Ukraine’s Call for Help Results in Global Cyberwar: Reviewing the Fallout
May 13, 2022
On the 24th of February, after months of failed diplomacy, the existing geopolitical landscape of Russia, Ukraine, NATO, the EU, China, and the myriad of complex international relationships drastically changed. Thousands of Russian troops and equipment crossed over into Ukraine’s sovereign territory and missile strikes of critical infrastructure and historical landmarks sent its people deep into bunkers underneath the cities, while other took up arms to defend their country.
While the kinetic war waged in the physical realm, Ukraine’s Ministry of Digital Transformation turned to the digital realm for assistance. Within days of the invasion, a call across underground forums and chatrooms was placed and hundreds of thousands of volunteers – many who identify with the Anonymous hacktivist collective – answered.
Ukraine’s call for help sparked off the first ever global cyberwar.
Weeks before tanks and soldiers marched on the cities of Ukraine, Russia had already carried out a series of successful cyberattacks against Ukraine, hitting critical infrastructure and financial institutions around the country with at least six unique strains of destructive wiper malware. DarkOwl observed data exfiltrated during some of those attacks surface in the darknet, such as the Free Civilian service on Tor where hundreds of gigabytes of Ukrainian citizens sensitive personal data appeared. Recent reporting confirms Russia’s GRU also carried out a massive cyberattack against Viasat, knocking its customers’ KA-SAT satellite broadband offline an hour before the invasion.
Russia’s pre-invasion attacks against Ukraine pale in comparison to the retaliative cyberattacks launched against Russia by the international hacktivist community over the last 77 days. Since the invasion began, thousands of hacktivists, cybersecurity researchers, pen-testers, and ‘greyhats’ are actively participating in daily campaigns to disrupt Russia’s military offensive and influence the perceptions of the Russian people trapped behind the walls of the iron curtain.
Cyber Warriors Use Their Keyboards and Phones as Weapons in Global Cyberwar
Ukraine’s Ministry of Digital Transformation has played a large roll in mobilizing calls to arms from a digital perspective. The IT Army of Ukraine – a digital army of over 275,000 volunteers that was tasked by The Ministry – targets Russian websites every day for widespread distributed denial of service (DDoS) attacks. The Ministry also coordinated directly with SpaceX on acquiring thousands of Starlink terminals for redundant satellite Internet access and spearheaded public calls to international business leaders and retail suppliers to withdraw from operating in Russia.
Hacktivist cyber cells aligned with the Anonymous collective and pro-Ukrainian criminal cyber threat actors conducted hundreds of direct information operations campaigns against Russia using any and every exploit in their arsenal. To this day, the attacks continue relentlessly despite Russia’s attempts to use geo-fencing and Cloudflare services.
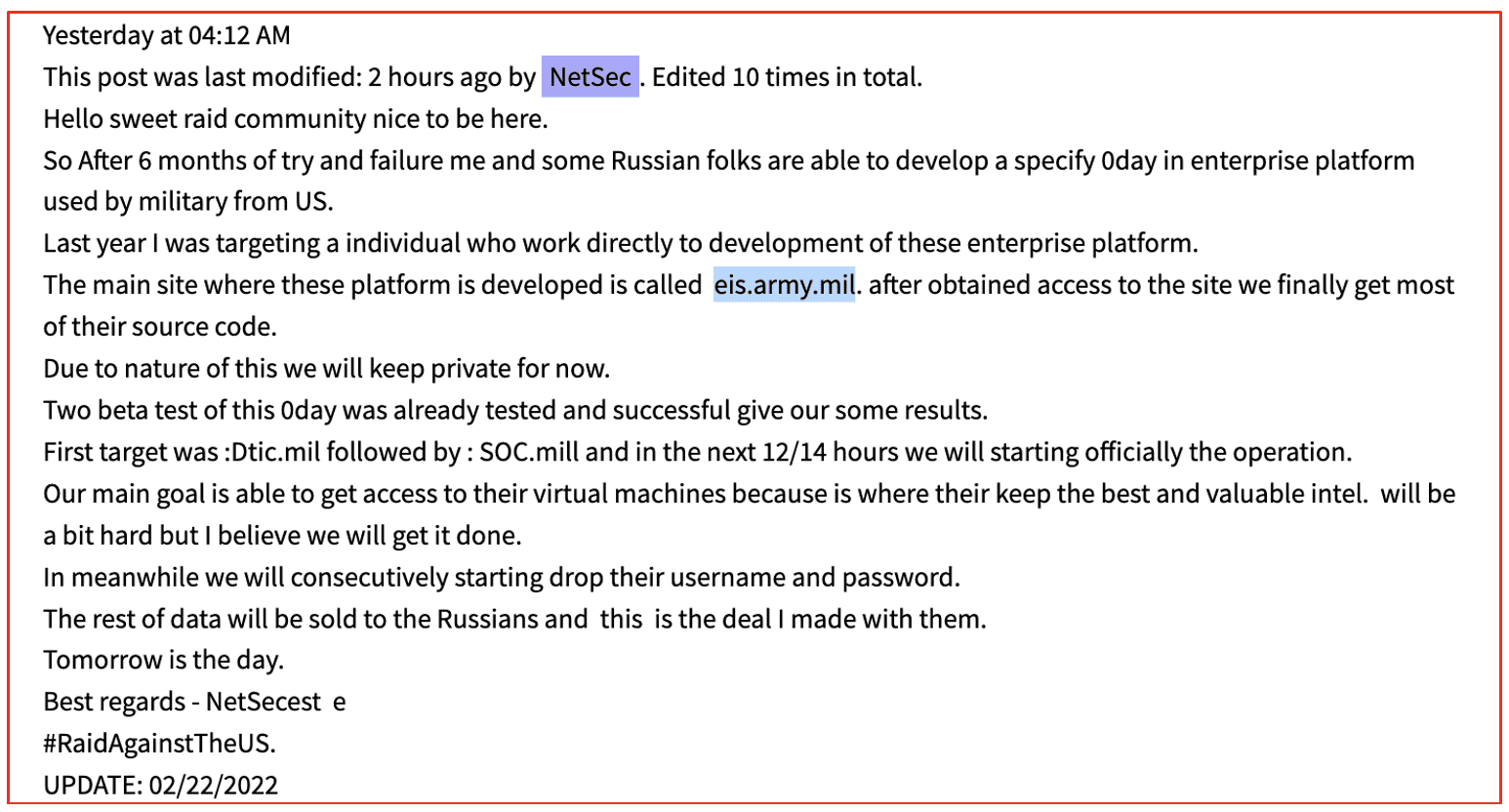
Within the first week of the war, we witnessed credentials for numerous critical Russian government ministries leaked on the deep web; the names, phone numbers and personal assets of Russian oligarchy released to the public; names, passports, and dates of birth for over 120,000 Russian soldiers deployed in Ukraine; internal documentation for Russia’s Police Force, Ministries of Foreign Affairs, and Economy leaked.
