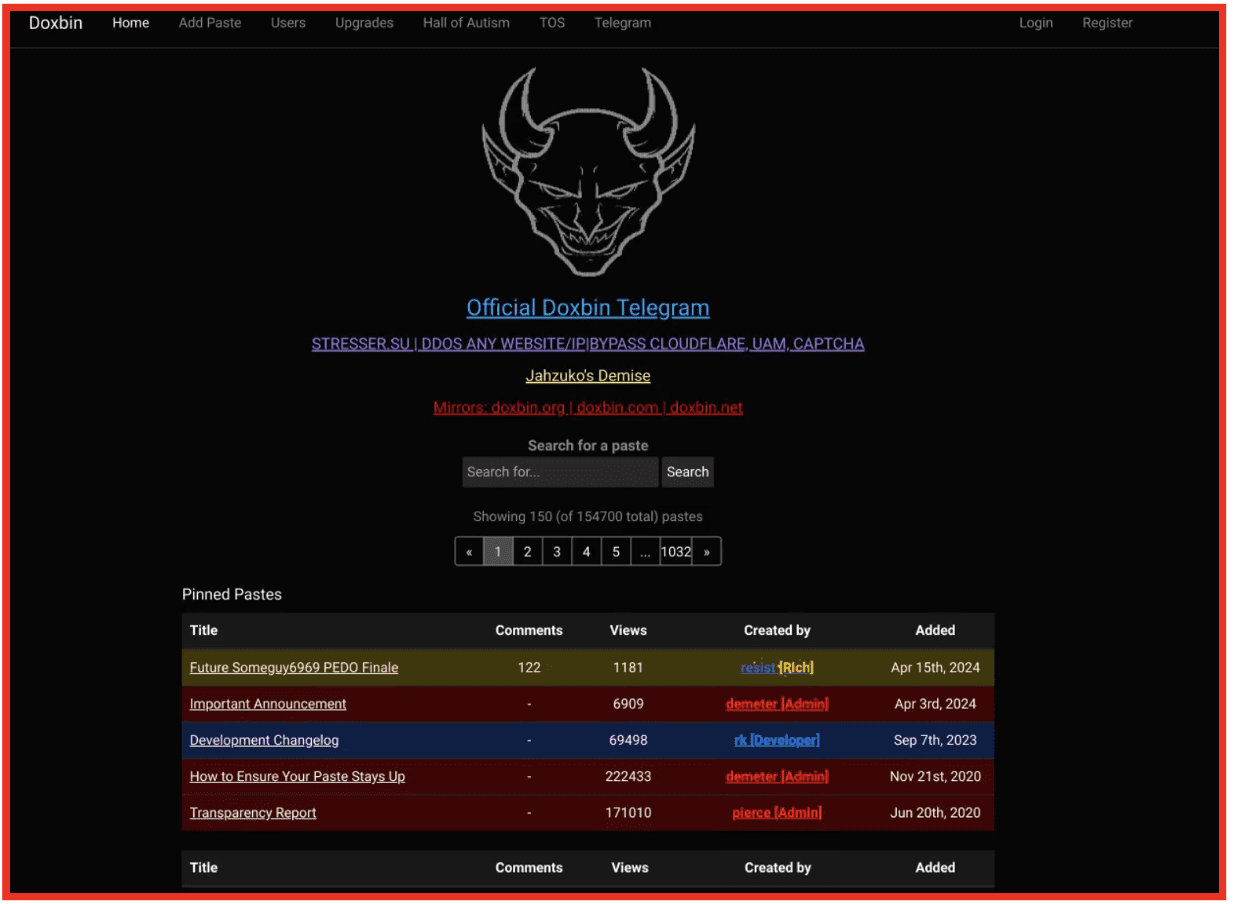
And then also a lot of threat actors will use the surface web to have their marketplaces, their vendor shops and their forums. And they feel that if they are using bulletproof hosting that it can’t be taken down, and especially if they’re in non-extradition company countries, they often feel that they don’t need to use the dark web as that extra level of security. So we do see marketplaces, forums, vendor shops that appear on the surface web and things like Doxbin, and Paste bin, where information was shared as well. So we do collect from all of these different areas as well as from the dark web itself.
