[Webinar Transcription] Leveraging Dark Web Intelligence for Real World OSINT Investigations
March 21, 2025
Or, watch on YouTube
Attendees of this webinar, hosted with Carahsoft, learned about how in today’s world, Open Source Intelligence (OSINT) plays a critical role in uncovering threats and mitigating risks by leveraging publicly available information. This webinar dove deep into the practical side of OSINT investigations, focusing on how dark web data can be strategically utilized to enhance threat detection and risk assessment for organizations.
During this webinar, the Director of Intelligence of Collections at DarkOwl, demonstrated the power of DarkOwl Vision through real-world examples, including:
- Tracking stolen credentials from a recent data breach
- Monitoring dark web marketplaces for insider threats
- Identifying emerging cybercrime trends
- Analyzing chatter on forums to predict potential attacks
- Protecting executives and high-profile individuals
Participants gained hands-on insights into gathering, analyzing, and interpreting OSINT data, with a focus on applying dark web intelligence to solve real challenges.
NOTE: Some content has been edited for length and clarity.
Erin: Hi everybody. I am the Director of Intelligence and Collections at DarkOwl and I’m going to talk you through some background on the dark web and some OSINT investigations.
What we’re going to cover today, I’m going to give you a little bit of background on who DarkOwl are, what the dark web is, why it’s important, how we can use it in OSINT. And I’m going to do a couple of use cases and walk you through some examples of what we see on the dark web and how you might be able to use it for OSINT.
A bit of background about DarkOwl. We’ve been around since 2014, but collecting data I would say from the dark web in earnest since around 2017-2018. So, our goal is to collect data from the dark web so people are able to use that data for their investigations and to protect their organizations. We allow people to do that in a number of different ways, so you can access data through our platform Vision, which I’ll be showing you how to use today, but we also have APIs and data feeds which allow you to access dark web data, and the idea really is challenging to access the dark web, and also it can be against policies and violations to access it. It’s not easy to access and there are things on there that you might want to avoid. So we allow you to access that data in a secure way.
What kind of data do we have? We have layers of the deep and dark web as well as some surface web, although we are primarily a dark web company. Everything that you see here in red is something that we do collect from. We’re always looking to increase our coverage though and look at other areas where we see criminals, cyber threat actors, insider threats, people proposing violence, operating. So, we’re always on the lookout for other areas that we can collect from. But as I said, we’re primarily dark web, TOR, onion sites is where we get most of our data from, but we do also collect some surface websites, things like Doxbin, paste sites, certain forums where we see extremist activity being discussed, as well as underground criminal forums and markets and discussion boards. We also collect from Telegram and Discord. We see a lot of criminal activity operating in those areas. And this just gives you a breakdown of the volume of data that we have.

I believe there’s a polling question up on the board for you now. And that’s just to highlight, are there any messaging apps you’re seeing as part of your investigations at the moment that you would like to have more coverage of. As I mentioned, we do cover Telegram and Discord, but we’re always looking for other options. So please fill that in. You can have multiple choices. But going back to the slides, you’ll see that we’ve got a large volume of data that we collect. We have been collecting since 2017, and we do not remove any historical data because that can still be important to your recent investigations. And so, you can see the numbers that we have here. We also extract particular entities, so email addresses, IP addresses, credit cards and crypto addresses that can help you with your recent investigations. And we also have a large volume of data leak records that we’ll talk about in a little bit more detail.

And this is just to give you an overview of how our ecosystem works. We do have the Vision UI where you can access all of our data as well as APIs. We have several API products that allow you to generate scores and risk assessments based on the exposure that an individual has as well as context information about our data leaks.

And we also provide darknet services. So, for those that don’t have the resources and/or do not have the experience working with the dark web, we are able to do investigations and OSINT investigations on your behalf and produce reports regarding whichever you’re investigating. So, this is our Vision UI, it supports Boolean logic, it has darknet data within it, and it can also be used for alerting, but I will go through that in a lot more detail later in the presentation. But so, just so that we’re on the same page, let’s start with talking about what is the dark web.
No OSINT presentation is complete without an iceberg slide so this is our obligatory iceberg slide which breaks down the surface net, the deep net and the darknet.

