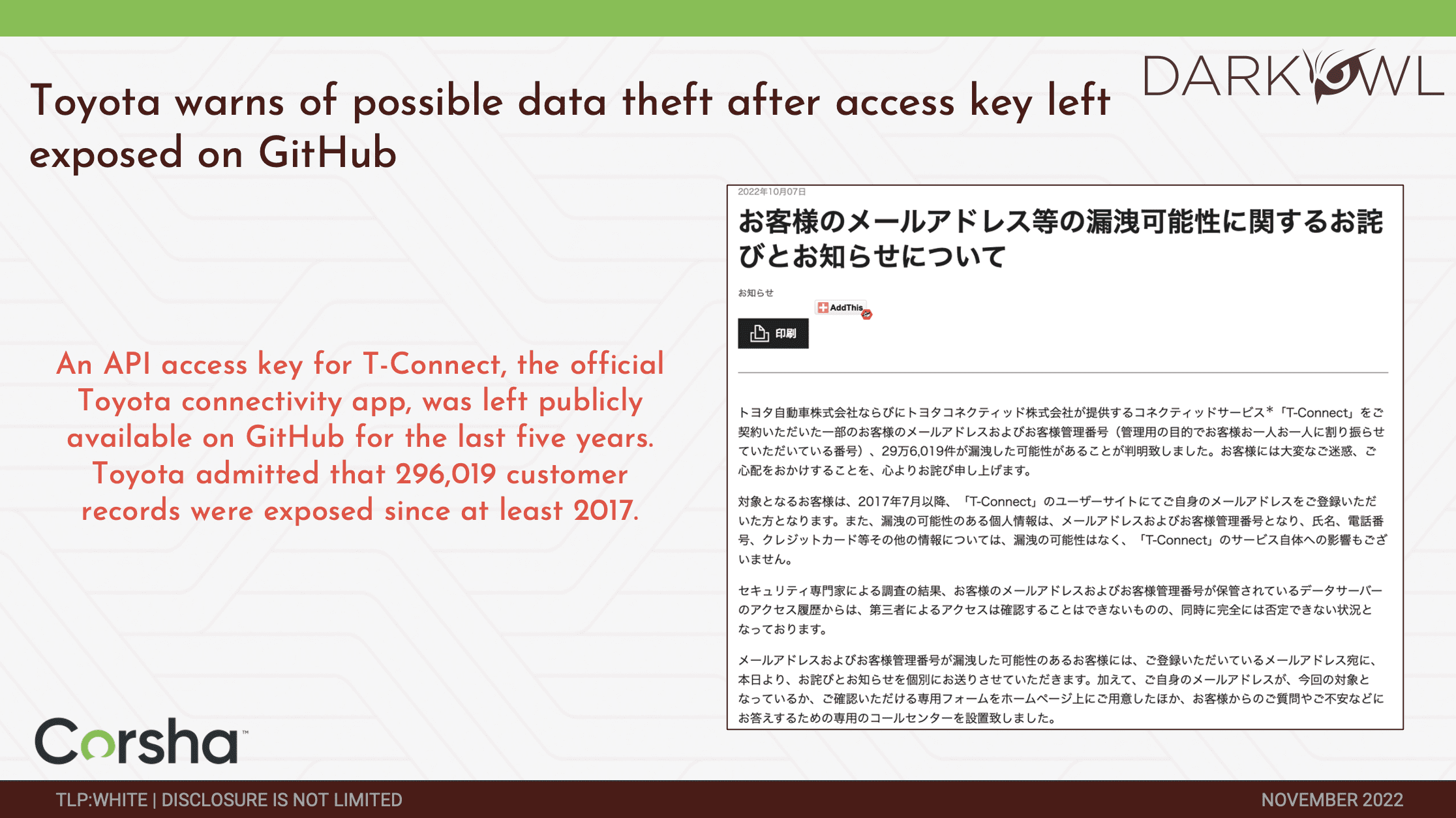
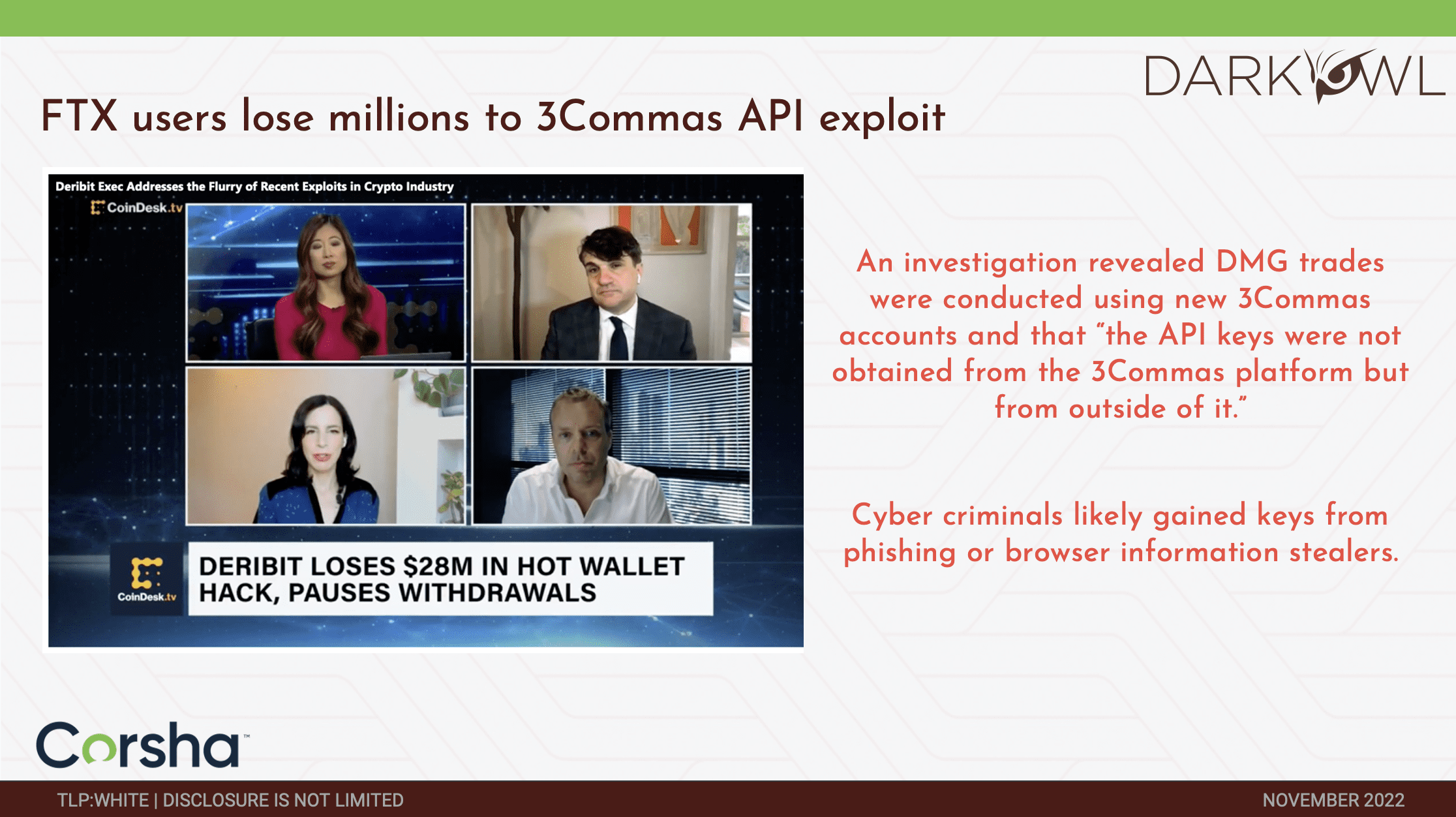
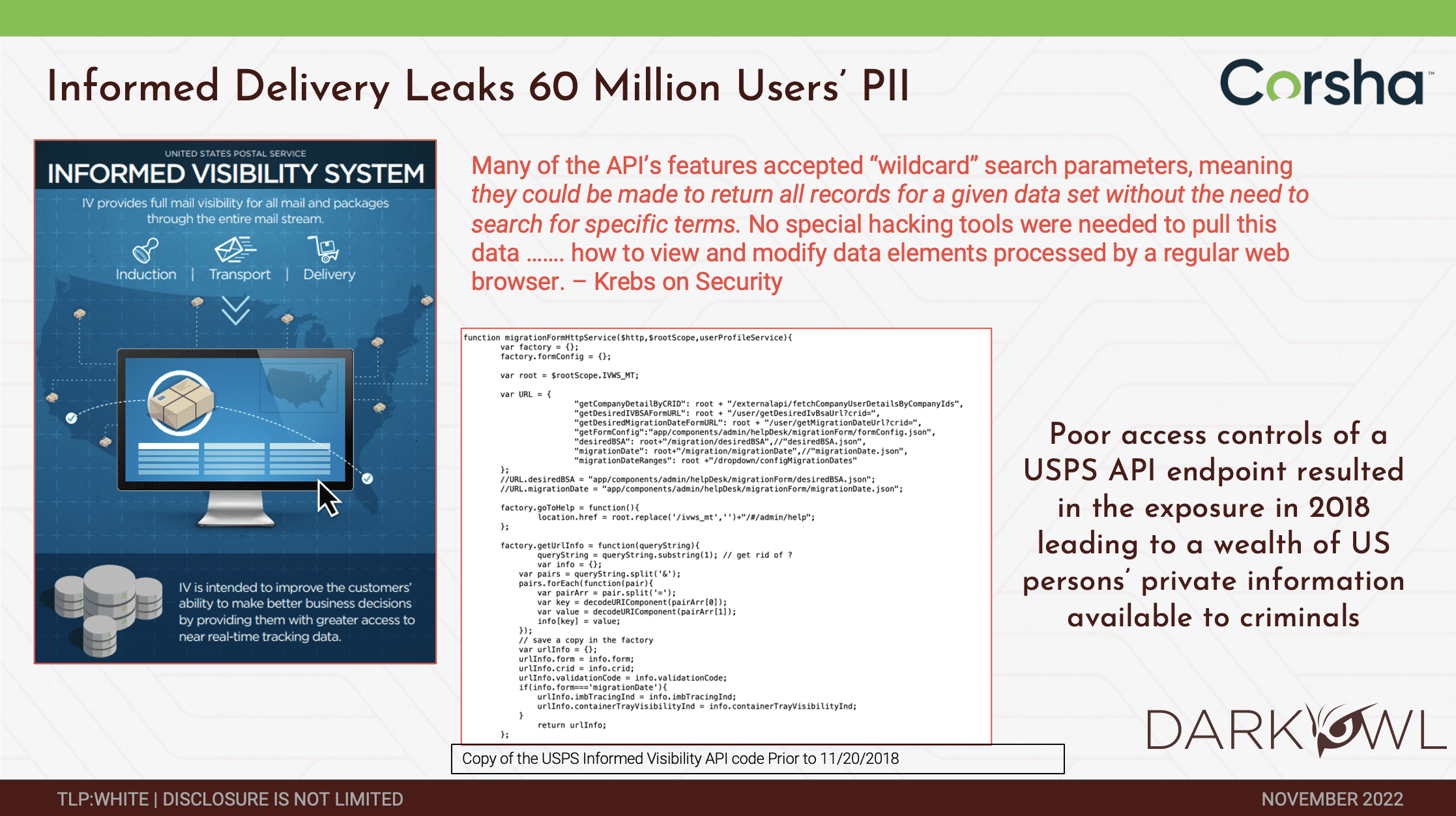
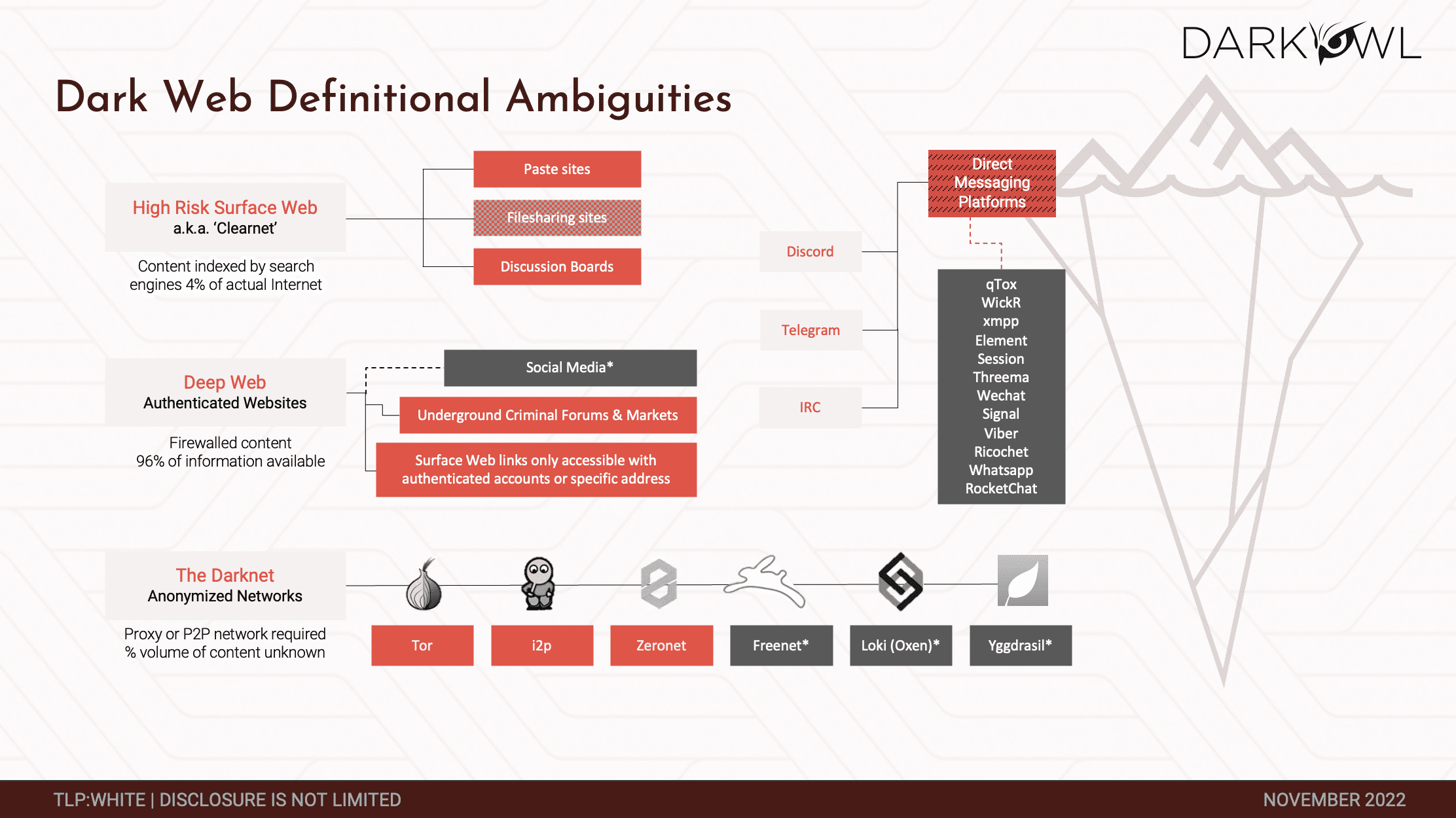
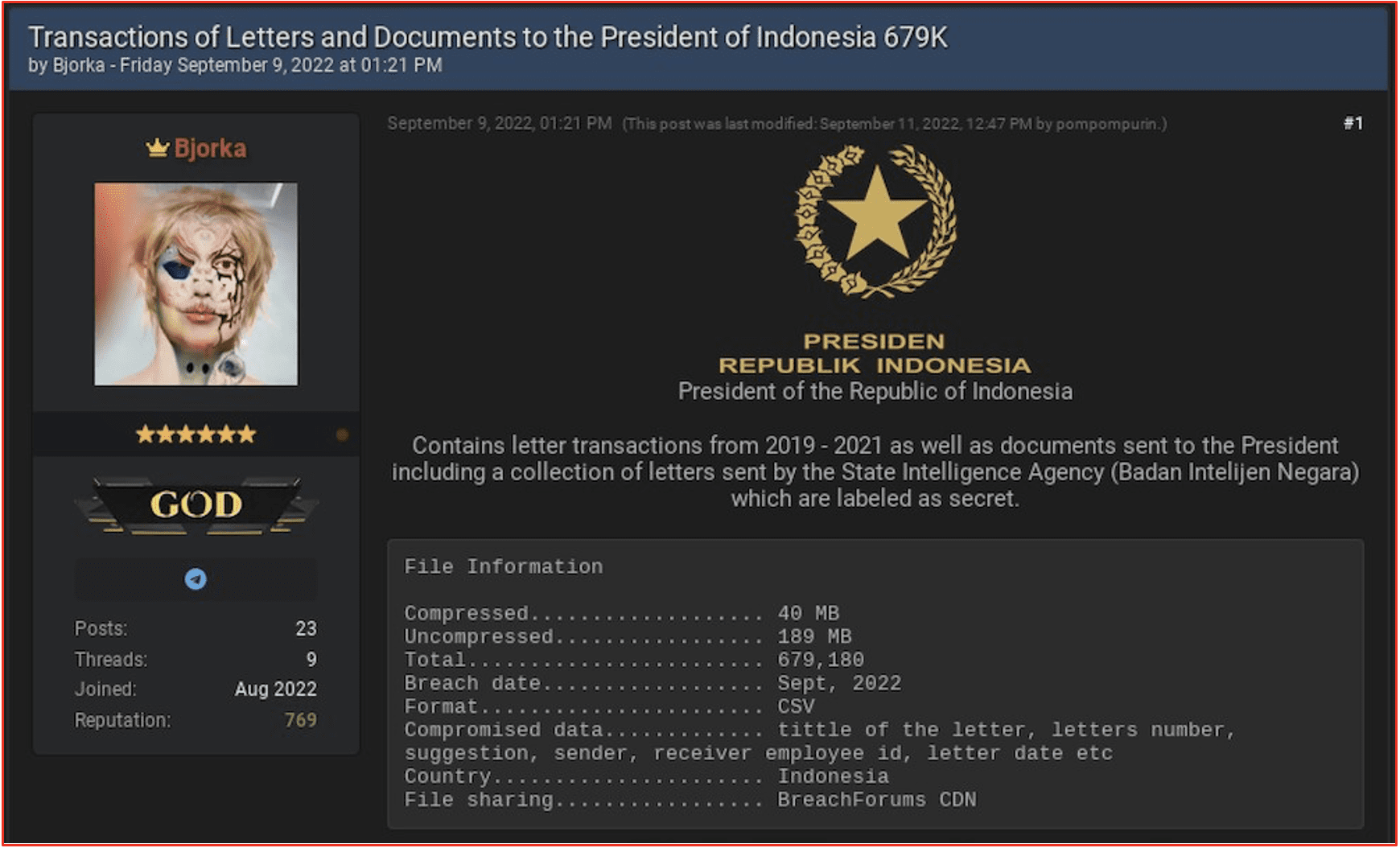
Darknet Marketplace Snapshot Series: OMG!OMG! Market
November 22, 2022
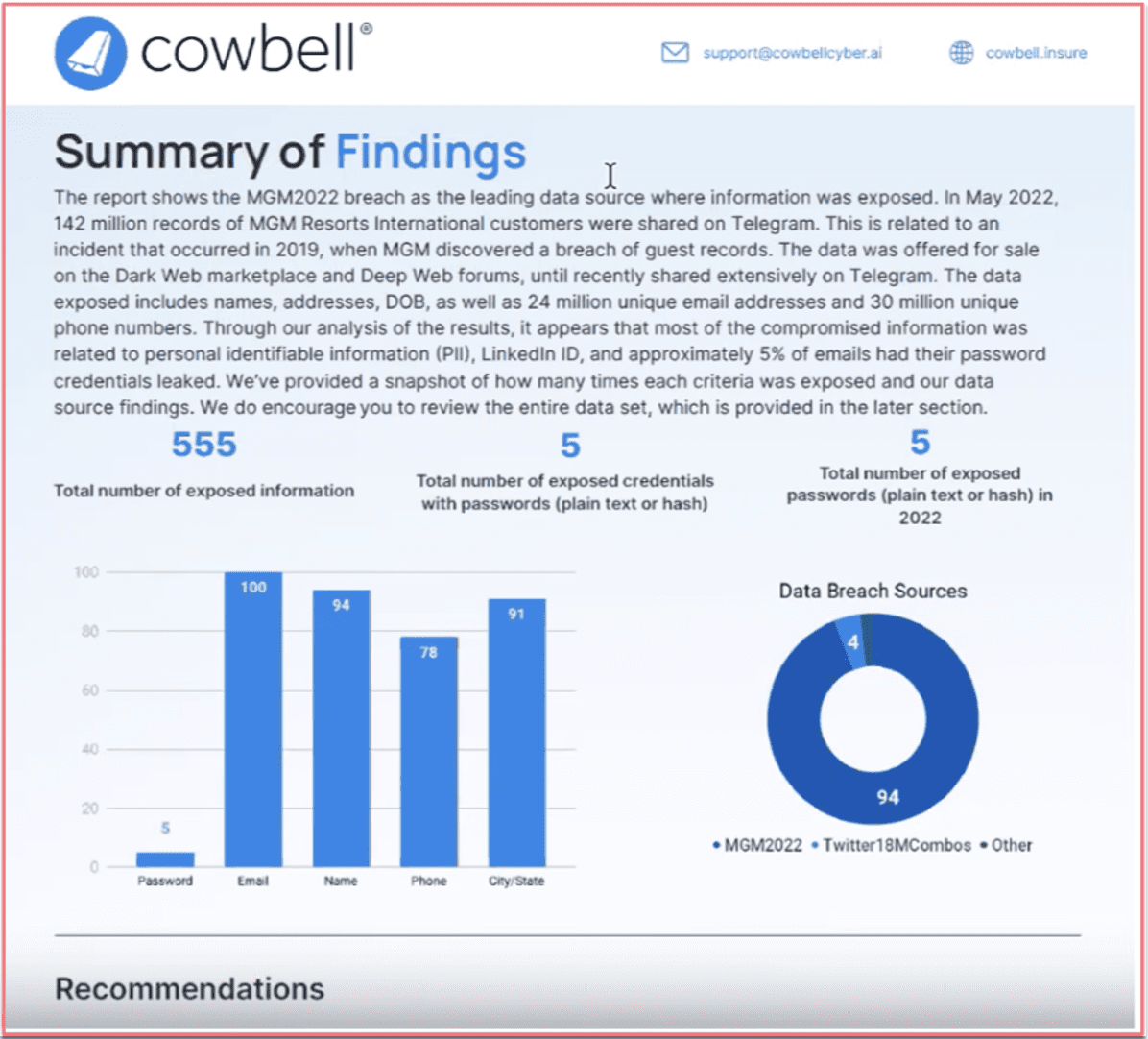