Darknet criminal communities split over their national alliances. Pro-Russian ransomware groups watched their affiliates abandon their programs and turn on them. We witnessed multiple groups have the internal documentation, source code, and private chats leaked. Several Tor forums and vendor markets hosted in Russia faced persecution through direct cyberattacks, database leaks, and deanonymization of IP addresses.
Propaganda as a Weapon
In any cyberwar, information is power. Knowing that Moscow would try to frame the war as a justified and a defensive strategic military operation, Anonymous worked immediately to identify facts and combat misinformationn. Videos of the attacks against civilian buildings went viral on social media, YouTube, and Discord. Russian television, radio, streaming services were illegally accessed to share images from Ukraine. Anonymous security specialists from Poland known simply as squad303 spun up their 1920.in service – named after a famous RAF squadron involved in WW2’s Battle of Britain – which allowed strangers to contact to a random Russian citizen via SMS, email, Whatsapp, and Viber using leaked lists of millions of Russian citizens’ personal contact information and social media.
As of the first week in May, the squad303 team announced that over 100 million direct messages had been sent using their service.

Figure 1: Screenshot of squad303’s Russian Citizen Phone Number Contact Service
The Kremlin responded by tightening their control on the public media narrative, shutting down social media platforms like Twitter, Instagram, and Facebook, officially calling their war a “special military operation” and using militarized riot police to enforce a strict ban on all forms of public protest of the invasion.
Western media and independent news sources have been threatened with journalists facing a potential 15-year prison sentence for reporting anything that countered Putin’s narrative of “denazification of Ukraine” and “freeing” its people from imminent nuclear threat from the US and NATO. Russian propaganda outlets began recirculating false claims of US-sponsored bioweapon laboratories and nuclear weapon storage facilities across Ukraine to justify the invasion.
Since the invasion, the Russian Internet Research Agency (IRA)-backed ‘troll army’ is in full force with thousands of bot accounts active across Twitter, Facebook, Discord, and Telegram spinning a different story on the ground in Ukraine. The accounts disseminate elaborate storylines of Ukraine shelling their own citizens and supporting fake videos and doctored media.
QAnon and Russian Disinformation
Deep web and darknet imageboards (or “chans”), historically supportive of the QAnon movement and home of the most outrageous conspiracy theories ever told, have also been supportive of Putin touting his critical international role – like that of former President Trump’s – in ridding the world of its secret Cabal and the greedy desires of the New World Order.
According to research shared by Bellingcat, posts on the imageboards in early March stated Russia capturing Ukraine’s Chernobyl plant was critical to stopping everything “from DNA experiments, adrenochrome, torture, childsex and rape facilities, cloning installations and much more.” Ironically, QAnon Russia – with one of the largest QAnon follower base at over 90,000 users – has a dissenting opinion and refuses to share the propaganda, but instead promotes peace in Ukraine, and a united brotherhood across all nations in the region including Belarus, Russia, and Ukraine.
Anonymous retaliated against these coordinated disinformation efforts by hacking Russia’s Roskozmador information and propaganda agency and its All-Russian State Television and Radio Broadcasting Company (VGTRK) and leaked over 900,000 emails and 360,000 files from across the organizations which detail how television and radio are tightly regulated and programs censored directly by the Kremlin.
In anticipation for Russian propaganda expected to be broadcast on Victory Day on May 9th, Anonymous successfully compromised Russian state television changing nearly every television description during Victory Day ceremonies to read:
“The blood of thousands of Ukrainians and hundreds of their murdered children is on your hands. TV and authorities are lying. No to war.”
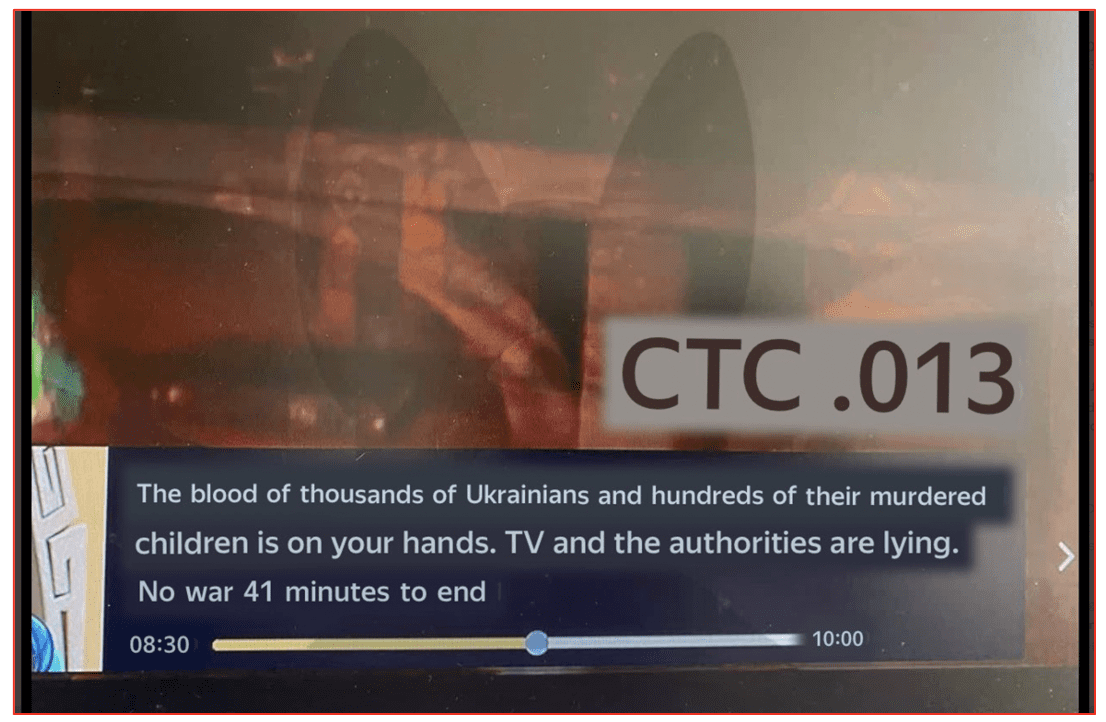
Figure 2: Television Program Description from Russian State TV Programming Hack (Source: Anonymous)
Virtual private network (VPN) use in Russia has skyrocketed increasing over 3,000% since mid-February. According to open sources, at least some percentage of curious Russian citizens are bypassing censorship by using VPNs to access international news about Ukraine and social media platforms. As of this week, reports estimated an average of 300,000 downloads of VPN applications occurred every day.