We really do focus on the darknet you know collecting from onion sites, TOR, ITP, ZeroNet that is specific software that you need to download to access that and also, it’s not indexed so you need to know the URL that you are going to in order to find that information. So, it makes it a lot more difficult to navigate and identify sources that are going to be beneficial to you as part of your recent investigations. And that’s one of the things that we assist with. We, you know, have broad coverage across the dark web. We’re always looking to identify new sites and new areas where individuals are communicating or buying and selling goods. And so that allows you to be able to search that information. We also do do the deep net. So, this is not indexed by search engines, usually behind a firewall of some kind or password protected. It’s not easy to access, but it’s easier to access than the dark web. You can still do it using your usual browser. And there are a lot of forums and marketplaces and vendor shops, et cetera, that sit on the deep net. And then you also have the surface net. So this is, you know, the internet we’re all used to. It’s indexed by search engines. So, you can, you know, go to Google, go to Yahoo and find a site that you’re looking for and it’s all open. I would say more and more we are seeing fights on the surface web that are also engaging in criminal activity. People seem to be less concerned about obfuscating what they’re doing then they had traditionally been and also, I think law enforcement’s been quite successful in taking down some dark net sites and that has kind of moved people onto the surface net so that’s an interesting trend that we’re seeing at the moment and that’s why we cover those areas as well as just the dark net.
To give you a little bit of history on the darknet, It started in around 2000. The Darknet Tor project itself was actually created by the US Navy as a means of secure communications for their operations. And then they decided to make it an open source tool. The Tor project is a not-for-profit that runs Tor and the onion sites and the bridges, et cetera. It’s always worth noting that there are fully legitimate reasons for using the dark web for those that live in countries where communications may be limited and, you know, they may not be able to access mainstream media, things like that. Tor can be used for that. And also, people who do really want privacy. They can use the dark web to enable that privacy. I’m not going to go through everything here on this slide obviously it goes up to 2020, but you can see that there’s been a lot of things that have happened in the darknet, things like cryptocurrency becoming more prevalent and being a semi-private way of people transacting and law enforcement operating on the dark web to take down sites has been a game changer as well. But there’s a lot of things that have happened on the dark web ecosystem and continue to happen to this day.
Okay, so why is dark web data important? I’ve kind of touched on this, but a lot of criminals operate on the dark web. So, we see people communicating on the dark web in forums, in messaging apps, having conversations, but we also see people selling and buying goods. We see people offering services. There is a lot of activity that happens on the dark web that can be useful to your investigations. And there’s also sites where people’s data is released. So, data leaks, stealer logs will go into in a little bit of detail, as well as things like DoxBin where people’s information is released. So, it can really help you in your investigations identifying information about individuals, but also can help you to kind of protect individuals from an executive protection perspective and we’ll talk about that in a bit more detail as well.
While we’re level setting on dark web, hopefully everyone on this webinar is aware of what OSINT is, but it’s basically the collection analysis and dissemination of information that is gathered from publicly accessible sources and these are a couple the sources that are out there that I think are familiar to most people doing OSINT investigations. But people don’t always think of the dark net. I think some people think it’s scary. There are questions about whether or not it’s truly open. But it is in fact open. It’s harder to access, but all of the data is out there for people to go and view if they choose to. So, I like to think of it as a tool in the toolbox that an OSIN investigator has. you know, you should be looking at social media, you should be looking at public records, you should be looking at, you know, other mainstream websites that are out there, things like the Wayback Machine, but the dark web is an important element of that investigation and gives you kind of a broader overview of information that you might not get from other sources. I feel like, again, I have the obligatory iceberg slide, this is my obligatory AI generated image. You can see that it’s AI generated because it’s the Dark Wab and not Dark Web. It seems that when you give it a few too many prompts, it gets confused, but this is my obligatory AI image.

Okay, so but what things do we see on the dark web? So hopefully people are familiar with some of these. I think some are more well known but marketplaces are definitely, you know, a mainstream and one of the things that first started in the kind of criminal ecosystem of the dark web with things like Silk Road, which was not the first market, I believe, Farm was, but, you know, marketplaces for buying and selling drugs, illicit goods, hacking tools, tutorials. You can purchase hitmen, you can purchase all manner of strange things, whether or not that’s legitimate or not is something that we can also discuss.
