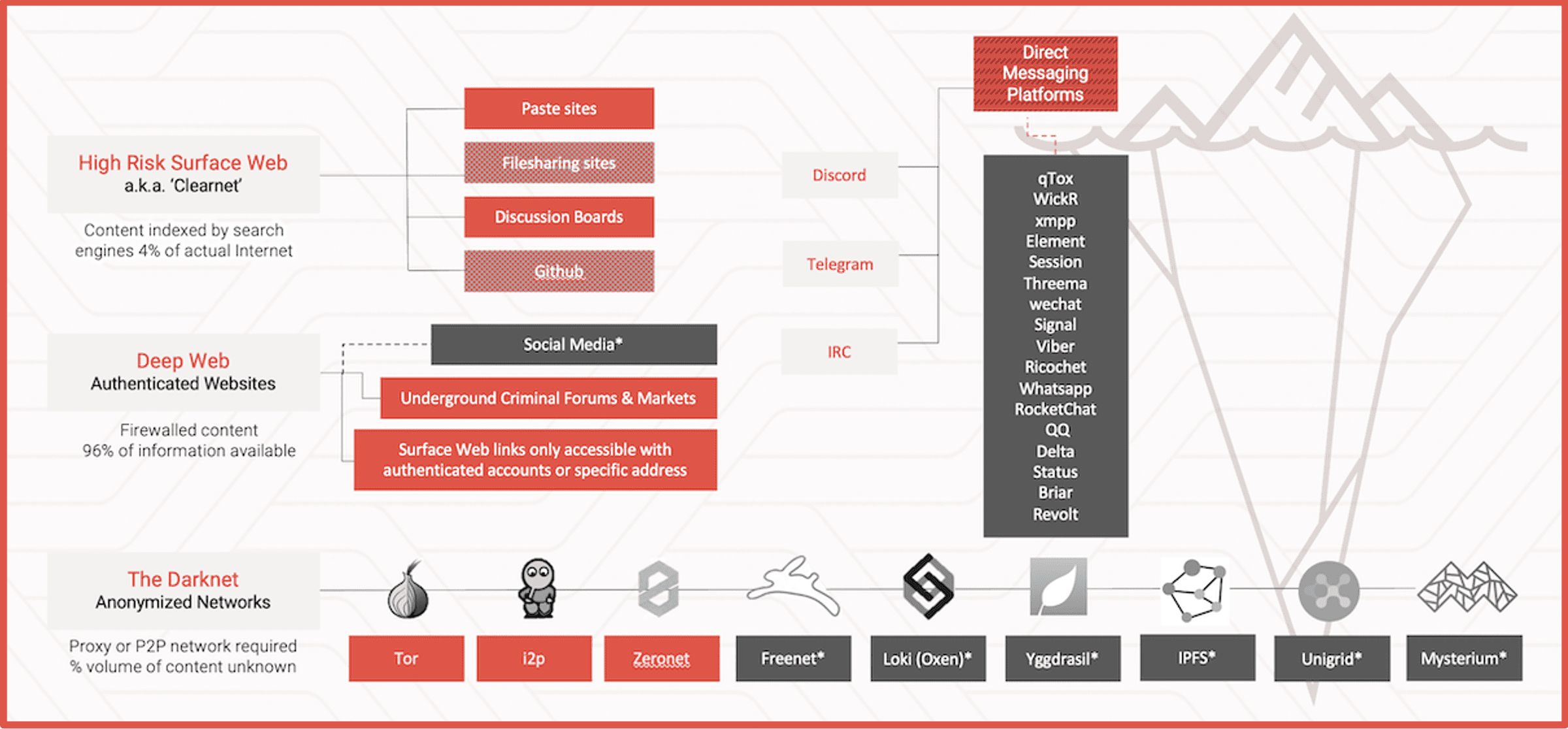
January 25, 2023
The simplest way to describe retail fraud is theft from a commercial retail establishment resulting in financial loss and harm to the retailer. Retail fraud is a criminal offense and there is a myriad of ways retail fraud can occur, both physically in a store and virtually online. With a shift towards more e-commerce-centric shopping environments, virtual retail fraud at scale has surged and darknet cyber criminals are at the crux of this fraud economy. In this blog, DarkOwl analysts review some of the most popular methods in use by cyber criminals and retail fraud related discussions observed in underground criminal networks.
Purchasing and/or Reselling Goods for Less than Market Value
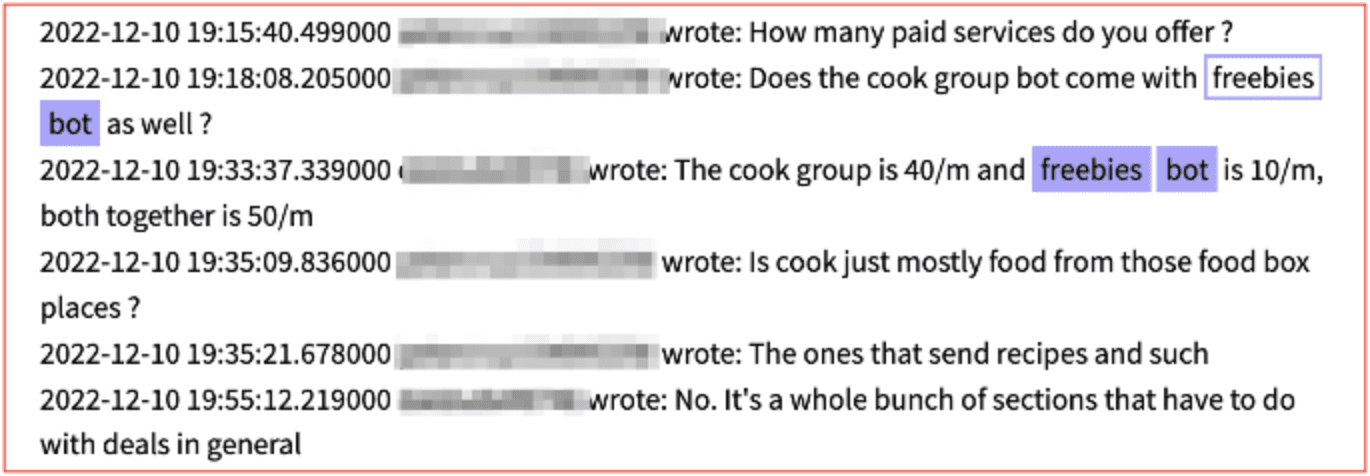
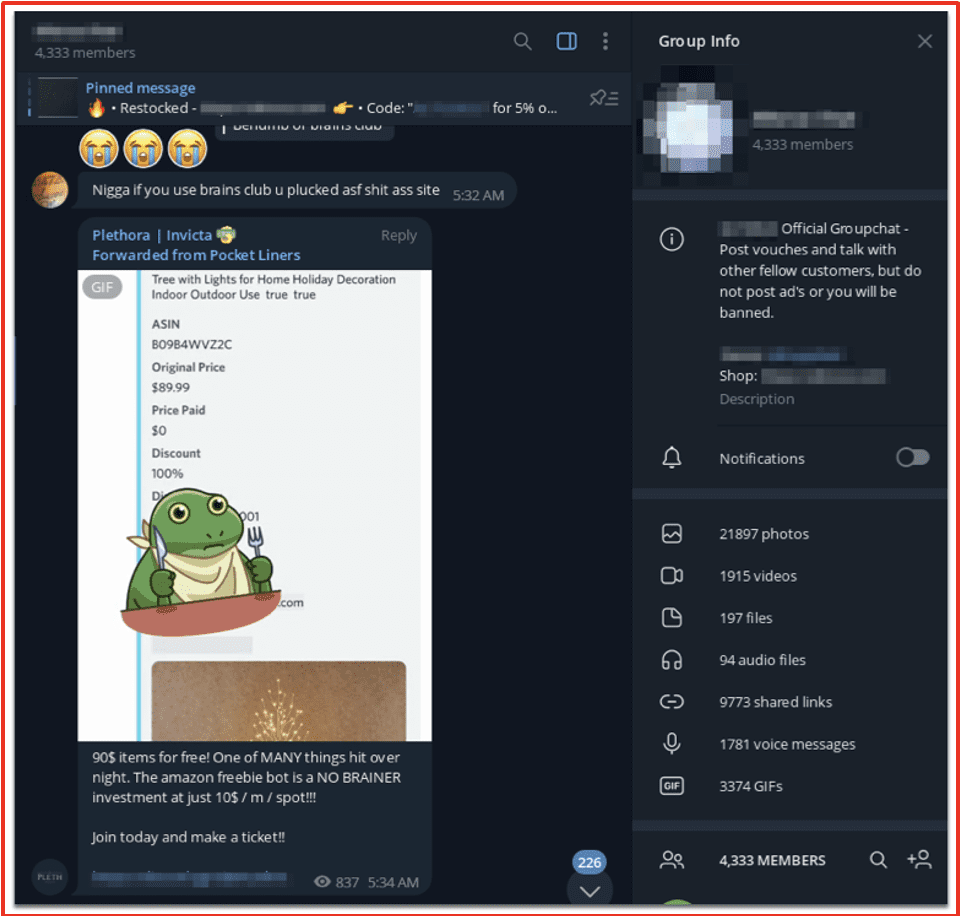
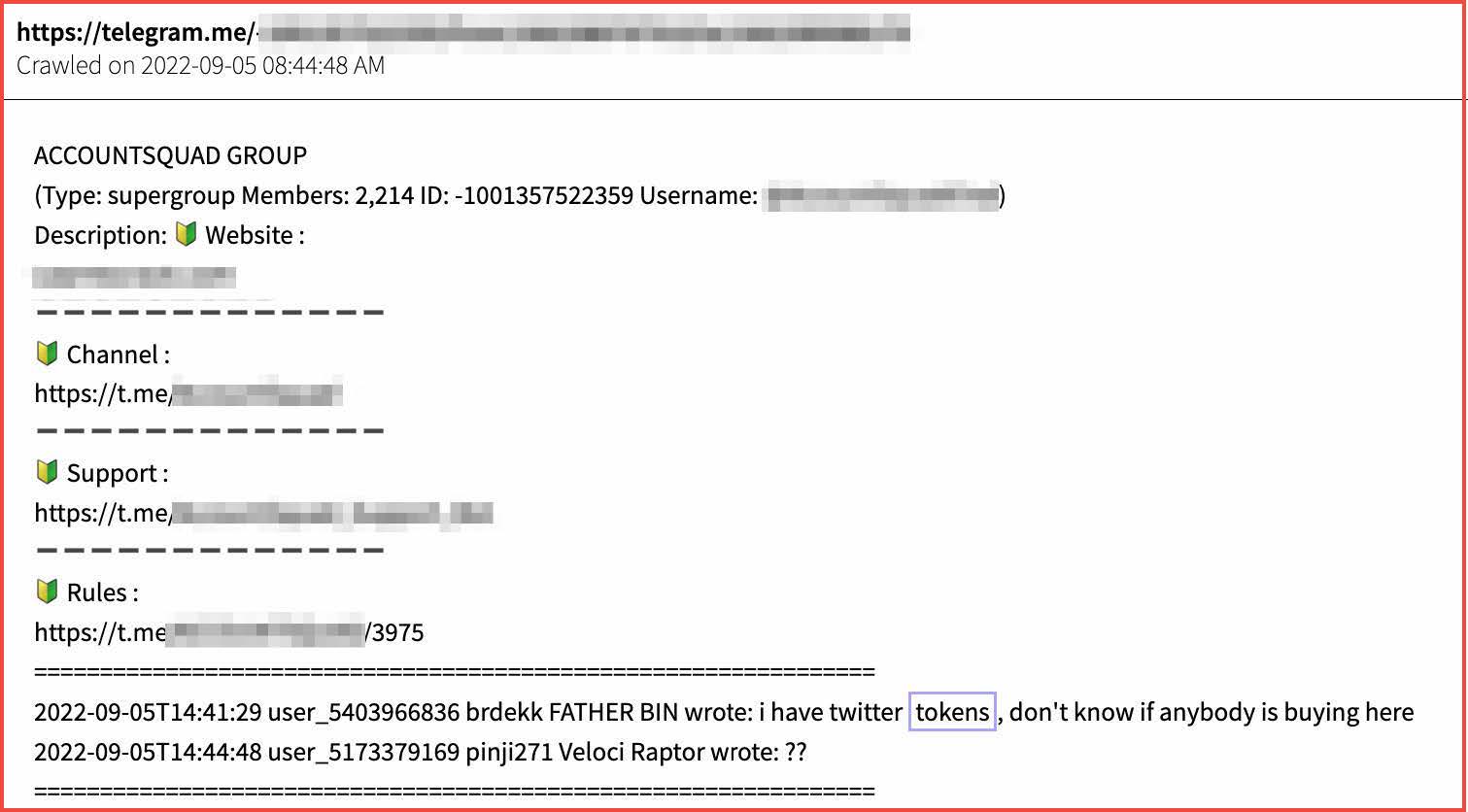
Freebie Bots
