July 11, 2024
DarkOwl analysts regularly follow threat actors on the darknet who openly discuss cyberattacks and disseminate stolen information such as critical corporate or personal data. Such analysis helps DarkOwl’s collection team direct crawlers and technical resources to potentially actionable and high-value content for the Vision platform and its clients.
Introduction
For fans of Pokémon, the name ShinyHunters refers to a practice of seeking out, capturing and collecting shiny Pokémon. However, on the dark web the term has a much more nefarious meaning.
ShinyHunters is a cybercriminal group known for their high-profile data breaches and relentless pursuit of sensitive information, and has carved out a reputation as one of the most prolific and dangerous actors in the cybercrime arena.
In this blog, we will take a deeper dive into their activities and their association with the dark web forum BreachForums.
Who are ShinyHunters?
Although it is unclear exactly who is a part of ShinyHunters, although at least one member was sentenced to three years in prison by a US court, they are assessed to be an international cyber threat group who first emerged in 2020 and quickly became associated with large-scale data breaches targeting both small and large organizations.
They are known to infiltrate company databases, exfiltrating sensitive information, and then selling this data on underground forums or using it for extortion purposes. They are not shy about sharing this information on dark web sites created to share exfiltrated data.
The group were known to be active on the site RaidForums, which was succeeded by BreachForums, selling data they had stolen from companies for a profit.
Figure 1: ShinyHunters RaidForums Profile
Tools, Techniques and Procedures
ShinyHunters utilize advanced hacking techniques to gain unauthorized access to company systems. They often exploit vulnerabilities in web applications, engage in credential stuffing attacks, and use phishing campaigns to steal login credentials.
The groups primary focus is on stealing large datasets, which often include personally identifiable information (PII) such as names, email addresses, phone numbers, and passwords. In some cases, they have also accessed financial information and proprietary corporate data. After obtaining data, ShinyHunters typically monetize their efforts by selling the information on dark web marketplaces and underground forums. They have also been known to attempt to extort companies by threatening to release the stolen data unless a ransom is paid.
It has been reported that ShinyHunters adopt a range of techniques as part of their hacking efforts including reviewing company Github repositories, exploiting unsecured cloud buckets (online storage spaces) targeting developer repositories accessing credentials and API keys as well as phishing campaigns.
ShinyHunters have also been observed collaborating with other cybercriminal groups. This trend of collaboration has enabled them to expand their reach and increase the sophistication of their attacks. Joint operations have led to more coordinated and devastating breaches, affecting a wider range of sectors and organizations.
Notable Victims
ShinyHunters’ initial wave of attacks in 2020 was characterized by a series of high-profile breaches. They claimed responsibility for infiltrating multiple companies and leaking vast amounts of user data. Some of their most notorious breaches include:
Tokopedia
In May 2020, ShinyHunters allegedly breached the Indonesian e-commerce giant, Tokopedia, stealing data of over 91 million users. This breach included sensitive information such as usernames, emails, and hashed passwords.
Microsoft
The group also claimed to have accessed private GitHub repositories belonging to Microsoft, exposing portions of the tech giant’s source code. Although Microsoft quickly responded, the incident highlighted the group’s capability to target even the most secure organizations.
BigBasket
In October 2020, ShinyHunters reportedly breached the Indian online grocery delivery service, BigBasket, leaking data of over 20 million users. The stolen data was later found being sold on the dark web.
AT&T
In August 2022, the group claimed to have successfully breached AT&T obtaining more than 70 million records. They sold this information for $200,000. The data was then leaked on Breach Forums in early 2024 for free.
Pizza Hut Australia
In September 2023 they claimed to have 30 million customer order records from Pizza Hut Australia as well as customer data.
Current
ShinyHunters have not slowed down since their initial wave of attacks. In 2023 and 2024, their activities have continued to evolve, showcasing their adaptability and persistence in the cyber threat landscape.
ShinyHunters have maintained their focus on the retail and e-commerce sectors. In late 2023, they targeted several online retail platforms, stealing customer data and payment information. This not only led to financial losses for the companies involved but also compromised the security of millions of users.
Furthermore, recognizing the value of healthcare data, ShinyHunters have shifted some of their focus to this sector. In early 2024, they breached a major healthcare provider, exposing sensitive patient information, including medical records and insurance details. This breach underscored the critical need for enhanced cybersecurity measures in the healthcare industry.
