September 19, 2023
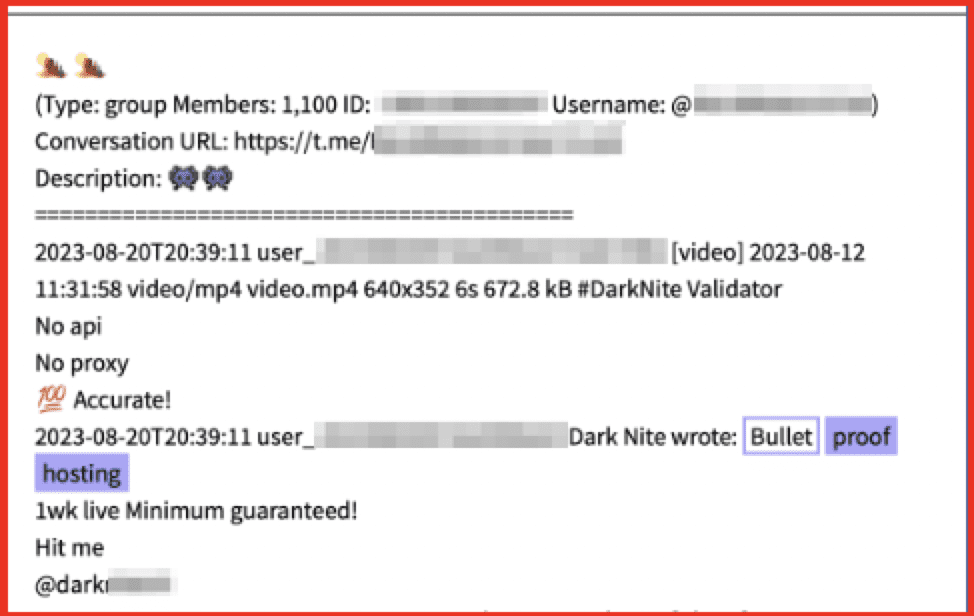
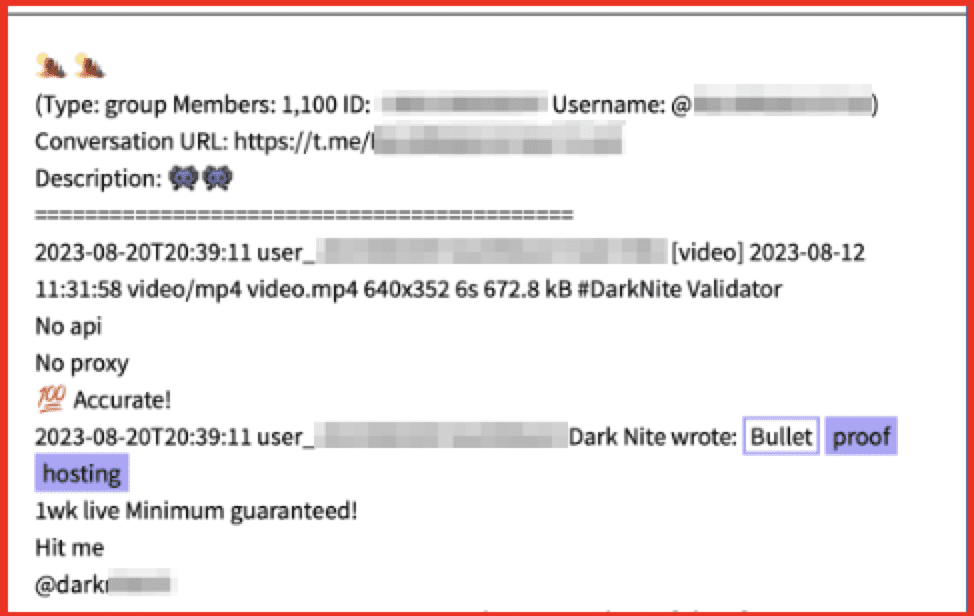
The darknet is a haven for illicit activities many of which can pose a direct threat to organizations and individuals with stolen data being made available for purchase, access to illicit goods, and hacking activities. In addition, forums are used to discuss all manner of topics from extremism to CSAM to hacking practices and education.
Accessing and analyzing data from the darknet is challenging, even for the most experienced of analysts. DarkOwl is the darknet expert, with access to the largest database of darknet content. Our customizable service options allow customers to leverage our in-house expertise to save time, keep their employees safe, and fulfill the need for actionable threat intelligence.
Interview with the DarkOwl Darknet Analyst Team
DarkOwl’s Director of Marketing, Dustin Smith, sat down with Erin, Director of Intelligence, Senior Threat Analyst, Steph Shample, and Darknet Intelligence Analyst, Richard Hancock, to understand a little more about their backgrounds, why they love cyber, projects they’re working on, and some tips and tricks for new analysts.
Editors Note: Some content has been edited for length and clarity.
Why did you get into cyber security and the darknet space in particular?
Erin: I kind of fell into it. I worked for the government and I was put onto cyber work, so that’s kind of how I started in cybersecurity. And I really enjoyed it. There’s a lot of fascinating characters and interesting people to investigate in that area. It’s very much been, in the 15 years or so that I’ve been doing it, a growth space with more information and more techniques and things happening all the time. So there’s always new stuff going on. And then the dark web has always been something that people are utilizing and using as a means of communicating. It’s always been fascinating in terms of its darkness, I guess, for want of a better phrase.
Rich: For my entrance into cyber security, I also kind of fell into it. It’s interesting because a lot of people who have a background in government contracting, working directly for the government and counterterrorism and linguistics, like myself, transitioned into cyber threat hunting. And I think that reflects a level of how foreign policy and national security interests are evolving as well. But actually, my first entrance into open source intelligence investigations was actually through a recruiting job where I had to get really good at finding people’s contact information online. That’s where I developed a lot of my Google dorking, Boolean skills is in the recruiting world. I didn’t study computer science or anything science related in college, I studied Arabic and international studies and something I tell a lot of younger people that are trying to get into cybersecurity is just because you didn’t study something technical, doesn’t mean you can’t work in cybersecurity.