Since most retailers have inventory available for purchase online, there is a growing network of opportunistic software developers deploying “bots” designed to capitalize on human errors and mispriced product SKUs (stock-keeping unit). Freebie bots scour the Internet, scraping e-commerce websites to discover items that have been accidentally mispriced and then purchase those products in bulk for resale. The developer or administrator of the bot will resell those items on other sites such as eBay, alibaba, and others, gaining significant profit. Since the retailer is beholden to transact at the erroneous price, the retailer is negatively impacted financially because they end up filling a high volume of mispriced orders.
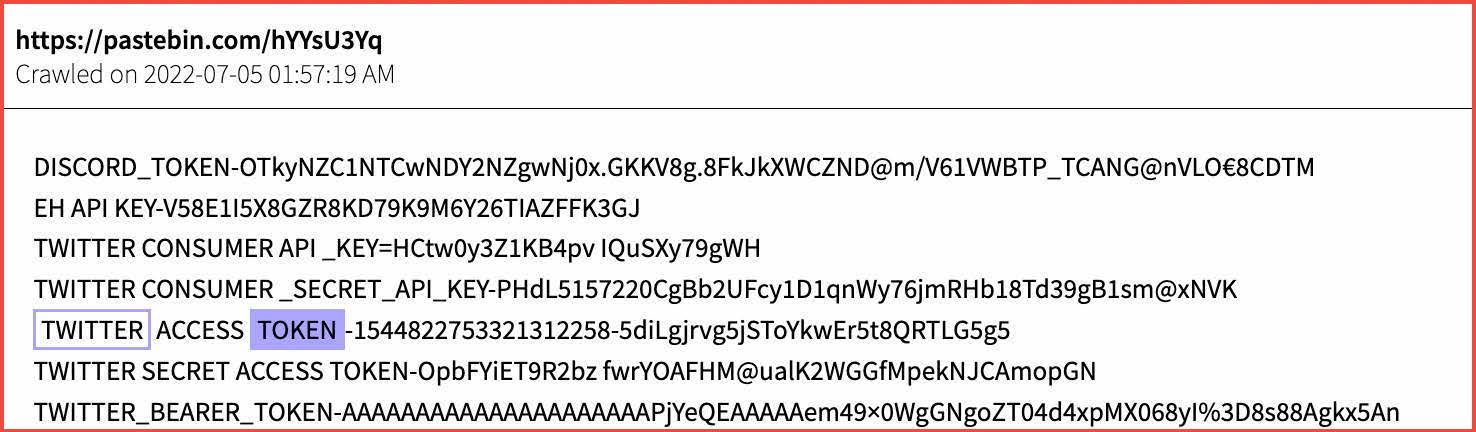
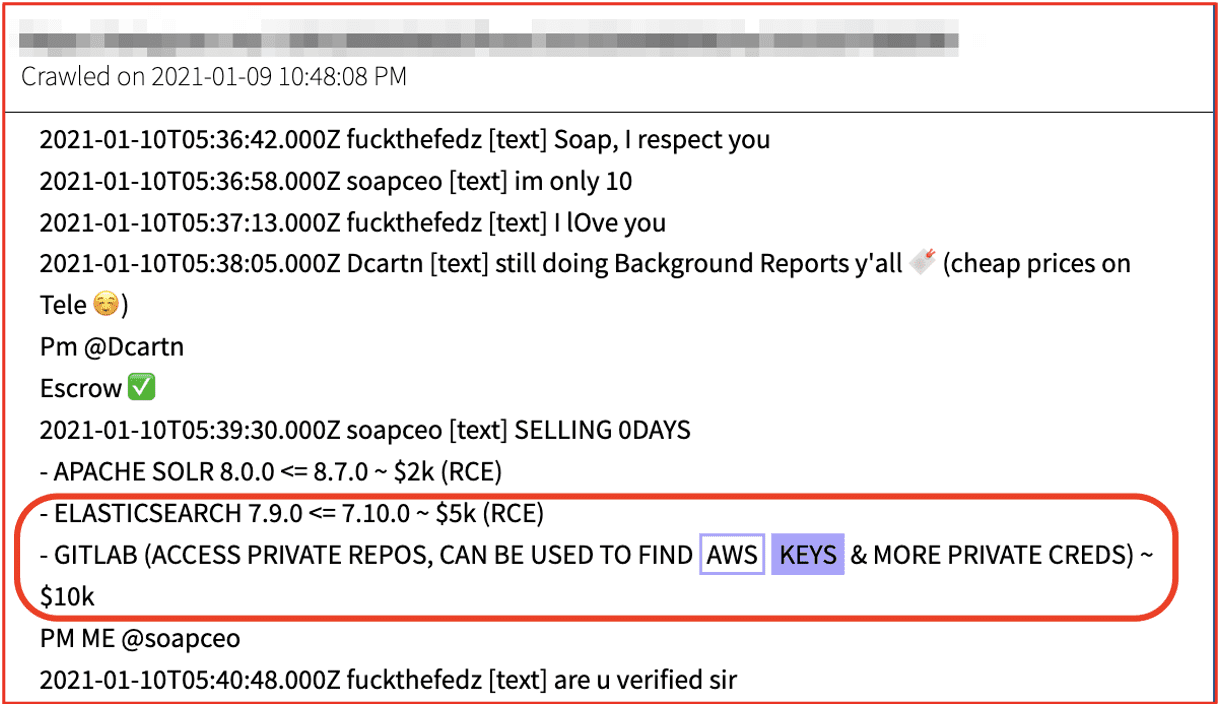
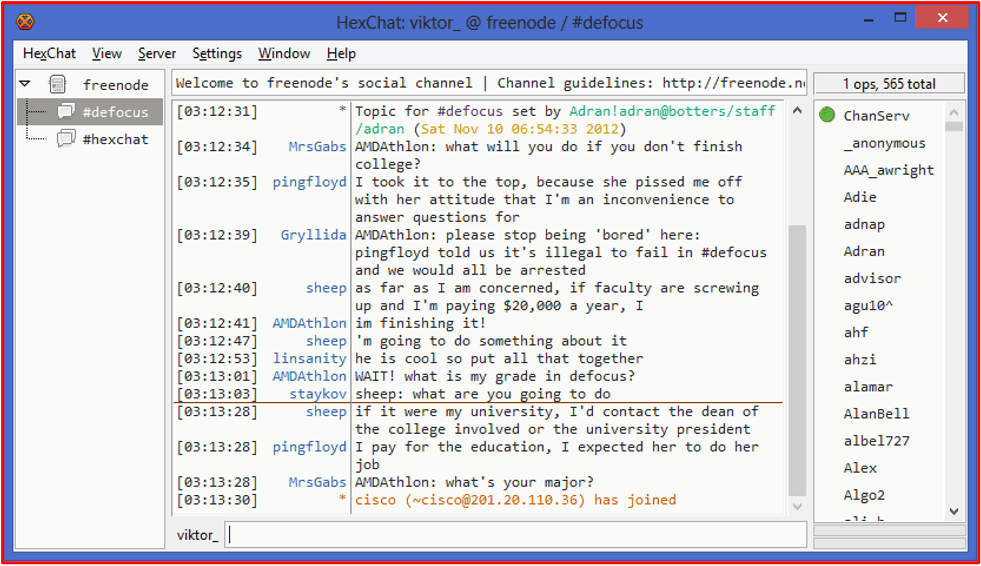
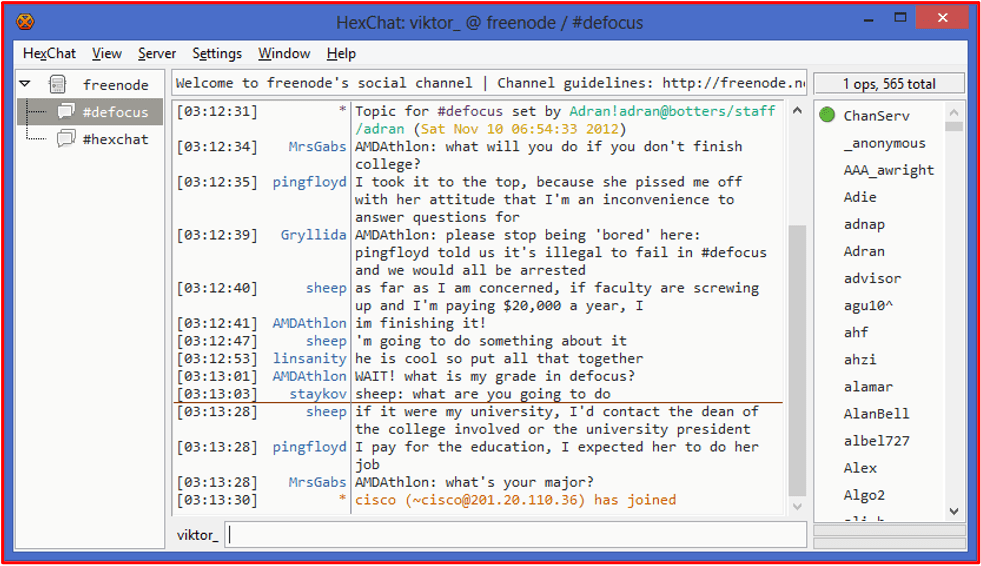
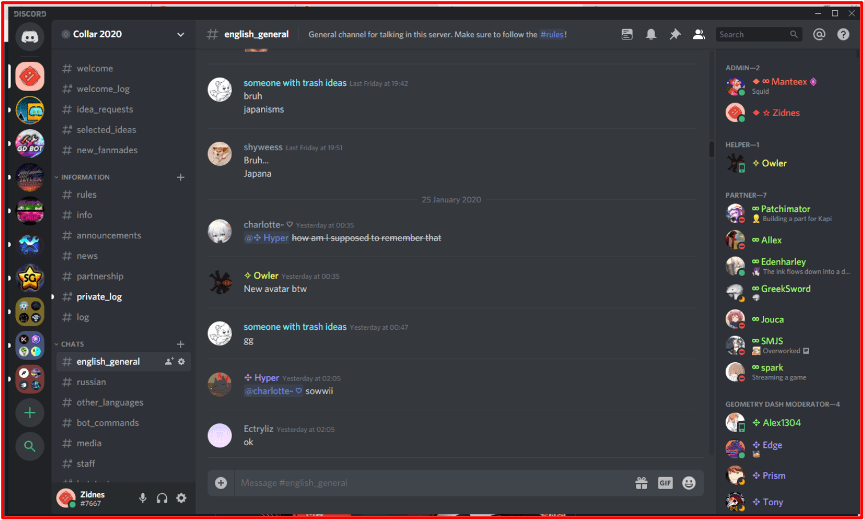
Such bots are regularly discussed and traded on popular darknet adjacent chat platforms like Discord. In the figure below, threat actors discuss the “cook group bot” where deals from online food services are scraped and available for exploitation.
