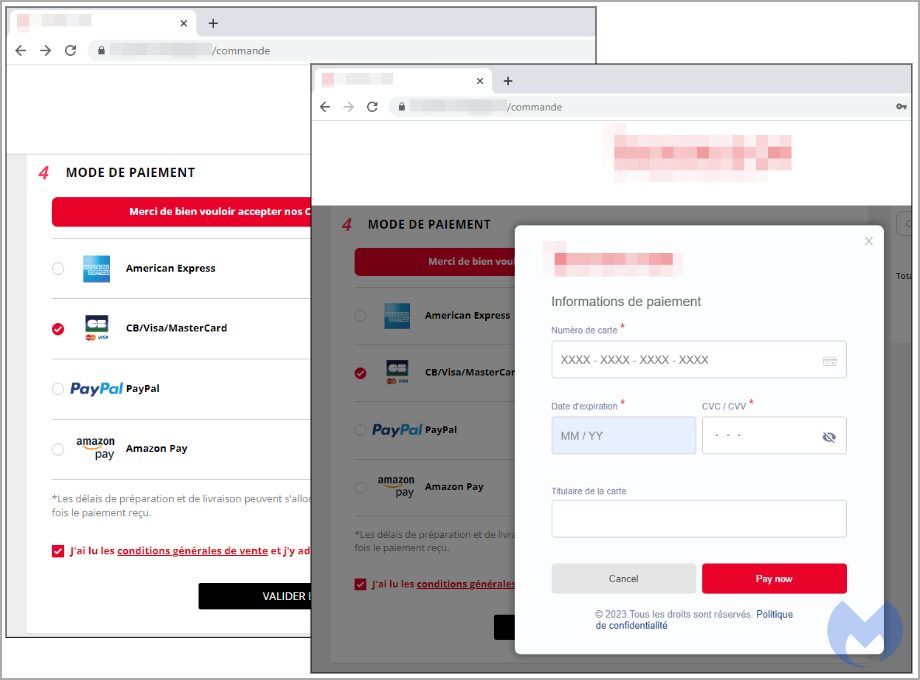
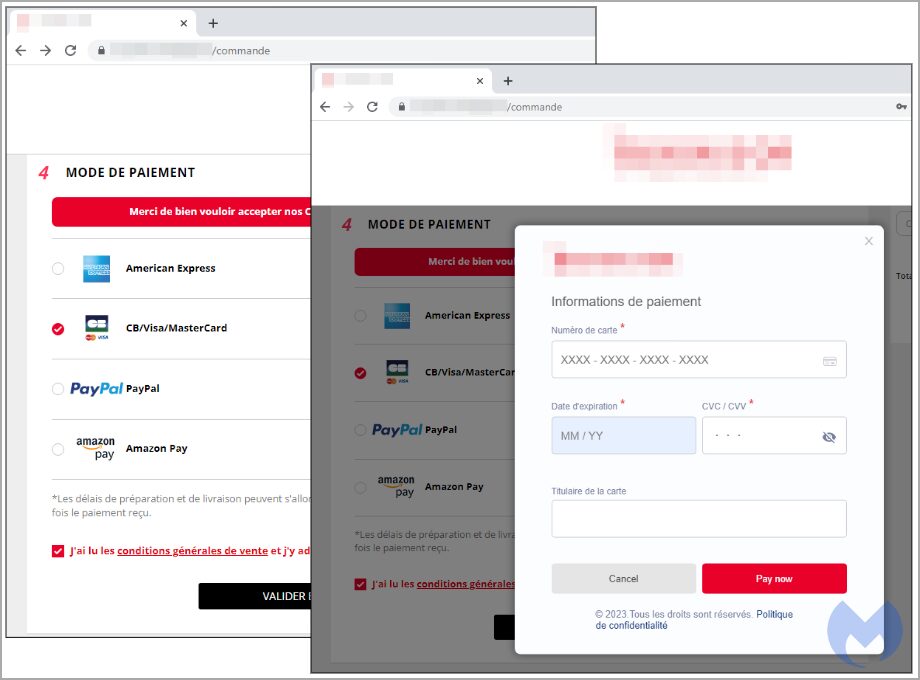
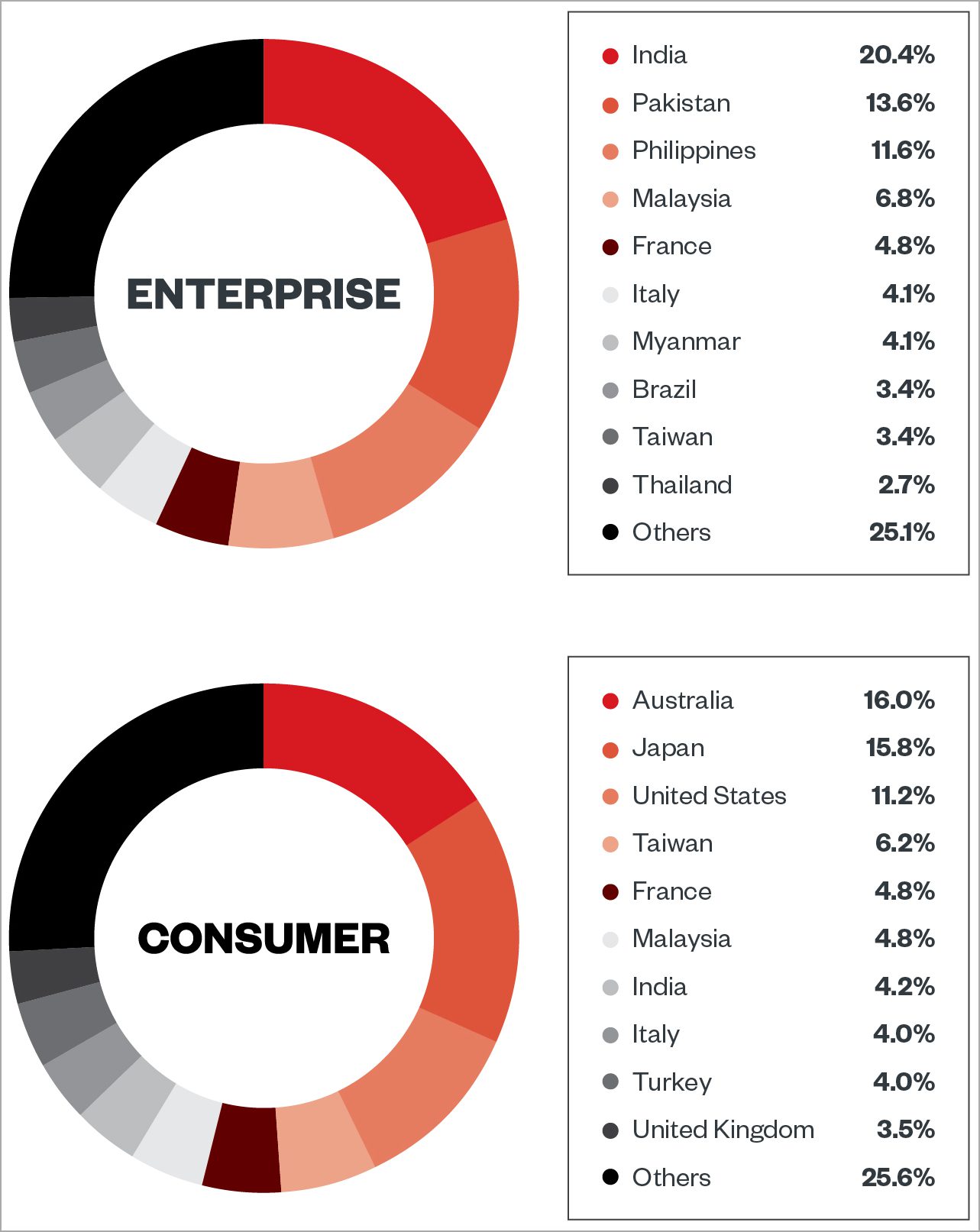
June 07, 2023
Alison Connolly Halland, DarkOwl’s CBO, and Andrew Bayers, Head of Threat Intel at Resilience, discuss the ways data is collected on the darknet and the tools protecting business information, on Building Cyber Resilience Podcast brought to you by Resilience.