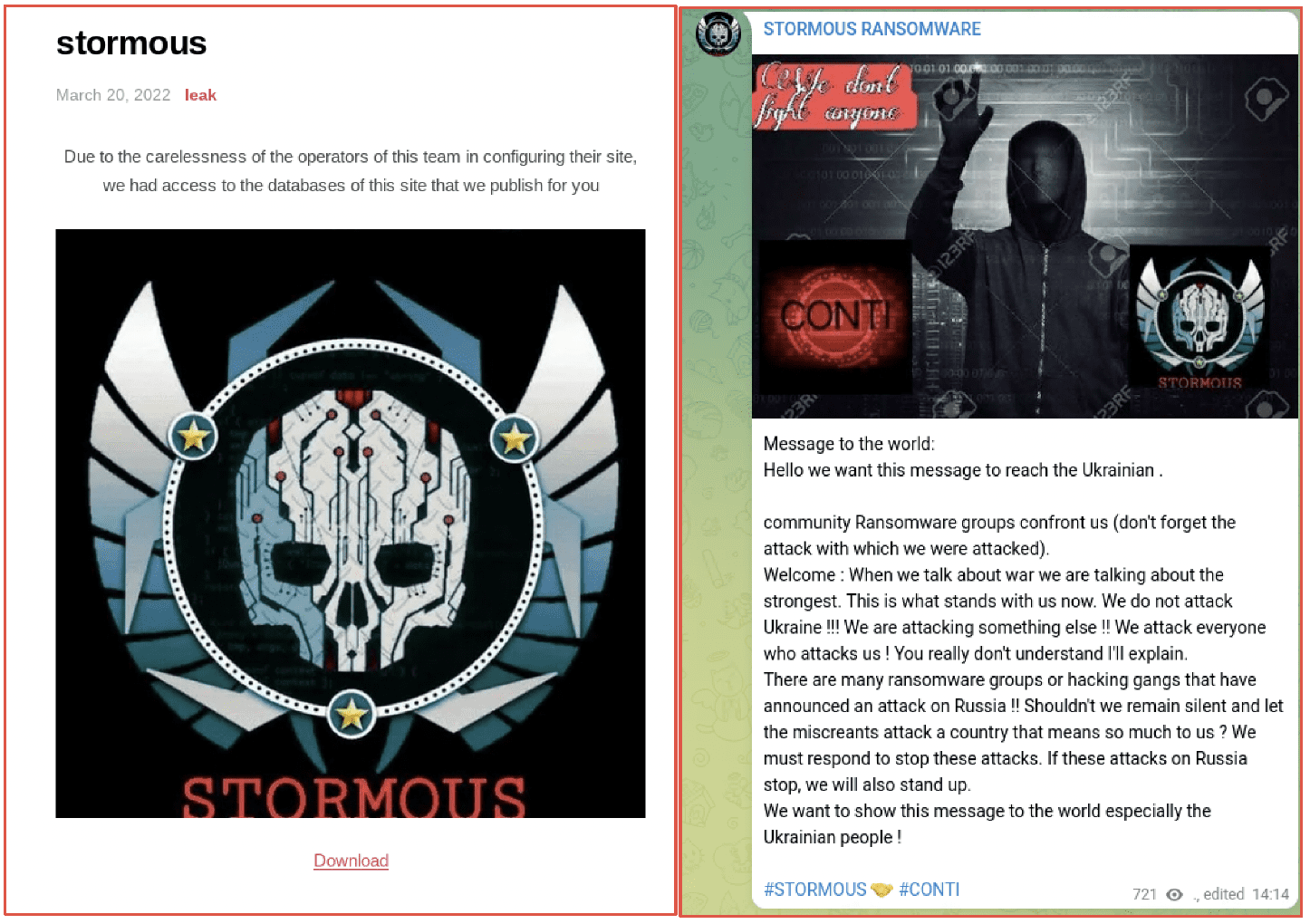
The first fallout in the darknet from the cyberwar was direct attacks against the CONTI ransomware gang shortly after they publicly declared their support for Russia’s invasion. A Ukrainian-based ‘security researcher’ took to Twitter to leak CONTI’s ransomware source code, details of their internal operations, botnet infrastructure, along with private jabber chats and PII from members of the team.
Similar leaks followed for members of the FSB-backed Trickbot group including dossiers of their members.
Several darknet forums, marketplaces, and XMPP chat servers were taken offline, and information leaked in a digital public shaming for each group’s association with Russia.
In March, Kelvinsecurity exploited a simple IDOR vulnerability on the darknet site: DATABASE Market and leaked the contents of the market’s SQL database and deanonymized the server publishing the IP address of their host located in St. Petersburg.
Earlier this month, member of Anonymous known as v0g3lsec hacked a Russian-linked darknet vendor shop and replaced the site’s content with a description of squad303’s information service and link to their surface website.
