What are APIs?
June 06, 2024
Cybersecurity might has well have its own language. There are so many acronyms, terms, sayings that cybersecurity professionals and threat actors both use that unless you are deeply knowledgeable, have experience in the security field or have a keen interest, one may not know. Understanding what these acronyms and terms mean is the first step to developing a thorough understanding of cybersecurity and in turn better protecting yourself, clients, and employees.
In this blog series, we aim to explain and simplify some of the most commonly used terms. Earlier this month, we covered CVEs. In this edition, let’s dive into APIs.
APIs 101
Simply put, application programming interfaces (APIs) allow for two software applications to communicate each other, to make requests, receive responses, and exchange data. This is true for both mobile and web-based applications. APIs permit humans and machines to exchange, process, and use data using rules and protocols. Once of the important benefits is that APIs allow for and enable applications that are written in different programming languages, or are running on different operating systems, to easily communicate and pass data.
While APIs run behind the scenes and allow for software to communicate with other software, but there are plenty of current examples of API use one might not be aware of. For instance, if a user logs into an account or service by opting to use their Google or a social media account (to avoid having to create a brand new account), this login flow uses API services to exchange authentication information between the Google or social media account and the platform to enable a convenient and seamless login experience for the user.
There are two primary designs for APIs – Simple Object Access Protocol (SOAP) and Representational State Transfer (REST) approaches. While we will not dive deep into the technical aspects, the main takeaway is that SOAP is a very structured XML data format, while REST is more flexible and permits data exchange in multiple formats, such as JSON, Plaintext, or XML. Being more flexible, REST can use SOAP protocol, but the reverse is not true – SOAP cannot use a REST protocol. REST protocols are useful for mobile devices that use an API.
Here at DarkOwl, we allow for access to our platform via a curated User Interface (UI) as well as several API endpoints. The APIs enable our customers to use DarkOwl Vision data in their own software applications. You can view our product offerings here.
Unfortunately, while APIs automate and permit quick transfer of a large amount of data, like so many facets of the cyber world, they are subject to malicious activity and attacks.
API Abuse