Steph: So we all kind of fell into it because I was also government. What’s interesting is that I have almost the exact same start as Rich, in that I was doing counterterrorism work. You take those investigation skills for online patterns of terrorists and kind of trying to get into closed networks and you have to take that to the cyber world as well. But same situation – I had no computer science, I was studying humanities in college. And then it was the linguistic aspect that… the needs were like, hey, Iranian cyber actors are coming online, African terrorists are using French forums… Can you translate this? Do you know what’s going on? So I think getting into it was accidental, but staying in it was definitely intentional because there is never a dull day.
There’s never a dull moment. You have to learn something new. It’s not a matter of, “oh, I like learning new things.” If you want to stay competitive in the field and if you want to stay on top of your game, you have to advance with technology. And so that makes it really exciting. Furthermore, to come into the Internet world that none of us had a background in, no computer science is one thing, but when you start seeing TORs and these closed down platforms and these kind of CAPTCHAs and you’re just like, “how did these people come up with this and how can they navigate this?” And then also wreak havoc across the world on every industry. From what Rich said, it influences policy, the defense sector, but it also influences the financial sector and industry of all kinds. And what these people can do, cyber criminals, namely on the dark web from remote places. It’s fascinating. And do you want to be part of the good or do you want to be part of the bad? Do you want to combat that and the damage they have internationally, or do you want to just let them go? So that’s why I stayed in it. And it’s amazing, especially the dark web. It’s fascinating.
I love how you transitioned into why you stay in cyber. Rich and Erin, do you have comments to add?
Rich: I’ll draw back to the link that Steph and I have, which is our cultural interests and linguistic interests, which got us into the industry. Why I’m going to be staying in it is because I’m constantly learning. I’ve had darknet experience at previous jobs, but the amount of information that I’ve learned since being here [at DarkOwl] and how much better I’ve gotten at doing cyber investigations and the exposure to different industries is because we’re not just selling to one particular type of client. It has been incredible. Developing darknet subject matter expertise is a really, really valuable skill that can be used in so many different ways moving forward.
Erin: I just really enjoy it, honestly, that’s why I stayed in it. I love figuring stuff out. I love a puzzle of, you’ve got to find something and how do you go and find it? And one of the things I think in the industry that’s so different from government is it’s really on you to go and find that information. I think in government and military, you’re getting SIGNIT [signals intelligence], you’re getting all of this information coming to you, and then you just do stuff with it. Whereas in the jobs that we do, it’s a case of: what can we find and what places are we going to look and who do we need to talk to find out that information? Steph and Rich say it’s having those linguistic abilities or having that knowledge of the different cultures and knowing the kind of subsectors of the groups within the dark web and what they’re interested in and what you need to talk about in order to kind of to get in with them. It’s just interesting. I enjoy it. And as the other guys have said, it’s constant learning. It’s a constant challenge. There’s always new things to do. It always keeps you on your toes.
Dustin: Erin, do you come from a computer science or tech background or more humanities?
Erin: Humanities. I always say to people when I’m talking about my job and what I do is that I’m not technical but I have the ability to translate technical stuff to other people. I can take the technical information and tell you what it means in clear English.
Steph: Can I piggyback off of that? I think another side skill that emerges when you talk about backgrounds, like Rich said, you don’t have to be from a computer science background or be a programmer, but all of us have the ability from government customers to industry customers to be able to translate what cyber actors are doing, nation states, governments at every level to C-Suites, Generals to HR [human resources] and everybody that has hands-on information. We get better at that every time there’s a new group or a new tactic because we have to essentially translate, how does this impact you? What is your risk and how can we help you make your environment better and safer? And it really is circumlocution direct approach, translation, running it off of each other. It’s a foreign language and its own lexicon in and of itself. And it’s really cool.
Switching gears a little bit, now that we know who you guys are. Explain the concept of Darknet Services and why DarkOwl launched this offering.
Erin: I think what Steph just said is a really great segue into this. One of the things that we’re able to do is take that technical information, take the trends that we’re seeing, take the groups that we’re seeing and put it into a report or presentation for people to understand what it is they’re looking at. The dark web is a very complex place, there are a lot of different groups on there, a lot of different individuals using it for a lot of different purposes. It can sometimes be kind of tricky to understand everything that’s going on and what that actually means and how that fits into the wider context of what’s going on in the cyber world and in the criminal world more widely and in geopolitical politics. And all of those things depend on what background you’re coming from or what and who you’re looking at.
So the idea with Darknet Services at DarkOwl is we really wanted to support our existing customers and any new customers that come on board with our expertise of investigations and the dark web. We can help explain what they are looking at, what risks they should be concerned about, what remediation, if any, action that they can take, and really support them throughout any investigation needs.
Steph: It’s everything that she just said. Absolutely. Darknet Services is also a really great offering because let’s face it, the tech and the dark web especially is intimidating and there’s a security risk. So we [DarkOwl analysts] assume that risk because we know it. Most of us have dealt with it for over a decade, if not two decades. So if you are an individual who isn’t comfortable with the darknet, you don’t know what you’re exposing inadvertently, you don’t want to be the weakest link in your organization, but you want to know what’s out there. We take that risk and we can do it as far as one website, or we can do it for a whole host of threats, a specific industry that you want to look into or a specific group that you want to look into. And we take being able to do those services very seriously because we want to make a positive contribution and a positive change.
Furthermore, let’s be serious about the fact that there’s new stuff emerging that even we [DarkOwl analysts] need outside assistance with doing. The platforms are ever-emerging and ever-changing. So, let the services team assume the risk to keep your organization protected because it is intimidating out there. But we do know the dark web, where to go, and how to be safe.
Rich: I think one point to add to that is the ideal audience for Darknet Services at DarkOwl could be somebody who’s more beginner when it comes to darknet knowledge, or somebody on the more veteran experience side. To explain that further, let’s say you’re trying to better understand what the main risks are to you as an organization, and doing some ongoing monitoring. It could be a more simple engagement for somebody who’s newer to the darknet and with the eventual hope that they’ll be able to do some of the investigating on their own within our platform. But also there’s opportunities for people who might have more complicated queries about what’s going on in the darknet and maybe specific asks for what is going on in this particular community or things like that as well. So I think it’s just important to note that there’s not one ideal audience for Darknet Services. It can be somebody who’s more experienced on the darknet or not as well.