Figure 1: Source DarkOwl Vision
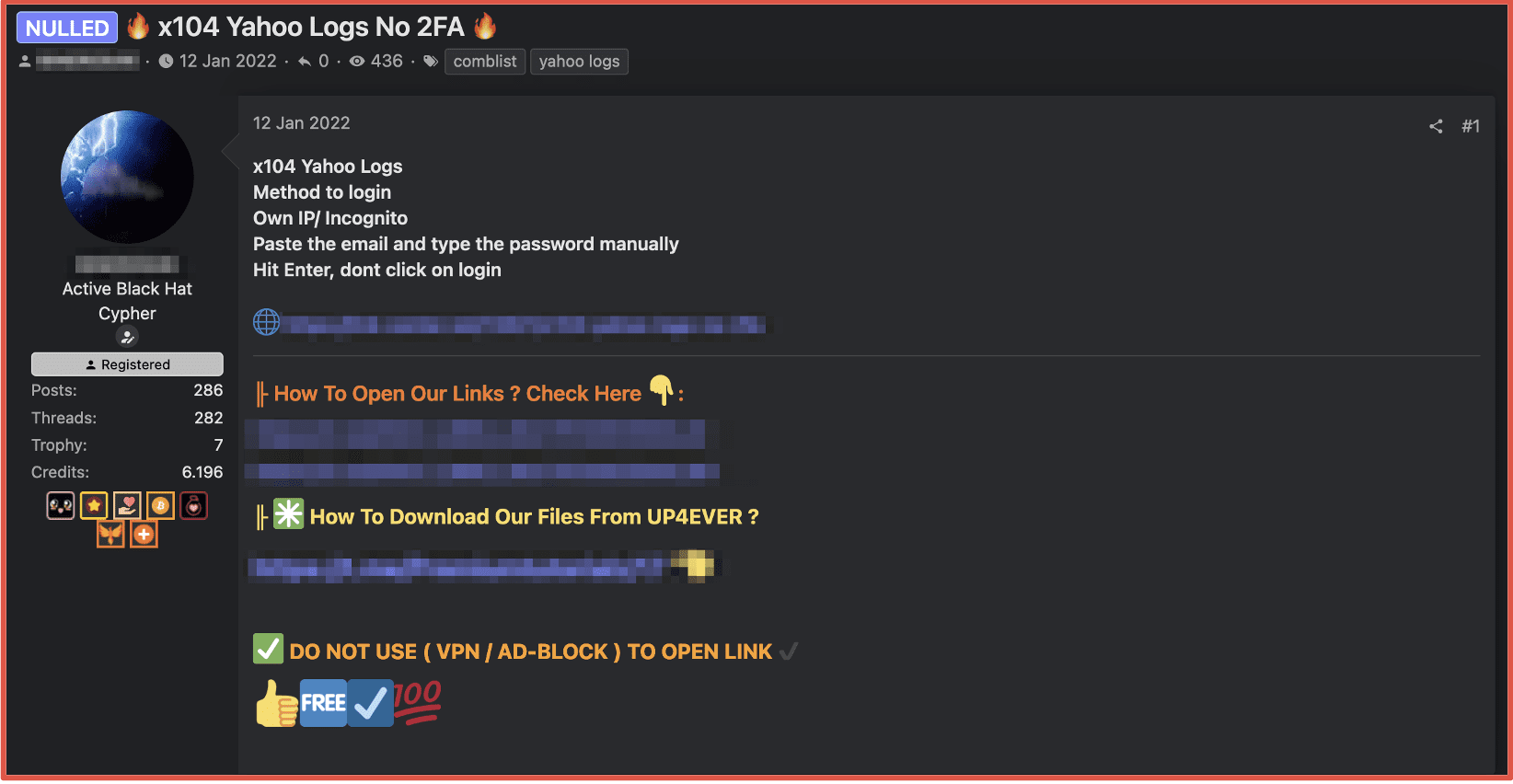
Figure 2: Freebie bot advertisement Source: Telegram, Channel Redacted
Counterfeits
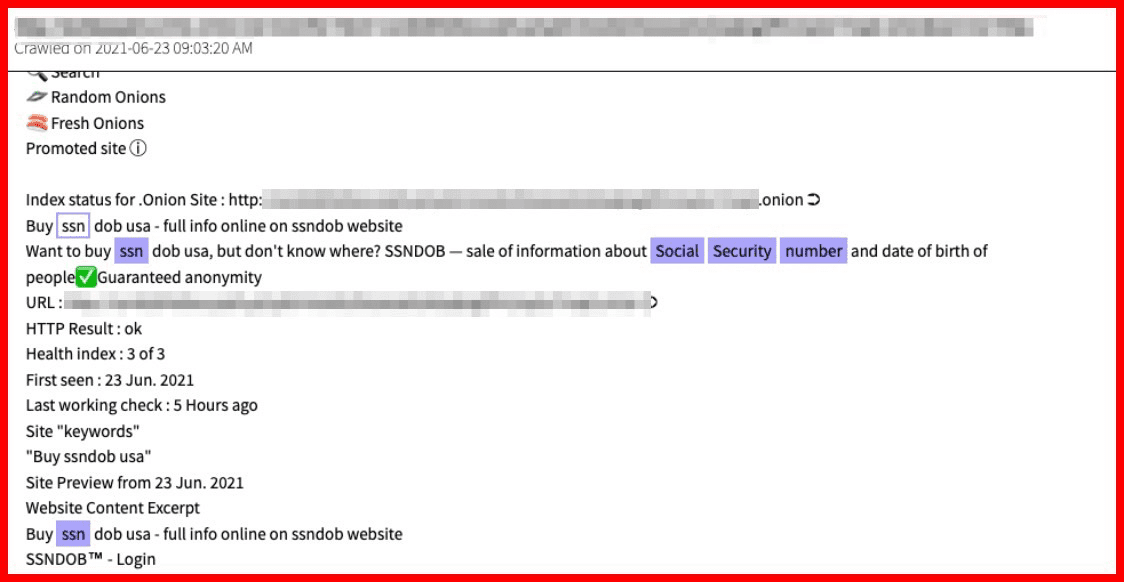
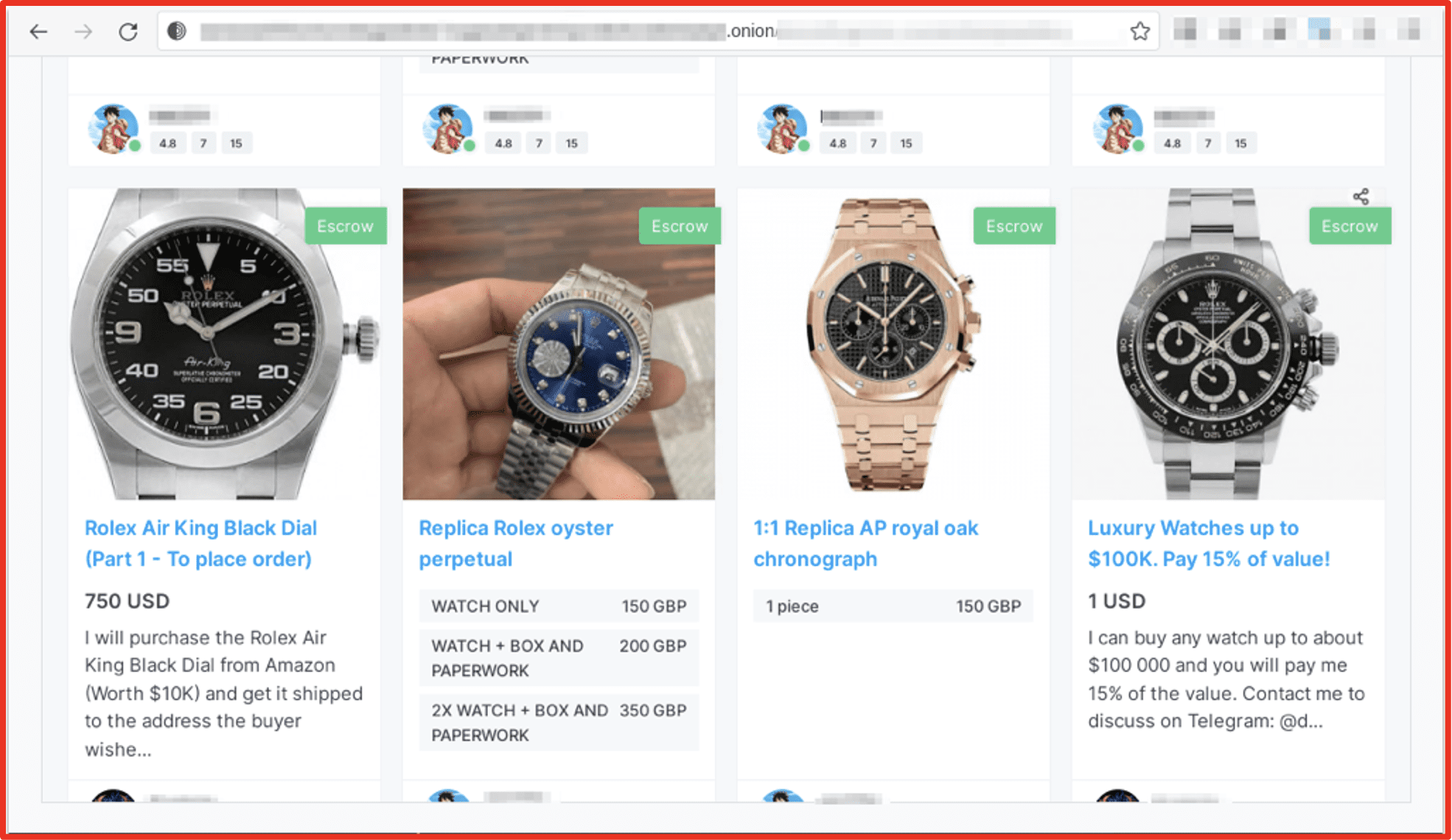
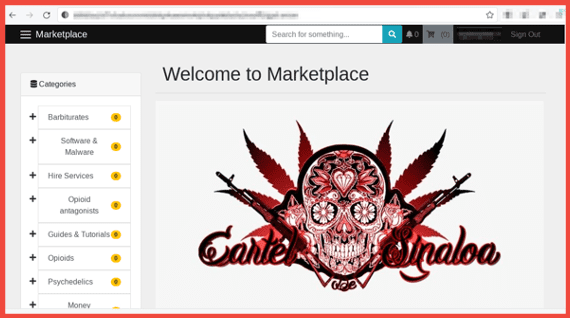
The illicit trade of counterfeit goods is a long proven multi-billion-dollar international industry – which according to counterfeit experts, continues to be led by China. According to Europol, surface web monitoring helps crack down on the major counterfeit goods suppliers, but many sophisticated networks have simply shifted to the darknet and use decentralized darknet markets to sell their counterfeited items.
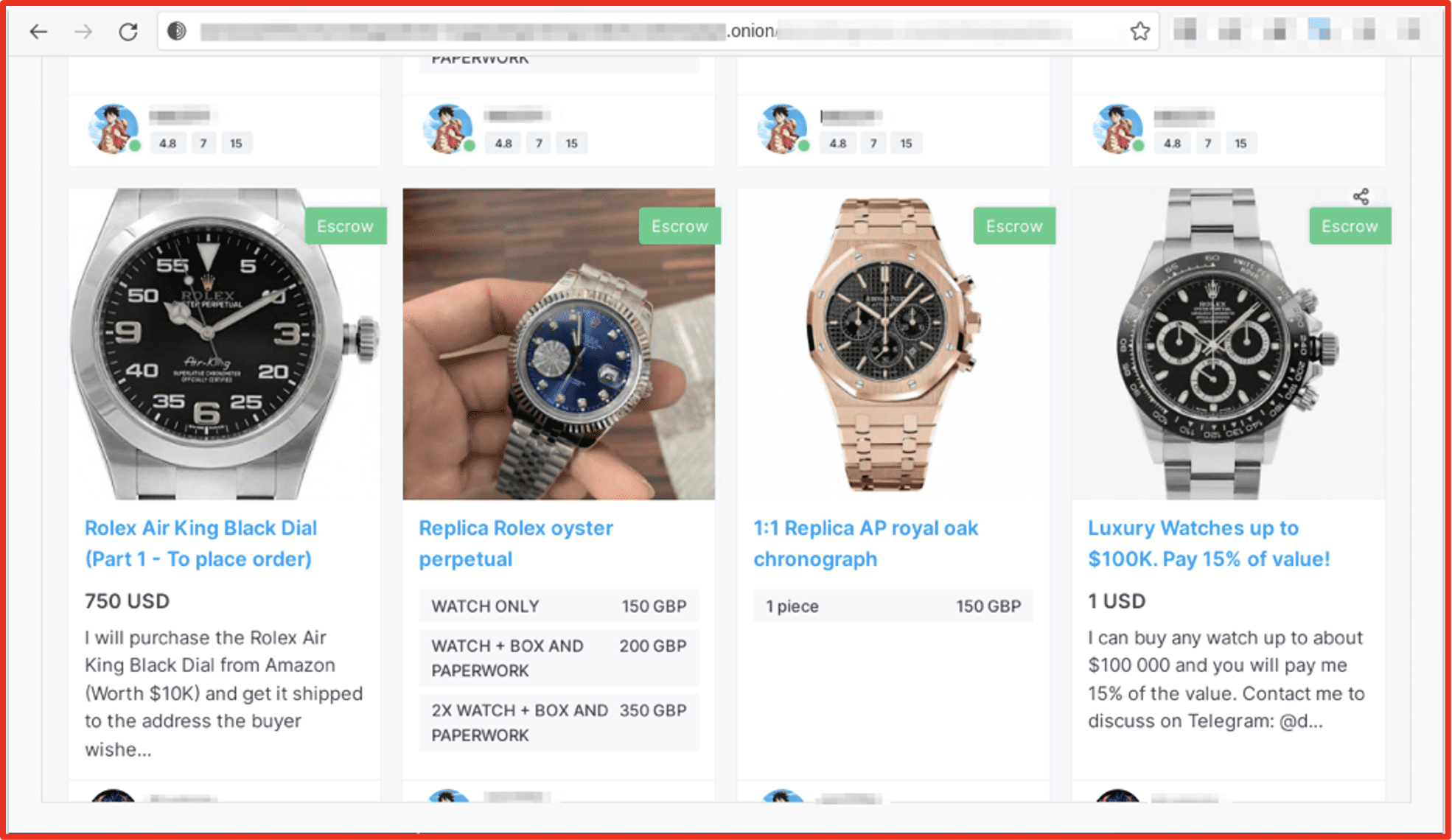
DarkOwl has observed darknet marketplaces that feature a section of “counterfeit goods” comprised of physical counterfeited items a buyer can purchase and have sent to them directly. Watches and fine jewelry are the most common physical goods offered on underground marketplaces, but clothing and electronics are also often on offer.
Figure 3: Listing for counterfeit Rolex watches on Nemesis Source: Tor Anonymous Network
Sweethearting
Sweethearting is a term used to describe a type of social engineering where employees are manipulated by criminals to give away or falsely discount products for purchase and/or potential future resale. Employees are often eligible for store discounts, 20 to 30% off the purchase total, which are applied to purchases initiated by the fraudster.
Employees typically give these undeserved discounts to close friends and family members, but in other cases, employees have been conned into giving them to criminals as well. Such discounts can add-up over time. One such example of costly Sweethearting involved an ex-Amazon employee from Arizona who issued $96,000 worth of refunds to accounts that they owned/were under their control.