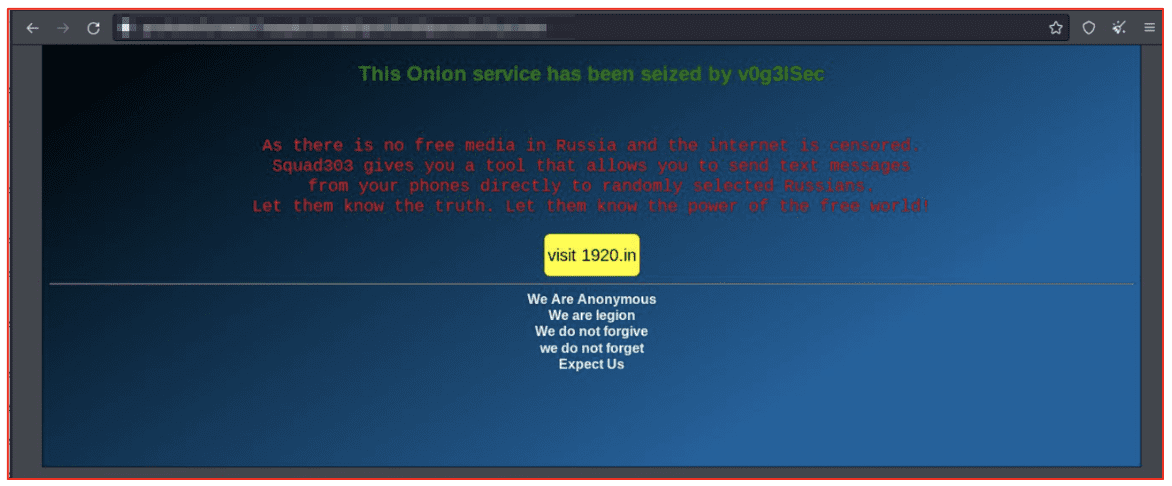
Figure 3: Tor Service Defacement by v0g3lsec
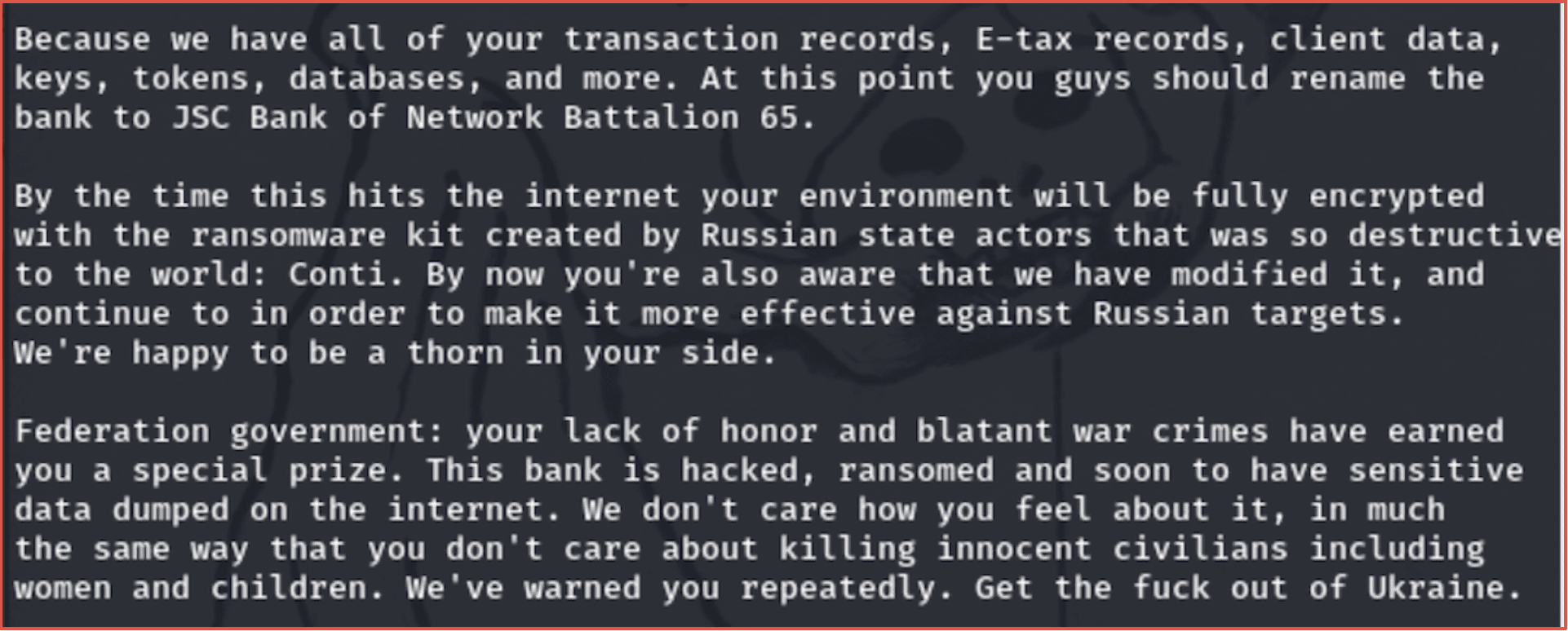
Network Battalion (nb65) successfully deployed CONTI’s leaked ransomware source code with a modified cipher and has carried out over half a dozen or more attacks against targets across Russia. Their most recent attack involved Qiwi Кошелек Russian payment system, with over 149,000 kiosks and terminals around the country. Earlier this week, the group shared a database containing over 7 million unique credit card numbers and associated PII for Qiwi platform users in Russia.
Critical Infrastructure Attacks
We have not observed a mass disruption of Russia’s critical infrastructure such as gas, power, and water supplies. This is likely because like the US, such systems decentralized and distributed across various districts across the country. However, some limited interruption has been observed during the conflict. In early March, Cyber Partisans utilized industrial control system (ICS) attacks to shutdown trainlines supplying the Russia military in Belarus. Automated ticketing stations were knocked offline and forced the transportation authorities to issue paper tickets causing delays.