There’s also a wide range of forums, so people kind of talking about things that interest them. Breach forums is probably one of the most famous forums out there that works in buying and selling data and sharing data. But there’s also extremist forums out there, things like the in-sell community, right-wing extremists operating on forums too or people just discussing general things not all of the forums are bad. There are some social media sites that are on the dark web too. There are mirrors of things like Facebook and Twitter that appear on the dark web so people can access them in countries where there might be censorship so that that’s one of the more legitimate areas and also we talk about social media and I’ll go onto this in the next slide as a dark web adjacent area where we do see criminals operating on mainstream social media as well.
Cryptocurrency obviously is the currency of the dark web. We still see bitcoin as the largest currency being used but things like Monero and Zcash and more of the privacy coins are also popular. You you know, wallet explorers, there are dark web wallets, there are tumblers, mixers, et cetera. So a lot of cryptocurrency activity can occur on the dark web as well as being, you know, again, perfectly legitimate information, there are a lot of new sites that are on the dark web. The BBC has a new site. I believe CNN has a new site. And there’s also just kind of other sites that share information. These can be kind of data repositories, you know, when information is leaked by whistleblowers that can sometimes appear on the dark web as well. And then we have data leaks. So rather than kind of whistleblowers, that’s more stolen data and data that’s been taken illegally. And in that vein, we also have ransomware. So, a lot of ransomware groups have leak sites on the dark web where they will kind of shame their victims into paying the ransom by saying that they are a victim and they’re gonna release the data. If the victim does not pay the ransom where they do usually then release that data which is downloadable on the dark web.
But as I mentioned, there’s also some things that we refer to as dark web adjacent. Oh, there’s a poll question. So, what areas of the dark web are of most use to you. So I’ve gone through some of them, but it’d be really interesting to know from your perspective what is most beneficial for you and your investigations and your day-to-day job. But in that thing we also have some dark web adjacent. That’s what we refer to as sites that aren’t or messaging apps or platforms that aren’t exactly on the dark web, but they’re still being used by the same community of people, i.e. usually criminals or extremists or some form of bad guy for one of the better phrase. Things like Telegram, ICQ, Jabber, Discord is a gaming site as is Twitch, where we see people are sharing classified information, they’re making threats. A lot of the so-called gore community are very active on places like Discord tends to be younger generations and people that are into gaming, as you would expect. But these are all areas that we think it’s important to also have coverage of in order to, you know, have a full coverage of these communities and these groups and how they’re interacting. Obviously, I would say there’s been some changes in Telegram. In recent months, but that we are still seeing a huge amount of people operating on Telegram in a malicious way. And then the surface web, marketplaces, vendor shops, forums, as I mentioned before, excuse me, we are seeing some people that are operating in the same way they operate on the dark web on the surface web. You can find those vendor stores and those marketplaces, which I think is an interesting evolution and how these communities are operating.
Okay, so there is a lot of data on the dark web as well. So, we’ve kind of talked about the general themes and the types of sites that there are, but there’s also a lot of different types of data and a lot of different types of information. So, a huge amount of PII appears in data leaks and is discussed on some of the sites as well. Financial information, There’s a huge ecosystem of financial fraud, people selling credit card data, selling banking information, selling details of how to operate in a financial fraud way. So, we see a lot of people doing tutorials and giving guidance about how to conduct some of these scams. There’s also a huge, as you would expect, cyber and hacking community. So, people trading malware, and exploits, and different tools that you can use, you know, the phrase script kiddies, individuals who aren’t necessarily that sophisticated enough to build code or build these vulnerabilities, but they can purchase them and execute them and still kind of use them for criminal activity. So, we see a lot of trading of those kind of things, drugs, obviously, and cryptocurrency I’ve also mentioned. There’s a lot of activity that can come from this kind of data. We see cyber-attacks. We see data exfiltration and hacking. There’s also cyber espionage. I mean, APT groups are hard to identify, but they’re definitely operating in some of these places. And insider threats as well, people, you know, talking about sharing information that they should not be sharing or making threats to their organization. These are all the types of things that we see on the dark web.