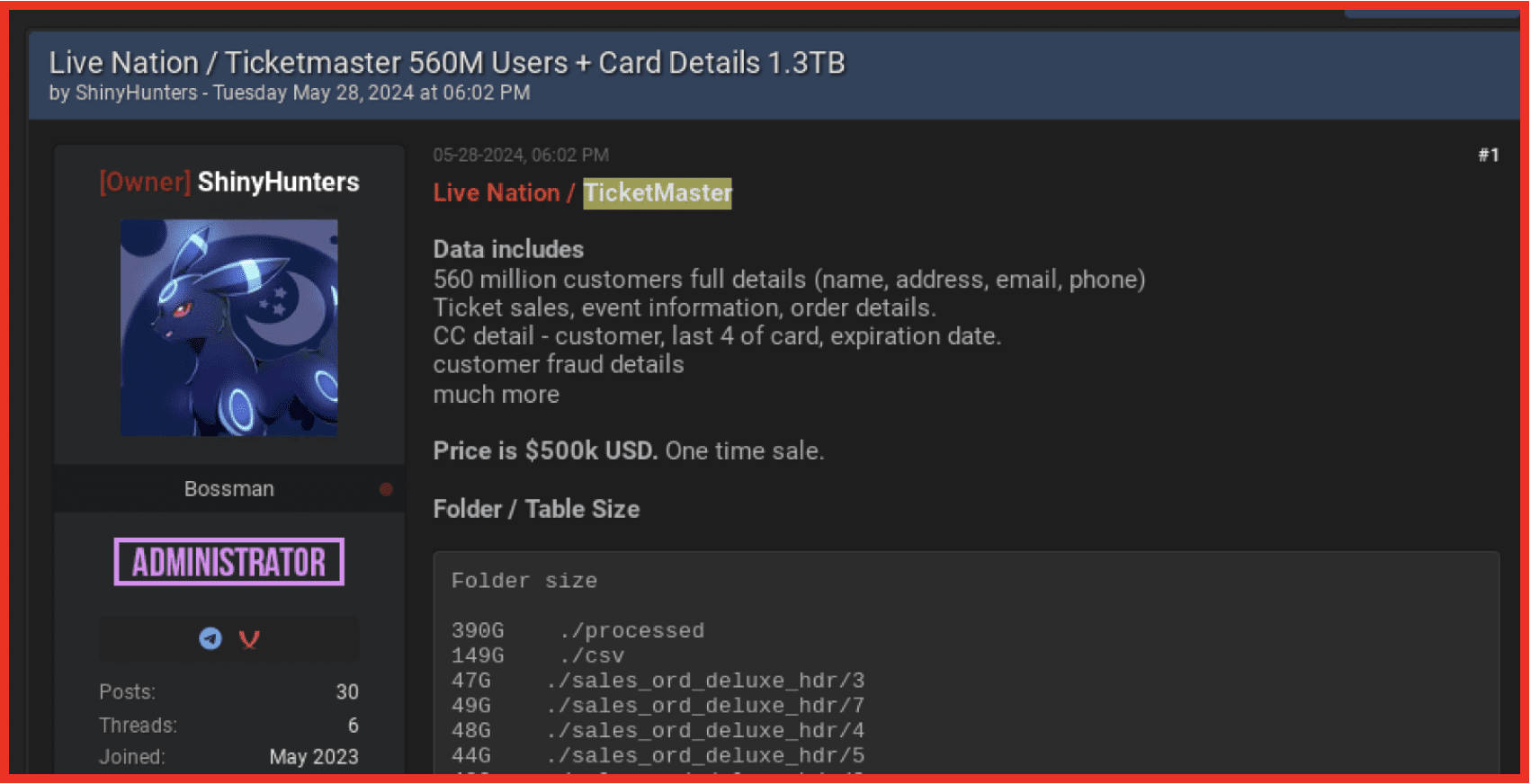
Most recently ShinyHunters have claimed to have access to LiveNation/Ticketmaster data which they made available for sale on BreachForums.
Figure 2: ShinyHunters advertise Ticketmaster data on BreachForums
ShinyHunters and BreachForums
ShinyHunters have been active participants in dark web forums, leveraging these platforms to sell the data they steal. By listing stolen datasets on these forums, they can reach a broad audience of potential buyers, maximizing their profits. The forums also provide a degree of anonymity, making it more challenging for law enforcement agencies to trace transactions back to the perpetrators.
As well as making their data available for sale, they will often release the data at a later date for free, meaning that some of this data can be widely distributed and used by a range of threat actors to conduct further attacks.
ShinyHunters were active on Raid Forums when they first emerged and then moved to BreachForums when it succeeded RF after law enforcement action. Since then, BreachForums has been the target of multiple law enforcement operations leading to the seizure of the site. However, each time this has occurred to date the site has re-emerged.
Figure 3: Seizure notice for BreachForums
After the seizure of BF in June 2023 ShinyHunters partnered with a previous administrator, Baphomet, to relaunch the site and they managed the site with Baphomet until it was seized again in May 2024.
Figure 4: Timeline of RaidForums and BreachForums
With the latest seizure, it was not just the forum itself that was targeted, but also Telegram channels associated with the site. It was also reported that Baphomet was arrested, but this has not been confirmed by Law Enforcement officials.
In response ShinyHunters relaunch the site, although many in the community feared that it was a honeypot. The site continued to come under attack with ShinyHunters releasing updates on the. Issues that they were dealing with.
However, soon after the return on June14th the account on Breach Forums for ShinyHunters announced their retirement stating that they were burned out by all the accusations of being a honeypot and the constant attacks. They stated that they would be handing off control of the site to a user named Anastasia.
Figure 6: Post on BreachForums retiring as admins
Their profile on the site is now showing as “banned” due to retirement.
Figure 7: Current BF profile page for ShinyHunters
It remains to be seen what this means for the group ShinyHunters and if they will remain active in stealing data and making it available for sale online. It is possible that data could be shared under another alias, or they could return. The communitys’ faith in BreachForums has also diminished with several threat actors claiming to be launching a new site which will replace BreachForums without fear of Law Enforcement involvement.
Conclusion
ShinyHunters represent a significant and ongoing threat in the world of cybersecurity, as we await what their next steps will be. Their activities on BreachForums illustrate the symbiotic relationship between cyber criminal groups and the underground marketplaces that facilitate their operations. To mitigate the risks posed by ShinyHunters and similar groups, organizations must prioritize monitoring these dark web activities to ensure they are taking the necessary steps to mitigate against threats from these groups.
Don’t miss any updates from the DarkOwl team. Follow us on LinkedIn.