Steph: Great point. Can I also add to that, like you said, it’s varied audiences and you might be a veteran, or you might be brand new. Furthermore, maybe you know that your company or organization is fairly safe and has good cyber hygiene, but your suppliers or your vendors or your third-party don’t. And maybe you don’t know how to investigate them and you don’t want to have that awkward conversation of like, “Hi, are you subjecting us to ransomware or credential theft?” So that’s another place where we come in and we can look at your supply chain and your vendors and that way you can have a more robust picture of all potential risks.
Erin: The other thing I just thought of as well is it’s not just about doing that investigation and looking at groups or looking at your exposure. We can also do data acquisition as well. So we’ve had a lot of customers that have come to us and said “we’ve been told our information is out there or we’ve seen someone advertising this particular piece of information. Can you please go and get it for us or can you confirm that it’s there and what’s in it?” And that’s a really tricky thing for a lot of people to do as well, because it involves interacting with threat actors, which most corporations don’t allow their employees to do and you probably wouldn’t want to do. There’s a lot of other factors that go into that. We are experienced in working with those factors in order to get that information that the customer wants. So there are several use cases that we can support.
Why is darknet data important in cyber investigations and risk monitoring?
Rich: Dark web data is just another component of open-source intelligence. There’s darknet intelligence, open-source intelligence, different forms of intelligence, and in order to conduct all source intelligence analysis, you need a factor in dark web intelligence into your picture.
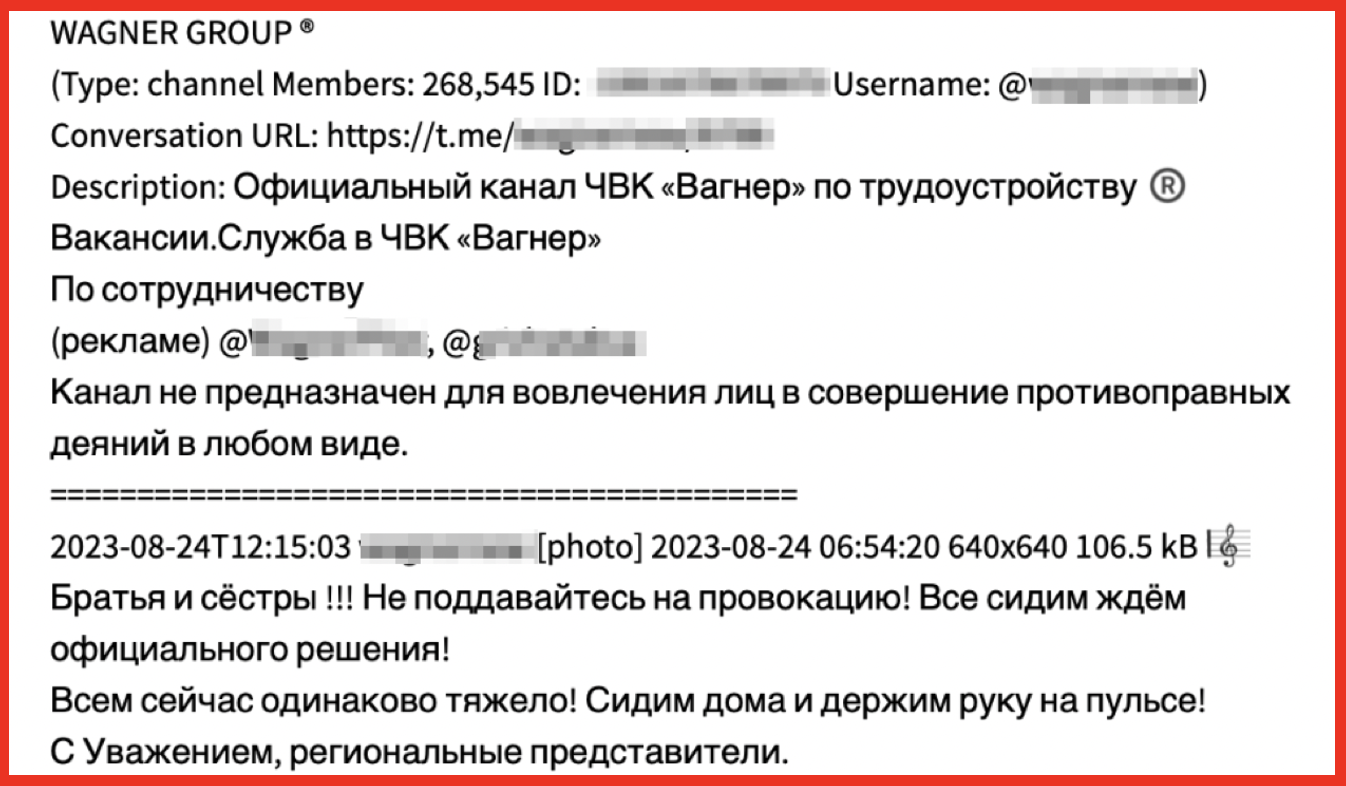
Steph: I think there’s an evolution of intel. Rich is right, darknet intelligence is a component. We’re not saying only focus on the dark web, but you do need a robust picture. Additionally, cyber actors in the evolution of technology follow the trends too. In the 2010s, when I first got on the darknet, these actors, and it’s still true to this day to an extent, feel safer on the dark web. They feel that it’s not as monitored as the open net or the clear net so they reveal TTPs [techniques, tactics and procedures], usernames, aliases, their whole criminal ecosystem. And now we were seeing threat actors on darknet adjacent sites, like chat platforms such as Telegram. You have to keep moving with them because they’re not as open on the dark web anymore, but they are on Telegram and other platforms and we can follow that evolution and follow that chatter to get some really deep insight that they don’t think is being monitored.