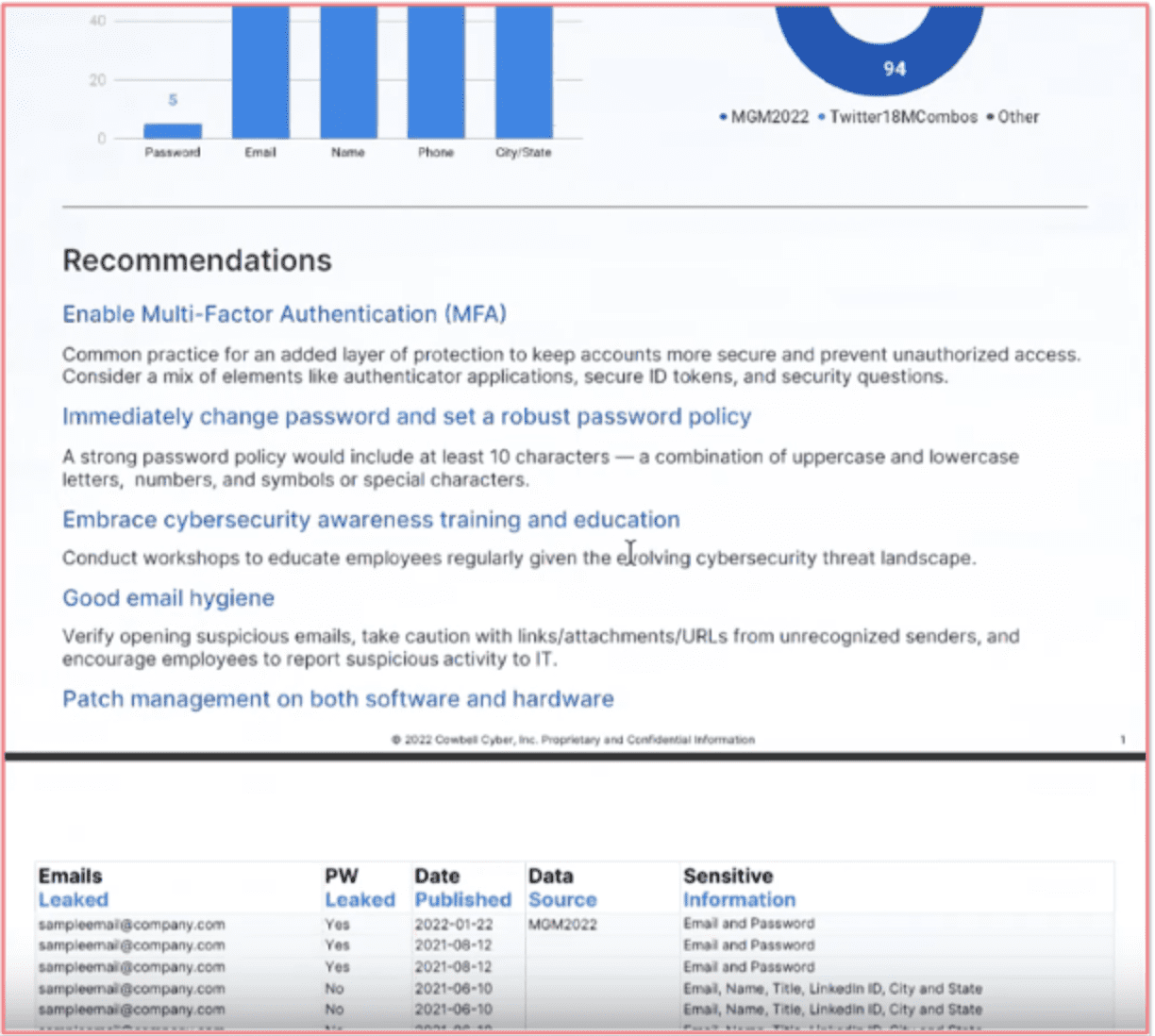
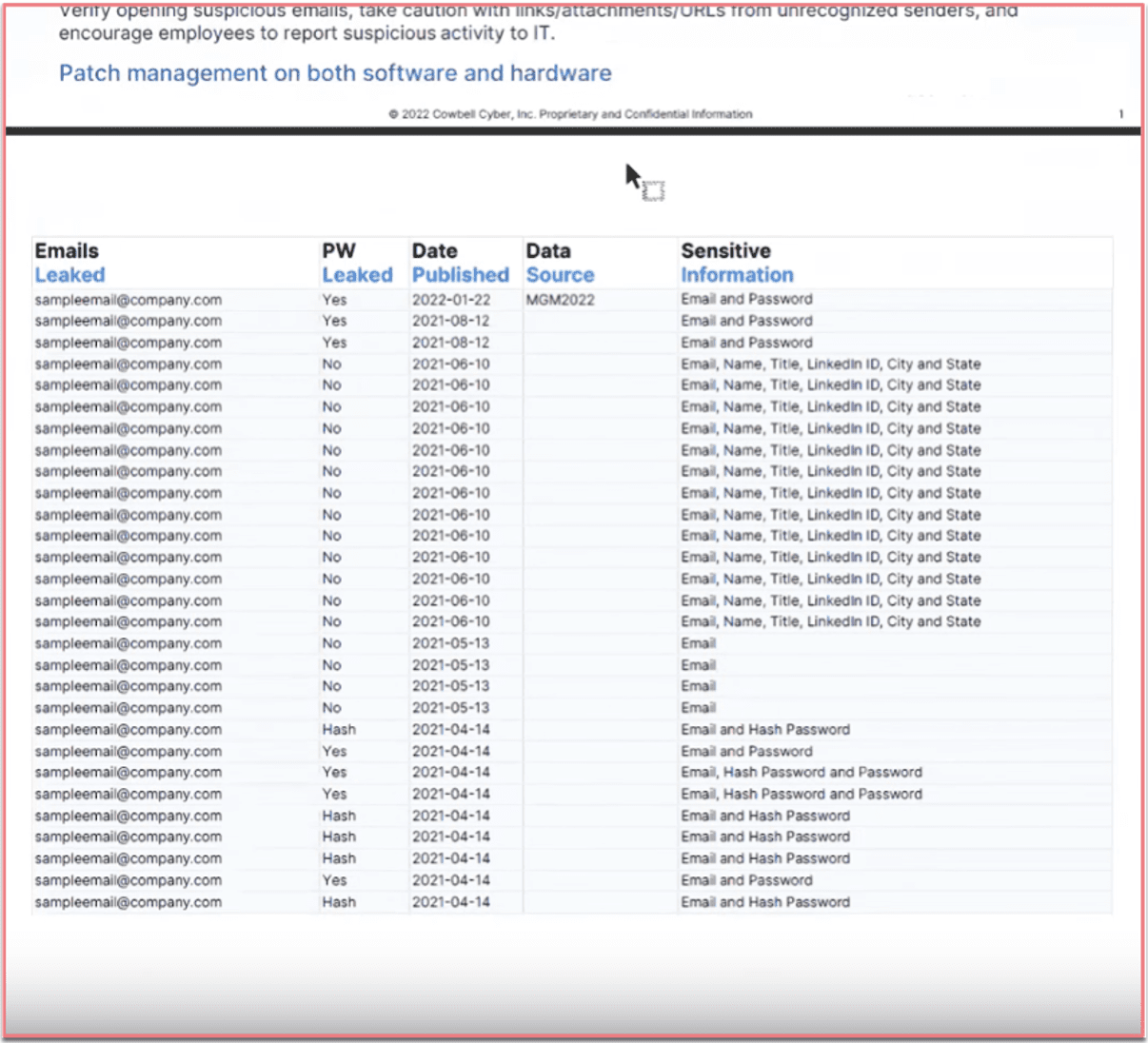
In DarkOwl’s Darknet Marketplace Snapshot blog series, our researchers provide short-form insight into a variety of darknet marketplaces: looking for trends, exploring new marketplaces, examining admin and vendor activities, and