What you’ll learn:
- The ways tools like DarkOwl use threat intelligence to improve resilience.
- The importance of having layers in your security strategy.
- Action steps for using darknet information for good.
For those that would rather read the conversation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity.
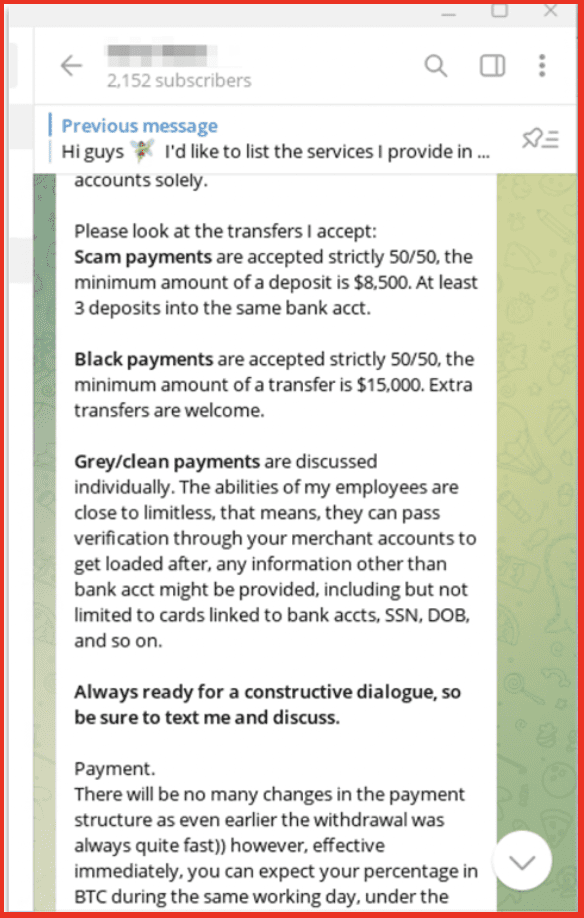
Alison: We searched for the organization’s email addresses that had been exposed. Those came up. There were plain text passwords associated with them for someone that was actually on the, on the call, which happens all the time. But the part that was embarrassing is their plane text password was not something you would want. My guess was they made it as a 17 year old teenage boy and hadn’t changed it yet.
Ann: Welcome to the Building Cyber Resilience Podcast by resilience. I’m Dr. Ann Irvine Chief Data Scientist and Vice President of Product Management.
Richard: And I’m Richard Seiersen, Chief Risk Officer.
Ann: That was DarkOwl’s Chief Business Officer, Allison Connolly Halland, at the top of the show sharing why it may be time to update your password if you haven’t changed it since high school. It’s because of her company’s innovations that her joke is just that and not a breach that destroyed a business.
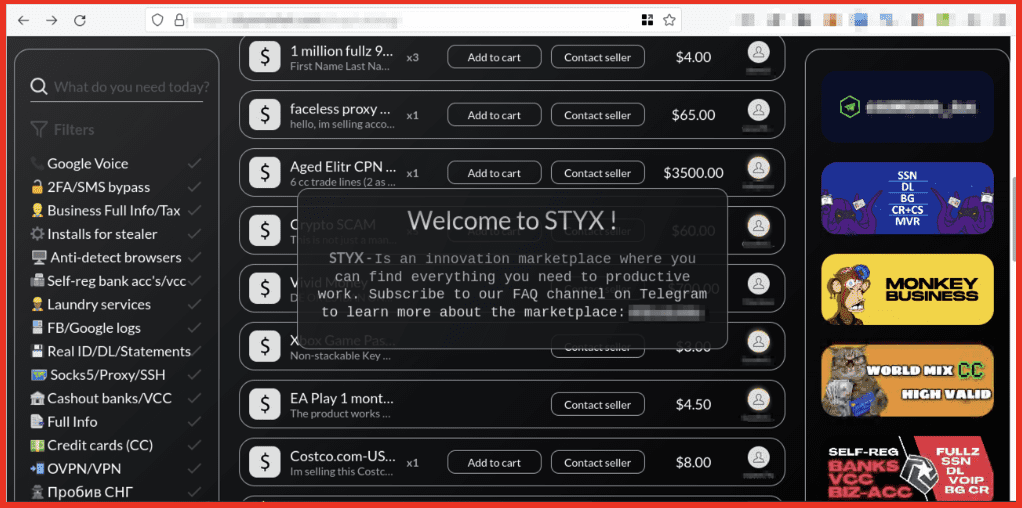
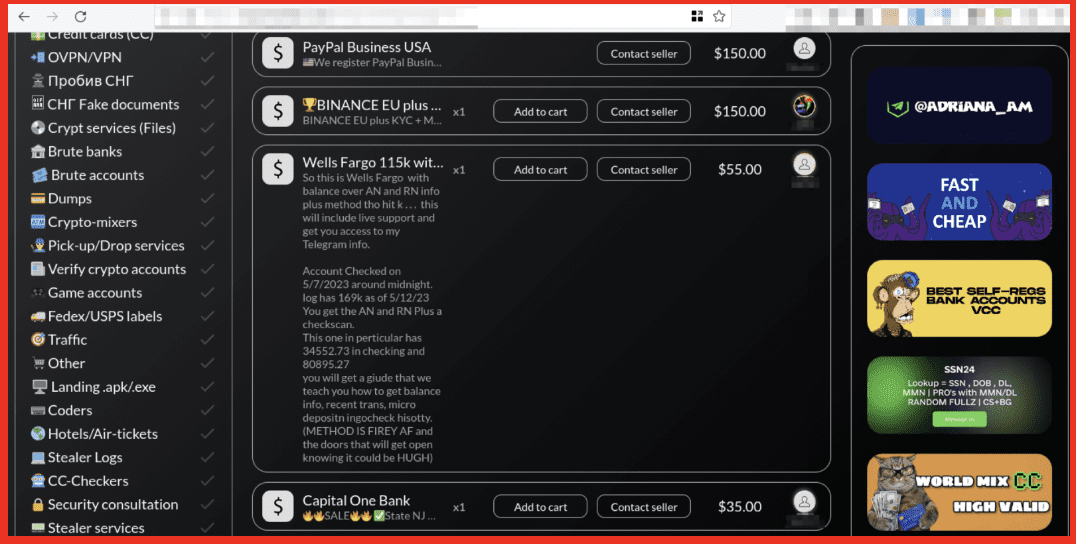
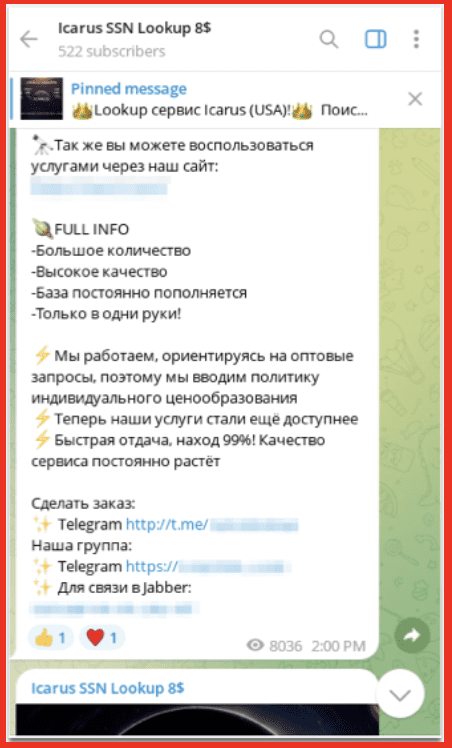
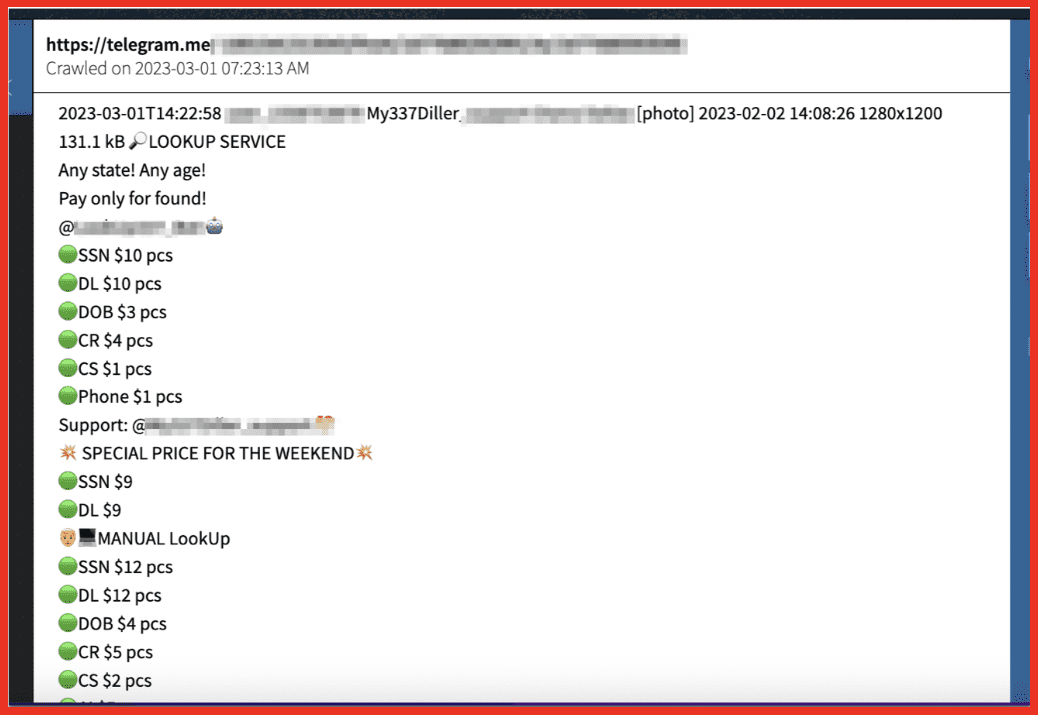
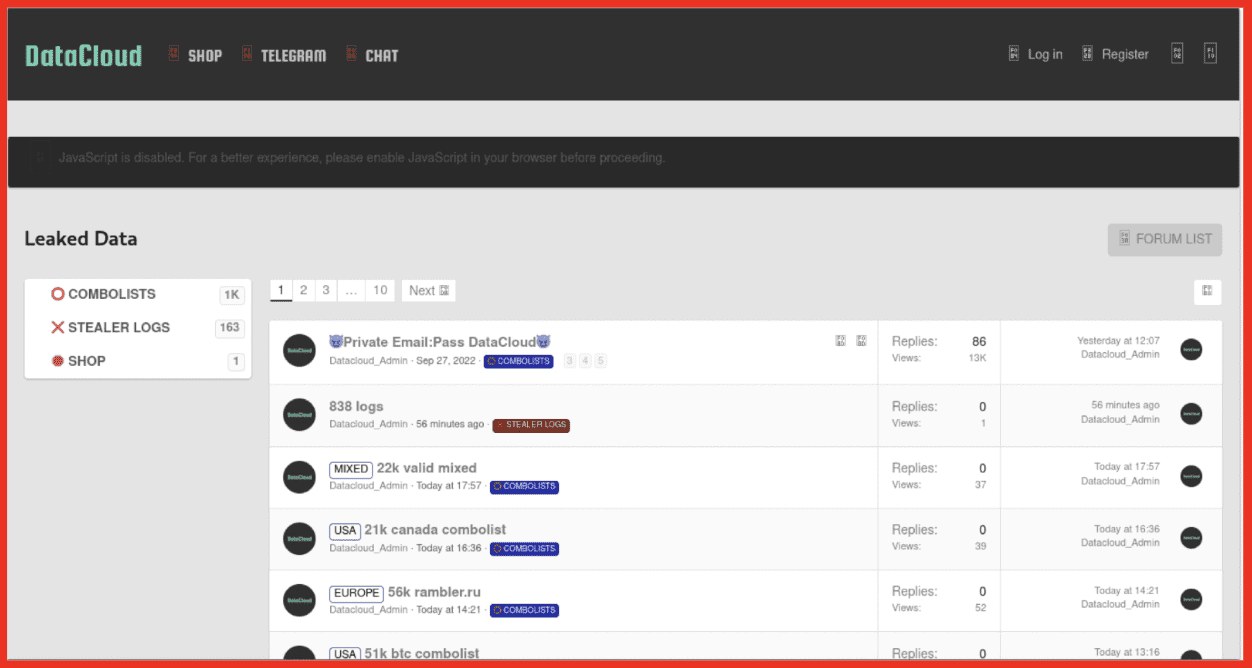
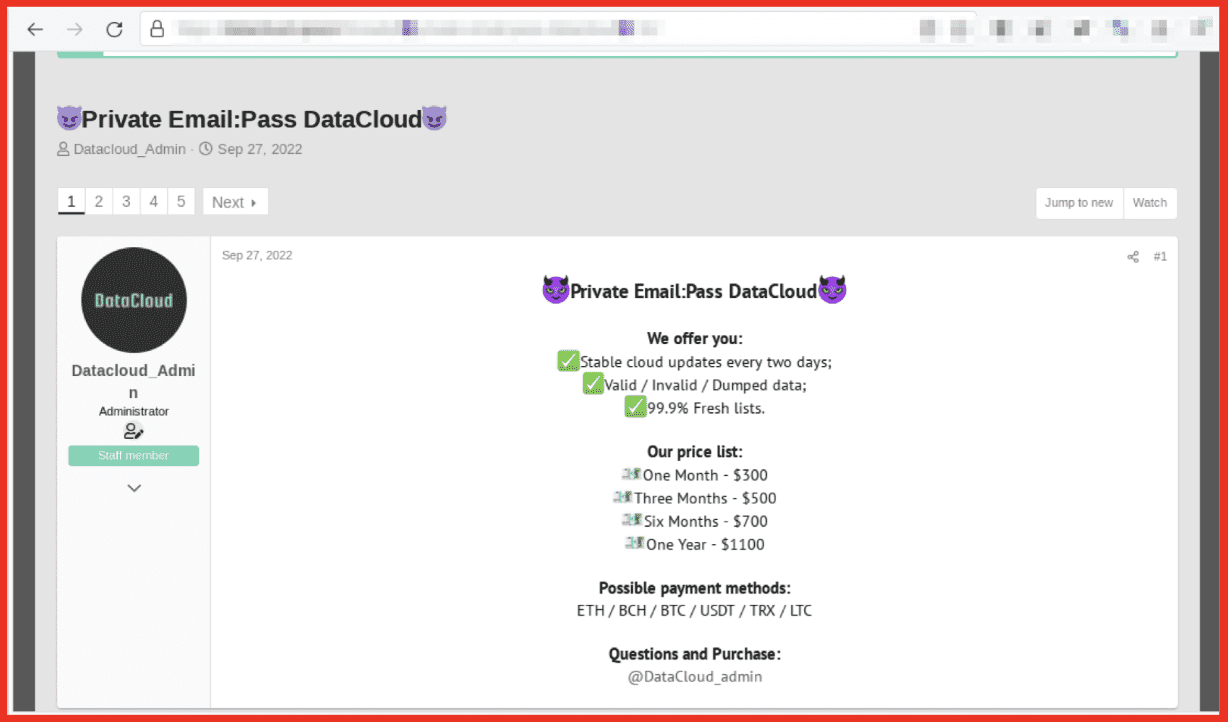
Alison: We are essentially darknet experts. So what we do 24/7 is we pull content off of the darknet, we park it in our own database, and then we provide our clients who are companies, not individuals, access to that data. Where our expertise lies is in the act of the collection – collecting data off of the darknet is not an easy task. And then number two, in filtering it, sorting it, layering on all of the bells and whistles on top of it so that you could go into our database and type in your social security number, up is gonna hopefully pop nothing, but if it does, it would show you those pages on the darknet that we, DarkOwl, have discovered that has that number present.