Oil and gas related entities in Russia such as: Gazprom Linde, MashOil, Neocom Geoservice, Enerpred, Aerogas, and Technotec have all suffered cyberattacks resulting in thousands of internal Microsoft Exchange email data leaks in the deep web. In late April multiple explosions occurred resulting in catastrophic fires and injuries at Druzhba oil depot. Subsequent open-source reports on Telegram suggest that the explosions at the Transneft-Druzhba Oil Depot supplier for military units were ‘delivered with the help of drones’ from Ukraine. The depot and associated pipeline is the main route for getting Russian oil into its European customers, although EU leaders have signaled a plan to stop purchasing oil from Russia by the end of the year which may lead to a full embargo across the continent.
In recent weeks, several other mysterious fires across the country have been reported including an ammunition depot in Staraya, another ammunition plant in the Russian town of Perm, an Aviation school in the same village of Perm, a government building in Korolev, a chemical plant near the border of Ukraine, an oil depot in Belgorod, a defense research center in Tver, a pro-Kremlin publishing house in Moscow, a storage hangar in the Bogorodskoe district, and oil tanks were set fire in the industrial zone of Nizhny Novgorod.
Another random fire also started in Belgorod less than two days ago. Reports have not specified where the fire originated specifically.

Figure 4: Recent Explosions in Belgorod Captured by Social Media Users (Source: VK)
It is unclear from reporting whether these explosions were a result of SCADA cyberattacks or direct arson and sabotage by Russian locals sympathetic with the situation in Ukraine. The darknet threat group GhostSec recently compromised Russia’s Metrospetstekhnika ASOTP system for transportation and successfully caused dozens of trains connected to the system to cease operation. The group claims they were able to access and disrupt the internal temperature, smoke, and backup battery systems for any of the trains connected to the network.