offering a host of insights into this transient and often criminal corner of the internet. This edition features OMG!OMG! market.
Don’t forget to subscribe to our blog at the bottom of this page to be notified as new blogs are published.
OMG!OMG! Market: An Intro
OMG!OMG! market is a large Russian-based decentralized darknet marketplace that this year has been elevated as a ‘Premium Darknet Drug Market’ following Hydra’s seizure in April of 2022. Recently, DarkOwl has observed the market being mentioned more frequently in drug-trade related discussions and advertisements on Russian forums. Many of the vendors on OMG!OMG! were active for years on Hydra, once again showing that although a marketplace is seized, the illicit trade shifts elsewhere and continues.
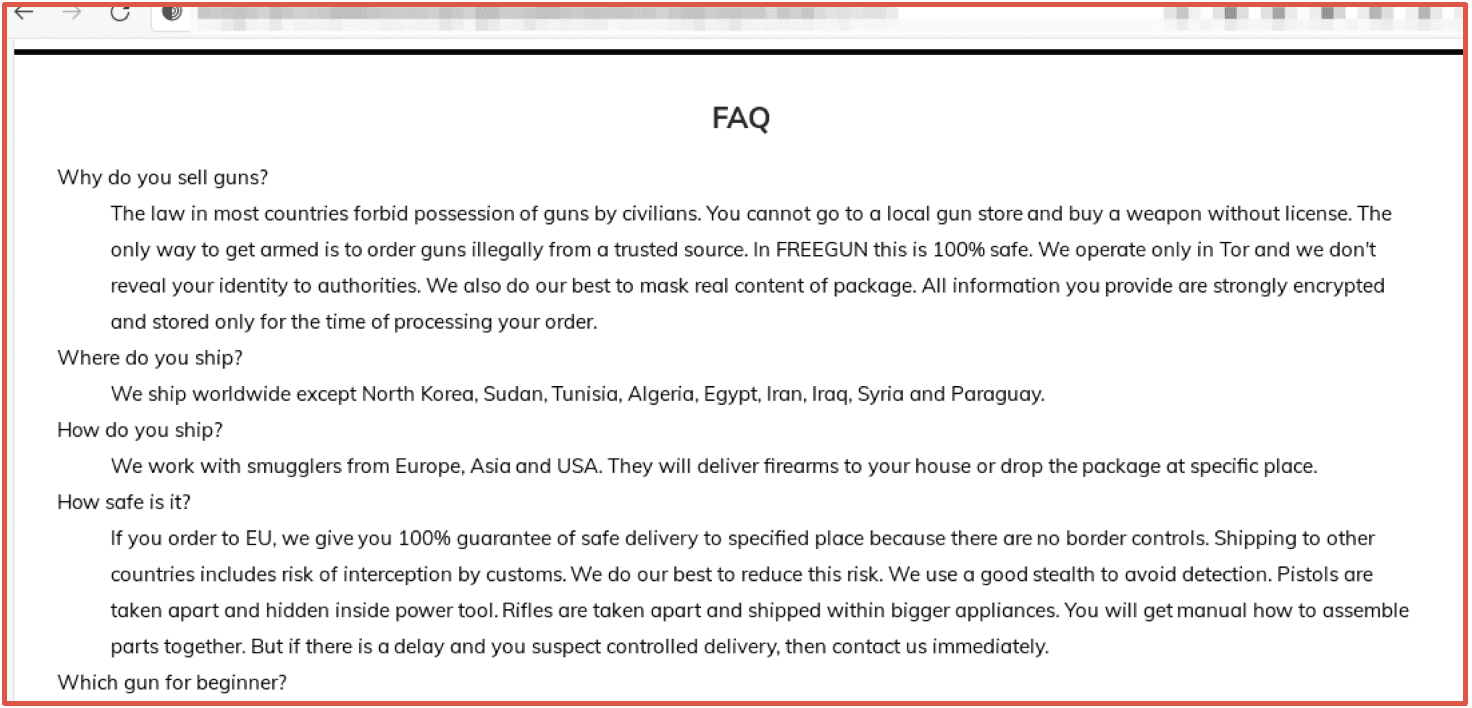
To access the marketplace on the Tor network and view vendor’s offerings, market visitors must solve a number and text-based captcha.