So just to kind of summarize that, there’s a lot of data that comes from the darknet and so you know there’s a lot of raw data, and there’s a lot of new things that we’re seeing emerge. So PII (personal identifiable information), I think is the main one that people are concerned about. Data leaks are being sold on a daily basis. They do include some very sensitive information in them as well, as you know some more generic things such as emails. You can get banking and transaction information as well as credit card data. We do see a lot of financial apps being transferred as well. So, accounts such as Cash app and Zelle and others are being transacted all the time. Corporate data, this is especially true with ransomware data,and where they’re basically just take everything they can from a victim and make that available.
We also see a lot of threat actors selling malware and toolkits, and then obviously ransomware as a service as well as selling those tools, we also see a lot of tutorials and that individuals on how to conduct attacks and you know the more traditional kind of script kiddies where they’re able to purchase these tools and instructions on how to use them and use them very successfully. Especially when those credentials are out there and that’s the easiest way for cybercriminal to get into a network or get into where they want is to have credentials rather than having to kind of use and exploit to get in there.
But we are also seeing more cyberattacks happening, DNS hijacking, cyber espionage. Although it’s harder to identify and as hacked to this, groups and others are kind of getting more into that realm and the line I would say is blurring for some countries between stay actors and criminal actors and that from the same area we are seeing some overlaps with that. And of course, there’s always DDoS attacks and cyber threats.
So, just to give you an idea of the landscape and how it works, these are different areas that we collect from everything that is highlighted in red are the areas where we focus.

But there are other areas out there, so I’ve mentioned Tor primarily, and that’s the one where we see most activity occurring. There are other Darknet software providers out there. So, we do also collect from I2P and ZeroNet. We have heard from some of our law enforcement partners, ZeroNet is actually, and I2P are increasingly being used for CSAM material, but TOR is still primarily used by most threat actors. But Freenet, Loki, Unigrid, Mysterium they are also available. We don’t see the same level of activity happening on those and the same chatter about them. And so, we don’t kind of direct our resources there, but should that change, we would increase our coverage of those areas.
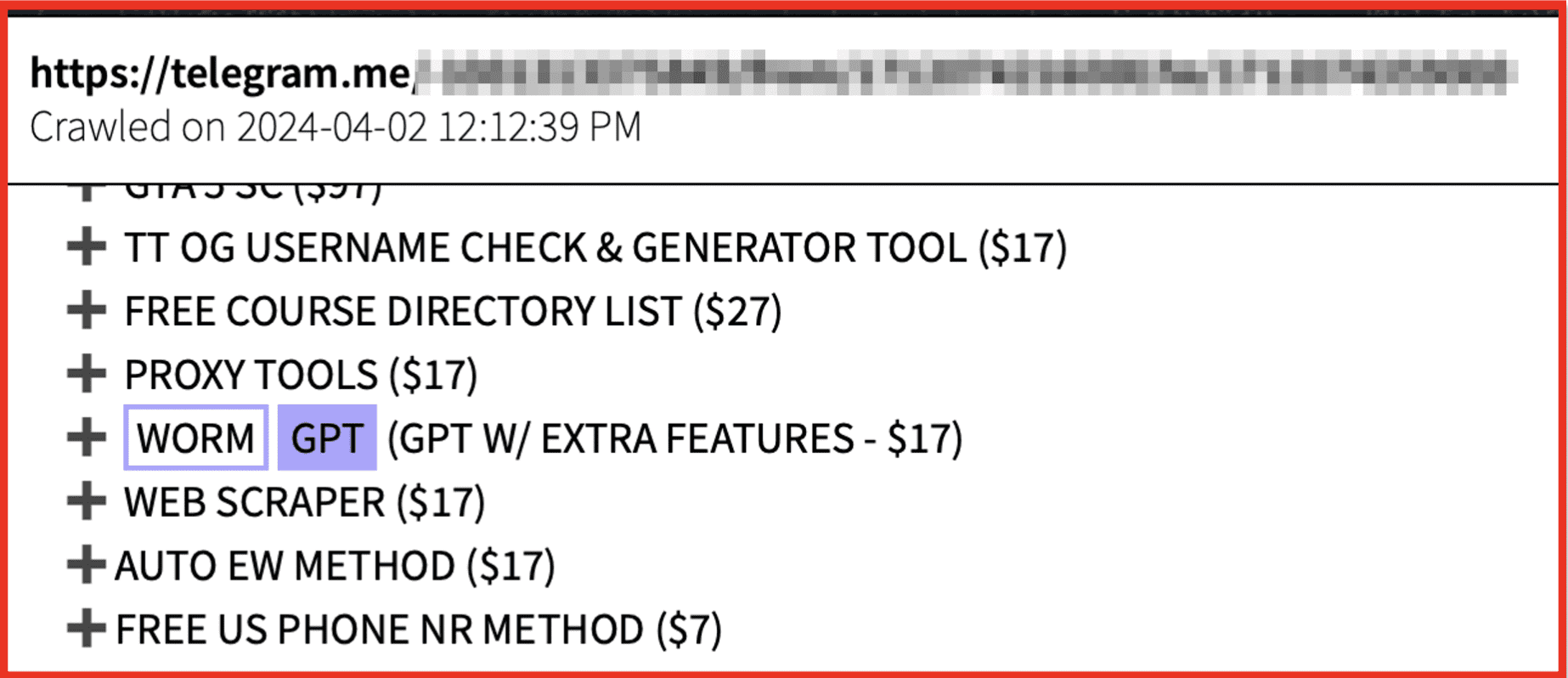