Ann: Alison originally started out in finance but was intrigued by some of her consulting clients in the security space. She eventually took the leap and joined the DarkOwl team in Denver, Colorado.
Alison: I’ve been here 6 years and we’ve been through a bunch of iterations and it’s been a really fun company to grow with. There’s just so much happening in the cybersecurity landscape that it’s great. I love it.
Richard: Allison’s work on the front lines helping security professionals use data from the darknet to inform their day-to-day operations is a very specific niche asset to the cybersecurity industry. But it’s important to define exactly why your work is so critical.
Andrew: Why would the CISO at a company care about what happens on the dark web? They have a website on the surface web, they don’t operate on the dark web. But seeing what’s happening today and where the conversations are going, that can help in the prioritization of how you address vulnerabilities. So threat intelligence, I like to say, puts a lot of the why behind a lot of the security controls we and our partners recommend to companies.
Richard: That’s Andrew Beires, Head of Threat Intel at Resilience, before this role, however, he wore several hats.
Andrew: I started in film school in New York City working at HBO on Sopranos and Sex and the City. And 9-11 happened and I rushed to a Marine Corps recruiting station and shipped off to Paris Island where I went through bootcamp and the Marine Corps sent me to the Defense Language Institute where I learned Korean and Chinese Mandarin. And then I worked on behalf of the Department of Defense and Marine Corps at the National Security Agency for the majority of my adult life. And that’s how I got into the cybersecurity space. So most of my work prior to rejoining resilience was as a nation sponsored, advanced persistent threat actor collecting foreign intelligence against our nation’s and allied nations foreign adversaries. So yeah, that’s me.
Richard: Andrew is in the trenches at Resilience, using threat intelligence tools like DarkOwl to not only protect our company but also to achieve our mission – to help our clients stay ahead of the bad guys.
Andrew: You know an organization that wants to protect their posture and their critical business functions, looking at the darkweb for those types of threats is critical.