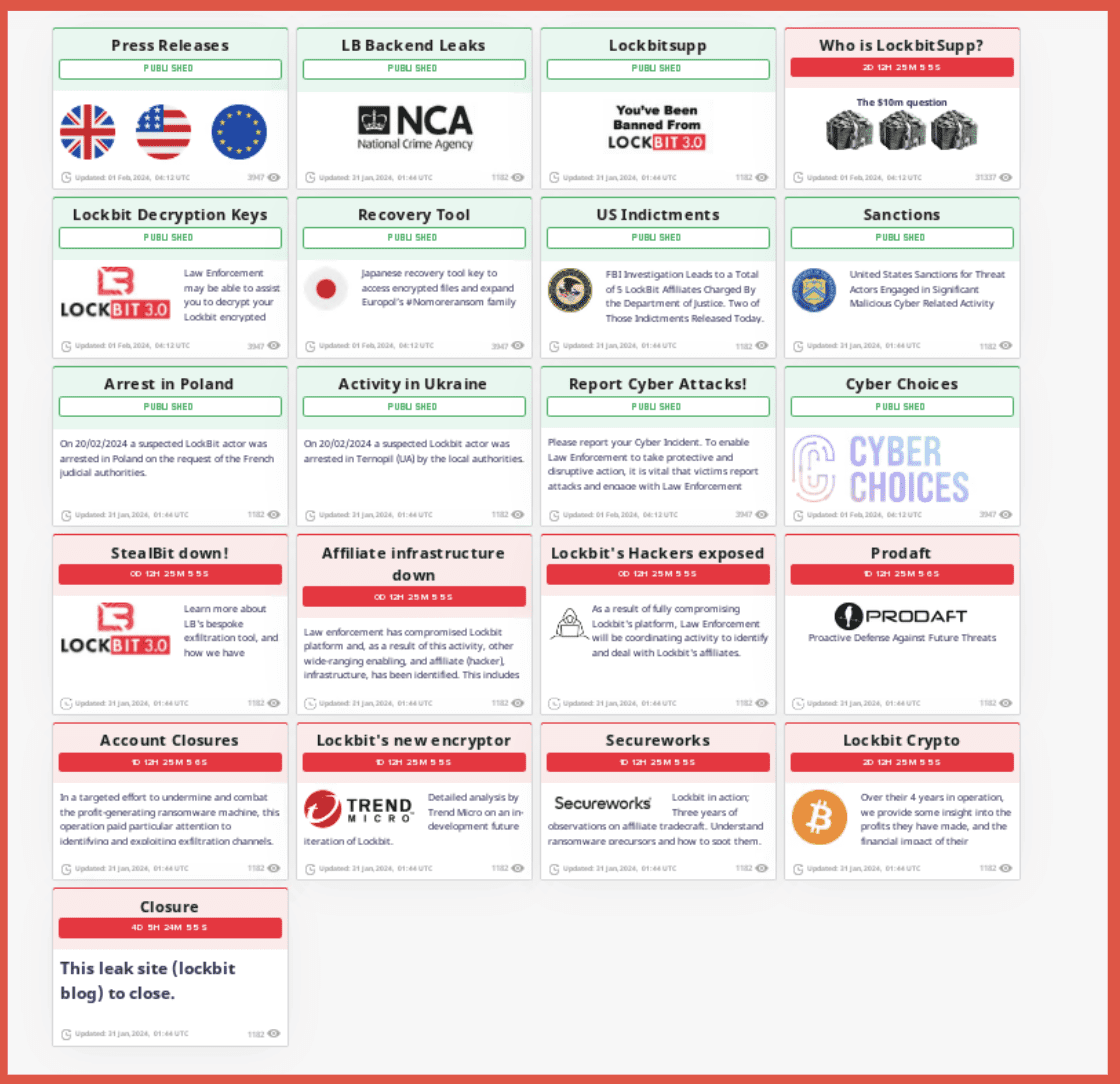
Let’s dive in a little bit more into what data we actually see and kind of try to look at it from an OSINT perspective where possible. Ransomware I have already mentioned. This is two examples of ransomware leak sites, one is LockBit, the other one, I actually don’t remember which ransomware site it is, but you can see like they will share the information about the company that has been victim of a ransomware attack.