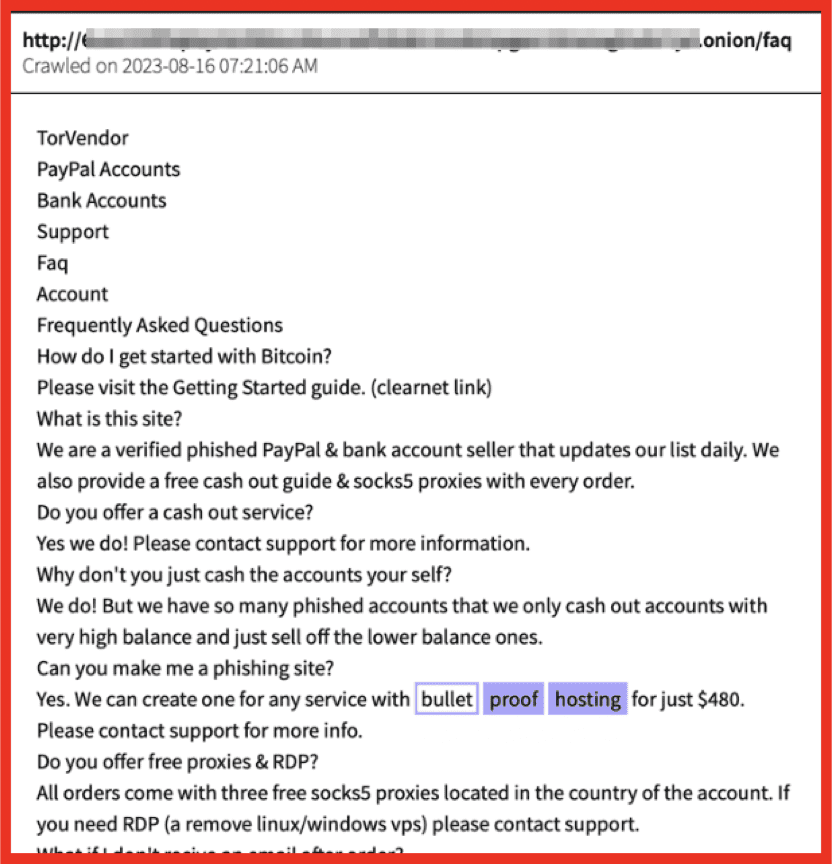
Erin: Just to echo that, although we’re a dark web company, we also cover a lot of dark web adjacent sources and we’re seeing them becoming more and more integral to the investigations that we’re doing. With the Russia-Ukraine War, we’re seeing a lot of pro-Russian and pro-Ukrainian Telegram channels that have thousands of followers. Telegram is becoming a really important vector. Seeing how threat actors communicate is going to always be a key aspect to knowing what they’re doing so we need to be aware of those communications, and also look at things on the dark web like marketplaces and forums, to gather trends. By doing this, we’re able to see what types of cryptocurrency actors are using, how they’re doing their escrow services, how are they doing financial transactions, what drugs are most popular at the moment, etc. One of the things that we’ve seen recently is there’s been an increase in black market pharmaceuticals of things like Ozempic because people want to lose weight rather than the more traditional drugs that people would think of. We’re seeing increases in counterfeit and things like that.
