[Webinar Transcription] Illuminating the Darknet for Government Agencies and Law Enforcement
February 09, 2024
Or, watch on YouTube
Due to the layer of anonymity the darknet provides, it is often a hub for illegal activity. The technology DarkOwl leverages to collect and index, 24/7/365 in near real time, hidden digital undergrounds is key in obtaining crucial data and situational awareness for intelligence and government agencies, and law enforcement.
DarkOwl, the leading provider of darknet data, reviews how darknet can be used to:
- Track illicit sales of drugs, human trafficking, and cyber weapons
- Detect potential threats and monitor persons of interest
- Stay one step ahead of foreign Nation-State adversarial activity and attacks
- Learn the latest tactics, techniques, and procedures of threat actors to better prevent future cyberattacks on critical infrastructure
For those that would rather read the presentation, we have transcribed it below.
NOTE: Some content has been edited for length and clarity.
Alison: Thank you Carahsoft for putting this together. Thank you all for logging on. I’m going to jump right in. I have a lot of content to cover. And as Erin mentioned, we will field some questions at the end.
So I’m going to go over a little DarkOwl history, specifically dig into why this data set is so crucial for so many areas of the US government and other government partners. We’re going to look at some data examples off of the darknet. It’s always fun to do. So I’m then going to end with the current events that have recently elevated the darknet data set just in a more global way. And then if there’s time, we’ll walk through an interesting data leak that we uncovered. Before I launch in, I did want to mention that DarkOwl will be at the AFCEA West conference, which is in San Diego next week. I would love meet anyone going there.
So history on DarkOWl. We’re based out here in Denver, Colorado. We have been doing darknet collection for over ten years. Essentially we 24 – 7 coverage of collecting data, pulling it off the darknet, parking it in our database, and then we give our clients access to that. Obviously, there’s a bunch of different formats that that can take. We have a user interface, there’s a bunch of different API endpoints. And like everything, the devil’s in the details. And I think the one thing I want all of you to walk away with today is, when we think about darknet collection, by definition, if you were to go out and take a look at, you know, a handful of Tor pages a couple times a month and store those in a database, you are, in fact, a darknet collector. That said, I would argue that DarkOwl’s strength is in how we define the darknet and what our collection efforts are focused on. And I think we do a really good job of walking the line of both automation. You can’t get the scale of data that’s going to be valuable if you’re trying to do this entirely manually. That said, if you’re doing it entirely automated, you’re not going to get into the hard to find sites or be able to maintain personas and get into forums and marketplaces. So we use both those techniques. If you’re looking at this slide here, I know this is a little noisy.

Everything in red is our data sources that we collect from. DarkOwl obviously we’ve been collecting from Tor forever, that’s been our bread and butter. We have really focused in the last year or so on a lot of the peer to peer networks. I’m getting so many questions from law enforcement, government, commercial on telegram collections. So we’re going to go into that a little bit further on. But you can see here telegram, discord, I2P, ZeroNet. Our collection team is always trying to figure out what the next platform is – where can we start to collect? And all these take different efforts from a collection standpoint. A lot of skill behind the behind the scenes here in navigating all of these, regardless of where we get it, it’s all parked in our database. And then you’re able to access it as a DarkOwl client.
So this slides this is just kind of a visualization of how the data flows through.

So as I mentioned, we’re doing all the collection. We park it in our database. And then as we bring that data in, we’re trying to tokenize and add as much structure and value as we can to make the searching and finding from all of your end a more streamlined process. We we will tokenize information such as email addresses, IPS, crypto wallets, credit cards, usernames. And then depending on what that tokenization looks like, the bottom line here is the product set that we, DarkOwl, spit out of that data. So on the far left hand side is our user interface. So that’s going to be an analyst dashboard. And then we have a lot of different API endpoints ranging from you know Scores which we call DarkSonar, which is a relative risk measurement of an organization or an agency or a government group’s presence on the dark web just numerically represented all the way down to DataFeeds, where we are just pushing data every couple of minutes to clients. So it runs the gamut. But the important takeaway here is that the collections is done by us. We do the tokenization, and then we let you search and filter that depending on what information you’re specifically looking for.