Ann: In this episode with Allison and Andrew, we explore both sides of the security workflow from learning how the data is collected and organized to why it is necessary for making business decisions both proactively and reactively. What is the dark net and why should we care about it? Why are layers so important to build into your cybersecurity strategy? Do you have to work in a basement and wear a black hoodie in order to access this information?
Richard: Alison and Andrew answer these questions and offer valuable action steps for how this underworld of information can be used for good and know, in case you are wondering, a basement office and black hoodie are not required unless that’s your style, of course, which is totally cool. Anyways, let’s get into it.
Alison: In some ways, people are overly confident on the darknet because they believe that given the lack of IP addresses and cookies and what not, remaining anonymous is kind of it’s defining feature so there is kinda some false sense of security there, that even if people are looking at that content, they can’t trace it back. The other thing I think is really funny, or I don’t know why it is funny because I was an econ major and I should know that all these market rules apply wether it is legal or illegal, is that the quest to be the best in the customer success department in the darknet is very much present. So there’s a lot of credit card forums, my favorite one says “we are here to serve our customers, we are the best! We ship overnight, free shipping, we are extremely reliable…” you know reading the verbiage just makes you laugh, because you think these are criminals, but like any business they are trying to win and maintain customers.
Ann: Same with ransomware gangs, right? They have entire customer success divisions.
Alison: Yup!
Andrew: Bad guys are in the business of business too, right?
Alison: Exactly.
Ann: Mm-hmm.
Richard: The darknet is an encrypted layer of the internet that cannot be found through regular search engines like Google. It is used mostly for illegal activities and is a breeding ground for data leaks. Laughs aside, the darknet is not a space you want to enter without proper preparation tools and support.