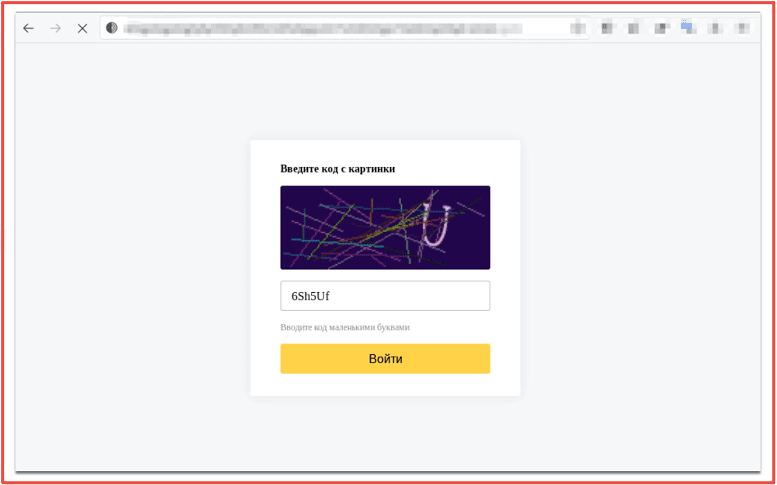
Figure 1 OMG!OMG! Marketplace Landing Page (pre-authentication) Source: Tor Anonymous Browser
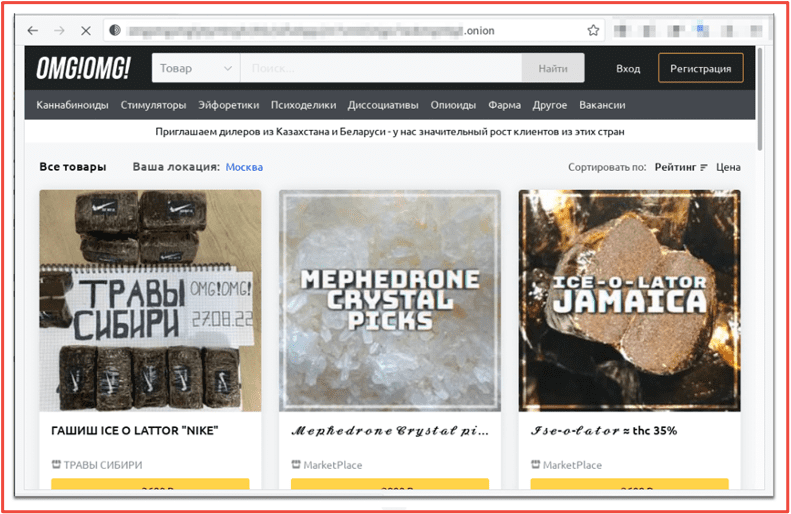
The landing page for the marketplace lists the daily exchange rates for Bitcoin and offers the site in both English and Russian. Users can also change the language of the site by clicking on the corresponding flag icons. The look and feel of OMG!OMG! market is very similar to Hydra, with the market’s logo on the top left, search bar in the center, and image-linked vendor shops arranged in a table on the main page.
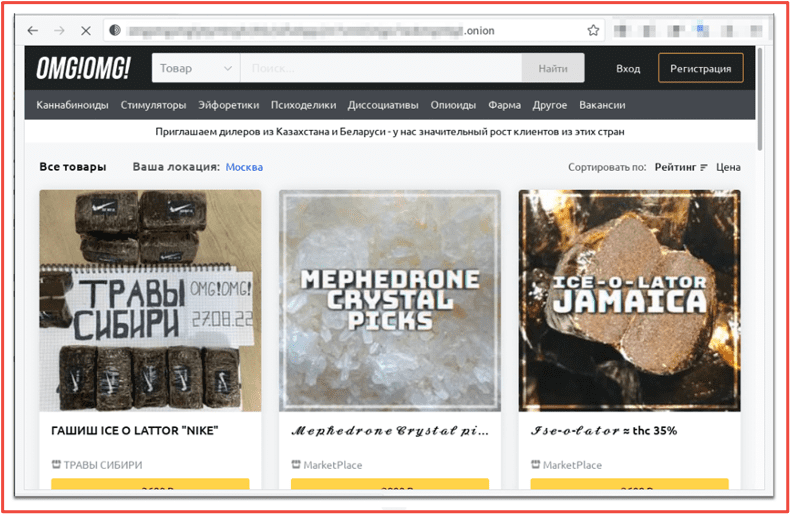
Figure 2 OMG!OMG! Marketplace Landing Page Source: Tor Anonymous Browser
Unique Characteristics of OMG!OMG! Marketplace
OMG!OMG! market shares characteristics that many other darknet marketplaces have; however, there are additional unique qualities that make this marketplace stand out.
Like most other marketplaces, Bitcoin is the only currency accepted and an ESCROW payment system is utilized. Users must have an account and money deposited in their Bitcoin wallets on the market to contact the administrators. The site claims it updates the conversion rate between Bitcoin and Rubles every 15 minutes. The marketplace does not list the number of vendors or sellers. However, DarkOwl analysts noted that there are over 3,400 vendors advertising on the marketplace, but, not all of those shops may be active. Like some other darknet marketplaces, OMG!OMG! market has a forum connected to the market. However, this part of the site gives the translated error message: “This section is under reconstruction.”
For security and anonymity purposes the marketplace encourages all users to install a PGP key and to use two-factor authentication for accounts.
Each vendor selling within the marketplace displays the number of deals they have completed. Some vendors have a blue checkmark next to their shop nameas well, to indicate that they have been verified by the market’s administration. A selectable heart button is accessible in each vendor shop so that customers may “favorite” certain products.
What really sets OMG!OMG! marketplace apart is its unique ordering and delivery mechanisms. Once a user places an order, the delivery is primarily set by location. A user is prompted to select their location immediately when accessing the site’s landing page – which is as odd for a darknet market that is designed to promote anonymity. This location data allows for corresponding products and vendors with the same location as the customer’s the option of “instant transactions.” After a customer sets their location in the marketplace, they can look for products in the search bar that are able to be delivered to them by sellers nearby.
After customers pay, the vendors, or potentially their hired couriers, will physically hide the purchase like a drop (referred by vendors as “treasure”) around the customer’s geographic location. Finally, the customer will receive coordinates and photographs to find and collect their purchases.
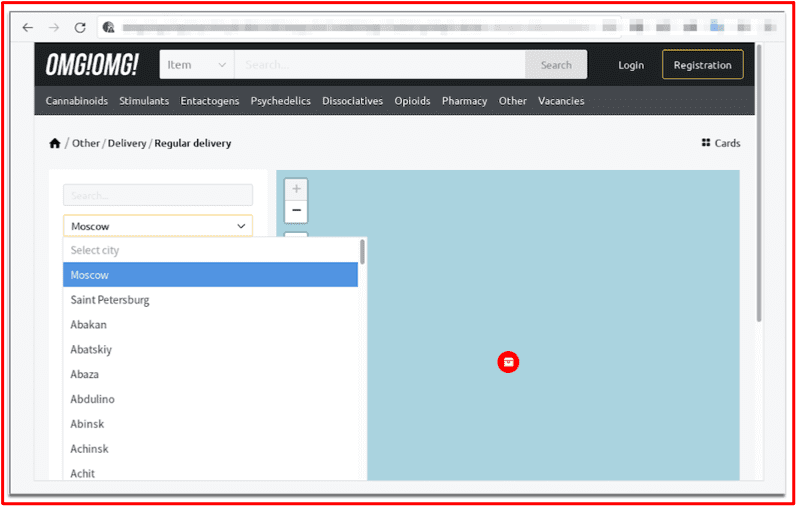
Figure 3 Regional Vendor Mapping from OMG!OMG! Market Source: Tor Anonymous Browser
There are three order options: instant, pre-order, and mail. An instant order, as described above, can be collected by the customer around their location right after they pay online. For a pre-order, the customer waits for confirmation from the seller until they transfer the item to a specified drop location. This takes more time but is customized and more secure than instant. Mail orders need to be confirmed by the seller and shipped by the seller via post or courier.