Point of Service (POS) Malware
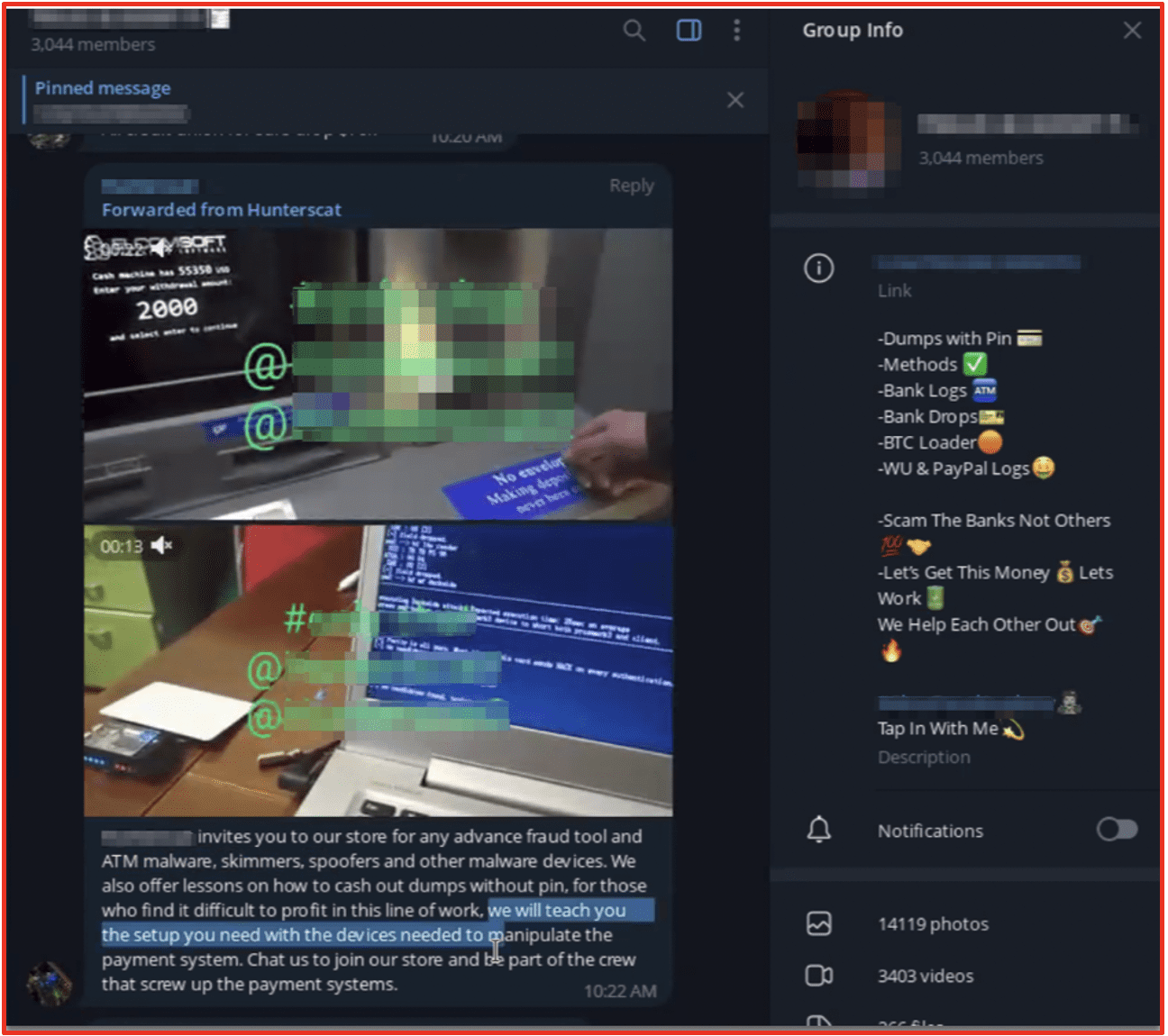
In addition to social engineering-led fraud, there are a subset of threat actors who develop malware and viruses designed to take advantage of Point of Service systems (POS) to conduct advanced retail fraud.
Such malicious code installs remote command and control of the front and back ends of the system, and manipulate prices at scale or as needed for individual fraudulent transactions. Often, such malware is utilized to apply steep discounts and manipulate SKU prices. A threat actor can remotely and temporarily manipulate the price without the retailer’s knowledge, and transactions still appears legitimate until a financial audit discovers the price (and subsequent profit) discrepancies.
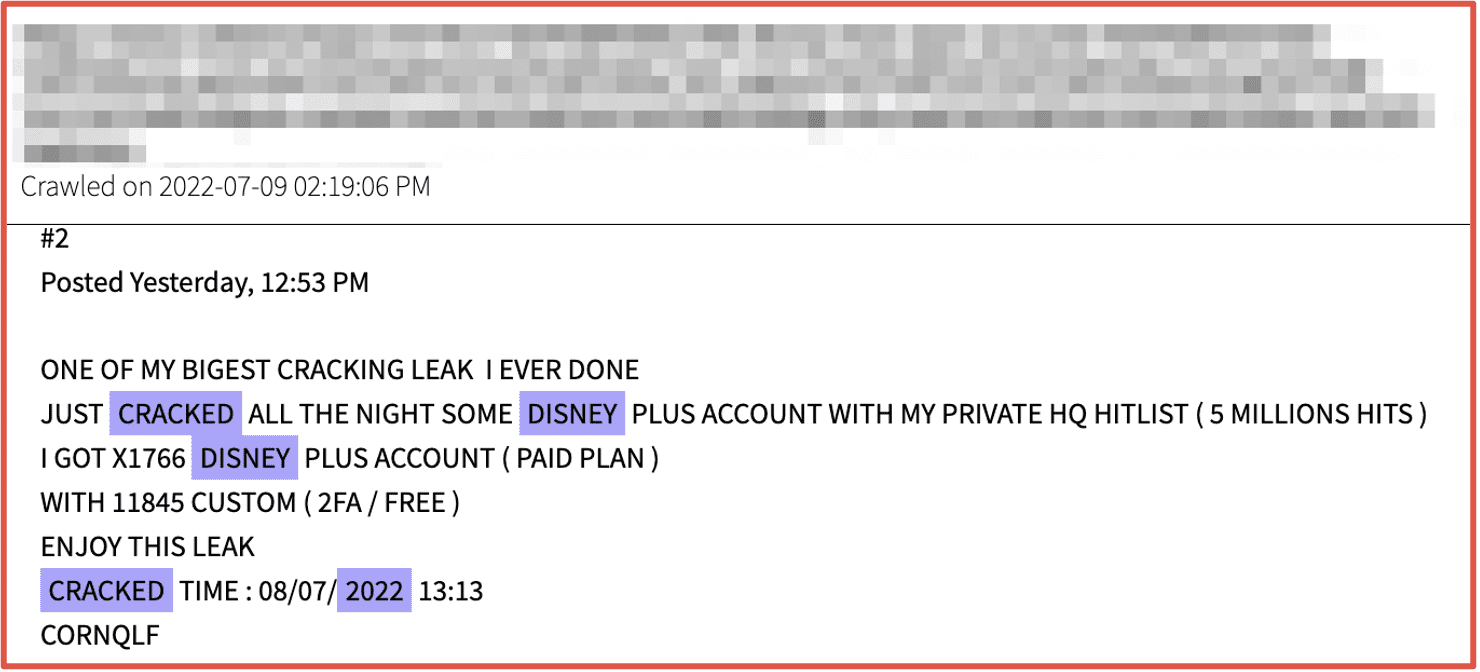
Figure 4: POS malware advertised Source: Telegram, Channel Redacted
Refund-Specific Fraud
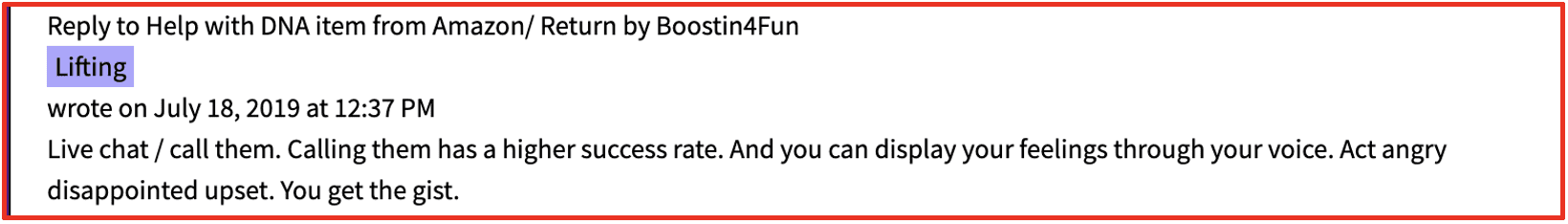
There are multiple forms of e-commerce fraud which usually entail purchasing items online, with intention to keep items, but receive financial compensation for defect or issue with delivery of the item. Popular methods of e-commerce refund fraud discussed on the darknet include using refunds-as-a-service, directly targeting employees, and did not arrive (DNA) fraud.