On the left hand side – these are our these are our sources. And as you can see by the numbers, we’re really trying to scale at all times. These numbers were just updated – 28 million records from telegram channels. All of these documents are coming in, being tokenized, and then and then accessible. And, you know, at the end of the day, I feel like we’re solving two problems. Number one, there is no reason any of you can’t go out and do this on your own. You can download Tor, you can have a burner device. It’s just extremely inefficient. Right? It’s going to take time for you to do that. Collection sites go up and down. So it’s an efficiency play. And then number two, especially in looking at the attendee list here, I know most of you are US government. There’s a real safety feature here in that DarkOwl has done the collection. You are only playing in the DarkOwl data set so you don’t run the risk of exposing your own organization or burning a persona. We’re doing all of that in the backend, so it’s efficiency and safety at the end of the day.
So thinking about the the darknet in regards to US government use cases.

And I kind of boiled it down to three here. I’m sure all of you can can come up with more, but the first one I think of is just the force protection side – looking out for our own exposure, monitoring for email exposure, looking for PII of prominent folks and alerting them and making sure that we have an understanding as a government of what potential vulnerabilities are out there. And that could run the gamut from exposed PII for someone in a senior position to military part numbers being sold or darknet forums discussing ways to penetrate organizations.
The middle one here – identity management. So I think of that as the investigation side of it – really using the data set to conduct research, to look into identities. How are people talking about this? What can we find? What can we correlate? Who can we associate with this? A lot of red team activities.
And then on the right hand side here, targeting and thinking about what can this data set tell us about nation states and other folks, threat actors, what’s trending, ransomware, there’s so much content out there that is powerful to be in the know on how that’s being talked about and presented.
So without further ado, let’s jump into some data data examples. And again, I highlighted before we do that, why is this data set so challenging to get your hands on. Part of it is just the time and effort that it takes to do this, these sites go up and down all the time, they move locations. Access to these forums and marketplaces – it’s not as simple as just signing in and you can’t scrape page one, scrape page two and park it in a database. You need to be very strategic about how you do that. So these are some of the skills that we possess and have been doing for a long time. CAPTCHAs. And I’m not going to do a live demo today, but I do continue to fail CAPTCHAs on the darknet. They are extremely hard. I’m always laughing at that piece. So we’re doing these collection efforts in the background and basically taking that time suck and that risk off of all of you. Then the evolution of where people are moving to, I mentioned these peer to peer networks. You know, we’ve seen such popularity there, especially with the start of the Russia conflict breaking out in Russia and Ukraine. Following those trends is something that we’re always staying on top of as well.
Alright. Darknet data. What’s out there? Um, I just pulled together some slides of examples that I thought might be compelling for some of you on the phone, and to just give you a sense for what we’re looking for. So, no surprise, a ton of PII, all sorts of banking and transaction data, credit cards for sale, exploit kits, malware. And remember, by definition, the reason to be on the darknet is to remain anonymous. So anyone trying to sell or transact or trade in any illegal goods or services is going to be attracted to that. So there’s forums and marketplaces on how to do these things. It’s a it’s a colorful space.
The next bunch of slides are going to be screenshots from our platform, which we call Vision. And I’ll highlight just some of the findings here.