To just touch on ransomware- ransomware is increasing exponentially and has been throughout last year and into this year. Ransomware groups are using the dark web to advertise the victims that they’re targeting. Then when they don’t get their ransom, the data from those victims is released. There’s a huge amount of information there. For corporations to know what exposure they have, it’s really important to be checking through all of those things because as Steph said, it’s third parties and vendors as well. Just because you didn’t get a ransomware attack doesn’t mean that your data hasn’t been exposed. Again, as Rich says, darknet data is part of the whole ecosystem of doing open investigations, and it’s something that should be covered. The Darknet is an area that a lot of people forget about. They tend to focus on social media, surface web forums, data brokers, and things like that and aren’t looking below the surface, and I think that’s where you find most of the useful information.
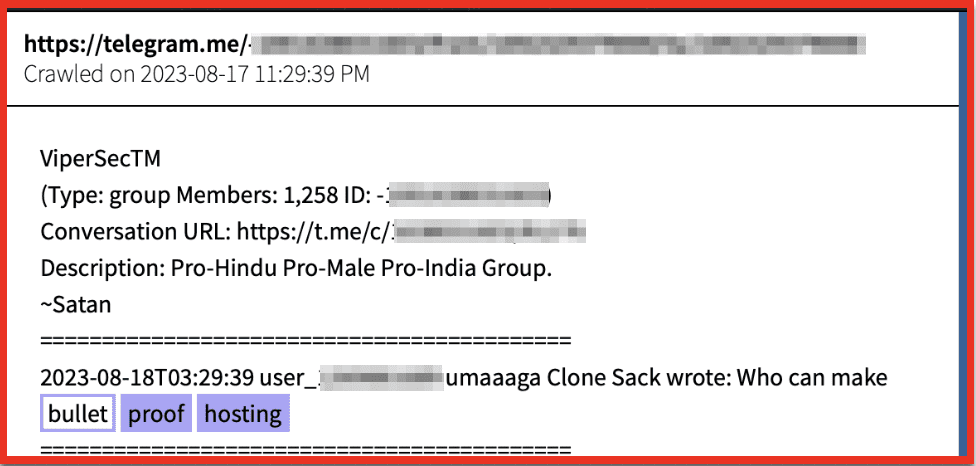
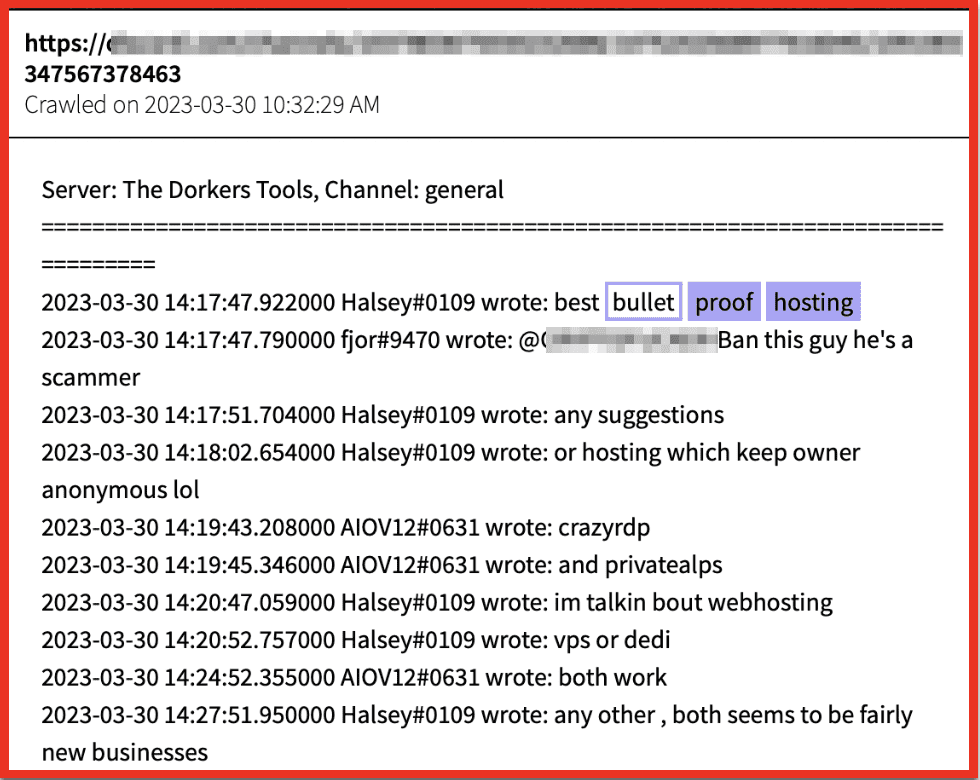
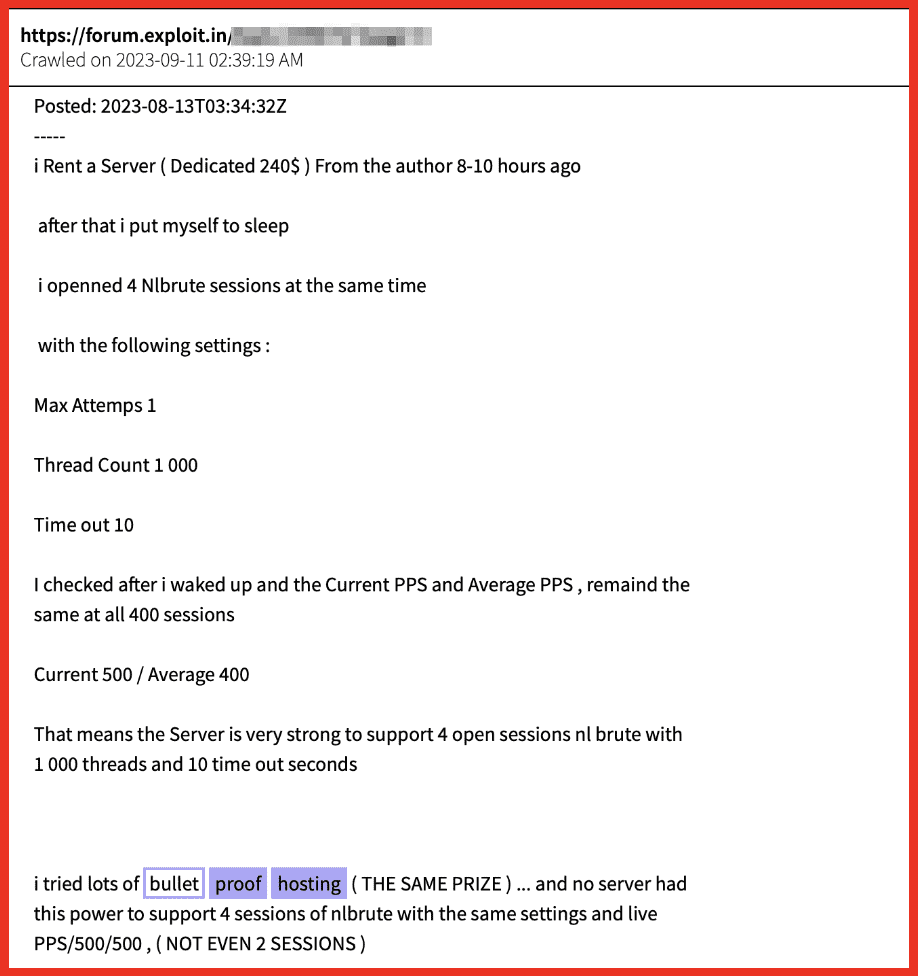
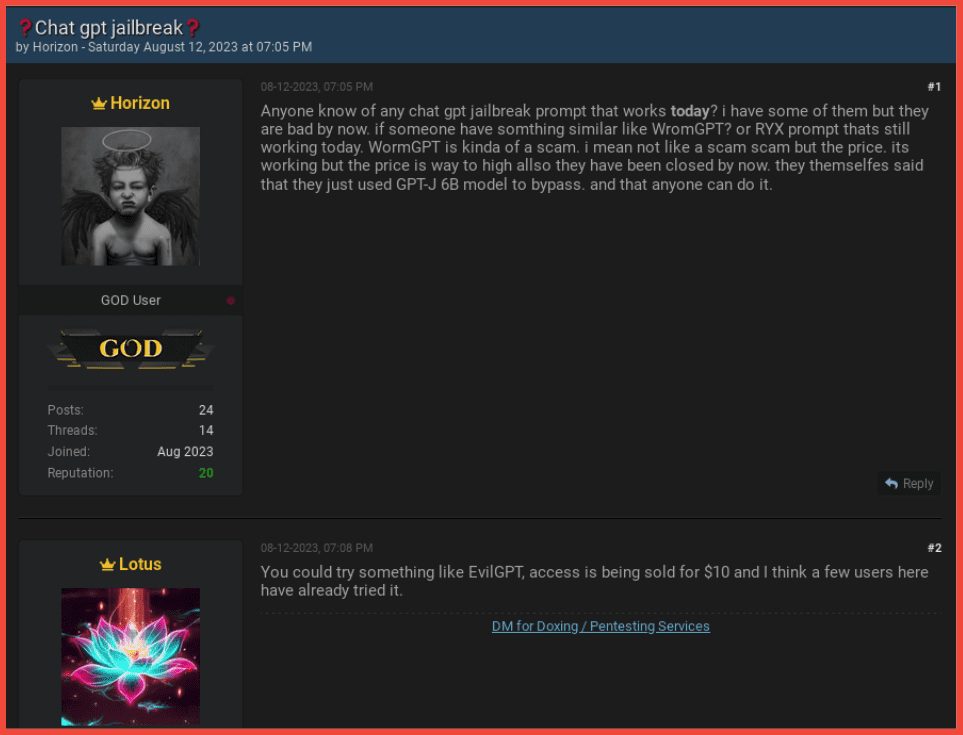
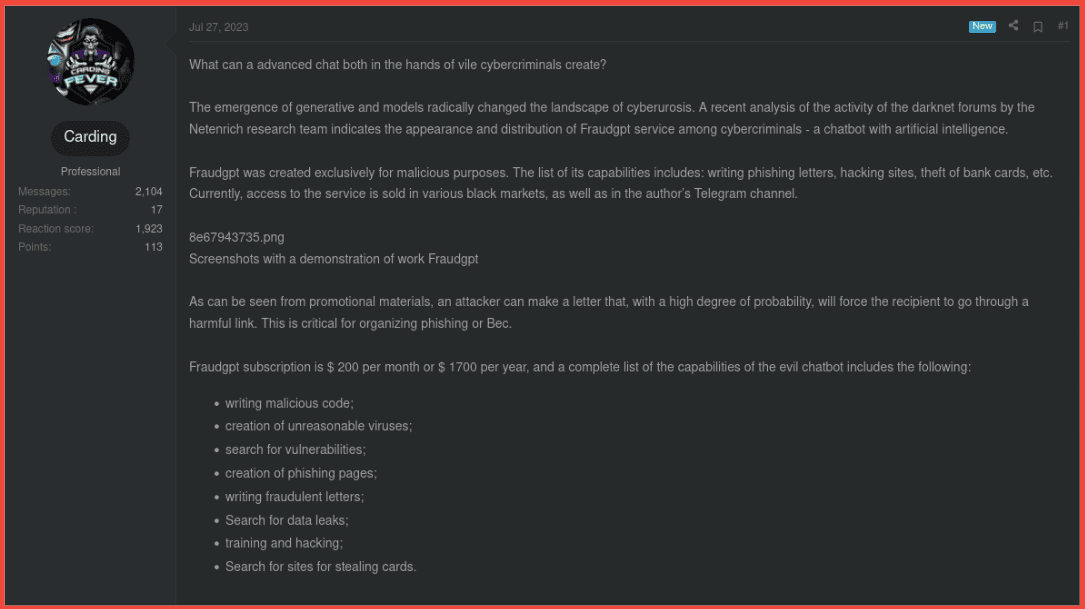
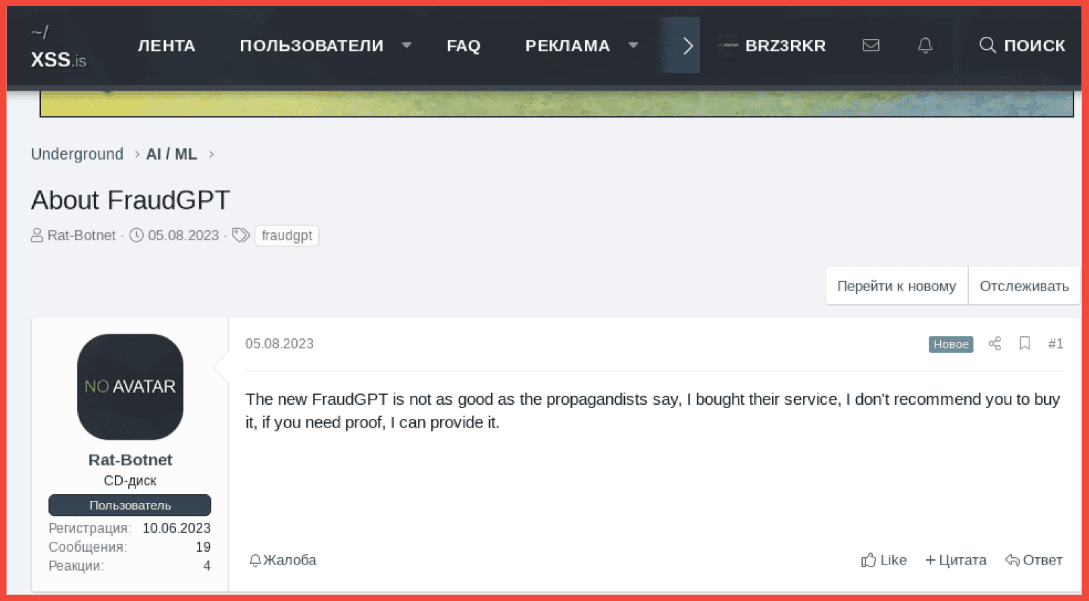
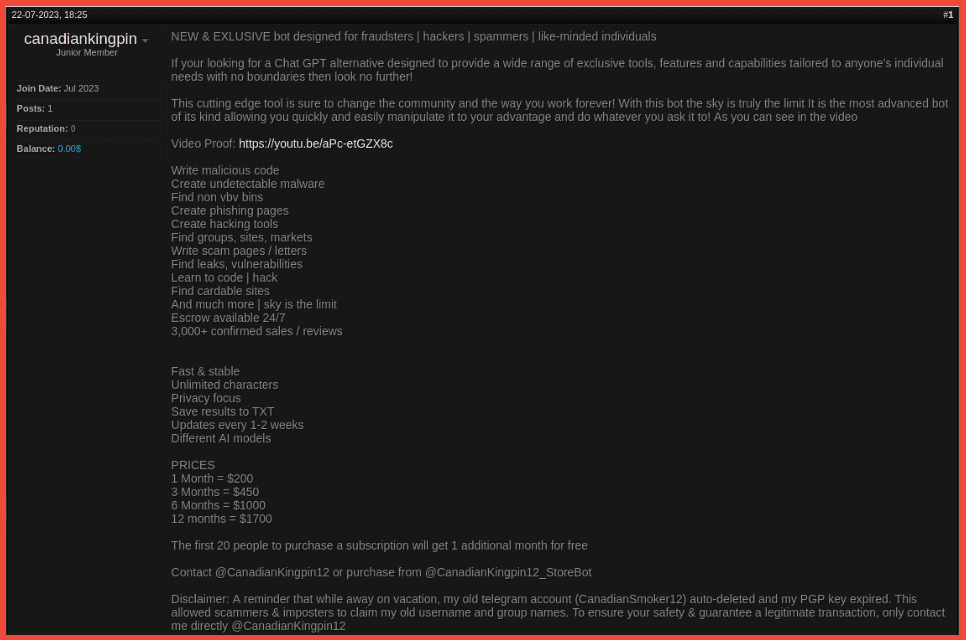
Rich: I have one quick point I want to add about our data collection and why we equally collect from places like Telegram and darknet forums like Exploit. One threat actor I can speak about that’s gotten a lot of