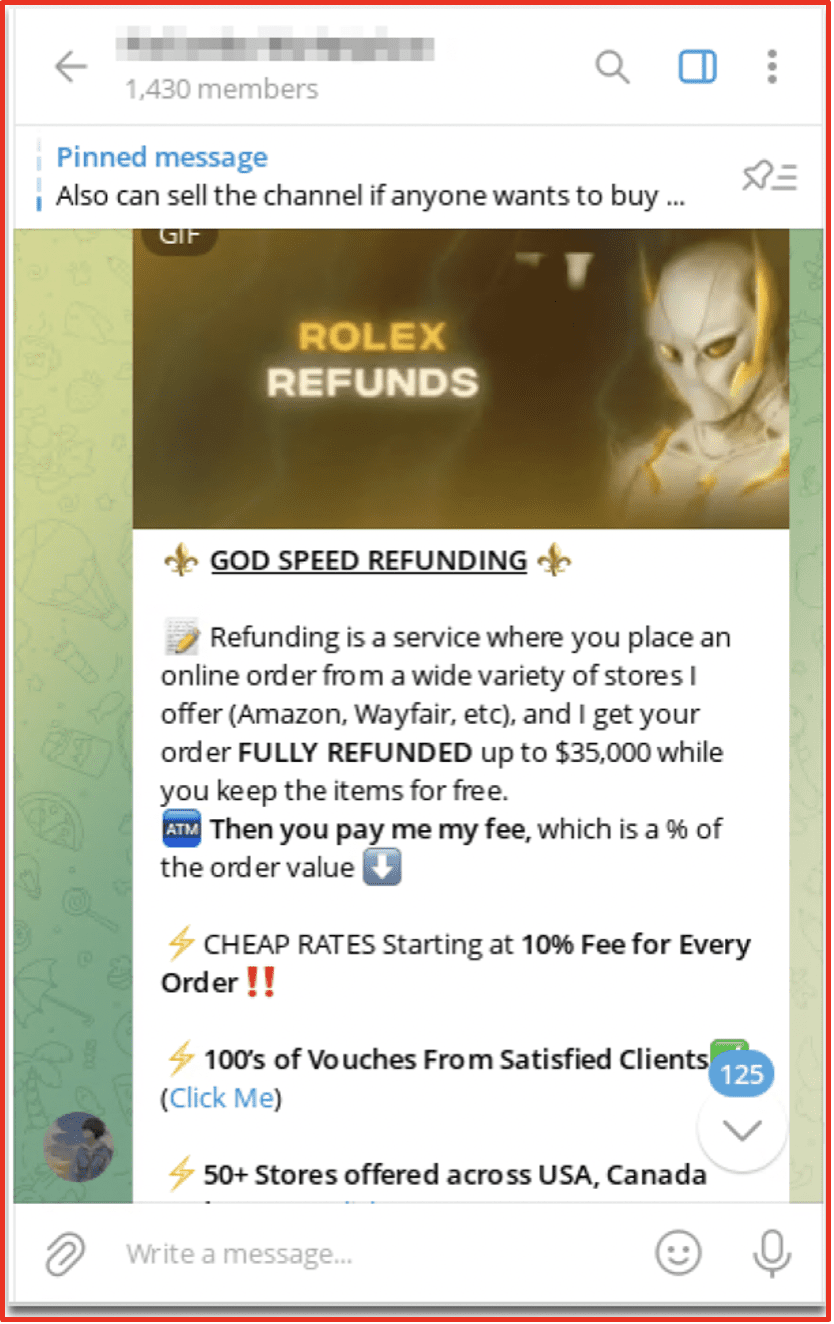
Refunds-as-a-service are a darknet affiliate scheme, primarily discussed on Telegram, where refund fraud is committed at scale on behalf of a customer. Customers outsource and solicit expert advice to receive a full or partial financial refund for items bought online and in stores. Like other “as-a-service” commodities on the darknet, the “refund service” providers facilitate fraud for a percentage of the refund.
In this model, the buyer purchases the product and then simply provides the refund service provider the details of their order and account and card information associated with it. The service provider then impersonates the customer and utilizes a series of advanced social engineering and phishing techniques to carry out the fraud. These include the use of chat bots to tell emotional stories of lost or damaged goods with the goal to illicit enough sympathy from the customer service representative to give a refund regardless of the company refund policies.
Proficient social engineers on the darknet can perform this refund service several times a week to easily make money without ever selling their methods. DarkOwl has observed compensation packages averaging 10% of the order value.
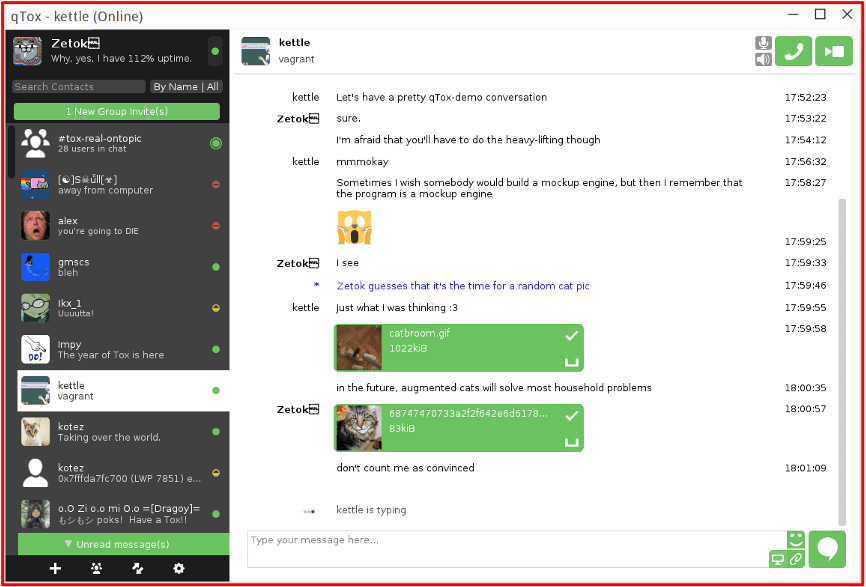
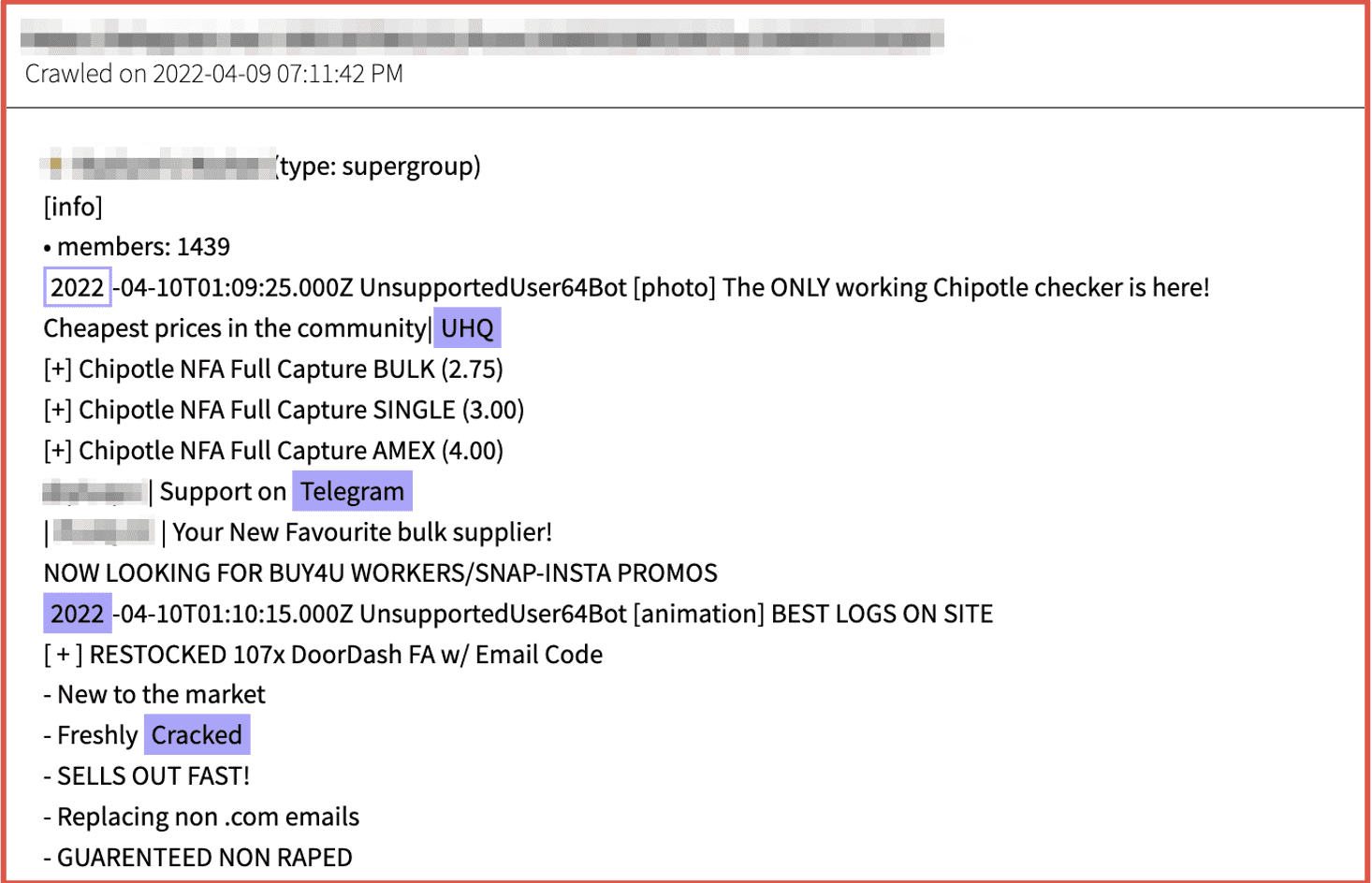
Figure 5: Source Telegram, Channel Redacted