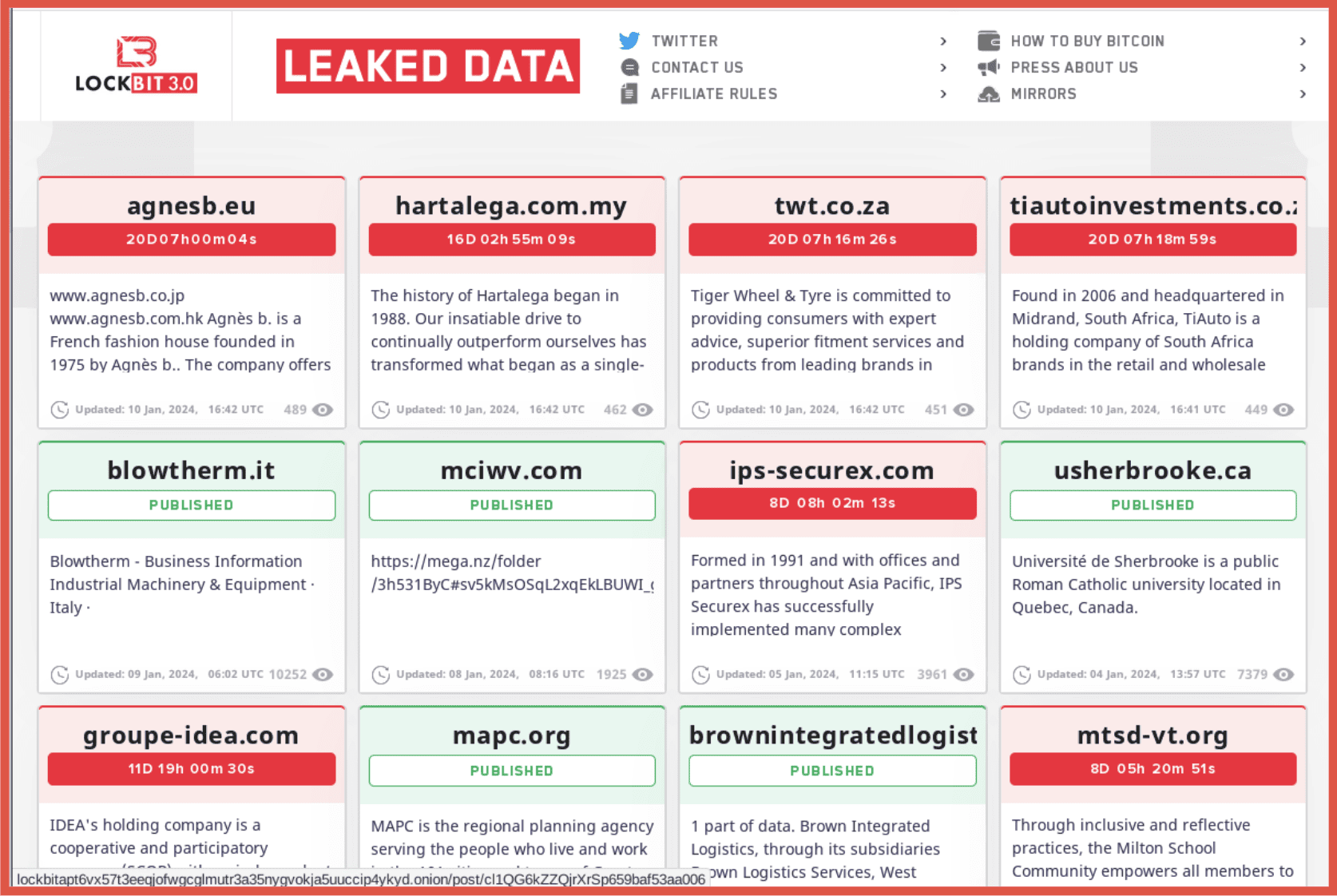
So I know it’s a little small on the background here, but if you look up at the top in caps it says DHS traders home addresses. So this is a hacker that’s uncovered some PII and is posting it out there, maybe in anger, unclear. And they’ve listed everything from title, home address, phone numbers. This is just someone posting this on a Tor page and we were able to capture that. And then this is a result right out of DarkOwl Vision.

Here’s another one. This is someone who is promoting their skills around making custom IDs, utility bills, bank statements and other documents, passports for sale. You can see the price here in in Bitcoin. This is this is very, very common – people trying to gain business and sell IDs and everything you can think of.
So here’s one that, um, I thought would be good for today.

This is a counterfeit item. They’re selling DOD ID cards and editable templates. You can even choose your own name and picture.
Alright, moving along – event and personnel protection. I looked at the registration list and I think some of you are tasked with some of these directives.

These are screenshots here of folks that, this one in the middle is actually a telegram group. You can see there’s 32,893 members in it. It’s entitled the Ultra Patriot Voice. You can see some words down here at the bottom. So these may be channels that would be worth monitoring. We’re collecting from them on an ongoing basis. We’re able to identify what users are are in those telegram channels, what their ID is, what their username is. And then, given some of our other sources, we can oftentimes back that into an actual person.
It wouldn’t be a good darknet presentation without the talk of ransomware. This is such a such a prominent thing for all of us.