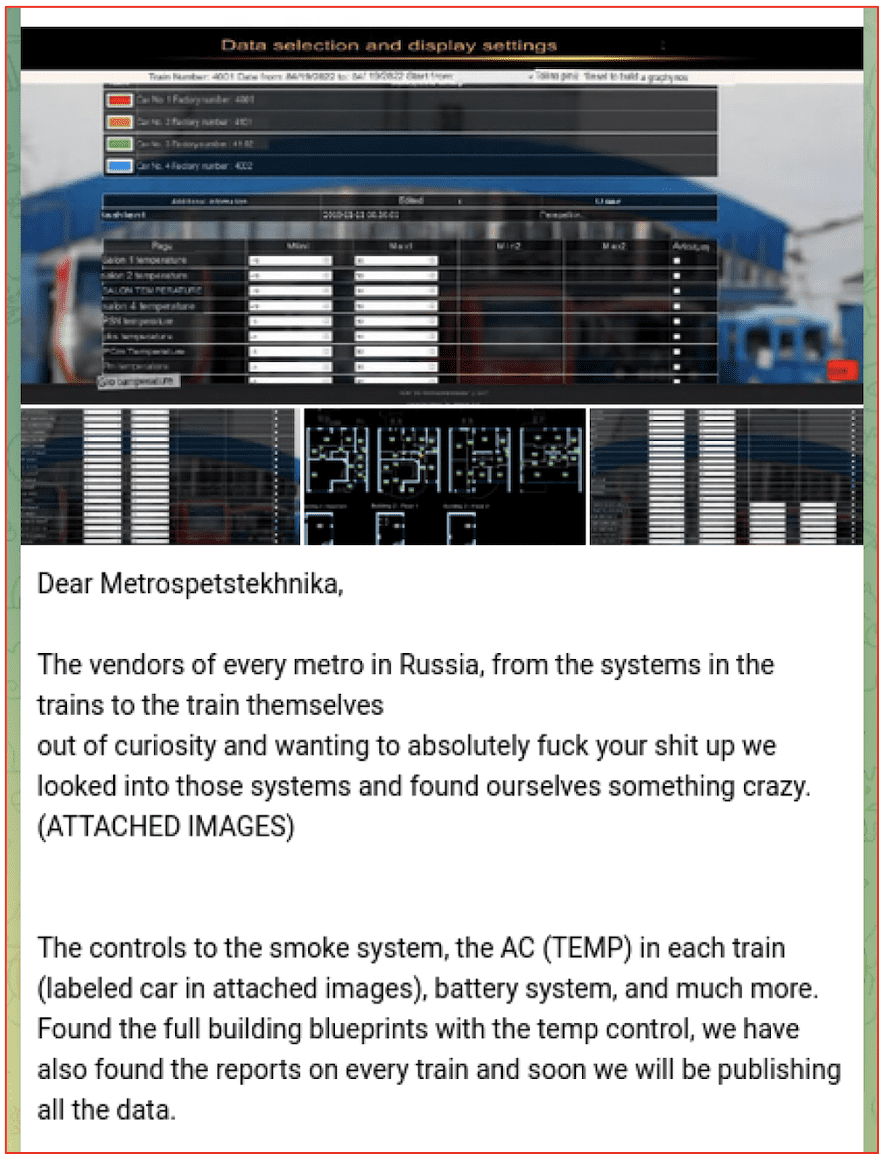
Figure 5: Announcement of Metro Train Attack by GhostSec (Source: Telegram)
Anonymous Leaks Stolen Data
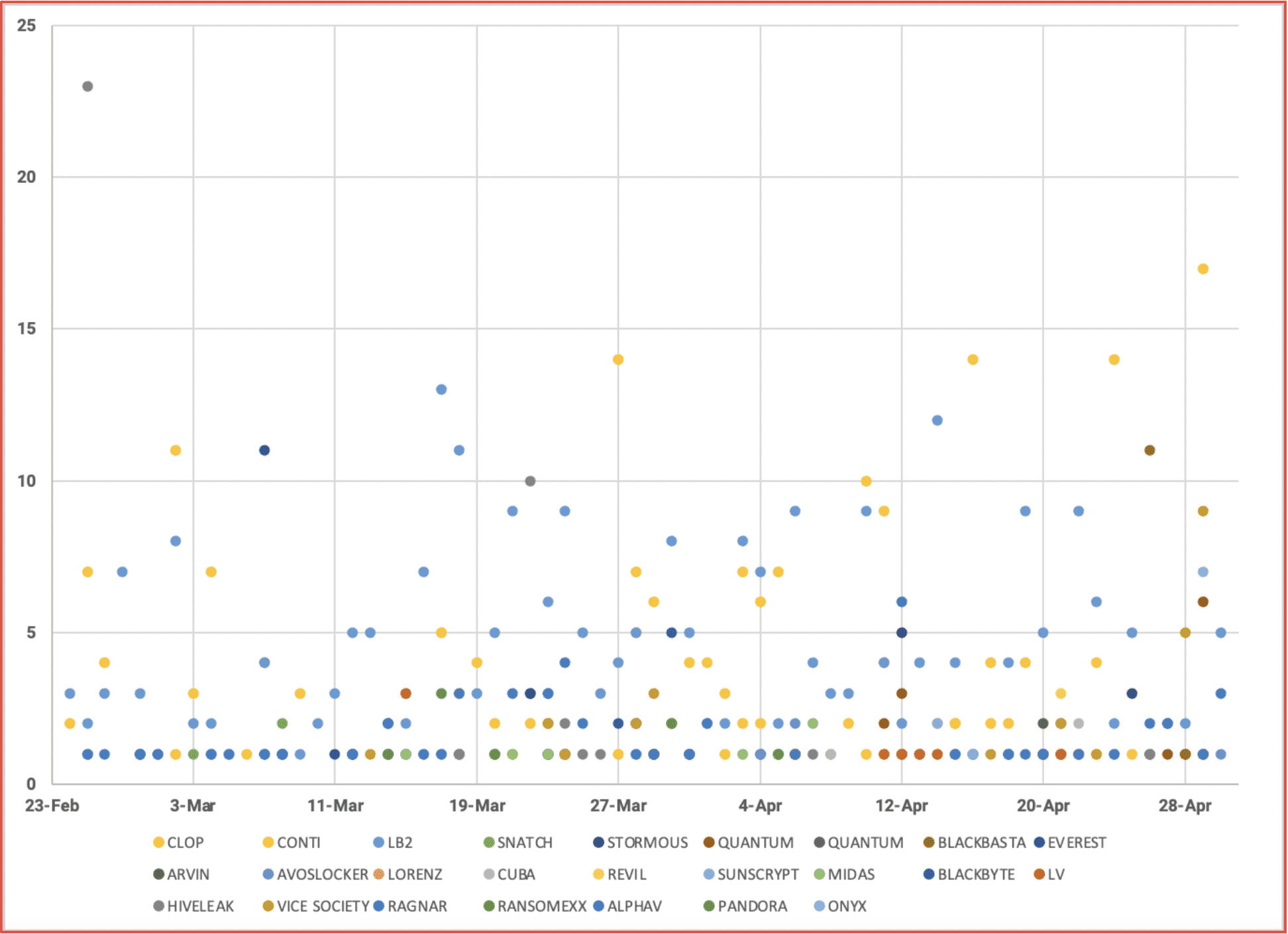
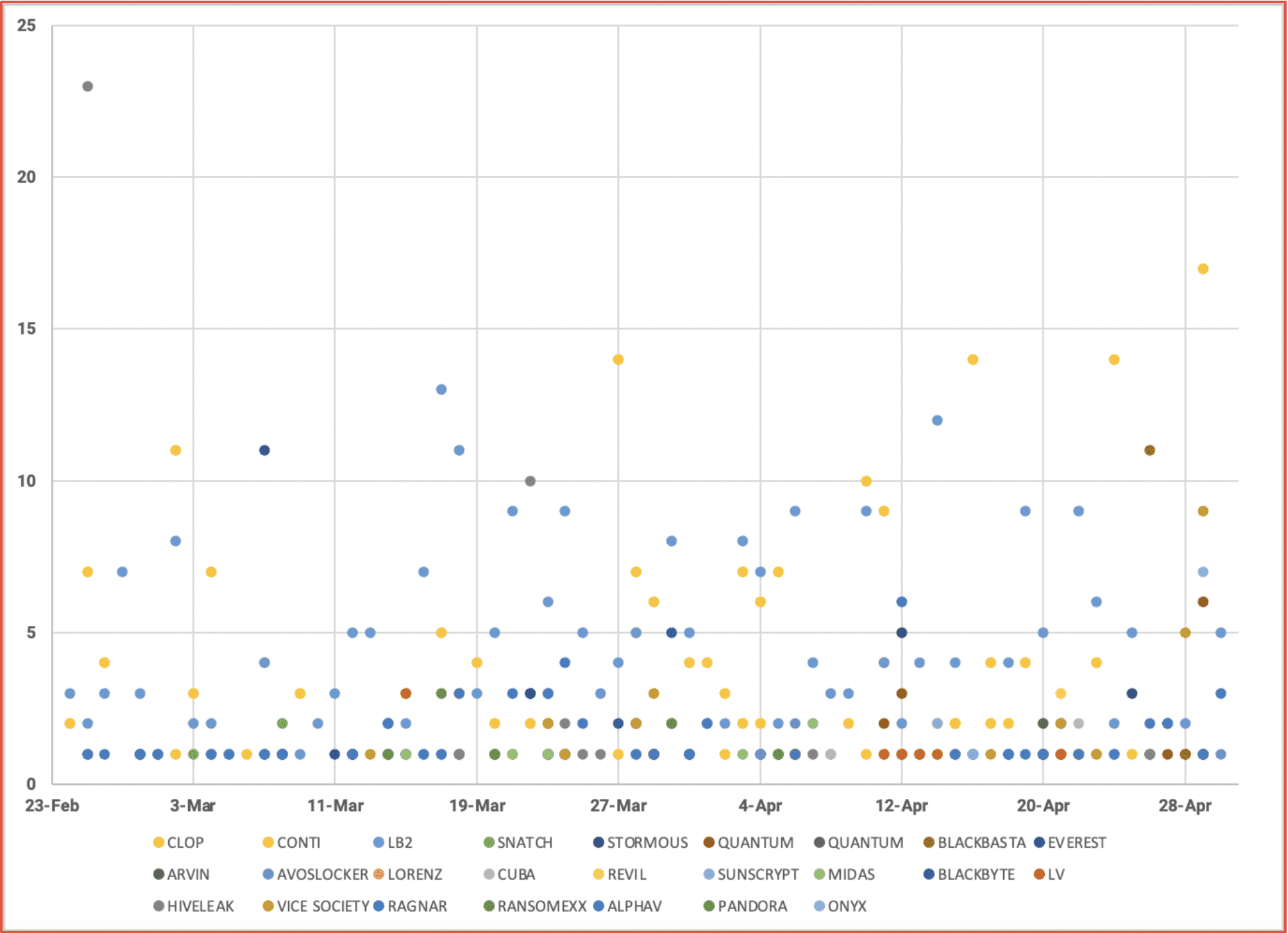
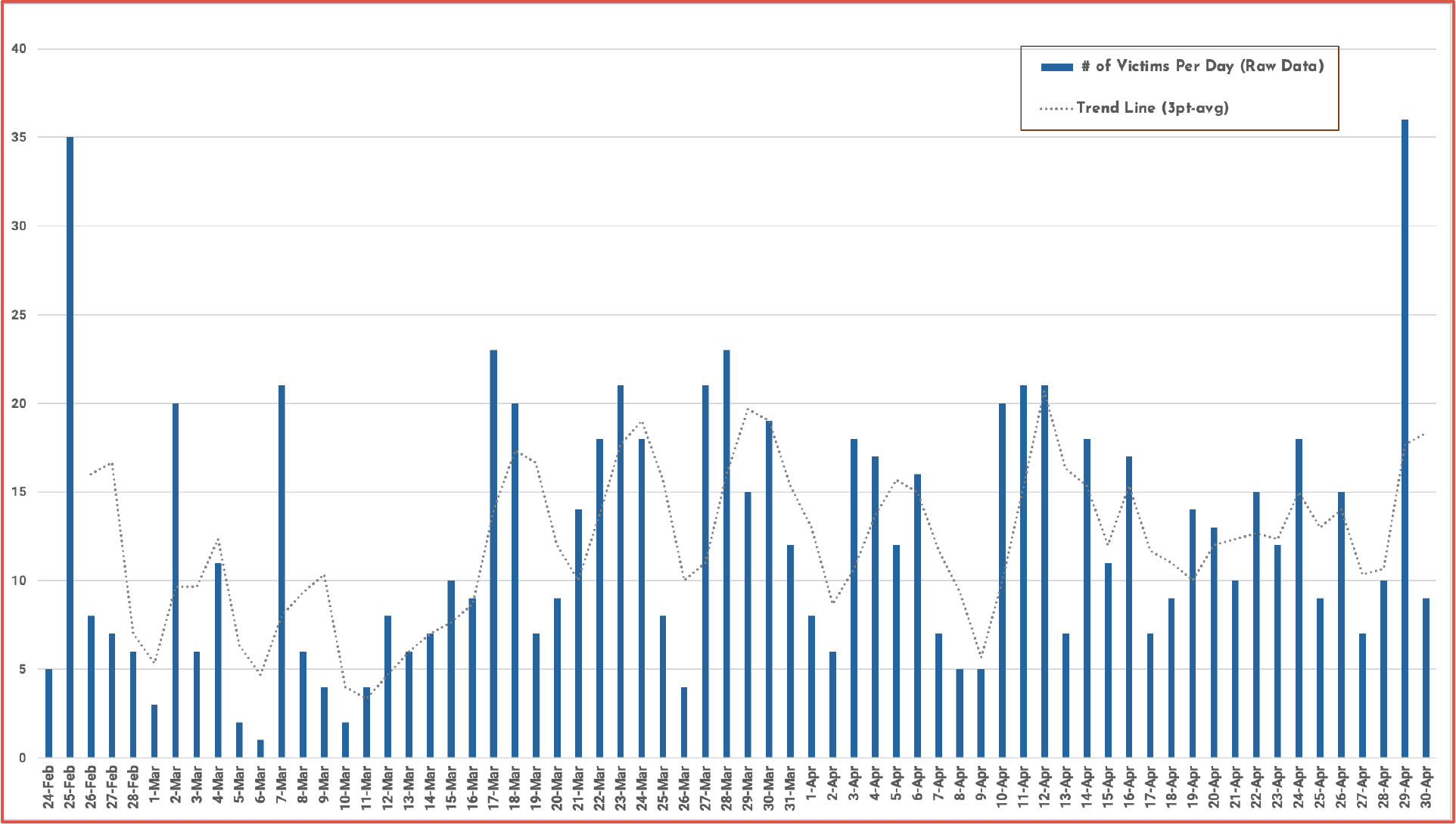
Within days of the invasion, targeting and exfiltrated data from targets across Russia surfaced in the deep web. DarkOwl has been monitoring mentions and announcements of data leaked in relation to the since the start of the cyberwar and found hundreds of leaks related to numerous government and commercial industrial sectors across Russia, Belarus, and China. The chart below demonstrates the volume of unique URLs observed containing information related to the war. In the early days, much of the leaked information contained network reconnaissance information (IP addresses, domains, credentials) for carrying out attacks against critical targets, and PII for government, military, and citizens of Russia.