Alison: You know, you run the risk of potentially running into content you don’t want to see, visually, you also run the risk of ending up in maybe a marketplace or a forum and potentially exposing your own identity without knowing it. And I think the other one, the third one, which is the reason we, DarkOwl, is in business is it’s an extremely, extremely inefficient place to navigate. So if you think about the surface web, you go onto Google type in your search term, and there are all the results and we all trust that Google has gotten that right. That’s why they are who they are. The darknet is not structured in that way. So if you were to go onto Tor, which you can, that is not an illegal act in itself. It’s just very hard to navigate. There’s not nice clean URLs to find, there’s no pretty search engines or search bars, so you’re gonna burn a lot of time frankly.
Ann: While the anonymous factor that Alison highlighted earlier is certainly part of the draw to the darknet, it’s not entirely true. Leaders like DarkOwl are making the data more searchable to help companies identify specific actors on the darknet through graphing.
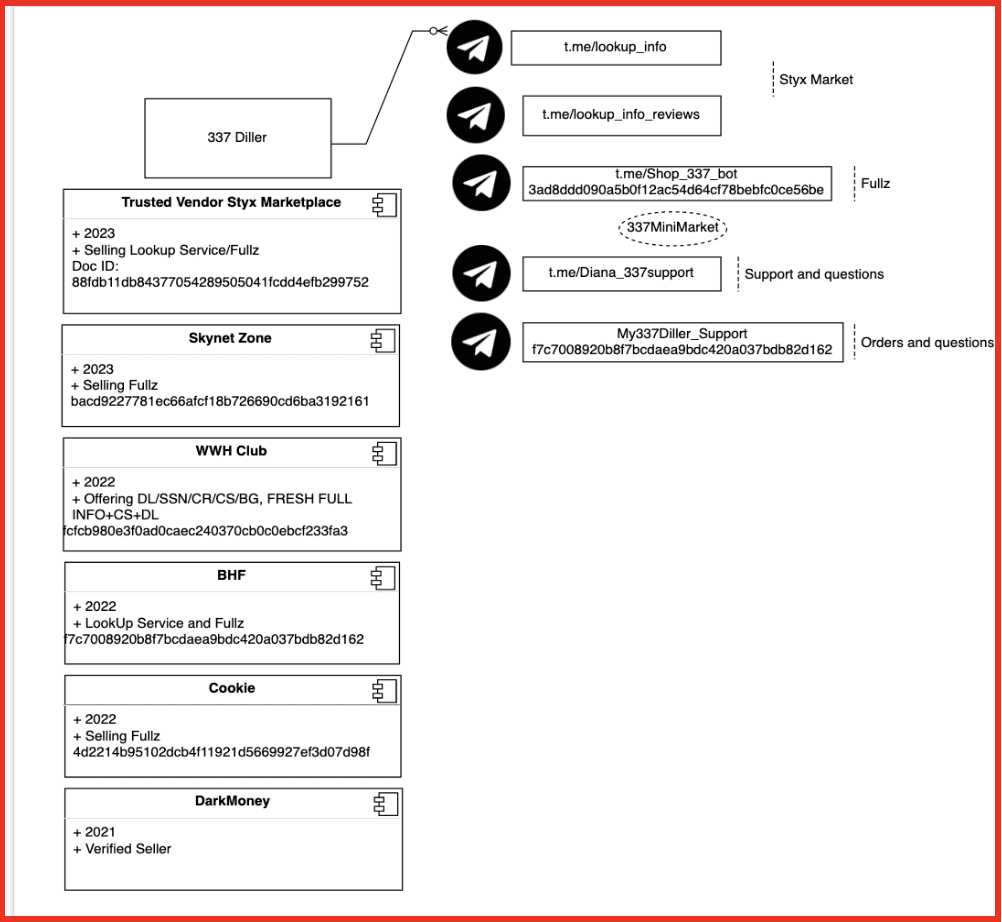
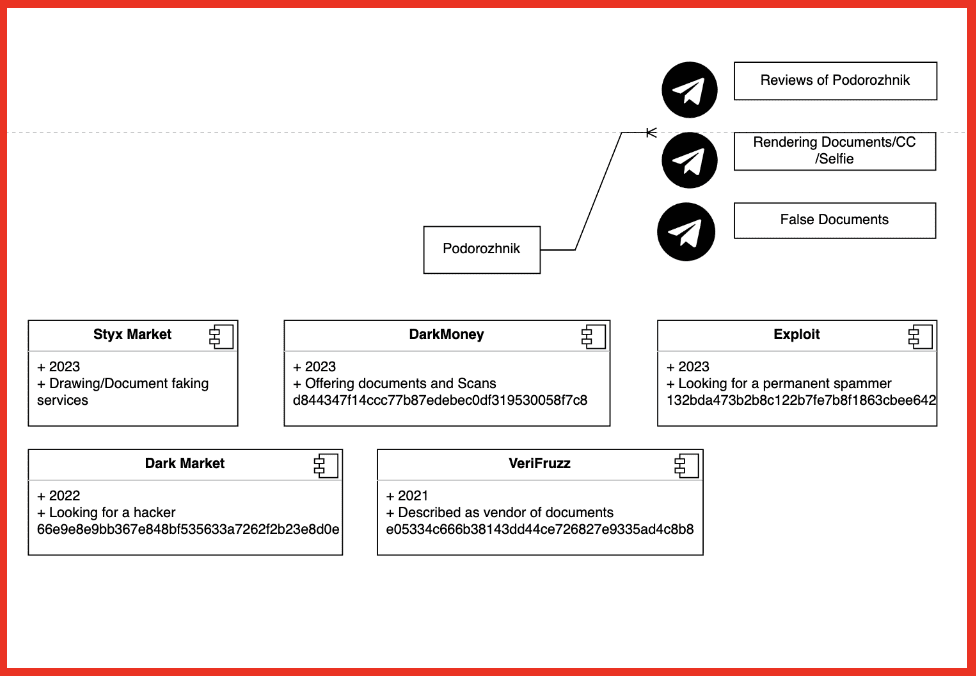
Alison: So I mean, part of it is us, as we collect all of this data and we’re indiscriminate in how we do that. And what I mean by that is we don’t look at, look at a page on the darknet and say, oh, this is outside of our industry – we’re not gonna grab it. We always grab it. And then once we do, the first thing we do is just tokenize everything that we see. Do we see social security number? Do we see an email address? Do we see a domain? Do we see an IP address? And obviously there’s tons of free text in between there, but we’re gonna tokenize as many items as we can, right? Is there an ampersand, like a threat actor name? And then once you’ve done that, like you said, it becomes really interesting when you can graphically represent the information, right? If you are a seller on a marketplace and we can connect you to a different seller that has a similar name that was, you start to play that game, which becomes really powerful in the investigation space. We are extremely strong on the identification of entities within the data. The graphing piece we are adamantly working on and have made some huge strides, but we haven’t, we definitely, if I’m being honest, we haven’t perfected that piece yet. And some of our clients actually use their own graphing abilities on top of our data.
Richard: So very interesting business model. And I’m just curious, maybe you can tell me about the type of clients you have and the threat intelligence groups and folks like that, that are in these organizations. I just have to assume their use cases are varied, but I’d like to hear more about that.
