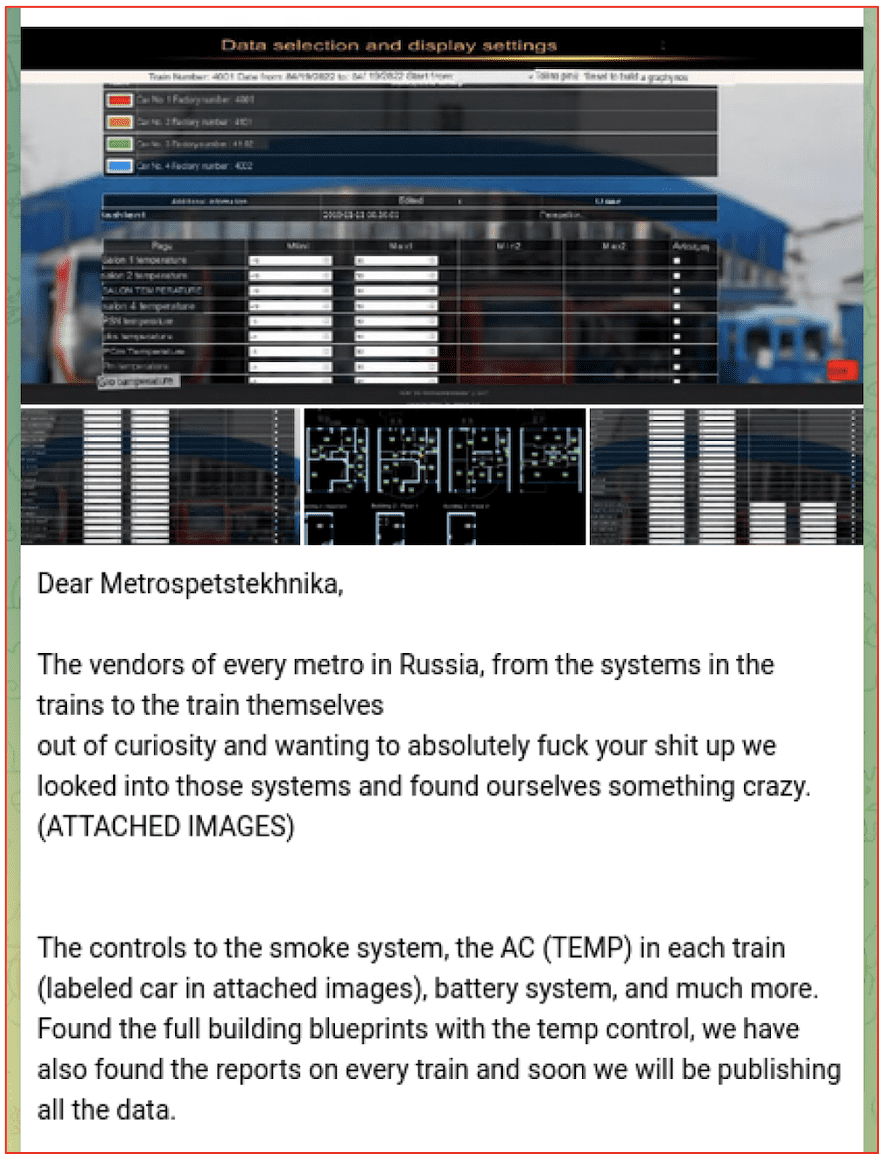
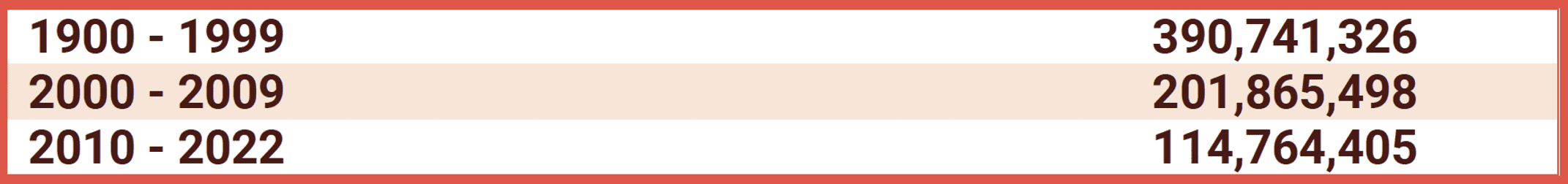
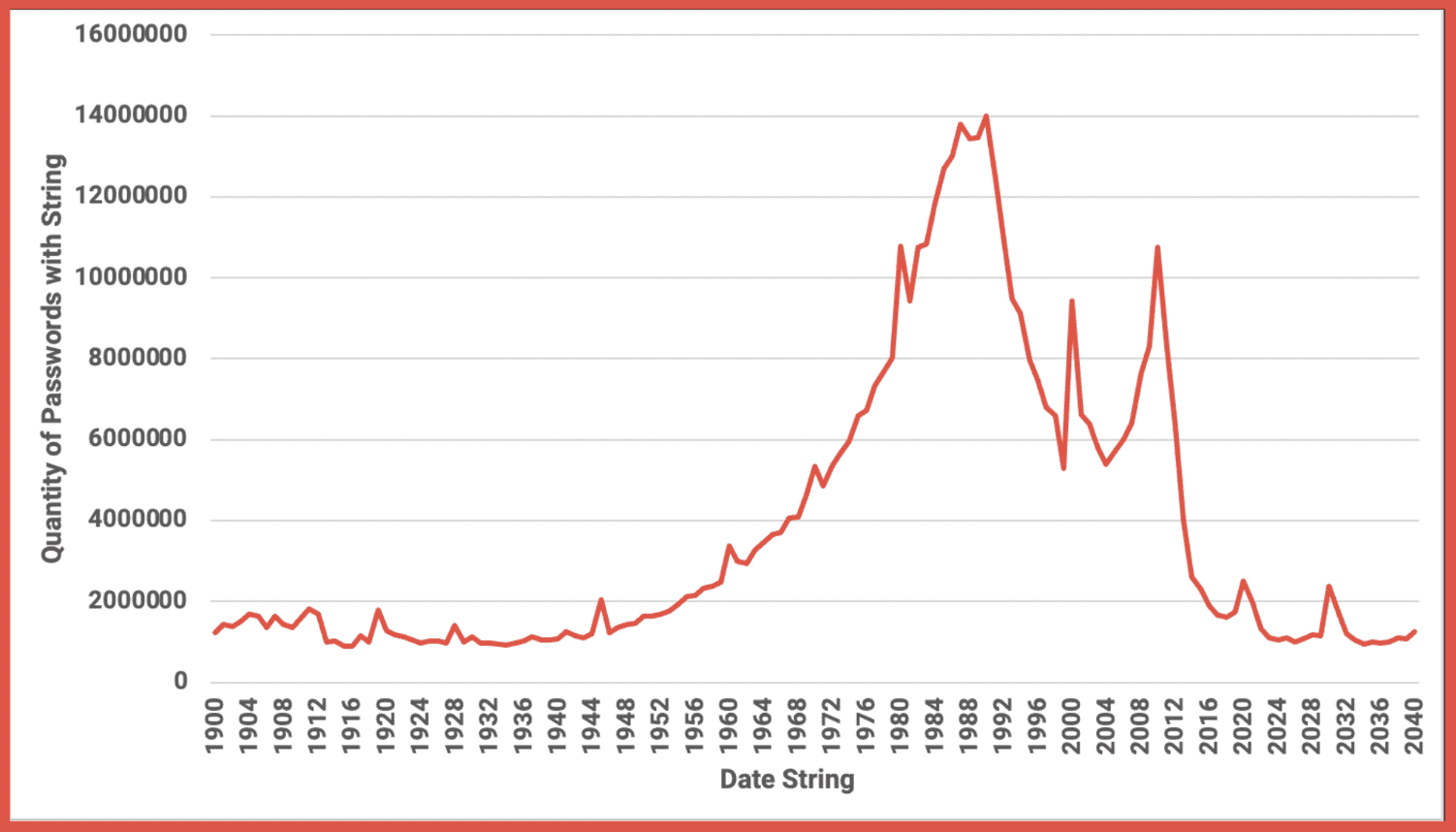
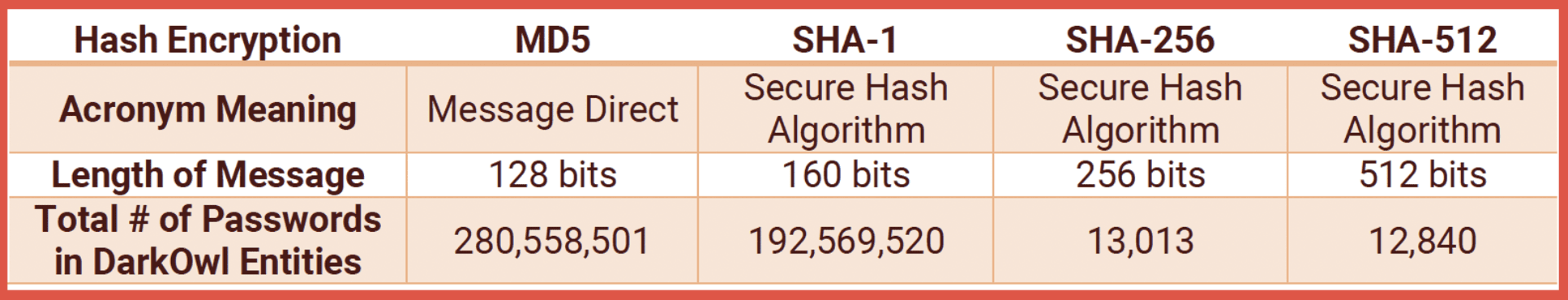
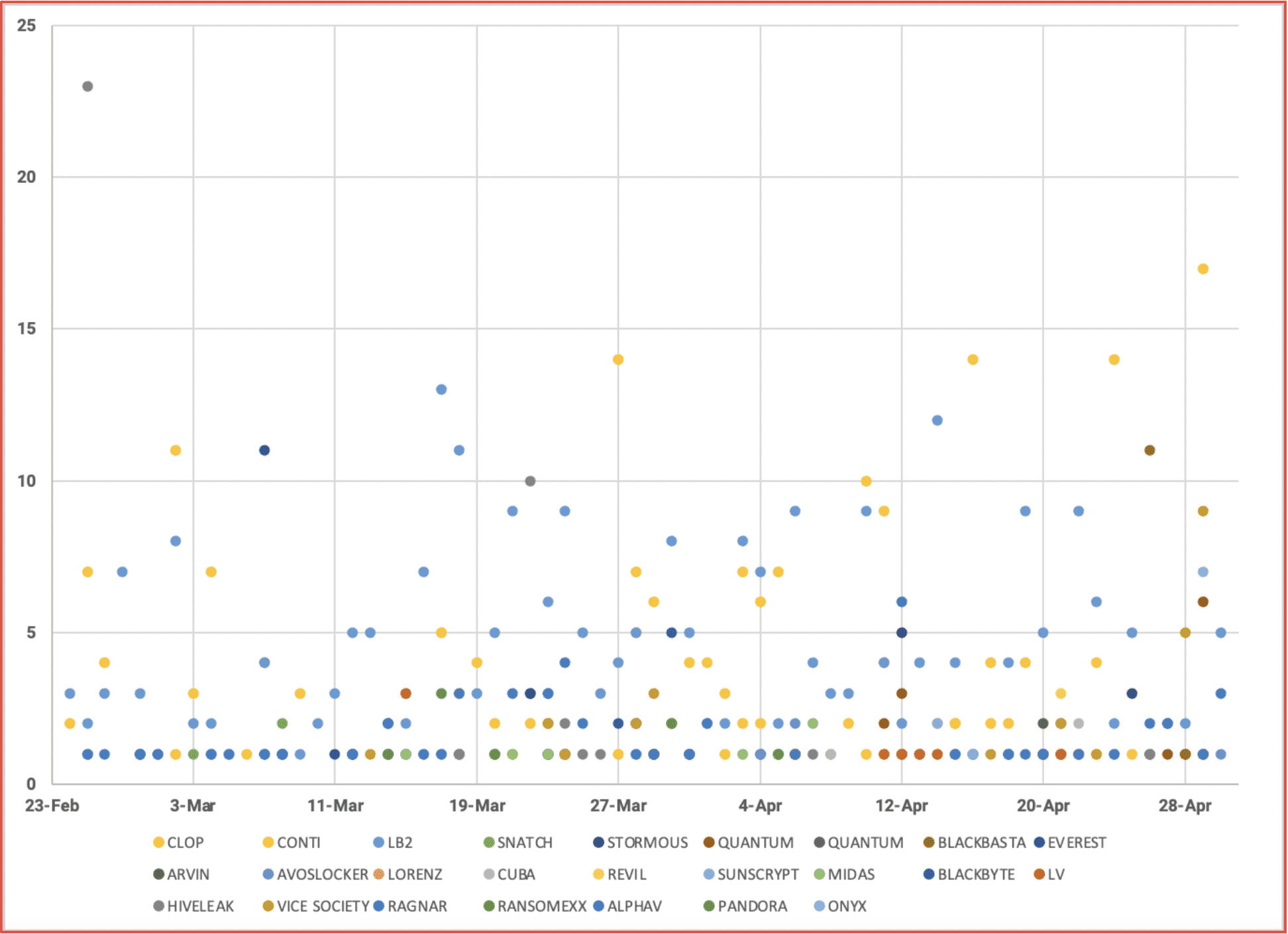
May 19, 2022
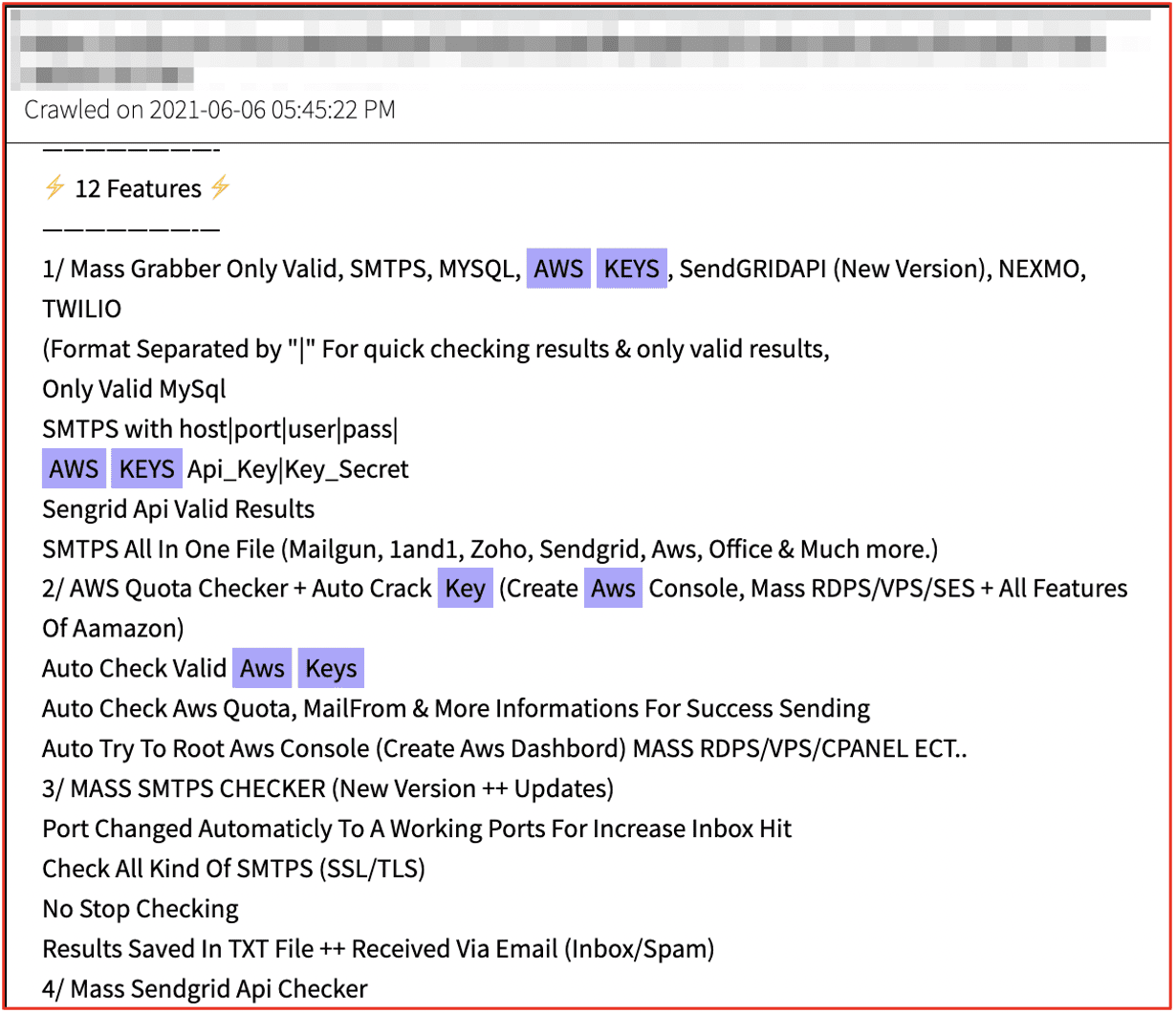
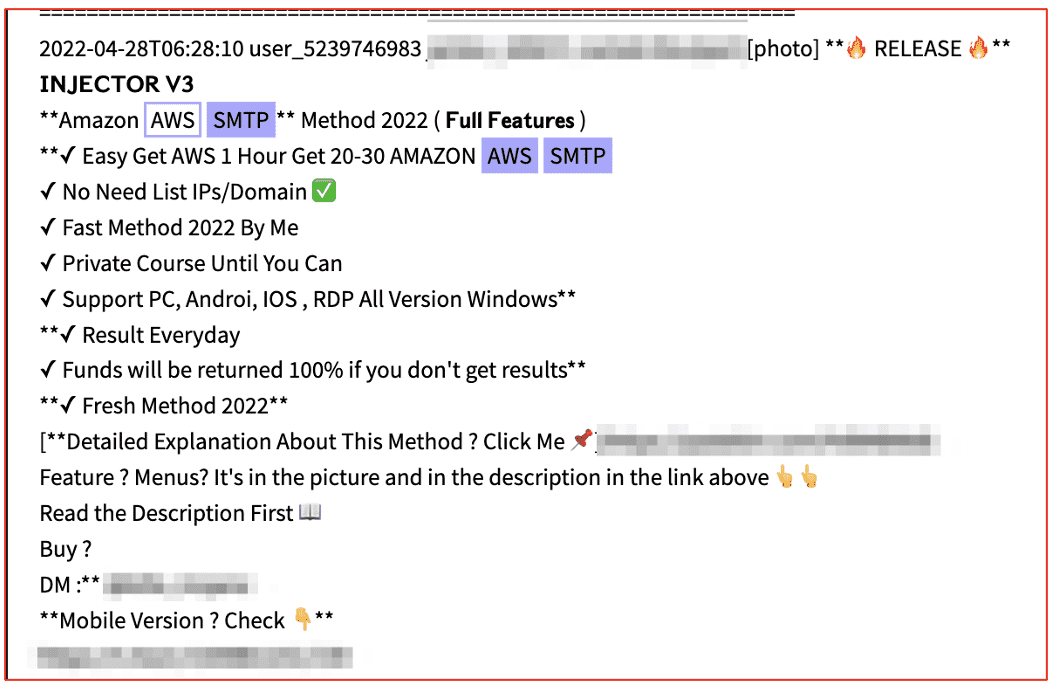
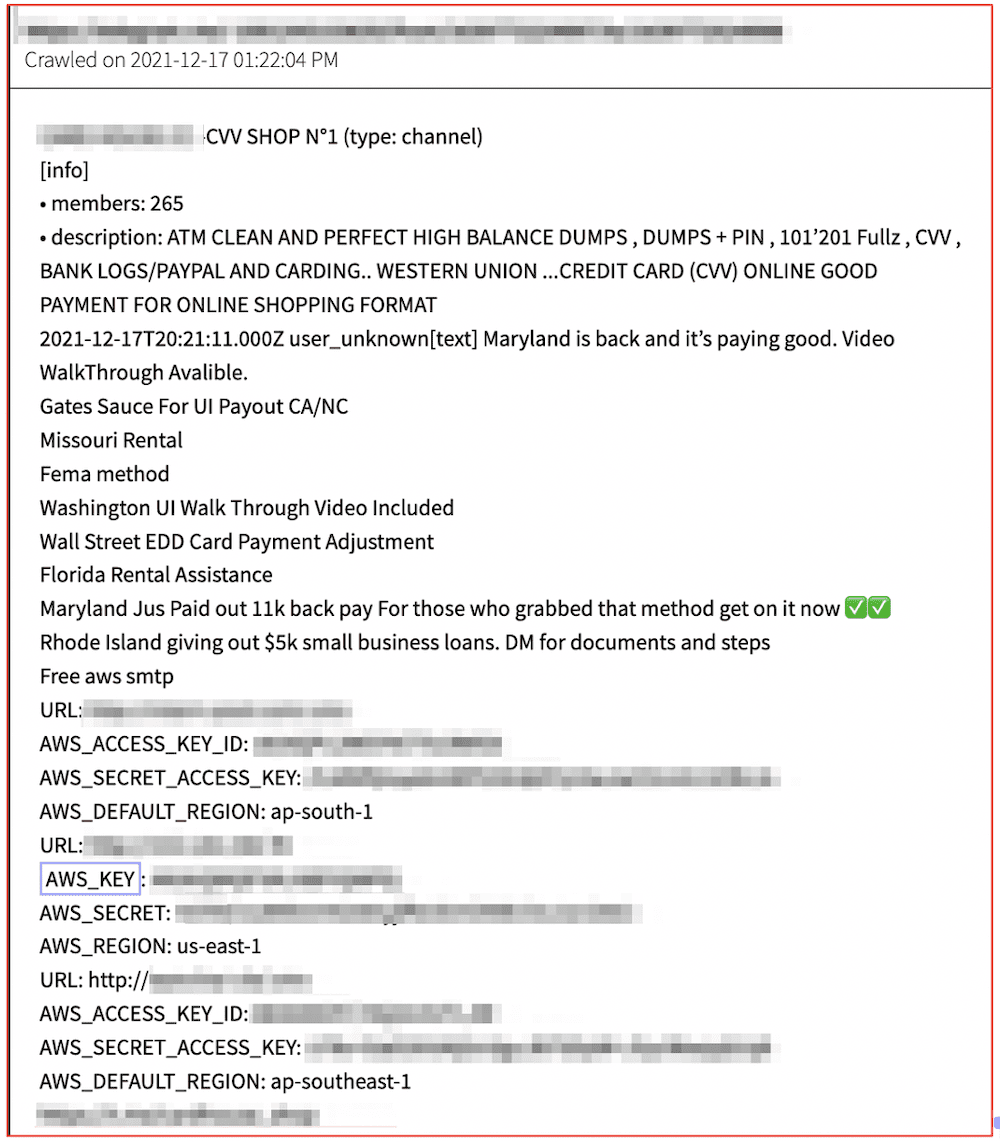
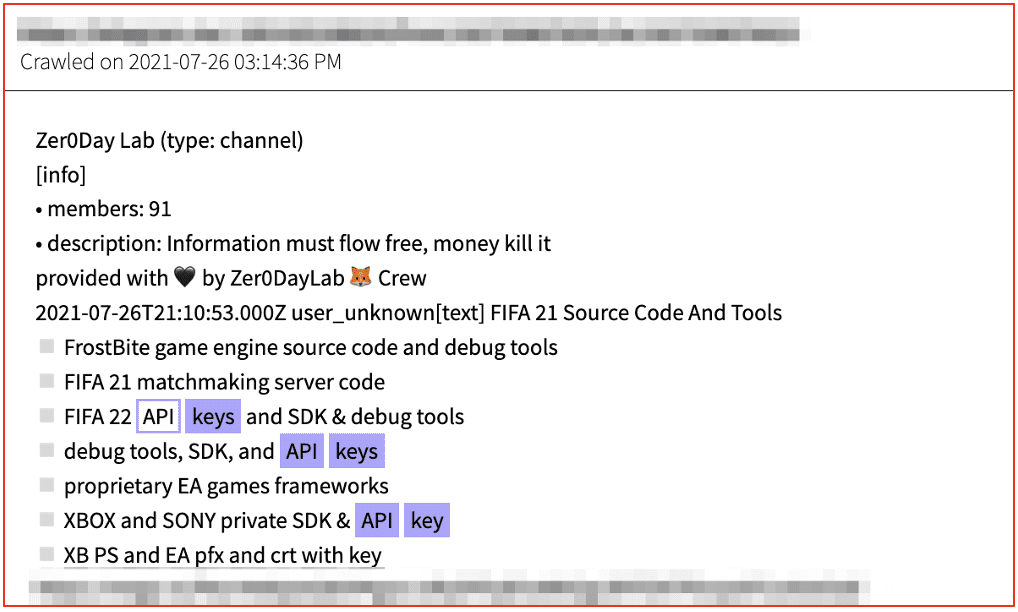
In recent months, DarkOwl has observed an increase in the number of posts advertising a specific type of malware known as “information stealers” or simply, ‘infostealers’ by the underground cybercriminal community. Most of the infostealer promotion appears on darknet and deep web malware/hacking forums and are available for sale across many darknet marketplaces.