Our commercial clients are are always very concerned about this. This is a screenshot of what we would see on the darknet side. So this is not what the victim would see on their own network. It’s important to understand here that the ransomware actors are hosting this content and they call them shame sites. So they’re posting this and saying, hey, and in this case, it was actually a, um, this is actually a grocery chain. And they were saying, you know, here’s the information we have. But why this is so critical is because this is where we can assess and figure out what actual data has been exposed. So monitoring these sites and being able to be there in real time is important.
This is a fun slide.

This was actually an investigation that DarkOwl had done where we identified and tracked a Portuguese speaking threat actor. They were involved in a mobile device malware issue. If you look kind of towards the bottom here, we were able to confirm that the suspect’s activities were in a bunch of these communities and the black part at the bottom here where it says steam, where you can see where it’s grayed out there. That was actually a leaked IP address that we were able to get a potential physical location for this gentleman that was in the Brazil area. I like to highlight this one because I think the first thought a lot of folks have in regards to the darknet is that there’s no geographical location because everyone has obfuscated their identity and their location. That said, there’s enough breadcrumbs in there that you can often back into it. So this was a case where we were able to do so.

Insider threats. So we see a lot of posts in regards to this. This is actually someone who’s looking to recruit insiders. You can see that this site toggles back and forth between English and Russian on the right hand side here towards the bottom – they talk about my team will lock, exfiltrate and pivot with your access keys and with your access, and you’ll keep a percentage of the money for giving access. So they’re recruiting folks to try and get in. This could be government related, commercial related and or both. So insider threat, no surprise there.
Drug and gun sales on the darknet isvery prominent. We see it all the time. There’s marketplaces dedicated to it.

I think there’s some folks on the on the phone from the DEA. Kudos to you guys. It is an uphill battle. And I know you’re fighting this daily. There’s so much and we’ve improved. One of the things we’ve done at DarkOwl very recently, is going into a lot of these forums and marketplaces and really dissecting how the chats are happening. So what I mean by that is looking at timestamps and who’s talking to who and trying to build out these networks so we can try and get to the bottom of some of these. There have been some really great use cases where our clients were able to use this data to solve a case.
One question we get often is what do we do with images, right? There is a lot of content on the darknet that none of us want to have eyes on. And so what we do at DarkOwl is we ingest all of the text into our database.