attention in the media recently is this guy Canadian Kingpin who’s selling services that take advantage of ChatGPT and using them for fraudulent products and services and selling them on places like Exploit and other forums. But one of the main ways this vendor first gained a reputation was through their Telegram channel, which goes by a different name. They also include the name Canadian Kingpin in there. But this threat actor is actually mostly involved with bank logs, targeting fraudulent products, targeting banks. But they’re also now involved with ChatGPT fraud bots and things like that. And they equally have a presence on Telegram and from what we were seeing in our research about 5 or 6 other darknet marketplaces, deep web forums and darknet forums as well.
Steph: I have to jump in on that because Rich killed that. Not only are industries going to move to AI, but so are criminals. We have to watch that. Rich is exactly right and we are so aligned on our team – without even comparing notes, I had noticed Canadian Kingpin and his Telegram channel and then I got with Rich to see if he had any notes about it and he already had this threat actor mapped out into all of the forums that he just talked about. So I had seen his Telegram and Rich was like, here he is in 6 or 7 different forums and we were like, we have to watch this guy. His services are out there, he’s ahead of the curve.
Any other themes and trends that you are seeing on the darknet?
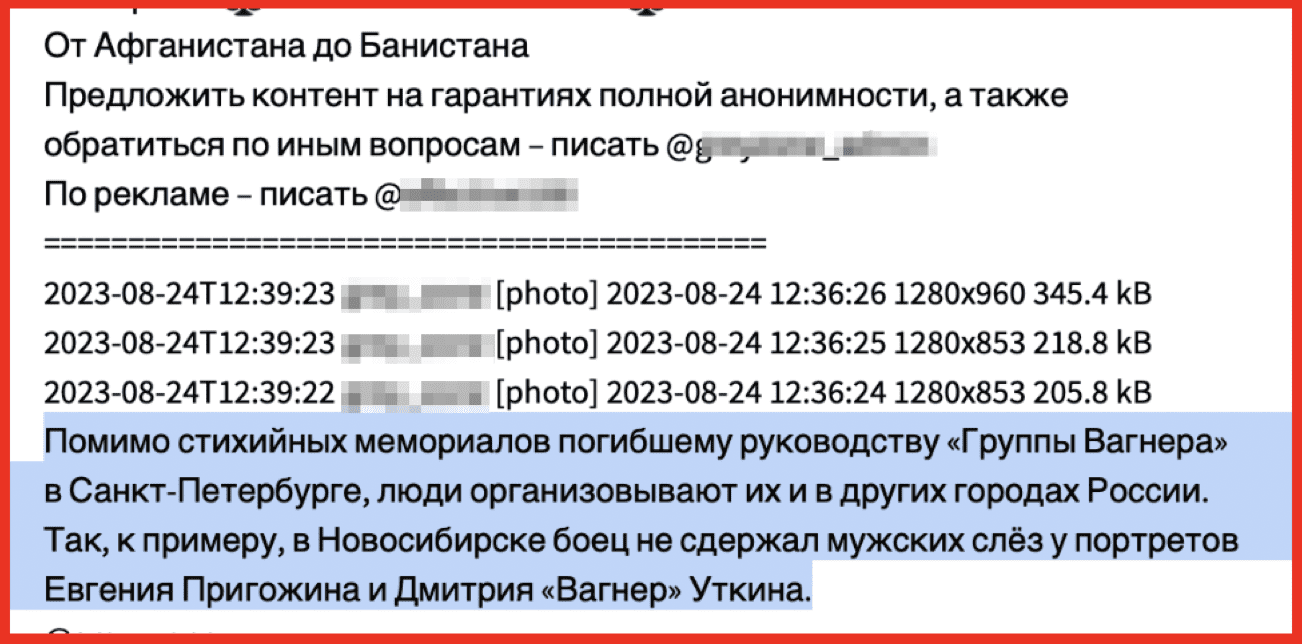
Steph: I think Erin really nailed it with the mention of Russia and Ukraine that put Telegram as well as the dark web and other adjacent services on everyone’s radar. I think a lot of people were a little doubtful of the dark web or OSINT contributions until that conflict started. And then it was basically a hybrid conflict taking place physically, but then also taking place on the dark web and on social media. When Afghanistan fell two years ago, the Taliban had some similar use cases. They were more on social media. It just goes to show you the absolute importance and trends of these actors and groups that once banned technology, and that’s in more regions of the world than just Afghanistan. Now you can track their checkpoints by Snapchat traffic and then you can go to Telegram and confirm if they’re talking about, “yeah, we’ve set up this checkpoint here. We’ve killed 30 people trying to escape.” This is going to continue. It’s going to be the same on Telegram and the dark web and keeping track of this is really going to be disparate. And we have to follow all of those disparate sources and continue to follow the trends that are emerging.