I’ve also mentioned the high-risk surface web areas. So ,things like paste-sites and discussion boards and there are a lot of extremist activities and protest groups and that are using violent means rather than peaceful protests that are discussing information on discussion boards. So, we want to make sure that we’ve got coverage of those and then the deep web also. We do avoid social media and there are a lot of other companies out there that do that and in such high volumes – we do try to target our collection to dark web and also messaging apps. Telegram is huge for us and we collect from almost 5000 channels. Those are curated to make sure that they’re relevant, and we do add new channels all of the time. But we are seeing a huge volume of actors using Telegram as a way of communicating. And I already mentioned BreachForums being seized a couple of weeks ago and as soon as that happened, you know, and interestingly, one of the Telegram channels was taken over as well. But we did see new Telegram channels popping up. That was how the treat actors were communicating. That was how the new Onion address for BreachForums were shared, and so it’s definitely very much intertwined. We will see a lot of ransomware groups and marketplace vendors have a Telegram ID on their dark web marketplaces, advertising that as a way to talk to them, as a way to do escrow payments and things like that.
Lorena: So you have this all these different sources. Where or how do you store all the data?
Erin: We store the data in the US, we use a AWS, so it’s all US based. We collect that information and host it with AWS.
So why is dark web data important? Hopefully you are already getting a sense of that, but one of the things I always say as analyst is different bits of data or different tools are one tool in the toolbox and you need to bring everything together to to be able to get a full picture. So, darknet data is definitely one element of that OSINT investigation that should be looked at. And corporations are being talked about, individuals are operating and discussing. You can get pattern of life information. You can get identifiers and also you can learn about what illicit activities are taking place. You know what the trends in terms of different malware or different attacks that are being talked about? Who are the primary targets? And it can really help law enforcement understand how groups are operating, and it can help corporations understand how they should protect themselves and given things that are taking place.
Being able to access those forums, those marketplaces, those communication channels and see how these threat actors are interacting, what they’re discussing and what they’re doing and also being able to target that illicit activity and obtain that information as evidence of of what they are conducting. So, it really does provide insight into cyber attacks, data breaches and drug trafficking, human trafficking. You know, there are a wide range of activities that are taking place on the darknet, and if that information isn’t being viewed, you’re not seeing the whole picture, I would say in most cases.
So, with that said, I wanted to jump into a couple of use cases and walk you through how you can use dark web data. So, we’re starting here with a LockBit affiliate, so LockBit is probably one of the most active groups out there. They were subject to law enforcement activity, and earlier this year, unfortunately, they did come back fairly quickly and and created a new kind of leak site, albeit a little bit more rudimentary than the one that they previously had. And as a side note, I loved what law enforcement did to their leak, in terms of using how they just set it up to advertise.