So on the left hand side here, you see a screenshot from Vision. That’s our platform. And I simply ran a search and said, I think my specific search was “glock”, and then the word “sale”, and I think I put in “Miami” as well, because I was talking to some folks in Florida and this page came up. So you can see we list where it came from, you can see the dot onion and then all of the text here. So if you’re sitting in the DarkOwl platform, you do not need to be concerned about coming across any child exploitation photos or anything in that regard. That said, sometimes the images that are captured can be quite compelling. So we have recently added what we are calling Direct to Darknet. You can see in the middle of the screen, there’s a little light blue bubble there. So if you click that button within the DarkOwl tool, it opens a new window. You’re in a safe, secure sandbox environment. I do it all the time off my DarkOwl laptop. This is not a burner device or anything. And up comes the actual page. And in this case, I’ve taken a screenshot off of the page, and you can see that the bracelet this person’s wearing, to me would help maybe frame the persona of who’s using this. We also have, if you see in the original text, they’ve provided a telegram handle here. So, you know, starting to gather a couple pieces of information that I think could be pretty compelling for an investigation here. So, again, the images won’t be pulled directly into the DarkOwl database intentionally, but you can go back out and capture those if needed.
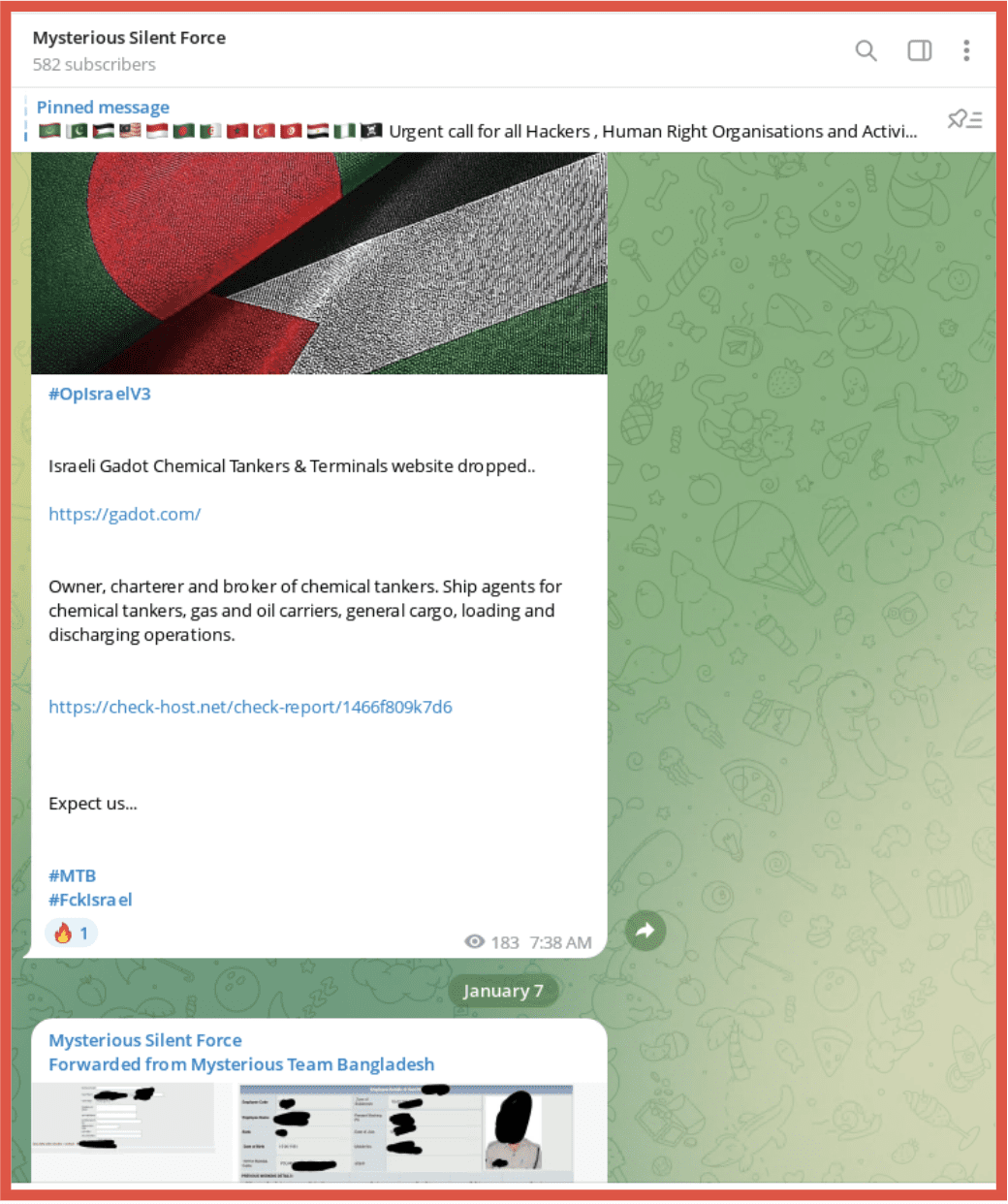
Alright, I’m going to switch gears a little bit. A lot of the examples I’ve provided are ones that folks are pretty aware of – trading, selling, transacting in illegal goods and services is and has been what the darknet has been used for forever. What’s been interesting in the last year or two is really the political climate and how there’s been such an increase in real time chat applications and encrypted communication platforms for people to collaborate both for good and evil. We’ve seen a huge growth in telegram use and therefore the request for telegram data. There’s a lot of these invite only and pay to play architecture that’s been spun up. It’s just such an evolving space. So it’s been really interesting to follow that evolution and start to do some of our collection from these peer to peer networks. So there’s a lot changing. And I would say that one of the catalysts for that was absolutely the Ukraine Russian war. I think our actual data database, so just DarkOwl’s data went up by maybe 10% to 20% just within the first couple months of that. Half a million hacktivists and gray hats were taking on Russia and their allies. We saw just a huge influx of data and communication. It’s been really compelling and interesting to see that evolution in the modern warfare today. In a similar vein, if we think about the Israel-Hamas conflict, very much the same, there’s been a lot of data leaked on both sides.