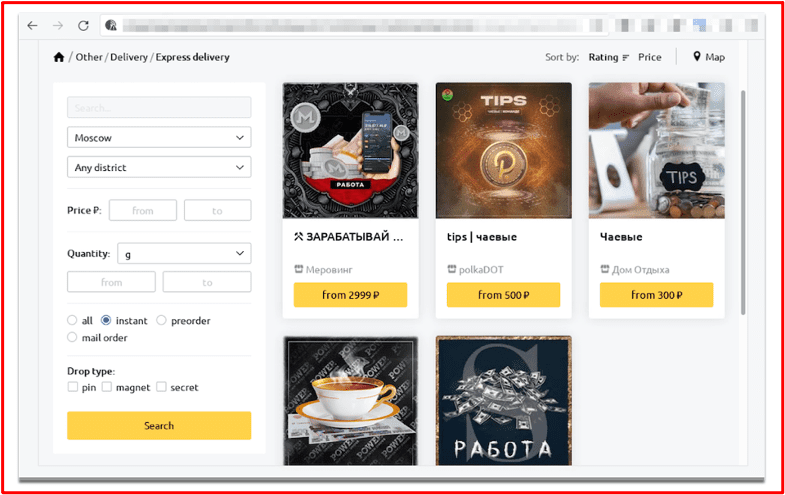
Figure 4 Regional Delivery Selection OMG!OMG! Market Source: Tor Anonymous Browser
There are also three different ways that instant delivery packages will be hidden to avoid possible interception or theft. DarkOwl extracted the excerpt below from the OMG!OMG!’s FAQ page; the original content was in Russian.
Editors note: We determined “bookmark” as translated by Google Translate means “delivery.”
[TRANSLATED IMAGE]
“There are 3 types of bookmarks – prikop, cache, magnet.
Prikop – the packed goods will be buried shallowly in the ground (possibly in the snow in winter). This type of bookmark provides sufficient reliability from the discovery of a treasure by an outsider, but it happens that it can be difficult to find such a treasure yourself.
Cache – a packaged item is disguised as a third-party item and left in a secluded place or just on the street. Such treasures are often quite easy to remove, the reliability of detection by strangers can be different and depends on the masking.
Magnet – the packaged product is attached to a metal surface in a place inaccessible to a direct view. Usually such treasures are very easy to shoot, but there are not very many reliable places for them.”
OMG!OMG! marketplace’s instant delivery features are built for those customers only residing in Russia, but vendors also deliver internationally such as to the United States and Europe. The marketplace advertises they support customers in and recruits dealers from the nearby Commonwealth of Independent States (CIS) countries:
“We invite dealers from Kazakhstan and Belarus – we have a significant increase in customers from these countries.”
OMG!OMG! Market: The Products
Drugs are by-far the most common good offered for sale on OMG!OMG! market. The categories of drugs advertised include: cannabinoids, stimulants, euphoretics, psychedelics, dissociates, opioids, and pharmaceuticals.
In addition to drugs, other common illicit goods, such as fraudulent documents, e.g. University diplomas, Russian passports, residence permits, driver’s licenses, letters from the internal Ministry of Affairs, etc., are available on the market. There does not appear to be products such as weapons or listings that are human-related. The “rules” portion of the market explains that shops including human trafficking or “renting” shops are not allowed on the site.
DarkOwl analysts observed digital goods like bank accounts, Qiwi wallets, and SIMs for sale in addition to source code and software, such as Telegram bots.
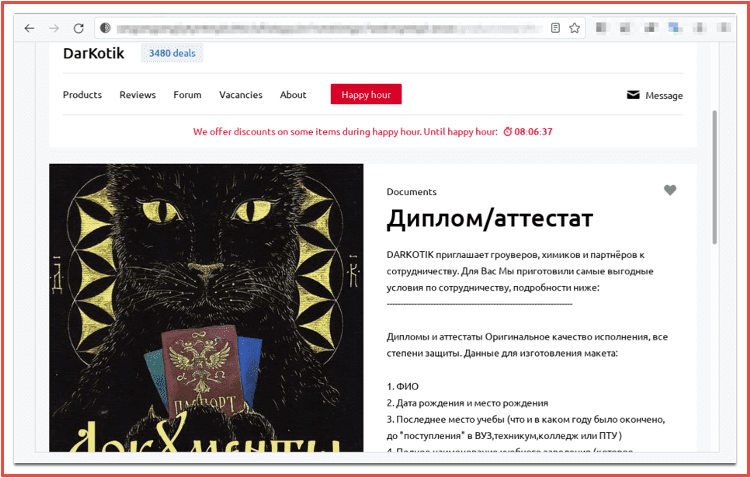
Figure 5 a fraudulent university diploma from OMG!OMG! source: Tor Anonymous Browser
[TRANSLATED IMAGE]
“Diplomas and certificates original workmanship, all degrees of protection. Data for the layout:
1. Name
2. Date of birth and place of birth
3. Last place of study (what and in what year was completed, before “entering” a university, technical school, college or vocational school)
4. Full name of the educational institution (which needs to be made)
5. Specialty
6. Years of study
7. Form of study
8. Approximate estimates (possible as a percentage)
9. Degree for universities (specialist, master or bachelor)
10. Full name, address, and phone number of the recipient (Required, this information is needed for the courier service to make delivery)
11. if there are any samples, then attach them too
Strictly on the points on the layout, check all the points carefully. After its coordination and approval, the document goes into production, where it will be impossible to correct errors! Manufactured and shipped within 3 working days
More than 5 years on the market! Over 150,000 trades on Hydra.”
The translated advertisement above includes the volume of trades the seller had on Hydra market to establish reputation on OMG!OMG! The OMG!OMG! market administrator added a light blue banner by the seller’s name to indicate the number of deals completed on OMG!OMG! for additional creditability. In this case, the vendor DARKOTIK has had amassed several thousand transactions (3,480 total). Many of the drug listings offer detailed information about the products.
Some include direct quotes of buyers’ experiences:
[TRANSLATED IMAGE]
Ecstasy users describe their internal state usually as euphoria, intimacy and closeness to other people – “all people are my friends”; a feeling of “flying, endless happiness, high sensitivity.”
Users who purchase products can provide feedback ratings on quality, delivery, and service on a scale from 1-5 to further establish vendor credibility. The veracity of the information posted is unclear and could easily be falsified.