Malicious actors are focusing on attacking APIs more and more as APIs transmit loads of valuable information and data. Without proper security, including regular software updates and securing the multiple entry points that facilitate API function, as well as legacy APIs which could be overlooked and left unprotected, APIs can be subjected for malicious use. This is especially true when in most cases, developers provide very detailed API documentation to allow for sanctioned API use. New and prospective customers are not the only ones who rely on API documentation to fine tune API use.
Actors can go against APIs with several traditional types of attacks. This list is not exhaustive, but is provided as a high-level example of the possible kinds of attacks directed against API infrastructure:
- Distributed denial of service (DDoS) attacks, which would overwhelm an API and make its services unavailable to legitimate, paying customers.
- Malicious actors can also brute-force APIs, using credentials to gain access and abuse the interface, and then steal sensitive/proprietary/corporate information.
- Machine-in-the-middle or attacker-in-the-middle (MITM or AITM, respectively) is where an actor can intercept and change communications, permitting data theft or manipulation of API data.
- Procuring legitimate API keys, which are often left accidentally exposed or compromised.
API Discussion in DarkOwl Vision
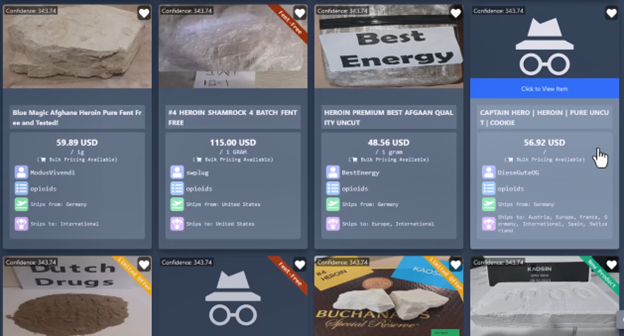
DarkOwl constantly observes actors discussing methods for API attacks at multiple layers of the tech stack, trading methods for having maximum impact, and selling possible API access to various organizations:

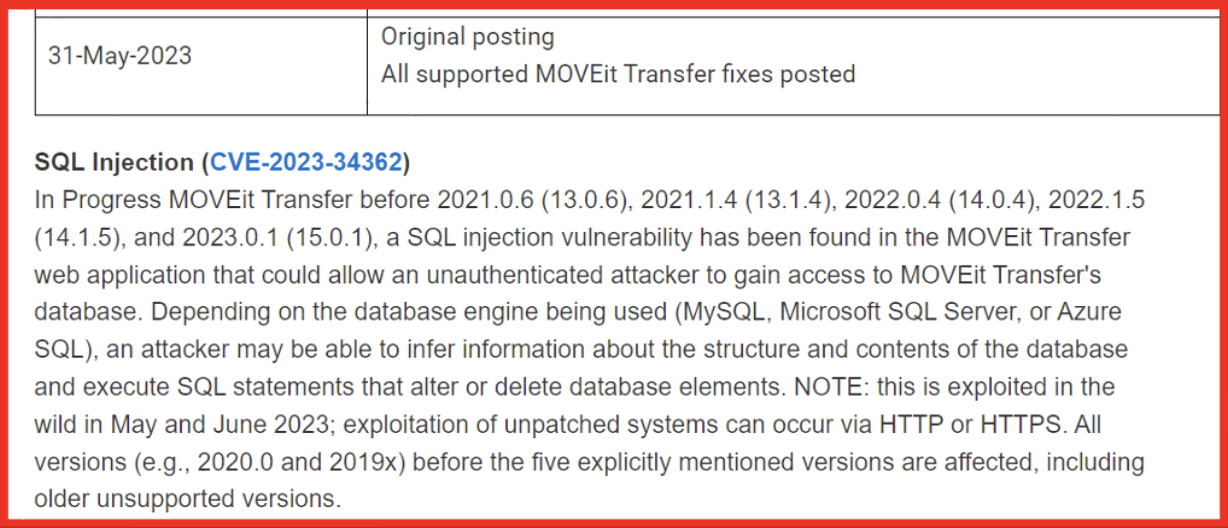
Figure 1: An actor on (now defunct) Breached Forums advertises possible methods to attack APIs at various levels of the tech stack; Source: DarkOwl Vision

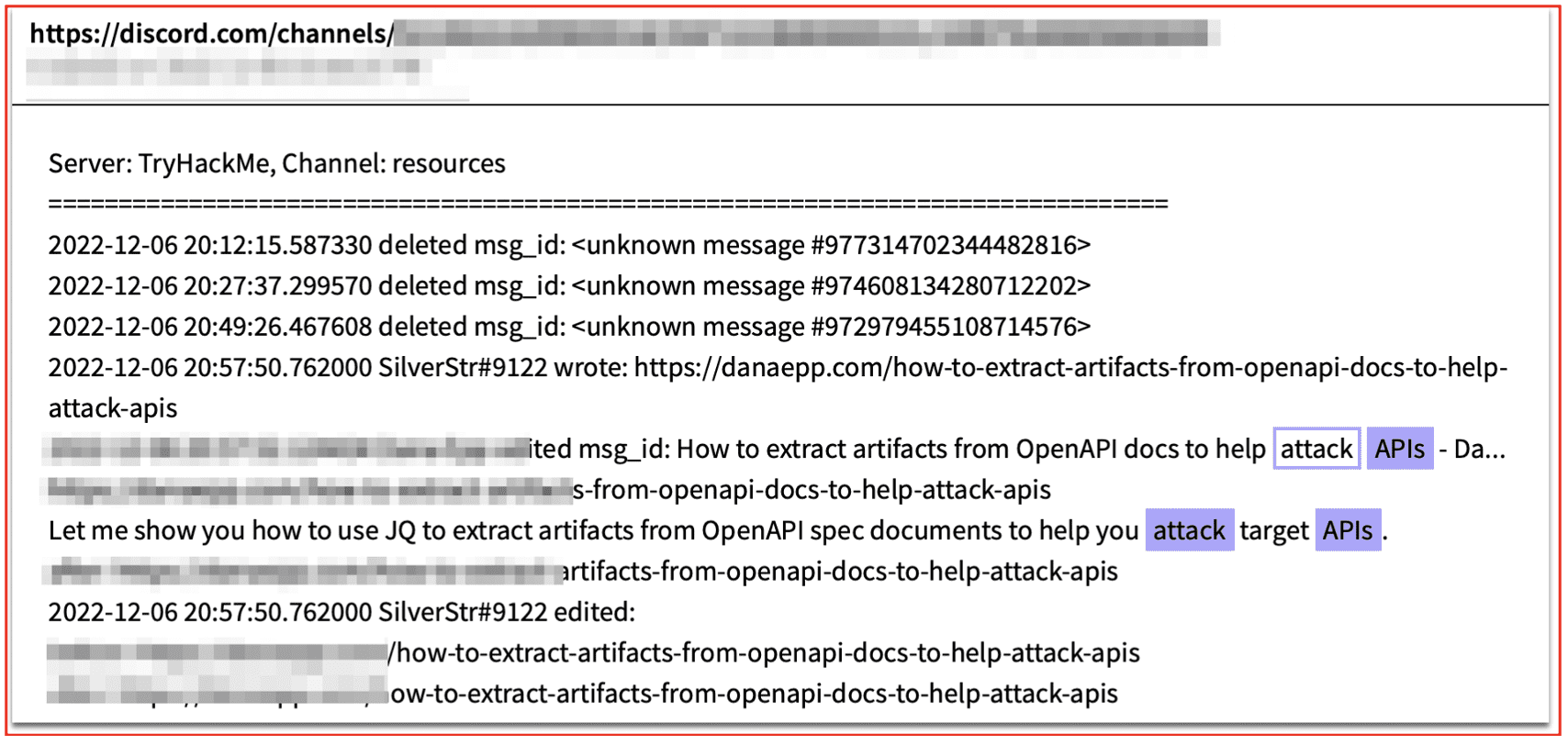
Figure 2: A Discord server publishes materials, including a website, that specifically aids attackers in going after and attacking APIs; Source: DarkOwl Vision
Securing and Protecting APIs
Mitigating API attacks includes protection at multiple stages.
- First, like everything that involves data transfer, data must be encrypted both at rest and during transit. Role-based access control (RBAC) permits explicitly approved applications and users to have access, lessening the possibility for an unintended individual to gain unauthorized access.
- APIs also have their own gateways, which are positioned between the client and the provided services. The gateway implements rules and standards that allow for access and authenticates attempted access.
- Finally, zero-trust models are also applicable to protecting APIs. Zero trust requires user rights for authentication and is an effective way to prevent repeat users that, behind the scenes, could be an imposter. In addition to all of the above specific steps, constant monitoring and vigilance is suggested, as API’s are a data rich source, and technology is constantly changing.