But you can see they’re also operating the yellow image. You see that they have a Telegram channel. They are on Twitter and they are on Facebook. So they have a dark website where they share this information, but they’re also operating on kind of more of the mainstream areas. And that can be really useful for you as part of an OSINT investigation. If you’re trying to identify more information about these, you’re building that kind of what we call darknet footprint and digital footprint for these groups and how they’re operating. So, you know, their sites can give you information about them that can help with understanding how they operate. But also, you know, the information that they share while stolen and really should not be shared can be used as part of investigations as well. Especially if you’re concerned about supply chain or third party risk, understanding what data has been released about an organization can help you protect your organization if, you if one of your supply chain vendors is in there, or if you are the person that has been leaked, sorry, had been ransomed, knowing what of your data has been released and is out there for other criminals to kind of delve into, is an important thing to know. And I think some people get concerned about this data and it’s stolen data, but the thing I think people need to understand is criminals have access to this data, threat actors have access to this data and they will use it to conduct more criminal attacks, so it’s important to know what is out there from a risk perspective so you can better protect yourself.
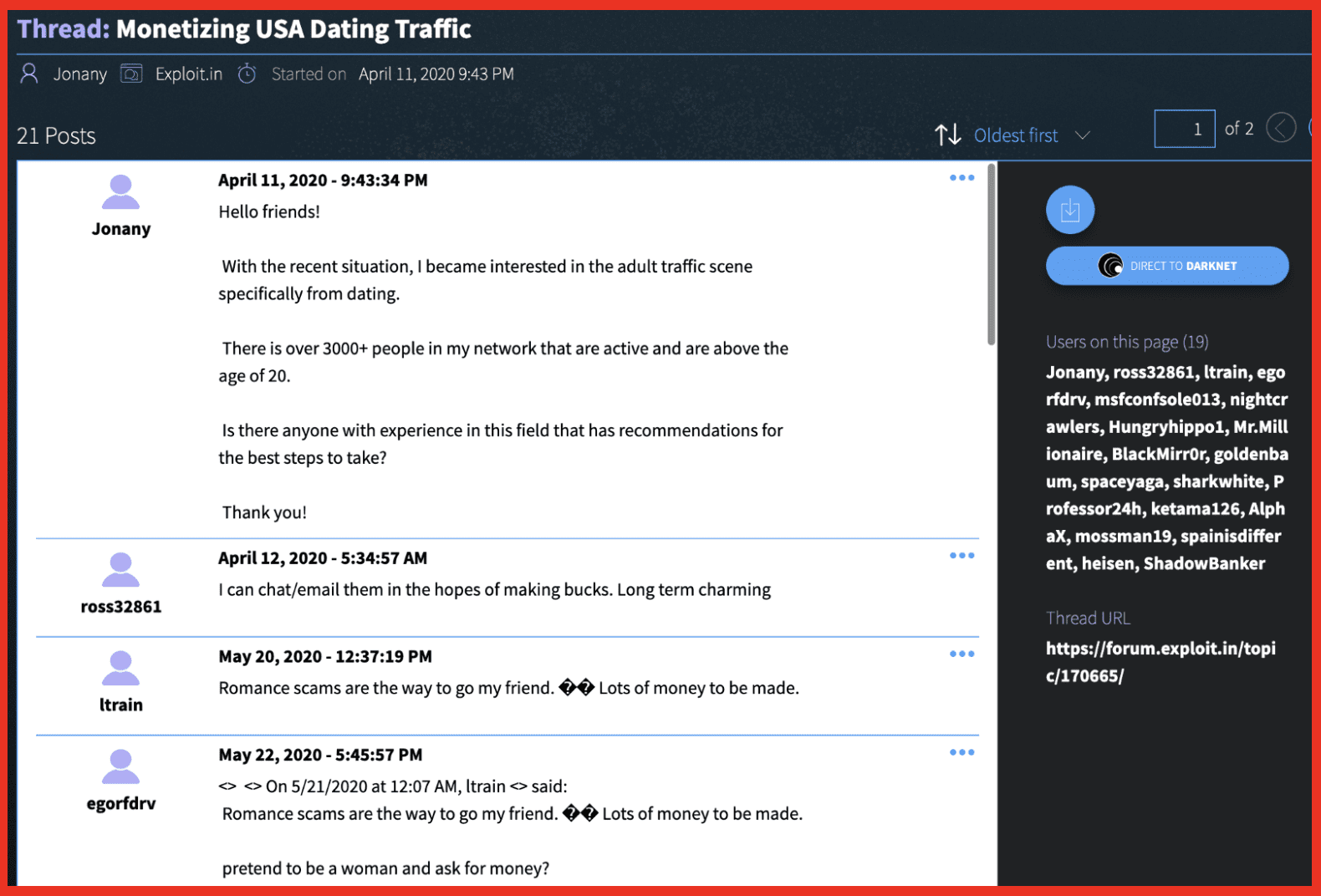
Financial crime I’ve mentioned, we see a lot of marketplaces but also places like Telegram being used as a market for people to sell financial information. So, you can see here there’s stimulus checks being sold, there’s people selling plain credit cards, there’s other things that they’re making available on here, cash apps, etc. So there is a huge ecosystem of this financial crime.
And in the theme of markets, we also see people selling drugs and weapons on the dark web as well.

You’ll see that a lot of these markets look similar to what you would expect to see from, you know, a commerce website on the surface web as well. They provide pricing, they provide images, they also provide reviews. And that can be really useful for us from an OSINT perspective. So, you know, things that you might want to look into on these markets that can give you some clues that you can go and look through in more traditional sources. So, you know, you’ve got OSINT, sorry, you’ve got reviews, as I just mentioned. So, these are some examples of reviews. I don’t know that they are legitimate to be honest, but you’ve got the username, you’ve got the date that they purchase, And