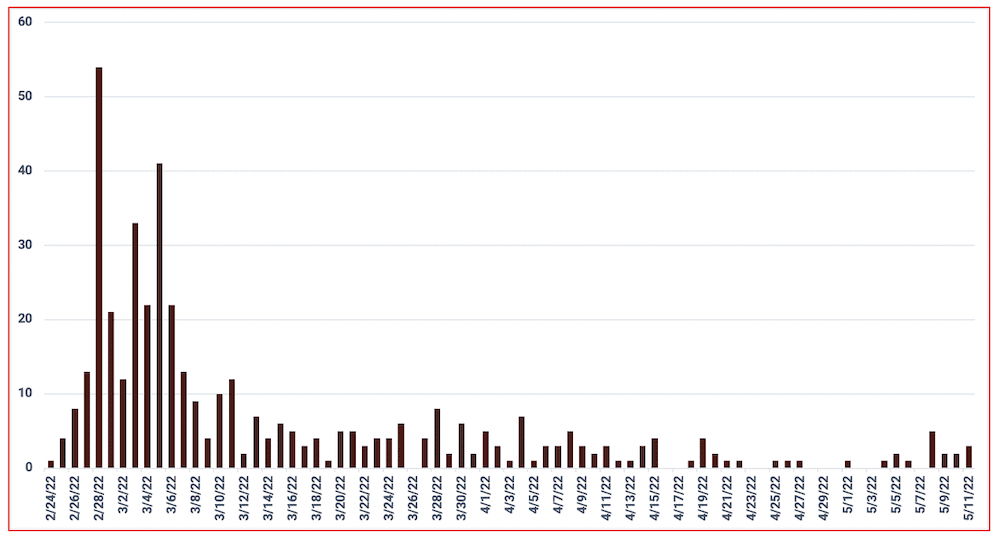
Figure 6: Distribution of Daily Data Leaks Related to Global Cyberwar
As the war progressed, stolen data of all kinds, e.g. intellectual property, design schematics, military plans, financial account data, and emails appeared. While in recent weeks the number of unique leaks are fewer, the contents contained therein are higher volume and significant in value. For example, over the last two weeks, Anonymous has released – via DDoSecrets – over 3TB of data archives containing thousands of emails and sensitive internal documents from victim organizations across Russia.
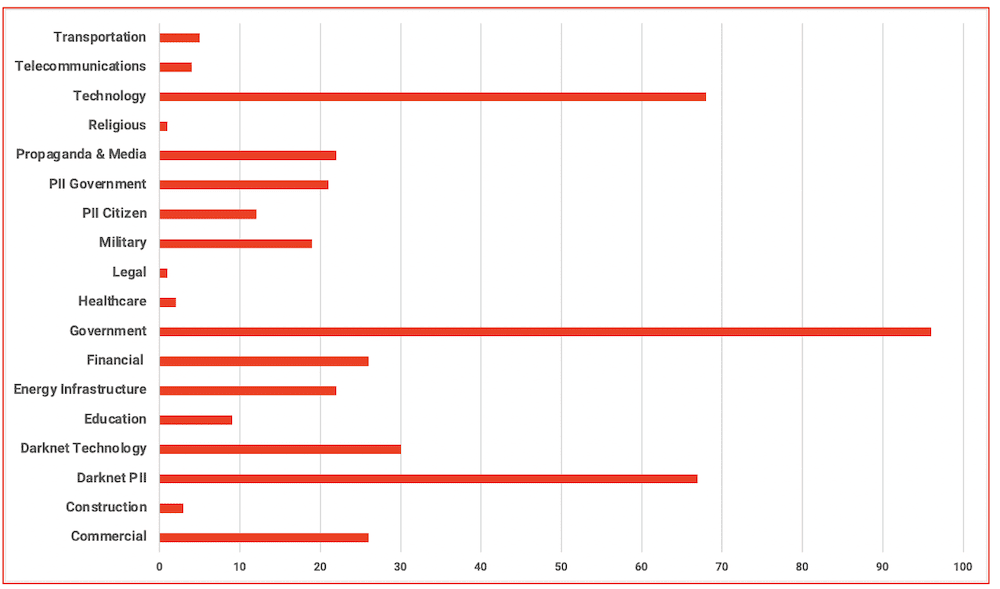
Figure 7: Distribution of Data Leaks from the Cyberwar by Industry Sector
Nearly 90% of the leaks DarkOwl has observed are related to targets in Russia. The figure below is a distribution of the non-Russian countries information that has surfaced, with direct mention of the cyberwar. The threat actor group, AgainstTheWest (ATW) concentrated on technology, government, and financial targets across China in the weeks following the invasion. ATW has since stopped participating in the campaign.
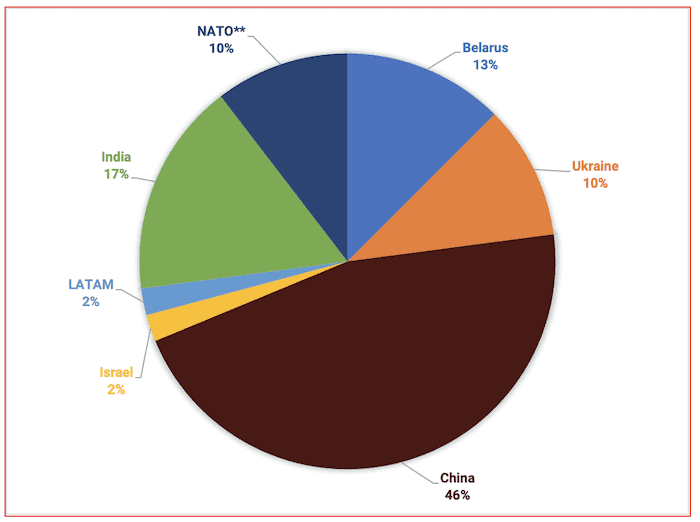
Figure 8: Percentage of non-Russian Data Leaked with Direct Mention of Global Cyberwar
Russia’s Response Takes Many Forms
Readers should not be fooled into thinking that this data means that Russia is sitting back idly during these attacks. In addition to the crippling Viasat attack the day of the invasion and widespread propaganda dissemination, GRU-affiliated cyber actors have regularly attacked Ukrainian telecommunications and critical infrastructure alongside its ground-based offensives. Elon Musk also recently stated that Starlink satellites in use by the Ukrainian government for Internet broadband access is under frequent targeted signal jamming by Russian-linked hackers.
State-sponsored malicious cyber actors, ransomware and affiliated extortion groups linked to Moscow continue to spray US and western European companies with widespread spear-phishing attacks and malware deployment. During our recent review, we estimate ransomware gangs successfully encrypt on average a dozen organizations per day.
DarkOwl will continue to monitor the darknet and deep web for critical information pertaining to the quickly evolving cyber landscape.












![Chat where RaidForums moderator, moot, locked the chat and Jaw suggested rf[.]to would be the new domain for future RaidForums operations.](https://www.darkowl.com/wp-content/uploads/2022/04/Screen-Shot-2022-04-04-at-4.41.02-PM.jpg)