Information stealers are designed to steal sensitive information from a compromised device. Most information stealers are designed to covertly access the application where data is stored, e.g. internet browser, and gather personal information such as authentication and credential data, crypto wallets, browser session cookies, etc, and remotely transmit the data back to the cybercriminal for conducting additional financially-focused extortion crime.
Infostealers are commonly delivered by social engineering, such as malspam campaigns and phishing emails. Attachments are typically included in the email with a lure, or a legitimate-looking trap encouraging victims to open the attachment and install the malware onto their device. Information stealers are on the rise and promise lucrative business opportunities for cyber criminals.
In this research, our team reviewed some of the most widely proliferated infostealers on offer on the darknet and discovered an elaborate data exfiltration ecosystem, with low-entry cost, providing cybercriminals access to a wealth of personal information without the victim’s knowledge. We also learned many infostealers are offered in alignment with a malware-as-a-service (MaaS) or “stealer-as-a-service” (SaaS) rental model with subscriptions-based access to the malware executables and associated command and control C2 botnets.
Redline
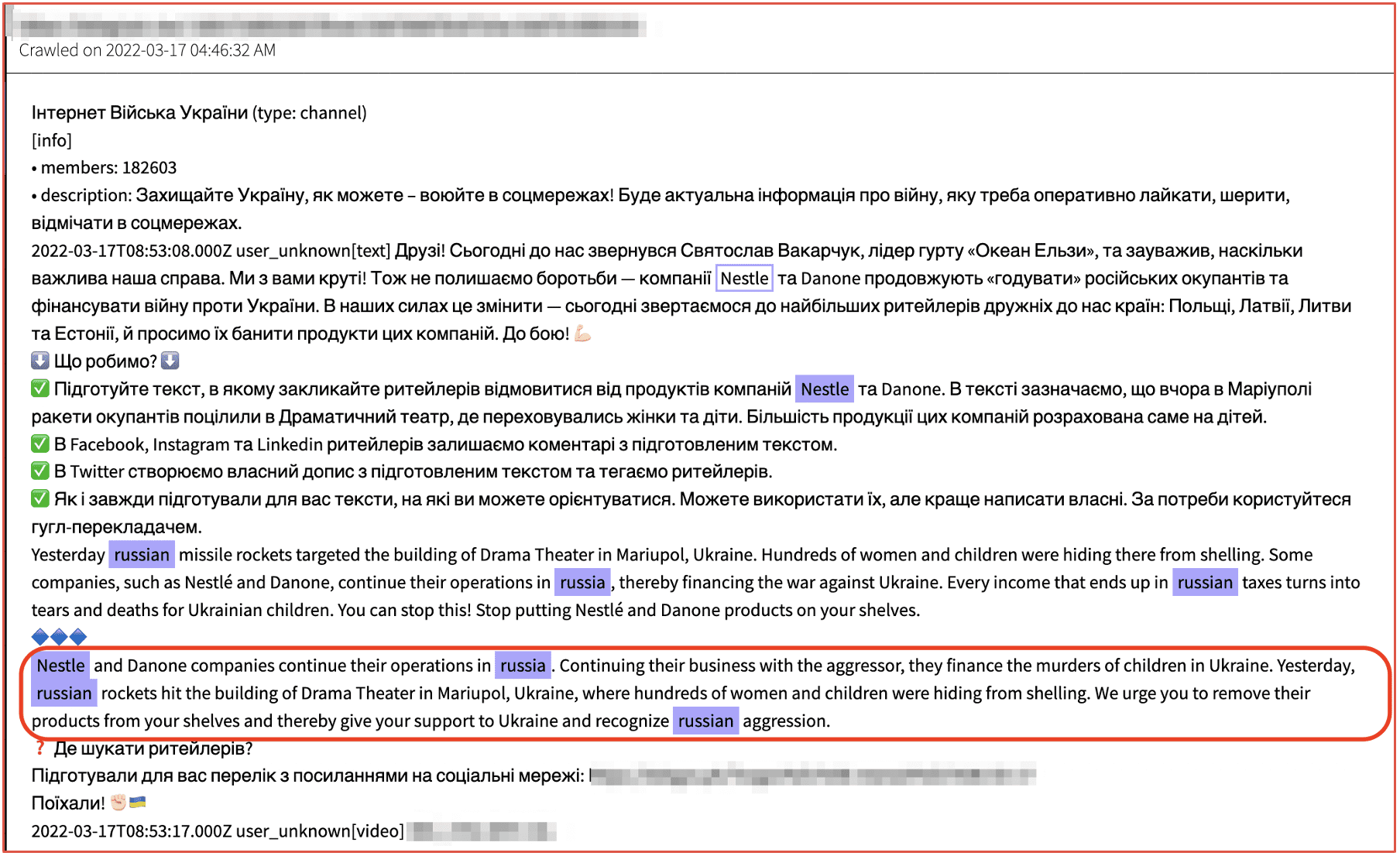
Redline is one of the most popular, widely recommended, and notorious information stealers available on the market. The first advertisement for Redline appeared in March 2020. Redline can be used for exfiltrating credentials, cryptocurrency wallets, browser information, as well as FTP client application data. The stealer also collects information about the victim device, including OS, system hardware, processes, and system language.