sometimes they give some information in there, like, you know, it arrived really promptly that could give you ideas about, you know, where are they based? Where are they purchasing from? And, you know, how it operates. We’ve also got here, like, more descriptions about the drugs that they’re selling. So, they’re telling you the type of drug. It’s a pressed pill. They’re made in-house. So that’s something that they’re, you know, Again, you can never really trust a threat actor, but they might be operating this themselves. That’s something to go on. And they’re also saying that we ship worldwide.
We’ve got other examples where they tell you where they’re shipping from. So, this is actually counterfeit money that they’re shipping. And they’re telling you kind of how they operate it, what techniques they have in terms of producing this counterfeit money, but also they say they’re shipping from Romania. It’s a pretty good starting point that they could be operating in Romania and that they’rei ndividuals based in that country. Again, with OSINT, you also always have to verify everything. You can’t take anything at face value, but these are data points that I think it’s important that you pull out.
And this one is a little bit maybe harder to read, but I thought it was important because they’re giving them details and almost like TTPs of how they’re operating. So they’re telling you they ship it in an envelope that it uses anti-extra bags and if it’s inspected, it will get through it. And they’re actually saying that the National Post Service is the safest way to order it and that they also use express shipping. So, if you’re doing an investigation into kind of the methodology of someone selling these drugs or counterfeit goods, I think I believe this one was still a counterfeit money. You can get from these marketplaces and from these sites information about how they are actually operating, which can really help you in your investigation and maybe where you wanna focus to identify things from other sources that are out there.
Stolen data is also a big one. I’m not really going to show real examples here because I don’t want to expose people’s PII, there’s some of that. But these are, this is Breach Forums and I believe LeapBase. These are sites that appear on the dark web where people are sharing data. And again, we get a lot of questions about is this open? I would say predominantly on these sites; the data is shared freely. Sometimes you need credits, so you need to have a reputation on the sites and that have built kind of some of that persona. But by and large, this is freely available data that again, criminals are going to have access to and it’s something to be aware of.
This gives you an idea. This is a breakdown from data that’s in our platform and Vision.