But here we’re looking at one of the affiliates that was indicted and added to the sanctions list in the US. So, it was a threat actor known as BASSTERLORD and searching on that username, we are able to see because we have that historic collection and that he appears over 8000 times in our data. So, a very active user across and multiple sites, but particularly Exploit and XSS forum on the dark web which are Russian language forums, a lot of them are invite only and so you need to have quite of the access to be able to get into those and see the information that’s being discussed and we could see through those discussions and you can see an example in in Cyrillic on the right hand side of the screen discussions that he’s having with other threat actors discussing malware he’s created and the hacking operations that he has conducted. Looking at his real name and identity that was released in the sanctions. We were also able to identify that his name appeared in several leaks. So, we were able to see information about him and also identify through those leaks, some of the social media presence that he had. And as an aside, again, just because I think it’s interesting LockBit actually put out a message saying that they would give money to anyone that got a tattoo of LockBit and several people did that and posted it online and which is insane to me, but I thought I would share that it kind of gives you an idea of the communities and how they operate and also what they will do for money.

I’m sticking with LockBit and they’re filiates and the second use case. This was another individual. He was sanctioned and so again, you know, we can search on that email address and see that he appears in several leaks with his full name in Cyrillic and also his phone number. So, we’re also able to pull out user agents and things like that. So, obviously this is after the fact, he was also already identified by law enforcement, but hopefully you can see I’m trying to highlight that if you did have an email address or a phone number for a suspect being able to look at this leak data, which you know unfortunately has been stolen and shared and can be a really useful tool for law enforcement and for attribution in terms of identifying more information about an individual and obviously you’d need to validate that in other ways. A leak is only one source, and it’s only as good as you know the threat actor that’s stolen it in some cases, but it really can give you a lot of information about specific individuals based on selectors on monikers that you’re able to identify as part of your investigation.
I mentioned that cryptocurrency is the main way that people transact on the dark web, and I wanted to give you a little bit of information about how we can kind of use OSINT tools and the information that’s out there on the blockchain to look at a particular cryptocurrency address or site. This is an Onion site. I don’t think it’s surface web, called Kiwi Farms. It’s predominantly used by extremists who have fairly difficult opinions. I would say and they share those actively on the site. So, it’s a forum where individuals can share information.

So, on the left-hand side of the screen you can see our platform, Vision, where we’re able to search. You can search specifically by cryptocurrency addresses and so I searched to see where cryptocurrency addresses appeared, and then I also wanted to see what the site actually looked like. So, we do have a feature within the platform called Direct to Darknet, which you can click on, and it will show you if the site is live, what the live site actually looks like. This is what the forum looks like on the dark web. We can see that there was a cryptocurrency address that was shared on this page.
Next, I wanted to delve into that and look into it in a bit more detail. So, using an open-source investigations tool, I searched that cryptocurrency address and can see that someone had already tagged it as Kiwi farms. So, it’s actually donation address at the forum was asking for and in order to keep their site up and going. Using open-source, crowd sourced information, you could see that it’d been labeled as Kiwi Farms. We were able to verify that because it came from the site itself and you can see the total amount of cryptocurrency that they’ve if received and that most of that has just gone straight out of the account. What I found interesting in this; is I was trying to figure out where they cashed out these funds to see if you could identify who was operating the forum. There were several exchanges that were where they cashed out, so Binance, Kraken, but one of them Bovada this specific address had been listed as related to terrorist activity and so you would need to dig into that more. And again, it’s unvalidated information, but it can highlight that nexus between what is being referred to as terrorist activity and then an extremist forum. So again, really highlighting that nexus between dark web data and other OSINT information that you can use.
I felt like I would be remiss without mentioning the Israel Hamas conflict as that as something that has been very prevalent on the dark web, but primarily Telegram. Ever since the attacks in October last year, we’ve seen a lot of hacktivist activity and also a lot of data breaches that are being shared on Telegram. These are just some examples in terms of data that’s being leaked, defacement attacks that are being promoted, but also stolen information of probably high value targets within their countries that are being added on Telegram. You can see there at the bottom there’s also a Maltego graph, we’re seeing a lot of these activist groups operating together and we’re seeing them sharing different information and mentioning each other and crediting each other in the attacks that are happening. So, it really starts to build that kind of network and of activity and that link analysis of the threat actors out there and you know, they have the defacement where they put their username, so you can associate individuals to that particular group. So, they have websites as well and some of them are also active on social media and they’ll provide that information that’s Twitter accounts or Instagram account. It provides that nexus.