Alison: I like to bucket our clients into three groups. There’s one that people don’t often think of, that is where the majority of our clients sit. So number one, we do serve government and law enforcement. If you work for the DEA and you are in charge of tracking down folks selling fentanyl, you would wanna have access to the darknet where they’re actually doing that. And the DEA is not a client for the record, but that is one bucket of our clients – although the smallest.
Number 2 is large enough corporations where the risk of having their own organization exposed on the darknet is worth looking at this data set. So think Fortune 1000, you’re the CISO of Nike, and you wanna know, is someone targeting my executives? Is someone going after my IP address? Is someone talking about a ransomware attack or are my newest designs of my Nike shoes being sold. Counterfeiting is a big use case for us. So clients that have products that are being sold in counterfeit markets. So those are companies that are purchasing DarkOwl data and they’re looking at it for their own edification. That’s bucket number two.
And then interestingly, the biggest bucket of our clients are clients that are purchasing DarkOwl data, aggregating it and looking at it on behalf of their clients. So most of those folks sit in the cybersecurity industry. So it’s other cybersecurity companies that are, and we are essentially that darknet component. So I sort of like to think of it – you buy a Dell computer and it, you know, they used on the ad, they’d be like, powered by Intel and then it would make that little noise. So, it’s DarkOwl or their darknet is powered by DarkOwl. So, and that runs the gamut. They could be layering it on top of social media data. They could be just doing penetration testing and they’re using our data. They could be like you all in the cyber insurance space and they’re looking at DarkOwl across tons of potential companies. So that’s where the majority of our data and our clients reside is those that are looking at added on behalf of their clients.
Ann: At Resilience, this is how we utilize DarkOwl. Andrew Beires, Head of Threat Intel, is quick to point out that what he is looking for in his role falls right in between the bad activity happening on the darknet. And the good activity.
Andrew: You hear about the dark web and the news and really all the conversations you hear about it are about most of the bad things that are happening, right? So, you know, the illicit financing, the money laundering, the drug, narcotics sales, the gang activity, the criminal underbelly, sort of like place of communication. But there are actually a lot of good things going on where people in more oppressed nations who have, you know, a difficult time getting information out of their countries and sharing that with the world, that’s a great place to do that. There are journalists there, whistleblowers, there are people doing good on the dark web. So there’s good stuff too, if that’s what you meant by good. Now there’s a lot of juicy stuff that we care about, but none of it is good. None of that is good, right?
Richard: So the juicy stuff goes under the general rubric of threat intelligence. I always like asking people what is threat intelligence and how would I know it’s happening to me?
I always like asking people that question because the answer points to why we do what we do at resilience, Andrew highlights exactly how this plays out in his day-to-day workflow.
Andrew: You know, it’s like know your enemy, right? So knowing the people behind the keyboards that are attacking you, or have the potential to attack you, what their behaviors are. Like, what are the types of malware that people are purchasing? What are the trending vulnerabilities that are being discussed? So we had pretty strict criteria about the things that we want to engage directly with our customers about, and it has to meet three pieces of criteria. One, the vulnerability, so we are consistently evaluating the posture of our book of business. And so, and that’s company by company. And with the help of a lot of great people in engineering and data science, we are able to do this on a regular basis that a lot of it is automated. And so for us, when we see a company that, let’s say we, we see a vulnerability that is associated with some asset that they have exposed to the internet.
So first, is it remotely accessible. Like is it exposed to the internet or is this some local vulnerability that there would be a sort of a higher bar of entry in order to get to that asset. So those aren’t those types of things we wouldn’t really see from what we do. So it has to be remotely accessible. So remotely exploitable, right? It has to be our customers. So, you know, not a CVSS score, right, of critical. It doesn’t necessarily have to be a critical vulnerability, but if it becomes a critical vulnerability to us, if we know attackers are exploiting it actively in the wild or a proof of concept has been released on how to exploit that vulnerability. The third piece is there is actionable mitigation or remediation measures that have either been released by the vendor or a security researcher or somebody. So there is a specific action that the customer can take to mitigate or remediate. And then when we identify those, so it meets those criteria, we engage directly with the customer to notify them and help them through the process of remediation.
Richard: One follow on to that. So one vector of course is the remote. But many bad guys these days, particularly ransomware, they’re attacking what we call layer A, the human right? So be it spear phishing or phishing in general, or you think about business email compromise, all these other vectors. What’s the bridge between that threat intelligence and how you work with your customers?
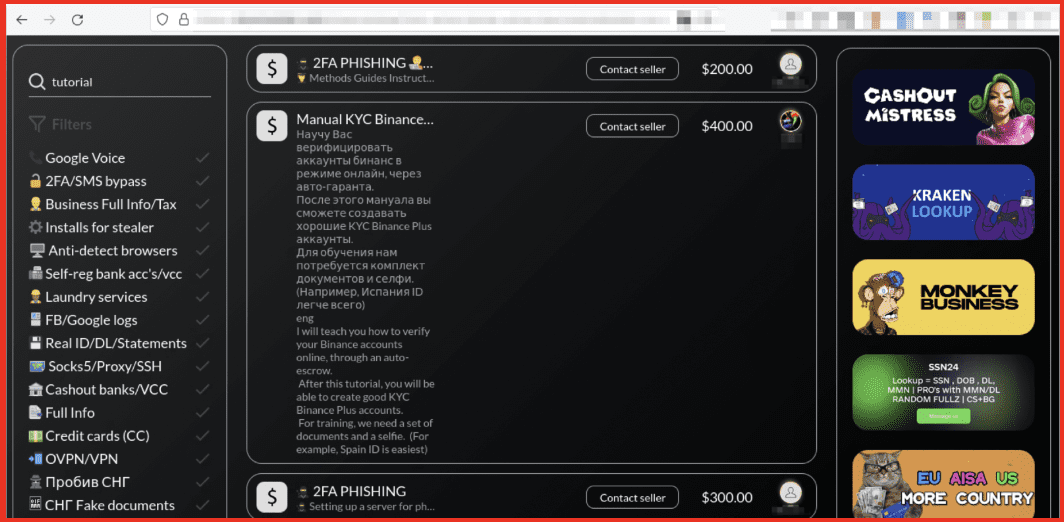
Andrew: Sure, the dark web is a great place to hunt for potential insider threats. And that doesn’t necessarily mean it has to be a malicious insider. Maybe it’s a negligent or unintentional error on the part of an insider that led to something like their credentials being exposed. Maybe it’s something through their own personal life that was exposed and then somehow that is, you know, associated to it enabling some sort of access to that organization. So another piece on the malicious sort of insider that the dark web is the place where people sell access to threat actors. So it is also the place where threat actors advertise paying for access to specific things like, “hey, do you work for this type of company? If so, and you have access, we would like to buy that from you.”
Ann: Wow, that’s terrifying to think about people sort of selling their access as an employee of an organization. A comparable thing happens, of course, and working with any nation state for espionage. But how often is that really happening? Is that happening frequently?
Andrew: Every day. And it’s on the rise, I would say like more in 2022 than in 2021. And I mean, the expectation is more in 2023. So our CISO loves to make this joking comment and I find it funny, but it is scary. Like you said, it’s terrifying, right? We’re all just one bad day away from being that threat actor selling access.