Directly Targeting Employees
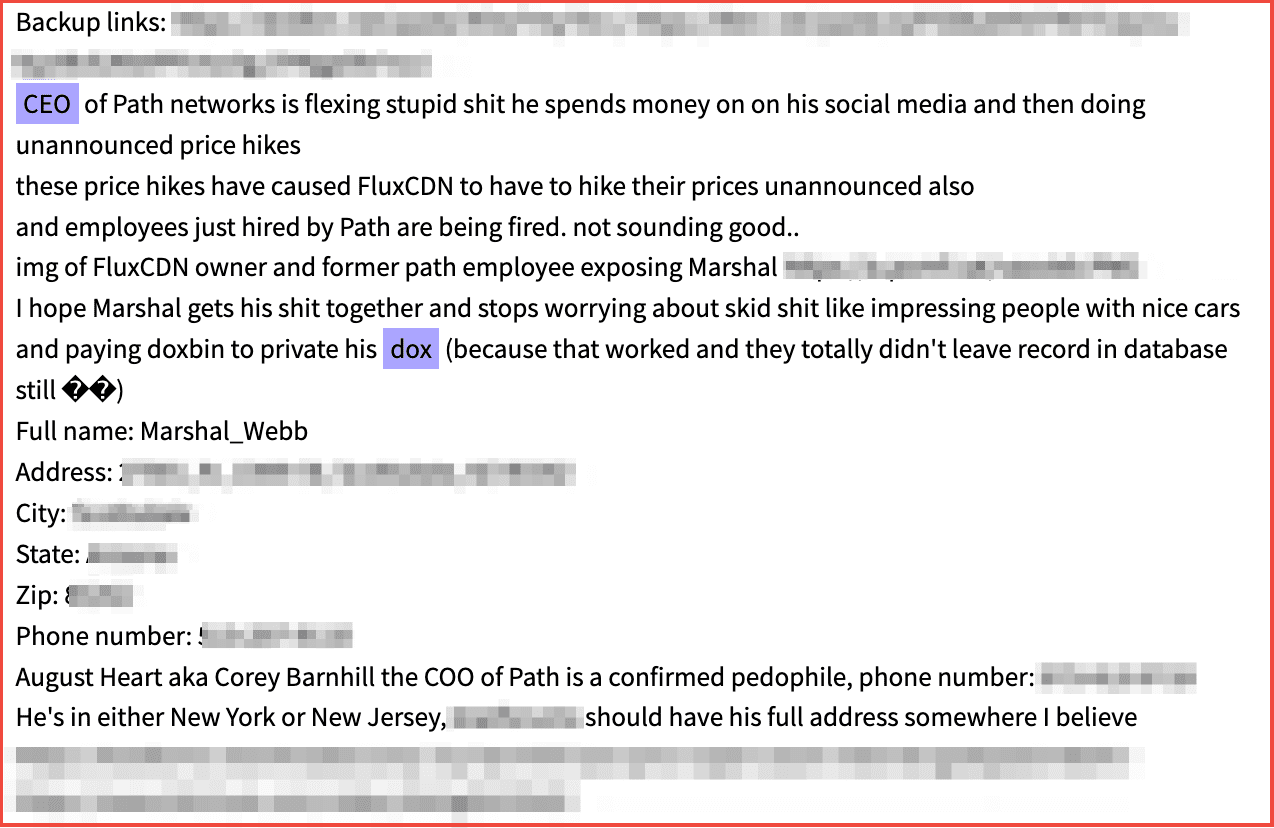
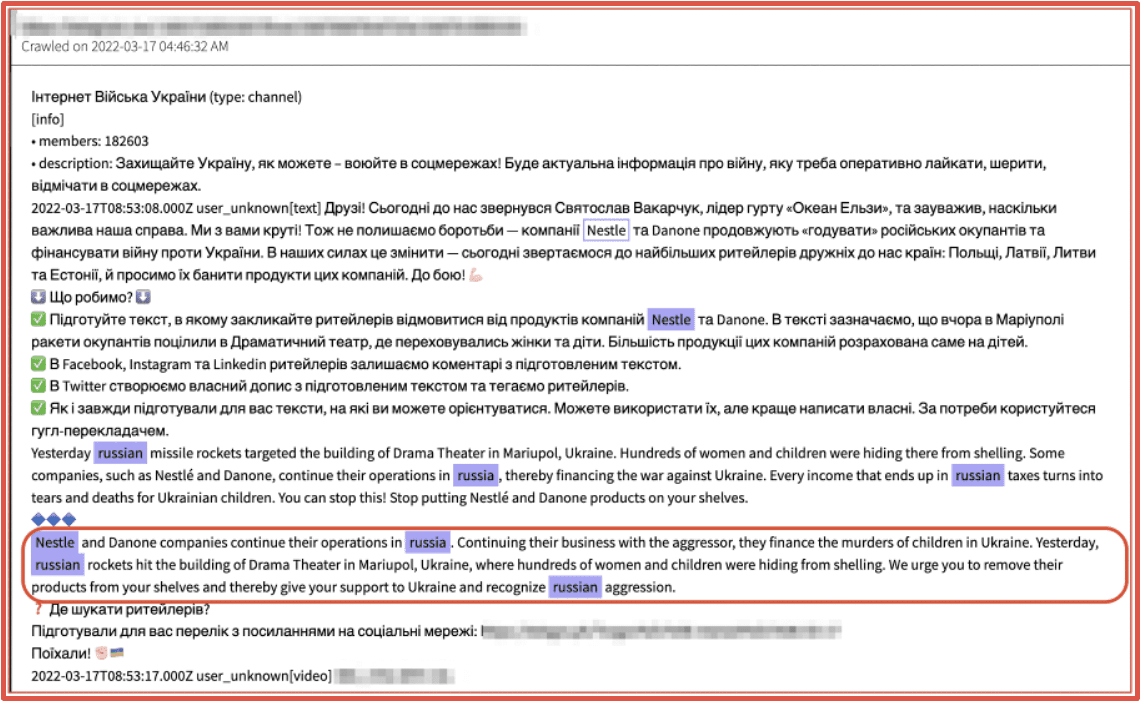
Similar to Sweethearting, another advanced social engineering refund method involves criminals directly targeting employees. DarkOwl has witnessed threat actors who specialize in fraud discuss the methods that they’ve employed to socially engineer retail employees to get discounts or refunds they didn’t qualify for or deserve. This type of fraud is typically accomplished by forming an emotional connection with the employee and using the connection to extort them and steal from the retailer.
Figure 6: Source DarkOwl Vision from Tor Anonymous Browser
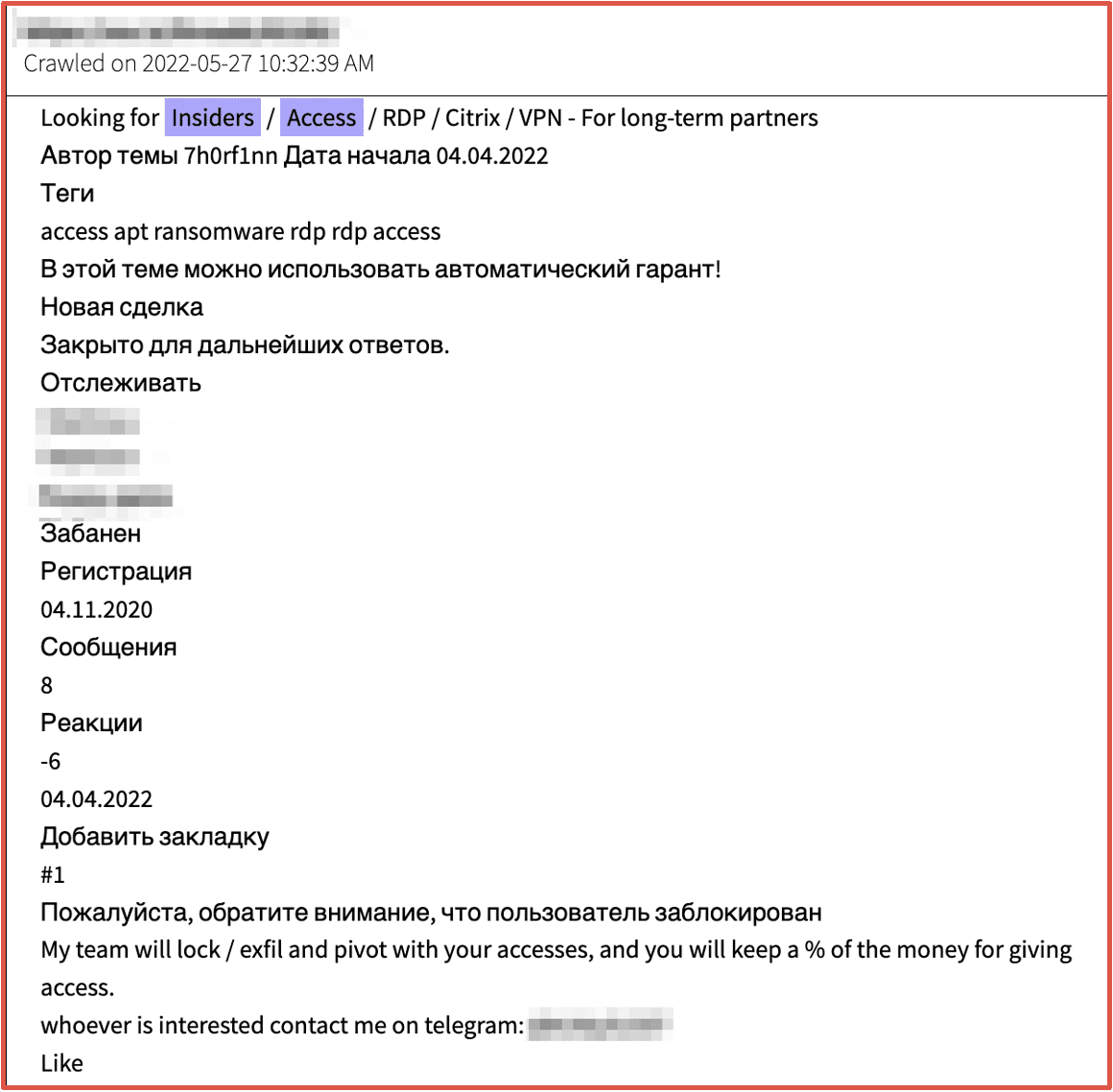
In addition to targeting employees emotionally to get discounts, some refund groups may try and recruit employees to come work for them. This provides the criminal group direct insider access to POS systems, gift cards and voucher codes, and credit card transactions.
Figure 7: Source DarkOwl Vision
Did Not Arrive Fraud
Did not arrive (DNA) fraud is one of the oldest methods of e-commerce-specific refund fraud. In this scam, customers claim that their package never came or was stolen, and will ask for a full refund even though the items did arrive. The international popularity of large e-commerce retailers like Amazon has propelled this type of fraud.