I think that the other thing that was interesting with this conflict and Telegram in particular is it was a way that information was being shared a lot quicker than by mainstream media. Obviously, that needs to be taken with a pinch of salt in terms of if it is true information or not, but it was certainly a way things were being shared and very early on in the conflict. Images were being shared online of Hamas coming through fences and gates and images of hostages, etcetera were being shown. So, it is a way that people are getting media. So not just looking at the threat active perspective, but also the disinformation and especially as we come into kind of an election year, it’s something I think to be aware of.

Again, I feel like I would be remiss if I didn’t mention drugs. I’m not going to say a lot about them, but the sale of drugs on the dark web is massively prevalent, and there are many, many marketplaces where drugs are their specialty and they do provide images of the drugs, details of how to ship them and where they will ship to, how to circumvent law enforcement, finding them, how to use drop addresses and things like that. And again, this is just highlighting how we can search within Vision for particular drug information and then view that on the dark web itself and see how their advertising it and you can see some of the prices here are actually really quite low.

And another group that I wanted to mention, this is the name given by cybersecurity researchers, Scattered Spider. They’ve been very active in the last year or two and have had some very high-profile attacks. MGM Grand and Caesars Palace in Vegas are probably the largest one and they have adopted social engineering and phishing techniques very successfully. They’re quite well known for bringing up help desks and convincing people to share passwords with them, but they also can be quite violent and extreme in terms of bullying individuals once they get their phone numbers and constantly messaging them and asking them for information until they share it. They’ve also been linked to swathing activity and been linked to a kind of a wider organization on the web, and Telegram in particular, known as the “Com”.
And so, there’s quite a lot of different groups that fit into that and as well as doing cyber attacks and they’ve also been doing some pretty nasty and other attacks in times of encouraging people to self-harm and conducting other acts and which are really quite awful. But again, it gives you that insight into not only the activities that they’re doing, but also how they’re operating, the kind of personalities that they have and how they’re communicating with each other and where their motivation comes from, and we see that you know very much through a number of different and telegram and discord and channels. But then they’re also linked to very large affiliates, like Black Cat and Alf and so they use their ransomware in their MGM ground attack. This is just an example of some of the administrators of one of the telegram channels, and that is linked to the COM and Scattered Spider. And so, you see, they’re kind of hiding in plain sight and obviously their images are of them and their names are not real, but the fact that you can even see here is admins are and they’re very cocky. They have egos, I think it’s the main thing.

I also wanted to mention seeing some kind of environmental crimes. I know that that is where a lot of the audience comes from. So, these are just some examples of where we have seen environmental crimes being shown on the dark web, on forums and on Telegram as well. So, you can see an image from a marketplace that is selling animal goods, illegal animal goods such as ivory and fur. We can also see advertisements. A lot of those on forums are the things like dogfights, cock fighting, and also animals for sale, and I would say that we do see this information and it is prevalent on the dark web, but we do also see a lot of that happening on the more mainstream sites such as TikTok and Instagram. But it’s certainly something on the forums and I would say Telegram and that other messaging apps in particular areas where we’re seeing that kind of activity and channels being set up to discuss both activities as well.
And then finally, given the audience, I wanted to give a couple examples that were specific to Canada. And so, I did a really simple search to highlight some of the things that are happening in terms of looking at Canada in our data and seeing where it appeared.

You can see a couple of different examples here. One of them is extremist, anti-Semitic rhetoric from individuals that are, I assume living in Canada and the discussions that they’re having on the forum. This is the image on the left and it’s from 4Chan, which is a well-known extremist forum. In the middle, Styx Market is one of the larger markets on the dark web that sells drugs, counterfeit goods, hacking tools, etcetera. You can see here they are selling Canadian passports and drivers licenses and they’re providing it with a selfie as well so that you can use it to get around KYC controls. But we see these sold all the time and you can see they’re not very expensive. How legitimate they are? I’m not sure, but that’s the kind of thing that we see and then also you can see false information being sold. So again, for identity theft and financial fraud, fullz is all the information about the individual – it’s got employer info as well as, Social Security numbers and names, addresses, etcetera, and that obviously is the image that’s come specifically from the dark web, I think it’s DarkDock Market. You can see is where it’s come from, and so you know you can use those keywords and that information to drill down into what you’re searching for. If you need to make sure that something has a nexus to calendar or the this the area that you operate in, and you can include that in your searches to make sure that it’s returning that information. One of the things I would say about the dark web is it is somewhat anonymous and it’s very difficult to know where people are coming from and so with all kind of cyber information, it’s difficult to know if an individual is a Canadian citizen or U.S. Citizen and so that can cause challenges, but you can search on those keywords and do what you can to find that information.