Ann: Yeah. In a way, I kind of hate talking about this in a public venue like this podcast, you know, I don’t wanna advertise that this is a thing… hey, go to the dark web and you can make a quick buck with your corporate credentials. But sounds like that could be the case.
Richard: I’m just endlessly fascinated with the area of threat intelligence because the possibilities in terms of the size of data and the types of questions that can be asked are endless. Obviously you’ve made it clear that one of the most plausible places to look for badness is the dark web as if that really constrains the search surface, for information. How is it that you go about getting at actionable information? You mentioned a little bit about data science and other forms of magic and mysticism, but maybe you can unravel that a little bit for our listeners. Like how does that actually work out? Because the reality is the dark web, it’s a big mysterious place, right? So how do you do it?
Andrew: We have relationships with intelligence providers both in the private sector and in the government. So, you know, this may be story time. So we’ve got alerts set up. If there are specific keywords maybe mentioned, so I’m not having to read, our teams and having to read every chat in every forum across the entire internet. But we obviously care about the insurance industry a lot. There is a threat actor selling access and you know, of course they will anonymize it, right? Not give the keys to the kingdom in the advertisement. So the company was not named, but it was an insurance company, global insurance company. And what was given was the zip code. So just piecing that together and working with one of our co-founders, we were able to figure out exactly which company that was.
And for us on the security side, we are what we consider white hats. So there’s this ethical responsibility, a very focused moral compass. So we did what we considered the right thing, which is to contact this insurance company and let them know that this was going on. And it was through scouring LinkedIn to find, just doing a little open source intelligence like who works at this company in security and would even begin to understand like why I’m trying to message them. And so we were able to get in contact with ’em, this was a Sunday afternoon and it went until maybe 11 at night and they were incredibly thankful. So that was a success story. Maybe we were able to prevent an attack and sort of shut that down before it led to an extortion event.
Richard: That’s awesome.
Ann: Andrew’s insight shows how these tools are used at a firm like Resilience to stop an attack in its tracks. Allison provides two more examples of real world use cases from a more proactive perspective.
Alison: So there’s absolutely a way to look at this data set and sort of get ahead of it. And I think, you know, the most simple example would be, let’s say you’re an organization and all of a sudden next Tuesday you see that 200 of your employees email addresses are part of a, a breach or a compilation or someone, someone says on a forum, “I have 200 email addresses and plain text passwords associated with this company.” And oftentimes they’ll actually put those up as kind of proof of life. And you know, the use case there, Rich, is what are the, if you can get that sample, which we at DarkOwl would pull down and would be in our database, then it becomes a much easier reconnaissance game of instead of just saying, oh my goodness, we have content on the darknet – I don’t know what it is, I don’t know what to do about it, I don’t know how it got there. If you can pull down those email addresses and say, wow, it turns out all 200 of these employees started on September 1st, or all 200 of these employees attended a conference in Florida two months ago, or all 200 of these employees are no longer with the company. Those are three totally different incident responses. You know, one of ’em you don’t even have to deal with, right? One of ’em is, let’s go to our HR platform, why are they, they were all onboarded, but it gives you the context to then figure out what the problem is rather than waiting for it to show up on the front page of the Wall Street Journal that your organization has been subject to XYZ.
So I think the context can provide that proactive piece and allow companies to understand and especially that definitely follows suit in regards to some of it’s more, you mentioned qualitative versus quantitative. Some folks are just looking at it for, in sort of the way you look at Glassdoor content, right? What are people saying about our company? Is there a negative talk about it or you know, is it notorious for easy to break into? I mean there’s a lot that you can gather from sort of the sentiment about how people talk about organizations that can be telling too, for an organization. We do have a sector of, and this is more recent, but it’s growing quickly of clients who are in the TPR, third party risk platform or management, where they’re looking at, think if you’re a huge organization and you’re considering all these different vendors as you kind of want to know how risky is that, do I have some that are, have a great deal of exposure on the dark net would be an a leading indicator that they may not be as buttoned up as you think.
And then that same sort of use case translates really well to the M&A [mergers and acquisitions] space. So we have folks that are looking at the data in regards to potential mergers or acquisitions saying, you know, is this a company I wanna purchase or emerge? Or they get a sense for what their hygiene is in some ways.
Ann: I have one kind of funny question. Sometimes when I find myself in the DarkOwl UI, as I said, I search for myself, the next thing I do is just sort of look at people’s, pick a company that I care about. You know, I’ll just kind of browse plain text passwords. I find them endlessly entertaining to just read like a novel. Do you have any interesting or funny anecdotes about just like, things that you’ve read or seen or been entertained by in this data?
Alison: Yes, absolutely. So, you know, obviously we do a lot of demos of our platform for potential customers and we almost always search for their organization in front of them and show them what content we have. And we have had, I think I’ve been in the room for two, one of ’em was in person, one of ’em was on the phone, but two demos that were extremely embarrassing. And what I mean by that, Ann, is we searched for the organization’s email addresses that had been exposed. Those came up, there were plain text passwords associated with them for someone that was actually on the call and which happens all the time. But the part that was embarrassing is their plain text password was not something you would want.
Ann: Didn’t read it aloud?
Alison: Yeah, no, we did not it out loud.
Ann: Amazing.
Alison: My guess was they made it as a 17 year old teenage boy and hadn’t changed it yet. So…
Ann: Or that’s what they still are on the inside.
Alison: I’ll Leave it at that. So we’ve had some interesting passwords, but yeah, I agree with you. I also read through plain text passwords like a novel. I find it fascinating.
Richard: Embarrassing passwords aside. These examples show how having access to this data allows your organization to be proactive. As Alison highlighted, organizations are using it to hedge their bets on mergers and acquisitions. Another emerging use is occurring in the insurance underwriting space.
Alison: I think we’re kind of at stage one, right? If I was someone underwriting policies for a company, I would just want to know that baseline, like what does that presence look like on the darknet? And I think where we can head, which would be a really neat space to be in, is can we look at that data and then incentivize that company to better their practices, to lower the risk, lower the policy. You know, I think there’s, that’s kind of the proactive piece that I think would be, that we’re headed towards. And there’s obviously a lot of work to be done, but the data can be informative and I think you guys are doing a really nice job at using it.
Richard: Actually, that’s a great opportunity for me to ask Ann a question about how we use your data in our models. Yeah, I’m actually very curious. And you know what, I bet you other people are too.
Ann: Yeah, I mean we use it for underwriting. So we collect data and we look at the results, our models consider the results with exactly what you said Alison, the sort of understanding that the goal is that organizations are not the worst among their peer group.
As I shared, Resilience uses DarkOwl for everything from defensive measures to proactive underwriting insight. Now every business will use this information differently depending on your unique goals, but the key is to use it to your advantage. How do you make sure your company is taking the optimal steps towards cyber resilience? Andrew has some advice.