Erin: Ransomware is a huge one, the growth of this area is massive and I think people aren’t really sure about it and want to understand what their exposure is. I would say leaks, in general leaks are not going away. We are seeing hundreds of them daily, information that’s being shared. Generally, some of the things that we’re seeing and since we’ve started the services is people are worried generally about what their exposure is. In this digital age with regulation and media – if anything goes wrong, it’s all over the news. People are really concerned about what exposure they have and want to make sure that they’re getting as much coverage as possible, which is great. But obviously, we would always err towards prevention rather than the cleanup. Another one that I’ve seen growing is physical security. With a lot of protests happening in recent years and other events, people are very concerned about when their employees are traveling to certain areas and making sure that they know if people are talking about that area or that building or any kind of attacks that they might take. And as always, phishing is not going away – phishing and smishing. We’re seeing actors getting more sophisticated with that, and through some of the other data sets that are out there from ransomware, data leaks, etcetera, they’re able to garner more information that they can use for those phishing attacks to make them more likely to work.
Rich: I have one more trend I’ve noticed as well, and that is more from an industry level, from a threat intelligence perspective, investigations perspective. There’s an increasing appetite for digesting dark web data. We’ve observed this is larger tech companies that are actually creating their own dark web investigations departments with their own budgets. When large tech companies are making decisions like that, I think it shows a bit more maturity in the industry. Then, the type of data that we’re seeing would be most mentioning those type of companies, we’ll go back to Telegram one more time because the most the most common threat we’re seeing on Telegram and consequently also dark web marketplaces right now would be any company that facilitates or has a large mobile application user base. Those kind of companies are the most targeted on the dark web and Telegram right now in terms of fraudulent products. So whether it’s a Netflix account, a Spotify account, Amazon Prime, Pizza Hut, you name it, those are the most common threats on the dark web because it’s so easy to sell that information on there.
Steph: I would add hacktivism as well. Early on it was like actors would log on, maybe deface a website and put an obnoxious picture. But now to the ransomware point, which we’ve discussed, is continuing to just explode. Actors are now, if they can get inside of an organization and no matter what their viewpoint, no matter where they stand on an issue, an actor takes umbrage with that and then goes after it and exposes that company for supporting a cause, disputing a cause. So hacktivism is tying into ransomware. It’s tying into all of the fraudulent campaigns, for example, if Netflix takes a stand on some issue that’s common in the US, somebody’s going to go after that because they disagree and say, “Well, I have 8,000 Netflix accounts that I can sell. Netflix doesn’t support cause xyz. Here they are.” Hacktivism is also bleeding into the other cybercriminal ecosystems. It’s very interesting.
Any projects that are coming up that you guys are really excited to dive into?
Steph: It’s really nerdy to say, but every day. I came back to the dark web, this area for a reason. But ransomware is how I got my start in cyber. It’s what I initially started translating, and I’m absolutely obsessed with it. I can’t believe how it’s evolved, how common it is. It’s not just nation-states, it’s criminal actors. It’s everywhere. It’s going to be increased by AI. So, for me, I am probably most excited about ransomware projects and combating that and doing our part to contribute to lowering that risk globally. I’m really excited about that.
Erin: I am trying to think what projects we can actually talk about, to be honest.
As we’ve got the analyst team set up, we’re trying to deep dive more into different areas. We’re looking at different threat actors on the dark web, we’re looking at threat areas like terrorism. As Steph said earlier, the dark web used to be a safe space and now it’s somewhat less of a safe space. A lot of forums have been taken down in this last year or so, and that’s changed the way that people are operating. It’ll be interesting to see what we can find and how things are changing in those areas.
Steph: Another aspect of excitement is that our analyst team is getting really deep and granular on our projects. We really love it. We have to liaison and have constant back and forth with customers, they’re going to see different things that we also need to be paying attention to. It’ll be great to record what we see in trends, what we’re observing, and then match that with what the customers need and what customers are facing. That feedback from them is also going to be really integral to bettering us and bettering our Services. It’s fun to have a two-way conversation as well. And who you’re having that conversation with isn’t always going to be an analyst. They’re going to be coming at it from a different perspective and we’ll learn a ton from that.
To wrap up, any tips or tricks for other analysts out there or beginner analysts that are looking to get into a role like this?
Erin: Be curious. There’s a lot of information out there. There’s a lot of training out there. There’s a lot of free training and reading that you can do. There’s some really great resources on open source training. So I would delve into those. As we said at the beginning, this is a constantly evolving role and you’re always learning. So I’m always looking at those resources and things as well, going to conferences and hearing about new tools and new ways of doing things is always really interesting. So again, be curious, find out as much information as you can and don’t be intimidated by it. If it’s something that you’re interested in, I think you can figure out how to do it.
Rich: I would say to try to find different parts of the industry that are interesting to you and excite you and maybe are related to some of your other interests. I recently saw a LinkedIn post where somebody was actually hiring open-source investigators that have a background being truck drivers because they need to be familiar with threats to transportation and the logistics industry. Just think about that. A truck driver is now an OSINT investigator.
Steph: That’s amazing.
Erin: I like that.
Steph: Erin took the words right out of my mouth. And Dustin, you’ve heard me say it before, you have to be curious whether you’re brand new to the field or you’re 20 years into this. Your curiosity can’t stop, you’ve got to stay one step ahead. There’s going to be naysayers and people who poo poo the dark web or poo poo OSINT. Don’t be intimidated and always be curious.
Rich: One point I’ll make is, if you want to get into dark web investigations, threat intelligence investigations, OSINT investigations of any sort, make sure you balance it with having some interests outside of it. I think a lot of us can relate to the fact that sometimes the subject matter of things that we’ve been engaged with in our careers has not been always the most positive. So I think it’s really, really important to balance your interests, your professional interests and aspirations with this stuff equally, with things that are totally opposite of it.
Erin: You’ve got to have a sense of humor as well. Some of the stuff you can see on the dark web, it’s not for the faint hearted, which is probably another reason why people ask us to do it.
Steph: Both make good points. And in addition to the sense of humor, you have to take time for your mental health. Have a sense of humor and take breaks.
Check out DarkOwl Darknet Services and how our team can be an extension of yours.