These images here on the right, the bottom one is, is an attempt to map some of the hacktivist groups that are working together. These top ones are actually images that were shared on a telegram channel. This is this is a whole new way to engage and it’s been just eye opening for us to see the amount of data that’s coming onto the darknet in regards to these conflicts and wars.
Telegram is coming up again and again. There’s so much information being passed through that. We had a concerted effort, right when the conflict broke out, to try and join a lot of these groups, we were able to get 320 of them into our collection efforts that were specific to the conflict. And we actually have a really awesome blog on our website – it’s worth the read.
Russians on the darknet. Interestingly, the second most represented language in our database is Russian. Their ransomware groups are very prominent, very sophisticated. There’s a lot of content that that we have found. I’m actually going to show a couple examples in the next couple slides.

In regards to this was an interesting leak where there was Bushehr nuclear power plant, sometimes referred to as the NPPD leak, came out on a telegram channel. This was a hacktivist group that had come out after the death of that woman and they had posted all of these, download the entire email server and posted a lot of these pictures on a telegram channel. We, DarkOwl, were able to go in and capture some of those. It was posted in a bunch of different parts, but the compelling piece here for you to take away is we were able to go in, we were able to grab these images and, and capture this. And this is the kind of stuff that, given the line of work that you all are in, can be pretty compelling to help with investigations. So these were some internal photos. You can see all of the metadata is captured there as well. Historically this has been a plant that I don’t think folks have had eyes, or at least, you know, we in the US, on the inside.

These were a bunch of passports. So everyone that came in and out of that plant had to submit a passport. All of that was being passed through email communications. And because they had downloaded or had taken down that whole email server, every single itinerary of people that had been in and out of that plant in the last couple of years was captured. So again compelling for anyone that was needing to do research in this area or learn more about what was going on here.