According to OSINT security researchers, the stealer can load remote payloads in addition to the SOAP protocol for covert C2 communication. Recent versions of Redline leverage SOAP, or Simple Objects Access Protocol over NET.TCP which helps obfuscate the communication data shared between the victim and the C2 servers. SOAP also facilitates smaller packet sizes, which translates to a smaller malware footprint.
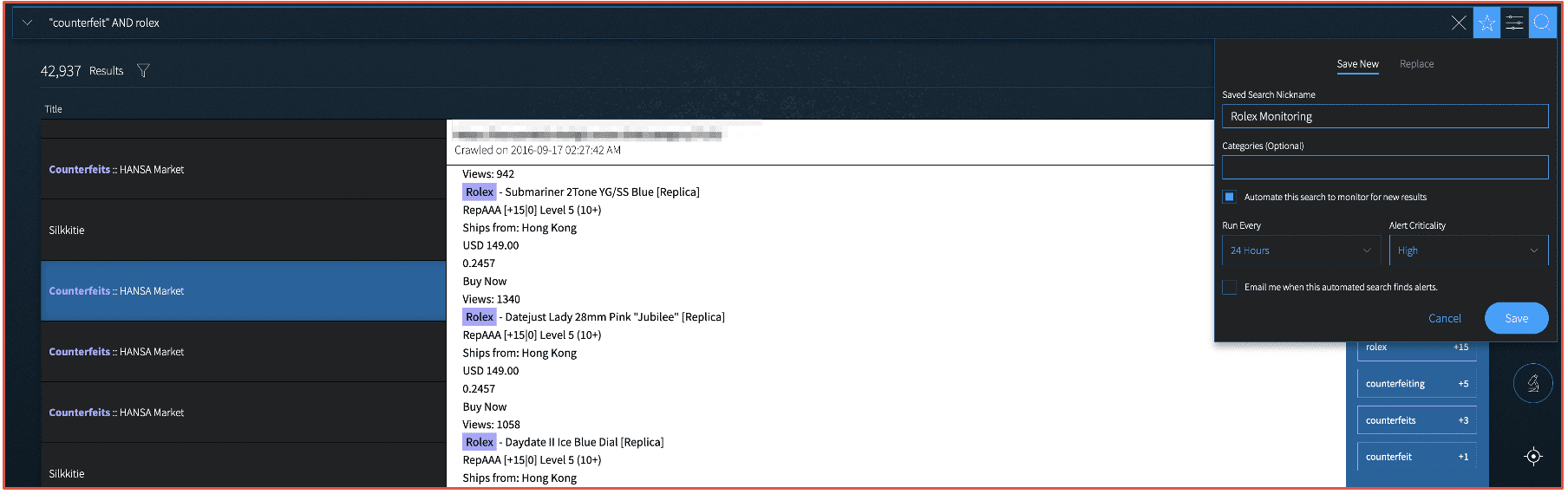
Redline is available on darknet marketplaces like DarkFox for as little as $150 USD for the “lite” version, $200 USD for an advertised “pro” version, or $100 USD for a monthly subscription with restricted access. Other marketplace offers indicate that the Redline team advertise various versions and configurations of their infostealer to support varying levels of threat actor sophistication.
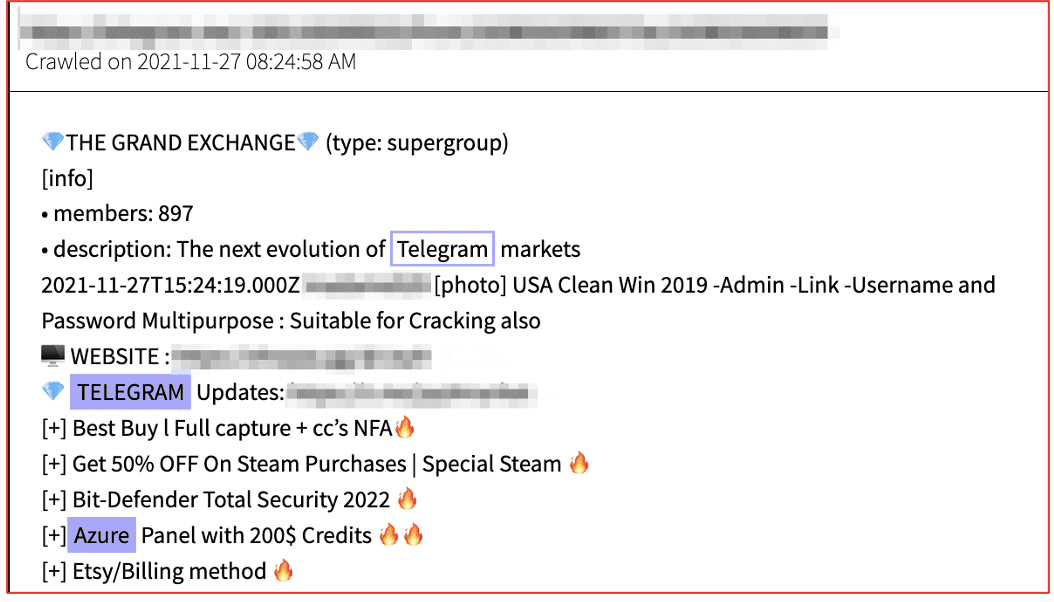
The malware is written in C# and uses a SOAP API to communicate with its C2. Attackers are contacted on Telegram and then can use the C2 panel installed on the victims’ device to use Redline. Redline source code is available on Github with 142 lines of code and built-in commands. (Source: Available Upon Request)
Figure 1: Offer for Redline Stealer for sale on Darkfox Darknet Marketplace
Racoon
According to open sources, Raccoon Stealer, a.k.a Racelar, was first offered for sale in April 2019 and associated with a Telgram user @gr33nl1ght. The Racoon stealer exfiltrates victim login credentials, credit card information, cryptocurrency wallets and browser information. It can also download and execute arbitrary files by command from the C2, operated from Telegram.
DarkOwl has observed advertisements in the darknet for Raccoon offered under the malware-as-a-service model for $75 USD a week or $200 USD per month. Some advertisements on Telegram decrease with longer commitment, e.g. $500 for two months and $499 for four months. The Raccoon stealer executables are available on Github and the source code has been archived in Pastebin.