Andrew: It’s like trying to align your sort of cyber risk with your critical business functions and how those align and if it makes sense financially. To try to build a capability in-house, that is one way, right? But there are also businesses built, that have been members of the intelligence community previously or black hat types previously that do this every day. And so paying for that as a service is another, is another option. But there is no doubt that insight to what is going on on a lot of these forms. And then sort of back to your question as well, Dr. Ann, a lot of the groups that exist, they have very specific requirements in order for you to be let in the room really, right? So sometimes it could be proven track record of successful attacks.
So those are ways they are trying to evade obviously being on these more accessible forums. But back to your question, Rich, there are companies that are built for this. So whether or not it’s better to build an in-house capability or pay for that as a service, either way there are so many reasons why you want to know what’s going on. One, you know, is your company being targeted right now today? Do any of your credentials show up in data dumps? How do I prioritize like patching vulnerabilities? Not saying the only factor to consider is what’s being talked about, what is trending on the dark web, but that is a factor.
Richard: So let me and Ann, I have to drill in here cuz it’s like on this path of operationalizing this stuff, you know, there was the Lockheed Martin kill chain and that was fun to say, I like saying kill chain, but now there’s mitre attack, right? And you know, you have all the STIX and TAXII and you know, the idea that, log aggregators or a scene, whatever you like are now and soar are being able to consume in theory this data and you have data sharing and all that stuff with the intent. I think the belief as a buyer, this is as a consumer, as a CSO, the idea is, hey, you can scale out this sort of stuff without having to have an Andrew and you can make it actionable. That rests uneasy with me. This is maybe just to my own bias, maybe you can tell me a, what sort of value do you get out of like mitre attack, STIX and TAXII? How have you seen that get operationalized in the seam space or log aggregation space? What are your, again, getting back to the CSO or security person listening and thinking about how do I do this and what do I need to look out for? I know that was a big question, but there you go.
Andrew: Sure. So I would say, you know, specifically there is value in like the STIXs of the TAXIIs, right? So any specific indicator of compromise. That anything that I could ingest and automatically be able to detect or flag something specific that is known to be used by a threat actor, that’s great. Like how it all, so how you prioritize what to do first. Like that I think is where the human element comes in. Whether it’s from an incident response perspective or whether it’s trying to, for instance, stop an attack during the reconnaissance phase, like you mentioned the kill chain, so before initial access. Some of our partnerships enable us to have alerting from the intelligence community where they are sitting on the internet and they may see something like a staging sort of operation or preparations like planning being conducted to potentially target a company and then being able to alert that company. Like there’s such a human element to it. I don’t ever see the entire process being completely automated away. I mean that would be sign me up, I’ll find a nice warm beach to sit on.
Richard: Andrew’s point about humans being inseparable and paramount to this entire process, no matter how many autonomous upgrades and AI insights we add to it is key. To illustrate how these layers of security create a strategy that works. I shared a recent story that caught my attention.
There’s an NFT loss where the, where it was guy who’s the CEO of one of these NFT processor, he had his wallet or something hacked into, he lost millions of dollars of NFT value, but he said it didn’t impact his company. Cause they have, they have multi-factor authorization. So I was just thinking about this is the practical thing when we think about customers, like if we start seeing like there’s this campaign for business email compromise, it’s associated this, we see it that it’s a long term drain by thousands of cuts, but these are the practical things that you can do as opposed to just patching, here’s some business process you can put in place. Here’s some other things you can put in place that will, you know, that yes, it’s very shift, right? But could be remedial or really impact reduction. Cause we always get so focused on what can we do that’s innovative from a technical perspective that’s important, but there’s this whole other side of responding to actual loss.
Andrew: It does seem that with novel techniques for attacking, right? Often it comes back to the same control. If implemented correctly could prevent it.
Richard: Yeah, it could be hugely preventative. Yes, we can put great in-line controls in place. Yes, we can put great endpoint, yes, we can do great training, that’s good, but are there things that we can do that in theory can potentially mitigate this becomes harder in large organizations. Like how many people actually are able to move money around? Do you even know? And that’s, that becomes part of an attack service, right? So that’s interesting too.
Andrew: Defense in depth – like all the different layers. It’s more than just training your folks not to click on suspicious emails. Well there’s that, but then there’s also all of these like email filtering processes you can implement as well. Not one thing is gonna be the answer, but layering. I guess I’m explaining defense in depth now too. So I think that’s the answer.
Richard: I think this is a really great, like these sorts of things that people can practically do to protect themselves coming from someone like you is just so useful. All right, Anne, ask your closing question. You’ve been so good, Andrew, you’re awesome.
Ann: Last question. At Resilience, we talk a lot about what makes a company cyber resilient. I’m curious how you would answer that question.
Andrew: So a layered approach to security. It’s not one thing, it’s a lot of layers. So for instance, in business email compromise, we were talking about how training employees to not click on suspicious links or don’t click on ads that are being served up on your real estate. If you’re on an intermediary service provider like you two, right? So it’s not about always necessarily having the highest castle walls and the moat and the drawbridge and everything, but it’s like what makes a company cyber resilient is that, you know, that you might get infiltrated, so to speak, and how can you then quickly quarantine that, get them out. So yeah, a layered approach. Defense in depth. There’s critical security controls that you just have to be a part of every organization. So, you know, it takes a village.
Ann: Alison echoes Andrew’s sentiment by acknowledging the reality that you will be attacked. Having this level of humility is essential, but how you arm yourself and stay vigilant is what will determine your success.
Alison: I think anyone who thinks they have it all figured out and are all buttoned up are the most susceptible. I think we can only strive to be better than someone behind us. I mean, the analogy I like to use is, if you’re in the woods and you run into a bear, you don’t need to outrun the bear. You just need to outrun the other person with you, right? And I think in the cyber resilience space, you don’t wanna be at the bottom of the barrel because that’s the easy pickings. And if you think you’re the best, you’re probably not. There’s always holes. So I think, staying humble and making sure that you’re doing everything you can. I guess that would be my answer.
Ann: Yeah. Awesome.
Richard: So we often talk about the need for more visibility. We’ve got a lot of telemetry on the security tools that we own. It could be scanning, it could be from penetration testing, it could be from security information event management. It could be from your insurance policies and questionnaires. Adding dark web adds a lot more information about an area of extreme uncertainty. And if we get information from there about an actual attack on a specific company or perhaps even a person and or a whole segment, we’ve just really up-leveled our ability to respond. This is why having really great context, context that’s connected across the stuff that you know empirically and the stuff you know, as possibilities and bringing that information to bear with risk transfer is so key and why it’s such a key part of what we do at Resilience.
Ann: The darknet is big, it’s diverse. There are a lot of different types of people in hoodies, not in hoodies, doing a lot of different types of things with different types of data. It’s important that we all stay realistic and and humble and pay attention to what’s going on out in the internet land.
Richard: Thank you to Allison and Andrew for their time, expertise, and valuable insights. And to our production team at Come Alive Creative. Follow the Building Cyber Resilience Podcast wherever you listen so you don’t miss an episode, we’ll catch you on the next show.
Curious how darknet data applies to your use case? Contact us.