I looked at the last 90 days and it gives you a breakdown of some of the PII that is available in these leaks. So, you know, names and email addresses you’d expect, but you’re also seeing identification numbers, information about people’s genders, information about companies, phone numbers, dates of birth. You know, there’s kind of two use cases for this kind of data, I think, in the OSINT realm. One is, you know, attribution of looking at threat actors. There’s so much leaked data out there now, but threat actor information is going to appear in there as well as, you know, legitimate people’s data. So, it can really help you with that kind of attribution use case but also from a risk analysis perspective understanding what information is out there about yourself or your employees or you know individuals that you might seek to protect. This lets you know kind of what level of risk they have, what level of exposure they have and how criminals might be able to target them.
Stealer Logs is something that we’ve seen a huge rise in. They’re not new, but they just seem to be a lot more prevalent in the last year or two than they were previously. This is an example. ALIEN TXTBASE is a group that have been sharing not full stealer logs, actually, but what we would call combo stealer logs, where it has the URL, the password, and the username of an individual. And they’re making that available on Telegram. So, you know, this is great for criminals in terms of they are able to log into accounts, do account takeover attacks, depending on what URLs appear here, it could be access into someone’s network. But CELA logs are basically malware that exists on your computer or a victim’s computer and steal things like cookies like your auto fills on your browser, your passwords, and your usernames. It can also steal things like cryptocurrency wallet addresses, basically anything you’re doing on the internet, it can hoover up and we have some good blogs that I would recommend about stealer logs and how they work and how they operate and the different types of them. But they have a huge wealth of data in them.
And again, threat actors have been victims of these as well as legitimate citizens. And we’ve seen a lot of research where you are able to search for places like XXS or exploit, you know, dark web forums and see people’s user information and that can really help with attribution, but also knowing that risk of your password and your username is out there and that can be used for a variety of different attacks is really important and also because the cookies are in there it can help threat actors get past two-factor authentication and OTP codes as well, so that’s something to bear in mind. Again, I said I wasn’t going to share actual data, so I wanted to give a really basic description of how some of this data can be useful. But if you have an email address for a threat actor or someone you’re interested in understanding more about, you can search for that in leak data, and it might appear and show that it’s linked to a password. Depending on how unique that password is, you might be able to identify other accounts that they’re using because we all reuse passwords. We shouldn’t and we get told not to all the time, but most people do. So, you might be able to identify other email addresses and then you can use other OSINT techniques to find more information linked to that. There are tools out there that will allow you to search for an email address and using open-source techniques can find things like telephone numbers that link to social media accounts, that link to things like Cash App and Venmo that can give you access to the real identity of an individual. So, this is a very basic, simplistic way of talking about the workflow, but you can definitely use information and data leaks to be able to investigate individuals. I see it as another tool in the toolkit of data that’s open that you can use as part of your investigation.
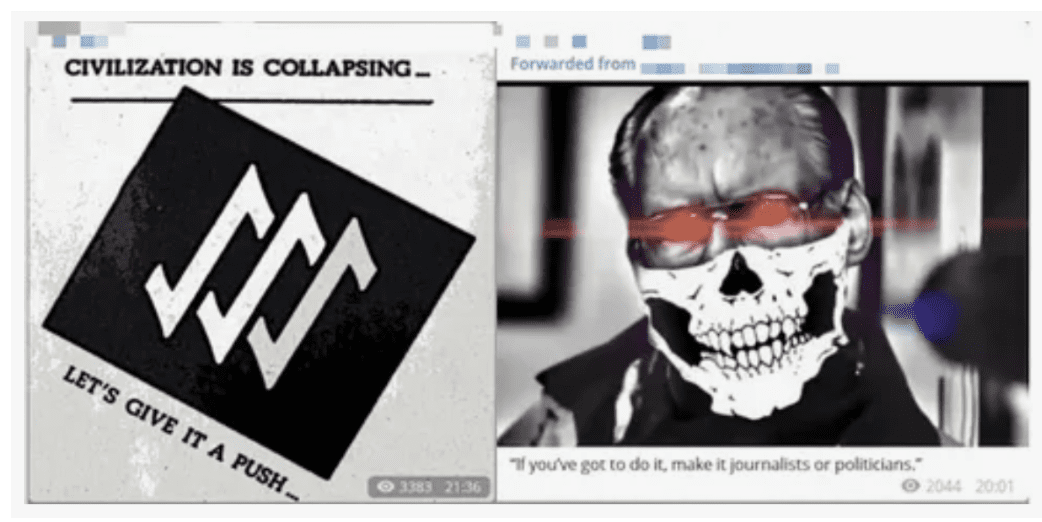
We also see a lot of extremist activity on the dark web and on particularly Telegram. So, these are some images that we identified related to ISIS but we also have things on there that are you know right-wing, extremist, racist information that’s being shared and it’s important to monitor these because they can lead to real world threats and so we need to identify what is being done. You can see with the ISIS threats these were around some sporting events where they were encouraging people to target the sporting events and they were giving specific areas that they should do that and this is something we’ve definitely seen an increase of is using the dark web using things like telegram to incite violence in others and create loan actor attacks. So, it’s definitely something that needs to be monitored.