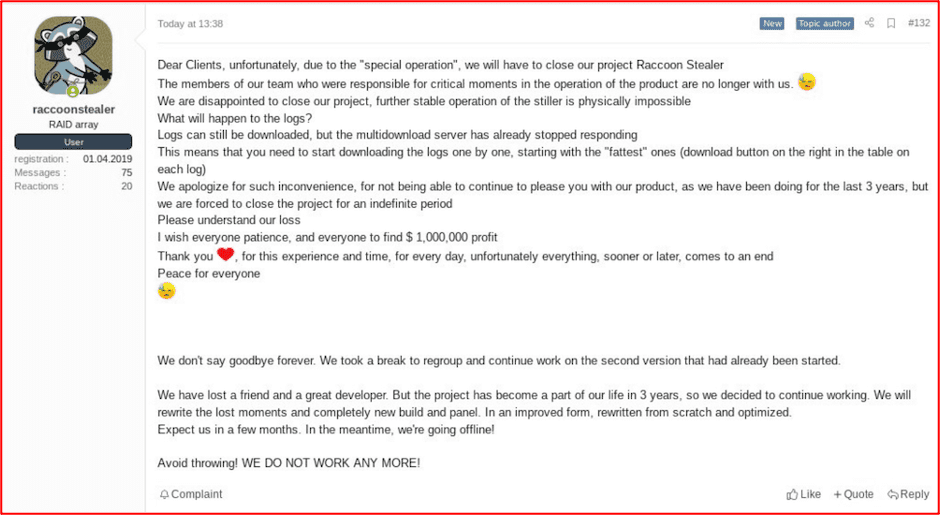
Despite the success of their operations, in March, the Raccon stealer group announced on a darknet forum they would be suspending operations due to the war in Ukraine and critical team members who are no longer available for key operations.
Figure 2: Raccoonstealer Representative Announcement of Shutdown due to Ukraine-Russia War
Vidar
According to analysts with Cyble, Vidar, also sold as Vidar PRO stealer, was first identified back in 2018. This infostealer variant steals sensitive information such as passwords, banking information, IP addresses, browser history, login credentials and crypto wallets which are sent back to threat actors’ command and control.
The stealer is widely advertised on Telegram and a DarkOwl Vision document captures a Vidar offer on Telegram for $500 USD, but prices on average range from $250 USD to $750 USD for the stealer malware. (Source: DarkOwl Vision)
Vidar is written in C++, and employs Mastadon servers for command and control. An interesting and in-depth analysis of the stealer code can be found on Github details how its stealer infrastructure operates. (Source Redacted but Available Upon Request)
Predator the Thief
Predator the Thief was first offered for sale on a Russian Darknet Forum on June 17, 2018 by a user known as Alexuiop1337. Predator the Thief is more comprehensive than a browser stealer alone and is able to take screenshots of the victim’s desktop in addition to typical exfiltration of credentials, payment data, crypto wallet information stored in the victim’s internet browsers. (Source)
The malware also includes anti-debug techniques, advanced evasion, and anti-analysis tricks for additional sophistication. It is still widely circulated and updated regularly. A Github repository containing the infostealer’s 332 lines of code is still maintained by a user with the same alias as the original post from 2018. (Source Redacted, but Available Upon Request)
The listing is currently offered on darknet forums as well as Telegram channels. The stealer sells for $150 USD, with an option of paying $100 more for the Clipper module allowing buyers to customize crypto wallet stealing options.
Mars
Mars stealer is the most recent version of OSKI stealer and was first seen circulating around July 2021 on a Russian darknet forum. (Source)
During our analysis, we also discovered Instructions for building the Mars’ stealer panel and using the “builder” are available across numerous darknet forums including how to turn off the exclusion for the stealer working in Commonwealth of Independent States (CIS) designated countries. This infostealer is advertised for $160 to $200 USD and is continually under development and improvement complicating Yara rule creation and AV detection.
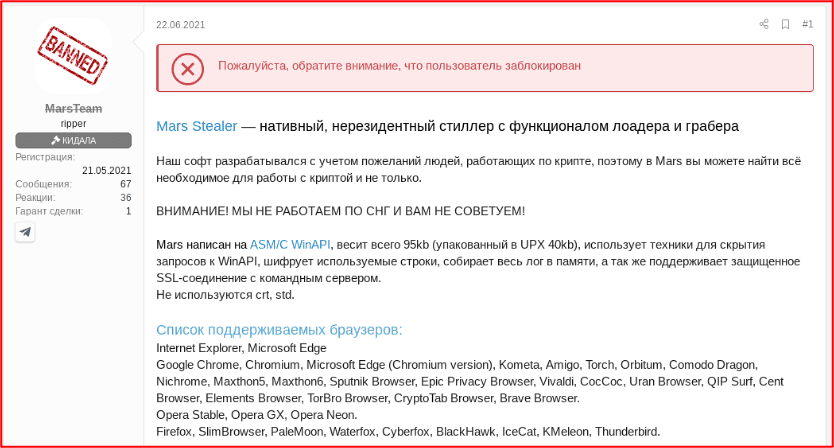
In early May, users on a darknet forum began circulating a cracked version of the software for use by the community. Many of the forum users warn against using ‘cracked’ versions of the software as there is higher risk of backdoors. We observed that a prominent MarsTeam account which shared some of the original advertisements for the Mars stealer on one popular darknet forum is banned and tagged as a scammer. The ban brings into question the stealer’s legitimacy.
Figure 3: Original post about the Mars Stealer whose Representative has since been banned
Regardless, a GitHub repository containing code for the Mars Stealer is owned by a developer with an impressive collection of various malicious software and other stealers in their repositories, including Loki and Oski stealer as well as Redline. The current version of Mars stealer is using Google Ads to put cloned OpenOffice sites high on search results.
Blackguard
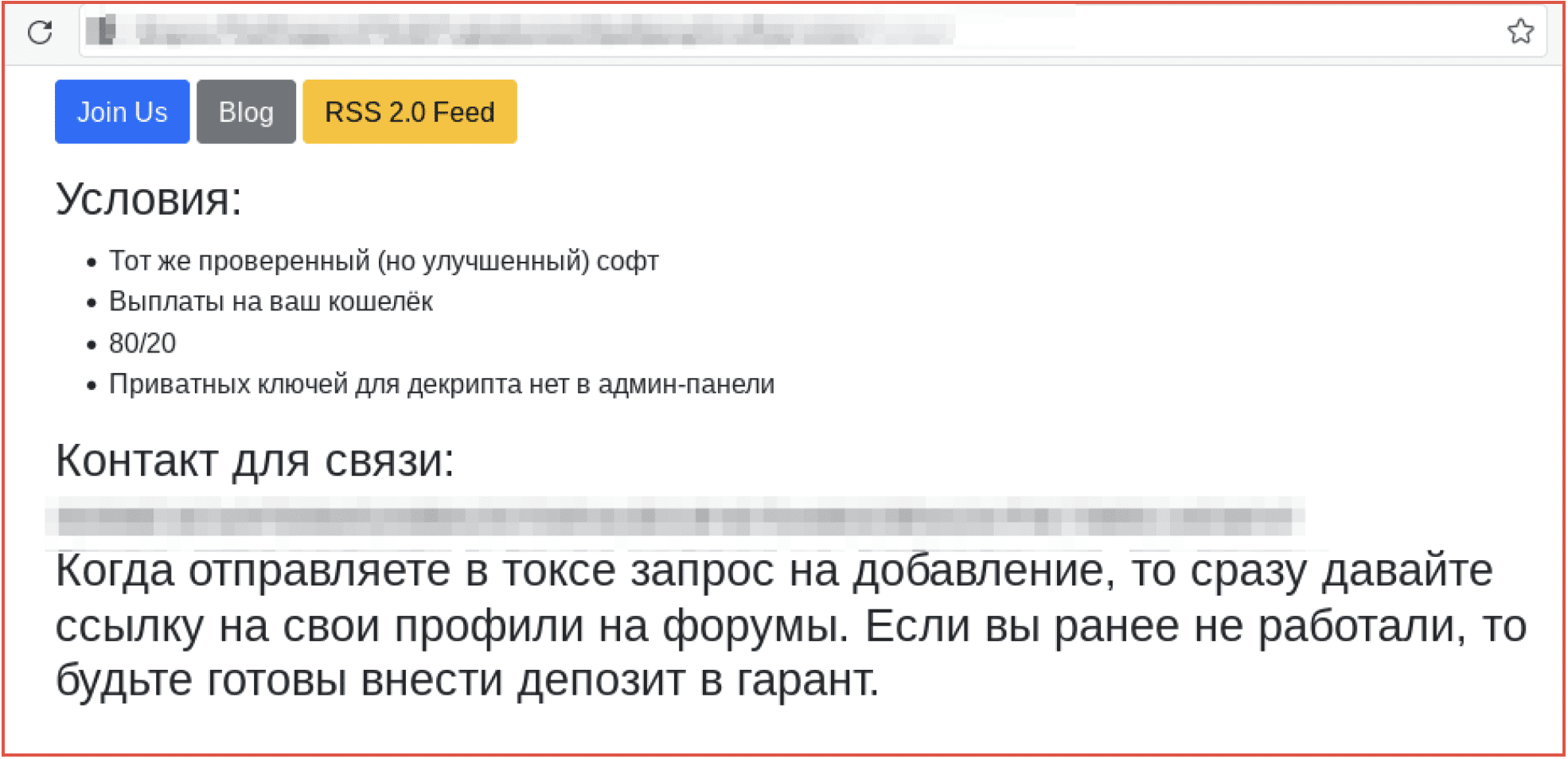
According to open sources, Blackguard first appeared in Russian forums in January 2020 and was advertised “for testing purposes.” The infostealer spent a year circulation before it was advertised for commercial use in 2021. Blackguard steals web browser data like extensions, cryptocurrency wallets, email, messengers, and other sensitive device information that can identify the victim.