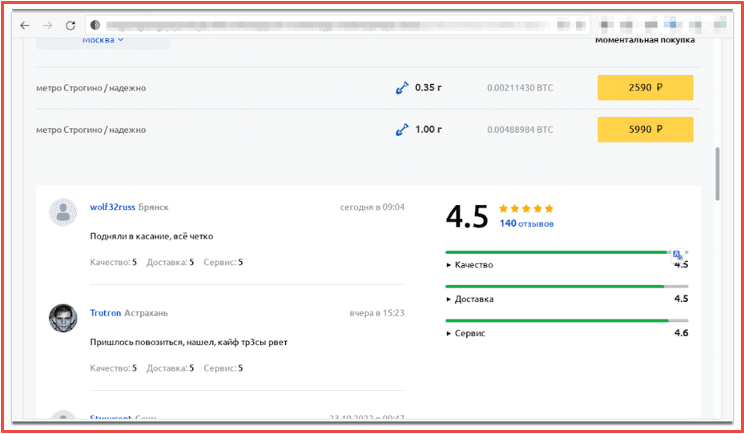
Figure 6: Diamond product review OMG!OMG! Market source: Tor Anonymous Browser
Some vendors with drug listings have an additional information button next to the product listing. Following this link provides in-depth information for estimated dosage, preparation methods, and description and duration of the product’s effects.
Another category not common with other darknet decentralized marketplaces is job opportunities. This section includes options to apply for commercialized drug distribution supporting roles such as: Pawnbroker, Stock, Carrier, Manager, Chemist, and Grower.
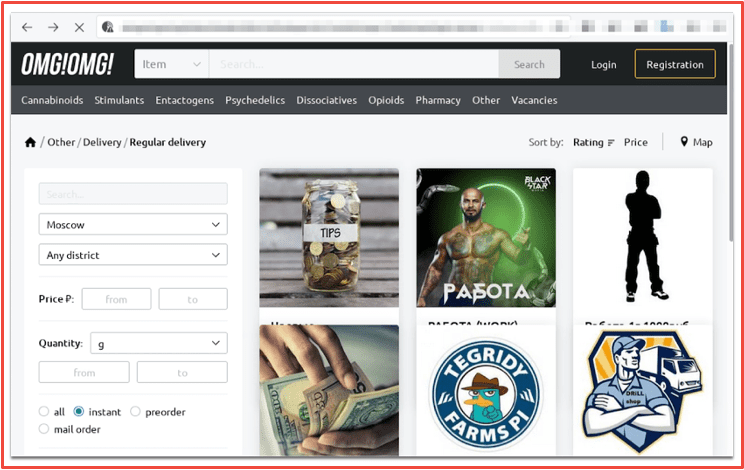
Figure 7: work opportunity listings on OMG!OMG! Market Source: Tor Anonymous Browser
Below is a translated description for a job listing advertised on OMG!OMG market:
[TRANSLATED IMAGE]
We are glad to welcome you to “Black Star Mafia”, the fastest growing shop on the site! Due to recent events, many of us have lost our jobs and, consequently, our means of subsistence.
Experience is not required, we teach from A to Z all the subtleties of conducting shadow activities for your successful and safe development, a manager is assigned to you, someone who will guide you by the hand to the result throughout the entire journey, and will help you at a difficult moment to lighten your burden, reduce all the difficulties are gone.
For communication, write to us in the PM of the store, we answer around the clock!”
These work advertisements are likely to keep up with the premise of the marketplace that they will deliver directly to you if you are in Moscow.
OMG!OMG! Market: Across the Darknet
OMG!OMG! has been advertised extensively on other popular Russian darknet forums and markets, like Rutor. Many of the vendors active on the marketplace transact across multiple darknet markets including Alphabay, Nemesis, and Narnia.
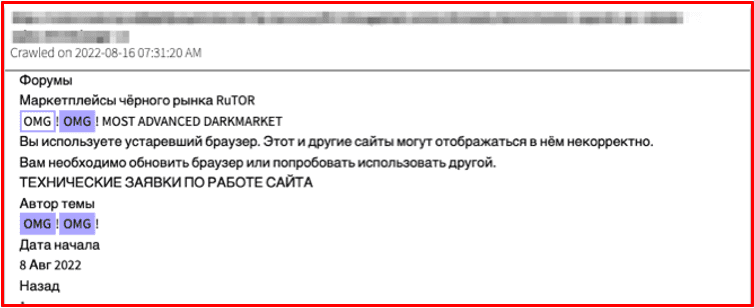
Figure 8: OMG!OMG! Market on Rutor Source: DarkOwl Vision
DarkOwl has not identified any functional mirrors of the site. The site itself claims that “any other sites, projects, mirrors, etc. have nothing to do with us and are scammers.” Some of the vendors present on OMG!OMG! marketplace have built out their professional operations across the darknet.
One vendor, known as Black Star Mafia, appears to have been involved in drug sales on the darknet for years. They have also been mentioned on Wayaway. A post crawled by DarkOwl Vision in 2018 identified Black Star Mafia in a forum advertising amphetamines in a discussion thread also mentioning coordinates, similar to how instant transactions work on OMG!OMG!
Another post, crawled by Vision in 2019 from an onion site, also identifies Black Star Mafia as a drug dealer and promotes the professionalism and experience of their hoarders. In this instance they are responding to a dispute over a product order and are outlining the requirements necessary for the dispute.
The administration of OMG!OMG! market is designed to moderate and intervene if there is a dispute between vendors and customers. The rules section of the site details that the names of Administration accounts are highlighted in red.
The use of PGP keys and 2FA mentioned earlier may at some point may have caused difficulties for the vendors. Posts crawled by DarkOwl Vision detail vendors having issues with enrollment, having funds correctly credited to accounts, and 2FA. A string of posts in a discussion thread sees multiple vendors on OMG!OMG! market describing issues they are having on the market, with some of them commenting at “WD” to intervene. After multiple vendors discussed issues they were having with 2FA and enrollment on OMG!OMG! one commenter wrote:
“WD Don’t you think it’s a seam project and nothing more? Solve the issue in coordination with this site. How many people will suffer before you make the right decision?”
There was also some doubt cast on whether the admin of OMG!OMG! still had control over their account and access to the PGP key. Someone repeatedly brought up issues with 2FA and the market admin responded that it was temporarily out of order and would be fixed soon. After issues were not resolved, vendors questioned if they still had access to their accounts. A self-identifying OMG!OMG! admin responded that they were still in control of their PGP key and promised to update the canary within 60 days and provided the latest Bitcoin hash. Later, another user in the thread pointed out that the admin was very behind with their promised updates.
“With this message, the site admin confirms that everything is fine with him, he did not fuck up his PGP key, and undertakes to update this message within 60 days. Only the date in the message 2021-07-13 is July 13, 2021, that is, this message was left 9 months ago, and already overdue by 7 months.
Either the admin is no longer an admin, or he blew the key, or simply forgot – in any case, these are serious arguments against the site – and in my opinion an official comment is necessary.
Are you pretending not to notice again?”
While researching and writing this piece DarkOwl analysts observed multiple days where the site was unavailable, which is likely a continuation of the general trend of widespread DDoS attacks against the Tor network. With Hydra out of the way, OMG!OMG! market could be poised for success or targeted to law enforcement intervention. Some of Hydra’s previous vendors appear to have made the migration to OMG!OMG!. However, the more successful a darknet marketplace grows, the larger of a target it can become to law enforcement efforts.
Additionally, prolonged issues with market access, vendors’ ability to access accounts, and discrepancies in money transferred and credited to accounts could all limit the use and retention of the marketplace by vendors and customers alike.
Subscribe to email to receive the latest research directly into your inbox every Thursday and don’t miss our next Darknet Marketplace Snapshot.
.