Lorena: Is it possible to turn on and off services within the platform to comply with Canadian law?
Erin: So I’m not sure the specificity of the Canadian law in terms of what that refers to but what I mentioned at the end there, we make all of our data available so it would be a case of focusing your searches to fit in with what’s acceptable and Canadian law. We do follow very strict guidelines in terms of the information that we collect and how we operate and to make sure that’s legally and ethically done and we comply with things like GDPR, I know that’s more European relevant, but you know data laws are becoming a thing everywhere so that is something that we certainly try to comply with and we could work with anyone in terms of you know what laws we needed to work around to, to make sure that we can support that.
Lorena: We can imagine that the amount of data you can find changes between one language and the other. But do you have any example or experience? If you have to manage in the past Investigations where you need to use two different languages like it is an example here in Canada like French and English and what features does this platform have and how to manage these types of investigations.
Erin: Yes. We collect all of the data and as it is, and we don’t make any changes to it. I think it’s important, as investigators and analysts, to see the raw data as it was written by the individuals and not changed in any way, and that’s one of the reasons we don’t offer any kind of translation services, but we do support over 50 languages now within the platform. For example, if you were doing English and French, you could search in both of those languages to see if information was returned in French or if it was returned in English. One of the features that we have in the platform also is what we refer to as Search Blocks, you can create search terms related to specific activities and we also supply some of those within the platform, things like drugs, counterfeit goods, hacking and generic terms, but we do provide those in multiple languages. We support English, French, Arabic, Russian, Chinese, I believe German for those Search Blocks, so that’s how we add that in to be able to search in in those different languages. And I should say as well that we make every effort to make sure that the data we’re collecting is as global as possible. We do try to make sure that we collect things that are in other languages and are going to be relevant to law enforcement and corporations globally.
Lorena: Can you please expand on current tools you use to navigate search the darknet?
Erin: The main tool we have is Vision, my team it’s obviously looking and sourcing that information all of the time and part of that is reviewing our collection that we already have and seeing other marketplaces and things that people are talking about and making sure that we can identify that, review that and see if it’s worth adding to our collection. There are some lists or websites that will list Tor or Onion URLs that you can use to find information as well and so we do review those periodically. We constantly search for new URLs that are created as well within the dark web and review those to see if they are applicable and then for things like Telegram and Discord and you know we do keyword searches and we have analysts that are operating in these channels and on these sites that are seeing mentions and discussions and identifying things that way. So I wouldn’t say there’s specific tools that we used and to navigate the dark web in terms of our collection efforts, but I would say that is the primary goal of the Vision platform that DarkOwl provides is to allow you to search the dark web and in a in a safe and secure way and you don’t need to worry about sock puppets or your VPNs or your proxies, but you’re able to see all of the data that’s being shared on the dark web.
Lorena: Can the information be used as intelligence in a court of law?
Erin: So, we’ve never tested that to be honest. We haven’t been asked to do that and it is something that we would support if we could. One of the things that we ensure that we do as part of our collection is maintain all of the metadata associated with the data that we’ve collected. So we’ll have the original URL, the date that it was collected, the method that was used to collect it, and you know other things that show where we got it from and where it was stored to have that providence and data because we know that that’s important to our law enforcement and customers, but we yes, it’s never been tested. So, we’ve never been asked to present it in a court of law to date.
Lorena: How do you deal with the ephemeral nature of onion sites? Similarly, how do you like some anonymous users from different sites? Neither sites nor users will cryptographically sign their pages messages to validate identity or do they?
Erin: The ephemeral nature of Onion sites, it’s just constantly reviewing them. They do go up and down. Because of the coverage that we have, we’re able to quickly identify when new sites are created or if they changed. A lot of the sites as well will also provide a list of validated mirrors and information as such as that that we will record. We do maintain a database of all of the sites that are most relevant, and the mirrors associated with them, but it is a constant thing to be able to kind of keep on top of that and how they’re moving. And as I mentioned, being part of those communities with anonymous accounts allows us to see what people are talking about and what the latest trend is.