Blackguard is sold as a malware-as-service where stolen information is archived into a zip file which is sent back to the C2 server. The source code is developed in .NET and is access is available for $200 USD a month or $700 for a lifetime subscription. (Source)
Acquisition of the stealer is generally limited to exchange with the malware’s representatives directly Telegram and Jabber.
Despite its popularity among cybercriminals and the existence of a cracked version recently in circulation, some dark web forums users are not impressed with this information stealer nor its price tag. Some users recently nominated the Blackguard stealer for the “worst stealer 2020-2022 award” and warn others from using this stealer for legitimate malicious cyber campaigns.
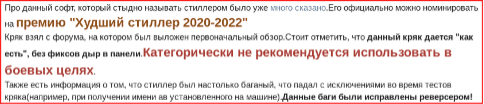
Figure 4: Forum post criticizing Blackguard stealer malware
[Figure Translated]
“The sold software, which is a shame to call a stealer, has already been said a lot. He can officially be nominated for the “Worst Stealer 2020-2022” award Crack taken from the forum where the initial review was posted. It is worth noting that this crack is given “as is”, without fixing holes in the panel. It is categorically not recommended to use it for combat purposes.There is also information that the stealer was so buggy that it fell with exceptions during the crack tests (for example, when getting the av name installed on the machine). These bugs have been fixed by the reverser!”
In other darknet threads, forum users stated that the Blackguard information stealer is “trash”, replete with errors, and requires too much overhead – in the form of persons to operate, especially for the $700 USD price.
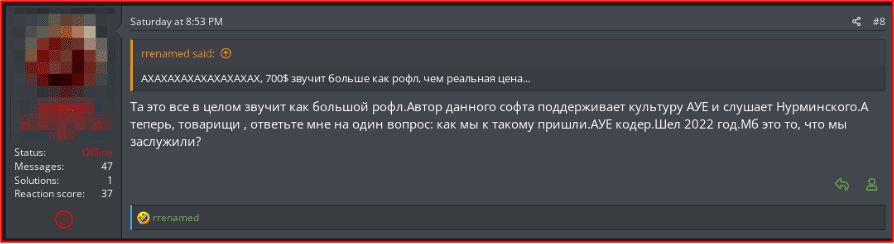
Figure 5: Forum post criticizing Blackguard’s lifetime subscription prices
[FIGURE TRANSLATED]
“AHAHAHAHAHAHAHAHAH, $700 sounds more like a rofl than the real price…” That all in all sounds like a big rofl. The author of this software supports the AUE culture and listens to Nurminsky. And now, comrades, answer me one question: how did we come to this. AUE coder. It is 2022. Is this what we deserve?”
The criticisms caused quite a controversy with the stealer representative on the forum confronting many users directly and suggesting they take it up with the moderators in Arbitration.
Jester
Jester is an information stealer that Cyble first noticed in darknet forums in July 2021. It targets the victim’s browser cookies, credentials, email clients, instant messaging applications, crypto wallets, gaming software, VPN and FTP client application data. (Source)
Advertisements on a darknet forum advertise that the stealer-C2 connection is encrypted using the AES-CBC-256 algorithm, with servers located in the tor network, all logs will be redirected to the user’s Telegram bot, and collection occurs in memory instead of on disk to evade detection. Jester is available on RuTor with links to pastebin sites explaining what the stealer does and how much it costs in different languages. The “Builder Jester” malware-as-a-service offering is priced based on length of subscription with $99 USD per month and two “forever” options for $250 USD and another for $999 USD.
Cyble suggested a Github owned by user L1ghtM4n linked to the Jester malware, but further investigation shows that user is linked to a repository called DynamicStealer. DarkOwl has not been able to confirm if the two malware source codes are affiliated; however, some very recent reporting suggests that Jester might be affiliated with the Eternity malware family.
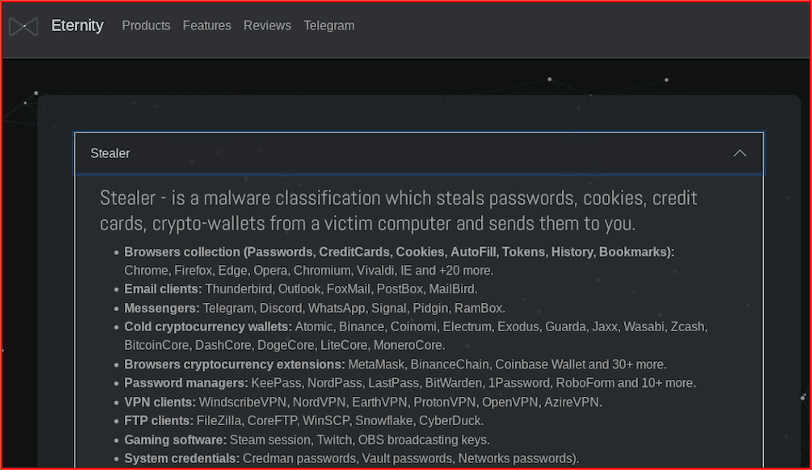
Users promoting Eternity deny the connection, but flaunt that Eternity offers not only a cookie stealer, but a cryptocurrency malware variant, a cryptocurrency address clipboard “clipper”, a DDoS botnet, Worm and Dropper system, as well as a ransomware variant. A new Eternity stealer Tor service claims they successfully exfiltrate a considerable amount of information from the victim including Signal contacts and password manager data on the device like LastPass.
Figure 6: Eternity stealer promotional information provided by the threat actor
Taurus
Taurus Stealer, also referred to as Taurus project is an information stealer that has been observed promoted by the authors of the Predator the Thief on Russian chat forums in early April 2020. It can steal VPN, social media, credentials, cookies, autofill forms, popular cryptocurrency wallets, and the history of Chromium and Gecko based browsers. It collects information on installer software installation and system configuration, sending it back to the attacker to be used for further lateral exploits across the compromised machine.
Like Mars Stealer, the source code will not execute on victims located in the CIS region, suggesting the authors are likely located in the Russia Federation.