Executive protection is also a use case that we’re seeing more and more active on the dark web or the data on the dark web helping with that use case I should say. So here I’ve got and I apologize for some of the language in this, but just to highlight, on the left-hand side, we’ve got a post from DoxBin where they’re talking about X FBI agent, whether this information is accurate, I don’t know, but you can see they’re providing things like date of birth, address,] telephone number, his wife’s information, what their role was. He’s also got their daughter’s information. So, huge amounts of data are being shared about individuals on Doxbin. If you’re not monitoring that, then that’s going to be an issue because, you know, a lot of when people’s information is shared here, it can lead to real -world attacks, like things like swatting attacks. A lot of that information would come from Doxbin. You can also see we’ve got a data leak here that specifically mentioned CrowdStrike employees. Again, I haven’t provided any of the actual data, but you’ve got first name, last name, email, where they’re located, their phone number, their job title. So, this is information that’s being released about employees. And again, why you need to kind of be monitoring data leaks for your employee’s information being shared. And I think it’s really important as well that you do that from a corporate perspective of looking at corporate email addresses, but to do this completely you also need to have access to personal information too. And then the the one with the not great language so apologies again for that is it’s from 4Chan and it is an example of a particular individual that I have blanked out being threatened and being said he will be shot, shot like the healthcare CEO and it’s a long time coming. So, we can see kind of chatter and rhetoric of people making threats against individual on dark websites as well. And it’s really important to analyze those and make a judgment about, you know, the risk that these individuals pose and then using OSINT techniques to see if you can identify who these individuals are so you can have a bigger picture. 4chan unfortunately, is a difficult one to do that with because it’s anonymous, but it’s so important to know what people are discussing.
And then you can also do threat actor investigations and attribution. So, this is a bit of a historic one, but Pompompouren was the admin of Breach Forums previously. He was also on raid forums, and you know, from analyzing the data, we were able to look at the username and see that he was active on all of these different dark web forums. We were really able to build that footprint of how he’s operating, but you’ll see he was also, on Discord. And so, it really allows you to kind of understand how this person’s operating, and obviously you can analyze their language and what they’re talking about. And if there’s any clues within those forums to location and information. But I highlighted the DoxBin for executives through Actors Get Docks all the time as well. So, this is an example of information relating to him that was shared online. Several people doxed this individual. So, it’s clear now that Pompompouren was Conor Bryant Fitzpatrick. He was subsequently arrested. So, using the data, and again, this is a very simplified version, but you’re able to identify a real person based on a username and kind of how people are interacting in the community. And from that, we were able to identify telephone numbers that they use that you can do further research on IP addresses that we use. And I believe one of the IP addresses that was associated with of Fitzpatrick was actually where he was hosting breach forums, and the FBI were able to use that. He is now or he was incarcerated, he was charged. So using the data and the information online can really help you doing investigations into threat actors as well.
Okay, and we have a third question. So what use cases are most important to you? I think it’s important to understand what use cases people are working on so we can best identify kind of the data that’s going to support that from the dark web.
But with that said, I’m going to move on to a couple of quick demos to show you real world examples of how we can find data using the Vision platform (see recording for demo portion).