And in terms of the anonymous users and I’m not sure, I got that entirely. But I think what you are asking is how do we know that individuals are who they say they are? And I think basically we don’t, we do see a lot of threat actors that will use PGP keys in order to validate the messages that they’re sharing. And you know, we’ve seen that with the administrators of breach forums and others and where they’ll put messages on Telegram, and they’ll sign it with a PGP key and they’ll have a website that that validates it. So, you can do that in in some ways, but I think you know very nature of the dark web anyone can create an account. You know some of these forums they do validate their members in terms of they’re trying to weed out law enforcement or cyber security professionals. So, they do make you come up with the back story and things like that. So, it can be difficult to access these sites, but I think the nature of it is you’re not necessarily going to know exactly who they are. They could be using multiple usernames; they could have different usernames across different platforms, and you know that’s one of the reasons they use it. My experience though has been – when it comes to attribution, a lot of these threat actors make mistakes and you know they may in some way connect a username to their true identity and that’s where things like leaks can be really beneficial or you know if there are on X or something like that, they have the accounts for a really long time sometimes you can identify phone numbers or email addresses that are associated with them. So, I’m not sure that really answered the question, but I think it’s the very nature of the dark web and the way that these user names are set up, it’s difficult to know exactly who they are and to validate who they are.
Lorena: How do you know a user for example, Baster, is same person on two different sites at and not a second person impersonating the first one.
Erin: Yeah, there’s no way to know that really. I think the only way to know that really would be with human analysis of interacting with them on both forums and seeing if there’s any similarities in language and things like that and if they’re using the same information, but it could, it could very well be an impersonation. They do try to validate some of the larger actors, more prevalent actors, where they’re operating and what they’re doing. I would say the dark web is very much built on reputation, and the threat actors like to show off and say what they’ve done and where they’re active and where you can get information from them but with all kinds of investigations, you need to validate that data and you have to view it with some skepticism. And so, unless you have, followed evidence that the suggests they are the same individual is gonna be difficult to do that.
Lorena: Are you using any generative AI or AI in general as a part of your platform or across the research you do?
Erin: Yeah. So, I think AI is definitely the buzzword of the moment in terms of everyone is jumping on that bandwagon and I personally think AI is really useful and a really exciting development and I think a tool that can definitely assist analysts in terms of their investigations with helping to write scripts and review images and things like that, I’ve seen a lot of demonstrations of how it can be beneficial and I’ve used it in some capacities myself. We don’t currently have it available in Vision through the tool. It is something that we are analyzing in terms of how we can use AI to best enrich our data and the information that we have. We don’t wanna rush into it in terms of adding just AI for the sake of AI. We want to make sure that it’s something that is beneficial to our users and so and as I said, we’re analyzing it and seeing what the best approach is. But you know, I can certainly think of some ways in terms of, to that previous question of threat actors, of having it analyze language patterns and things like that to see if there are correlations. Being able to identify particular attributes within kind of the data that we’re collecting, etcetera. So yeah, not something that we currently support, but definitely something that we are actively looking to support in the future.
Lorena: How can users on the dark web trust each other and coordinate?
Erin: I don’t think they can trust each other. To be honest, I mean, these groups are very nebulous. You constantly see chatter between these groups, accusing each other of being FBI agents or other law enforcement. They all think that people are watching them, which is probably true. And so I think the way that they probably grow those relationships that we see is, is taking the conversations and the communications to more direct messaging. So, something that we wouldn’t necessarily have site of recovery job, but I as I kind of alluded to before, a lot of it is built on reputation and trust and there are reviews. So, for instance, if you’re a seller of malware or drugs or something like that, people leave reviews. And if you haven’t spent, if you’ve stolen the money and not sent the goods, that will be reflected. If you have sent something that’s not good quality, you’ll get those reviews as well and these threat actors can be pretty and vindictive. So, you know, you do get people getting doxed all of their information being shared and being accused of, of certain things, their personal addresses being put out on the Internet. And you know, there have been cases of real-world attacks where someone will say this person lives here and they have this much Bitcoin and people have tried to kidnap them. So, I think they you can’t really trust anyone, and you have to be very careful. But that’s kind of the community and the activity that they enter into, to be honest.