A lifetime license to Taurus is available for $100 USD and can be customized for as little as $20 USD extra. One advertisement we observed on Telegram offered a 10% discount on license cost and the first update is available for free.
Both Taurus and Predator the Thief use BitsTransfer in their PowerShell commands; Bits Transfer is short for “Background Intelligent Transfer Service”, part of Microsoft’s Operating System, and is a way for programs to ask Windows to download or upload files from a remote HTTP or SMB file server.
Taurus links to download malicious GitHub repositories whereas Predator The Thief PowerShell works with LNK files after the stealer has sent the log. When BitsTransfer is executed in Taurus, it downloads three separate files from the Taurus Project on Github owned by andrewwilm. Github has since removed the repository.
In late December, the source for Taurus stealer + its builder, were leaked on a popular darknet forum. Earlier this week, a darknet user offered multiple software iterations of both Predator the Thief and Taurus for $4K USD in Monero cryptocurrency – stating the code was “straight from the author’s hands.” This implies that both Predator the Thief and Taurus stealers were most likely coded originally by the same person.
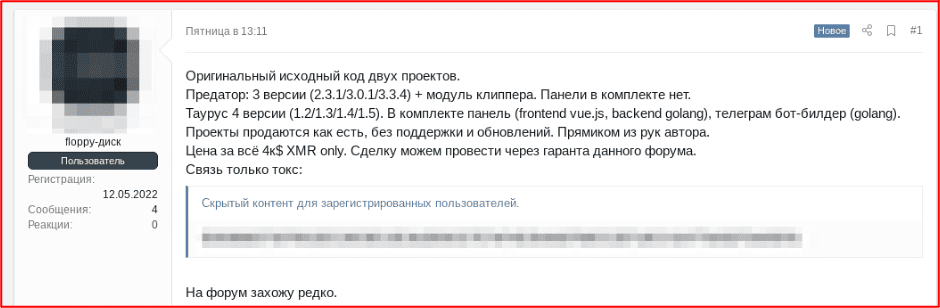
Figure 7: Offer of source code for sale for Predator the Thief and Taurus stealer software
[Figure Translated]
“The original source code of the two projects.
Predator: 3 versions (2.3.1/3.0.1/3.3.4 ) + clipper model. The panel is not included.
Taurus 4 versions (1.2/1.3/1.4/1.5). Included panel (frontend vue.js, backend golang), telegram bot builder (golang).
Projects are sold as is, without support and updates. Straight from the author’s hands.
The price for all 4k is $XMR only. We can conduct the transaction through the guarantor of this forum.”
Other Information Stealers
While the stealers mentioned above are the most widely circulated and discussed across the information security community and cybercriminals, we also found other less known stealers that are currently active in the underground.
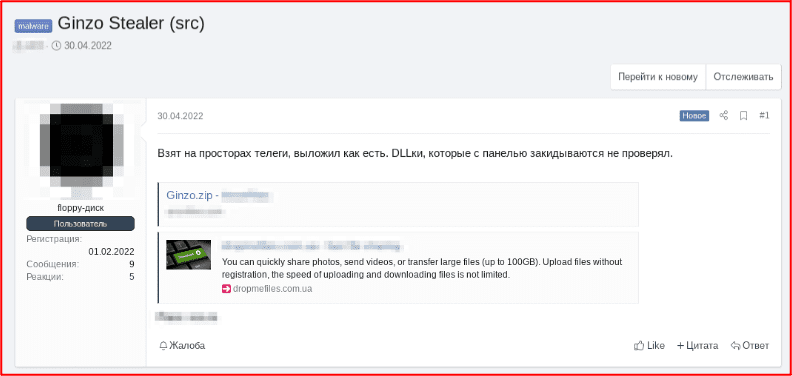
Ginzo
In late April, we found an “as-is” version of source code for a stealer known as “Ginzo” available to download from a popular third-party anonymous data repository. The Ginzo stealer targets Telegram session data when loaded on a victim’s device, along with Internet browser cookie data, desktop files, cryptocurrency wallet data, and Discord tokens.
Open-source reporting suggests that offering the stealer for free to download is a ploy to gain reputation and “get criminals hooked” on using Ginzo’s threat actors command and control servers.
[TRANSLATION]
“Taken in the vastness of the cart, laid out as is. DLL keys that are thrown with the panel have not been checked.”
Figure 8: Source code for Ginzo stealer offered for download
Grim
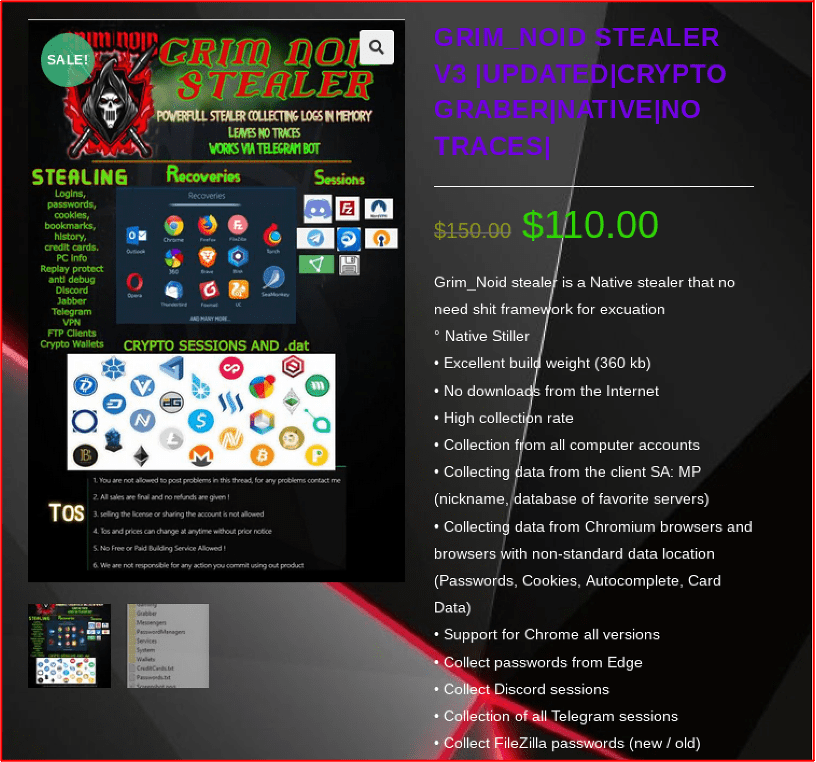
Another controversial stealer, called “Grim stealer” hosts its own deep web vendor shop and market offering their stealer for sale. The site claims there is a Telegram scammer which is causing the controversy on darknet forums as they are using the malware team’s logo and pulling a classic case of ‘alias hijacking’ to discredit the stealer’s reputation.
Like Eternity, the Grim shop offers their Grim Noid stealer for $110 USD as well as other products such as: a stealer builder for $60 USD, cryptocurrency clipboard “clipper” for $50 USD, a remote access trojan (RAT) for $100 USD, and botnets for the Surface Web and Telegram for $300 USD.
The technical specifications advertised are consistent with other infostealers on the market.
Figure 9: Grim Noid Stealer offered for sale
The market for information stealers is booming on the darknet, with stealer software variants readily available offering high volume data exfiltration, a relatively low-entry cost, and reliable C2 botnet support.
All the stealer families we reviewed advertise a supportive criminal ecosystem, providing cybercriminals steady access to a wealth of digital tokens and personal information that can be abused for subsequent fraud, digital identity theft, and potentially catastrophic critical infrastructure and supply chain attacks.
Curious about something you read? Interested in learning more? Contact us to find out how darknet data applies to your use-case.