You can see the flag here in the over on the right. This is obviously a Russian aircraft, some equipment, being delivered to this plant. So, again, just compelling information that would not have been able or clearly was not meant to be out into the public had been exposed on this telegram channel, and we were able to capture it and bring it into our data set.
So I’m going to pause there and wanted to take a couple questions.
Knowing that you folks cover Telegram and Discord channels/servers. What are the types of servers and channels that you usually collect from? E.g., are they solely reach groups, criminal groups, or a mixture?
Alison: Great question. So DarkOwl serves both a commercial client base and a government client base. So right now, our telegram and discord collection is focused on what our specific client use cases are. For instance, we had a client join a couple months ago that was concerned about some financial fraud that they were combating, so we joined a bunch of telegram channels on their behalf. So the short answer is it depends on our client’s use case, but I would say the ones that you referenced are all a part of our collection. We also love to do collection by demand. So what I mean is, as we bring on new clients, we always sit down during that onboarding and say, you know what’s of interest to you? What telegram groups can we join on your behalf? What is your use case? So a lot of that collection is customized to what our clients are looking for.
GEOs from the IP. Are you getting IP registration goes through a service like Maxmind or is it a GPS geo from a device using that IP.
Alison: So if you’re referencing the slide where I was talking about that actual investigation, we pulled the the actual IP address off of a post that we saw and then that we couldn’t we weren’t geo locating that within our tool so that that would have to be done outside of the Vision tool.
If Tor sites are always going up and down, how do you track this and find the news sites/markets?
Alison: I talked about this early in the presentation. It’s a combination of both manual and automated. So if we’re on a Tor site and crawling that and we see that there’s links to other pages, we will immediately spider and go to those pages and start collection there. Sometimes we’ll use one of our analysts to find a forum or marketplace. And oftentimes if those forums or marketplaces go down, they’ll post, hey, we’re moving it to this, or this has been taken down by law enforcement, we’re going to stand it up here. So it’s a combination of both spidering within the pages we collect and following those links, and then also our analysts just knowing the space and navigating to new forums and marketplaces. And the nice thing is, once we’ve captured the information, it’s retained in our data set. So if we were on a marketplace last week and we pulled down all the listings for, Glocks for sale in Miami, and then that site were to go down today, if you went into DarkOwl Vision, it would still be there. So there’s a nice lookback feature here because we don’t age off any data. So that’s, that’s where the capturing and looking back can be helpful.
Our unit’s focus is the commercial exploitation of children in the US, specifically California. How is your coverage of that topic?
Alison: We should talk because we actually have a partnership with a couple nonprofits that are in a similar line of work as you. We’re collecting this information at scale. So I guarantee we are going to have some sites of interest for you. The piece that would be important for you is that direct to darknet piece, where you would probably have to go out and actually capture some images there. I would want you to sit with our product team and walk through what that looks like. But my guess is we do have content that would help you with your work.
If we are looking for a particular chat, such as those including child exploitation, will your company actively search topics or is it only the data that has already been pulled available?
Alison: No, we will actively search sites if for some reason there’s a site that we are not already collecting from, whether that be a telegram group of discord server, a dot onion. We will go out and collect from it, per your request, as long as we’re able to do so.
What data sources are considered dark web?
Alison: It depends on your definition. I feel like everyone’s definition of dark web is a little different. We at DarkOwl consider that to be, Tor, I2P, ZeroNet. And then, as I mentioned, we collect from a lot of these dark web adjacent peer to peer networks. So telegram, discord, and some others. But the short answer is I think the definition of dark web can vary depending on who you ask. Ours is fairly broad, and we try and collect from a lot of adjacent sites as well.
How do you legally collect all this information? Is it Osint?
I’ll answer the first part – legally everything that we collect at DarkOwl is considered Osint, so open source we are able to do so with the right skill set. Any of you could go and find this information. A couple lines we will not cross. We will not purchase data. We won’t go behind firewalls. We follow very strictly the Department of Justice guidelines around data. Everything is done ethically. And again, we’re not purchasing data and or going behind firewalls. So we’re able to collect it because it’s open source information.
Can we search the data you collect by name, date of birth, etc.? Can you show how the application works live?
I can absolutely show how the application works live, not on this webinar because they’re recording it and going to be sending it out. I’d be happy to give you a demo outside of this webinar to answer the first part of your question. You can search for anything in our data set. Think of it as the Google of the darknet. So there’s a big search bar you can type in a term, an email address, a phrase, and hit search. And we’re going to show you all the results that are relevant to that, that have come out of all these varied collection sources. So yes, you can search for a date of birth, you can search for Social Security number, a phrase, whatever you want.
What are upcoming trends security practitioners should be looking out for?
I’m definitely not the best person to answer that question, but I would tell you that our collection team is always trying to stay ahead of what’s coming up next. And a lot of these forums and groups are talking about what the next technique is. I think the best we can do is all come together. Those of us that are on the the right side of the coin here and share what we’re seeing and hope that by sharing those practices and sharing what each of us is coming up against, we can make some headway. But I feel like I’m not the best one at DarkOwl to to field that question.
Do you have a newsletter, an email of examples of cases which were sought and closed and how they were investigated and the outcome?
Absolutely. We have a extremely comprehensive blog that we put out and there are white papers. I will tell you that if this topic is of interest in any capacity, any of the slides I showed, whether it’s in regards to some of the recent conflicts or very specific drug sales. Our blog is incredible. There’s so much information in there. All of those pieces were months and months of research.
Would you be able to say if any departments in new Jersey are currently using Dark Owl? I just want to see if this is something that would be beneficial to our detectives.
Off the top of my head, I don’t I don’t think we have any New Jersey specific clients, but I will tell you that we absolutely have state agencies and state departments that are using this. We have both federal clients and a lot of SLEDs. So I’m happy to make a referral to another state that is using it and see if that would be helpful to talk to them and learn more about their use case.