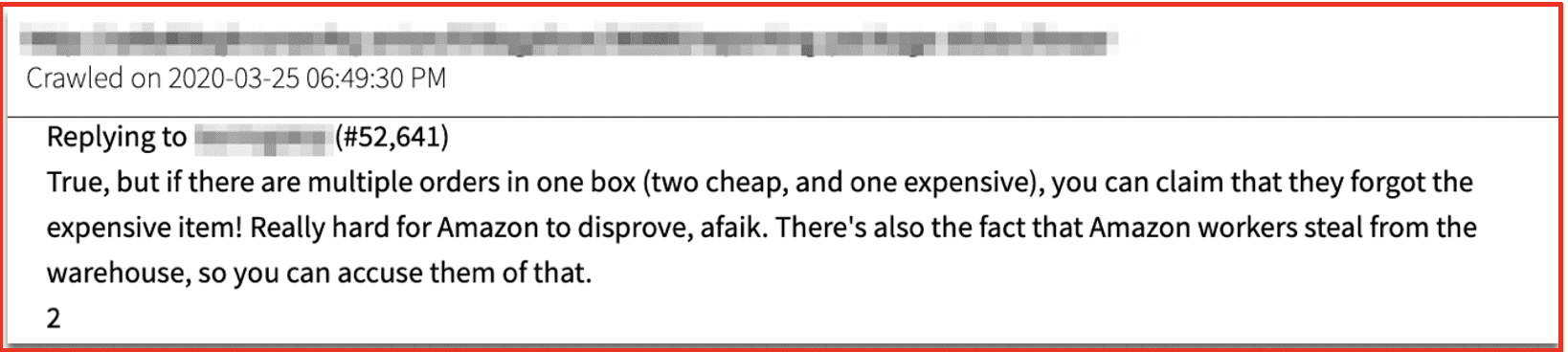
Empty Box Fraud
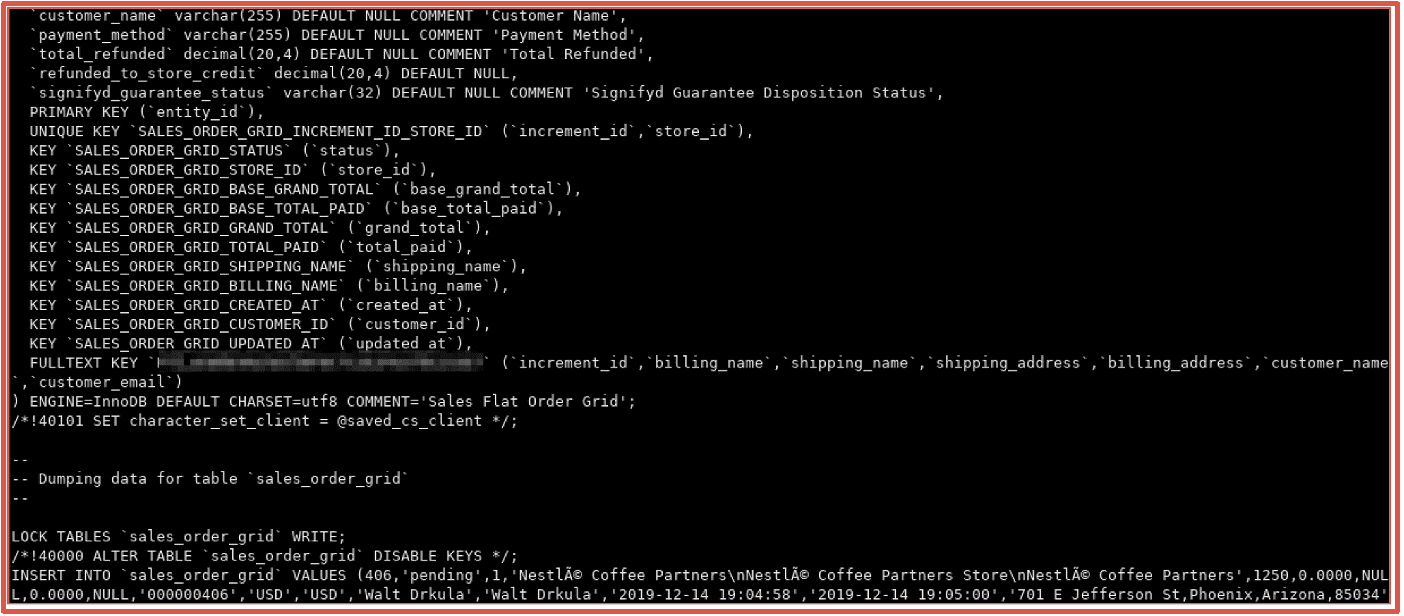
A similar kind of fraud is empty box or partial-empty box refund fraud. In this case the purchaser lies and claims that an item was packed incorrectly, damaged, or that it was stolen during the shipping process and asks for a full refund. Similarly, a fraudster will order a small high value item with a large low value item and initiates refund claiming that the high value item was not in the package delivered.
Figure 8: Source DarkOwl Vision
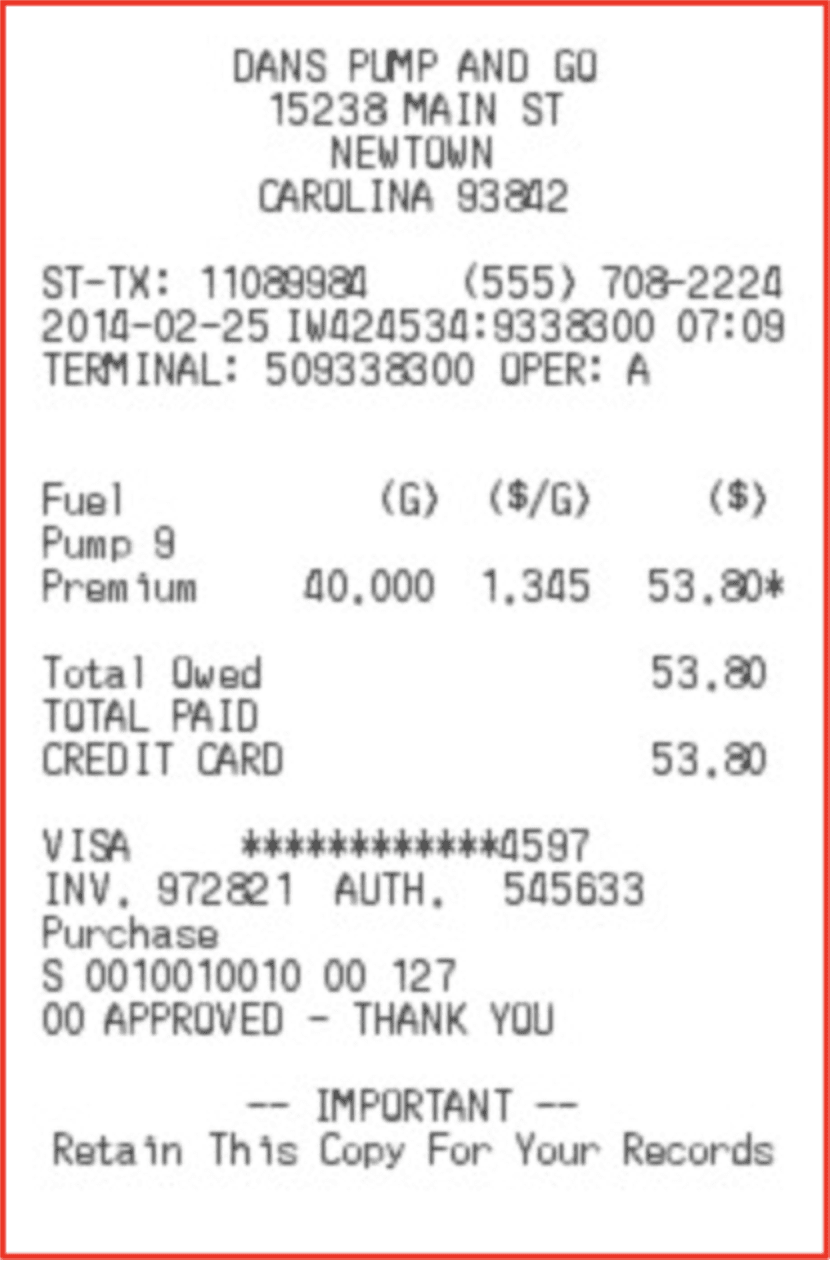
Receipt Fraud
Adjacent to retail refund fraud is receipt fraud, which entails generating fake receipts for goods never purchased at the retailer, often for the sole purposes of refund initiation or submitting falsified expense reports.
Threat actors specializing in receipt generation subscription models offer fraudsters access to numerous retailers’ receipt templates for as little as $9.99 USD per month. Both online and in-store purchase receipts are available for purchase. Electronics retailers like Best Buy, NewEgg, and CDW are regularly mentioned in addition to shipping services like FedEx and UPS.
Figure 9: Fake Fuel Purchase Receipt, Source DarkOwl Analysts
FTID (Fake Tracking ID) Scams
DarkOwl has witnessed increased mentions of tracking-related fraud, where scammers purchase expensive and valuable items, such as electronics with the intent to initiate a return and refund. They request a refund, which prompts the retailer to send them a shipping value to affix to the returned items’ package. Instead of placing the shipping label on a parcel, they put the shipping label on an empty envelope or piece of junk mail, which upon delivery to the mailbox of the business will be mistaken for trash and thrown away. The scammer has the tracking information to prove the label was returned to the retailer’s business address, receives the refund, and keeps the high-valued item.
In the example pictured below, a fraudster on a Telegram channel boasts how Amazon workers regularly steal from returned item mail sorting facilities which can be used as a potential theory why the item was not correctly returned.
Figure 10: Source Telegram Channel, Redacted
Wardrobe Fraud
Wardrobe fraud or “wardrobing” is popular with female fraudsters who purchase high valued clothes with the intent for single use and fraudulent return. Often a customer orders an item of clothing, typically expensive clothes for a black-tie or formal event, wears it one time, by concealing the tags inside the dress, or re-attaches them, and then sends the clothes back to the retailer after use. It is often likely that these worn clothes will be damaged and/or dirty. This type of fraud is conducted both in-store purchases and online.
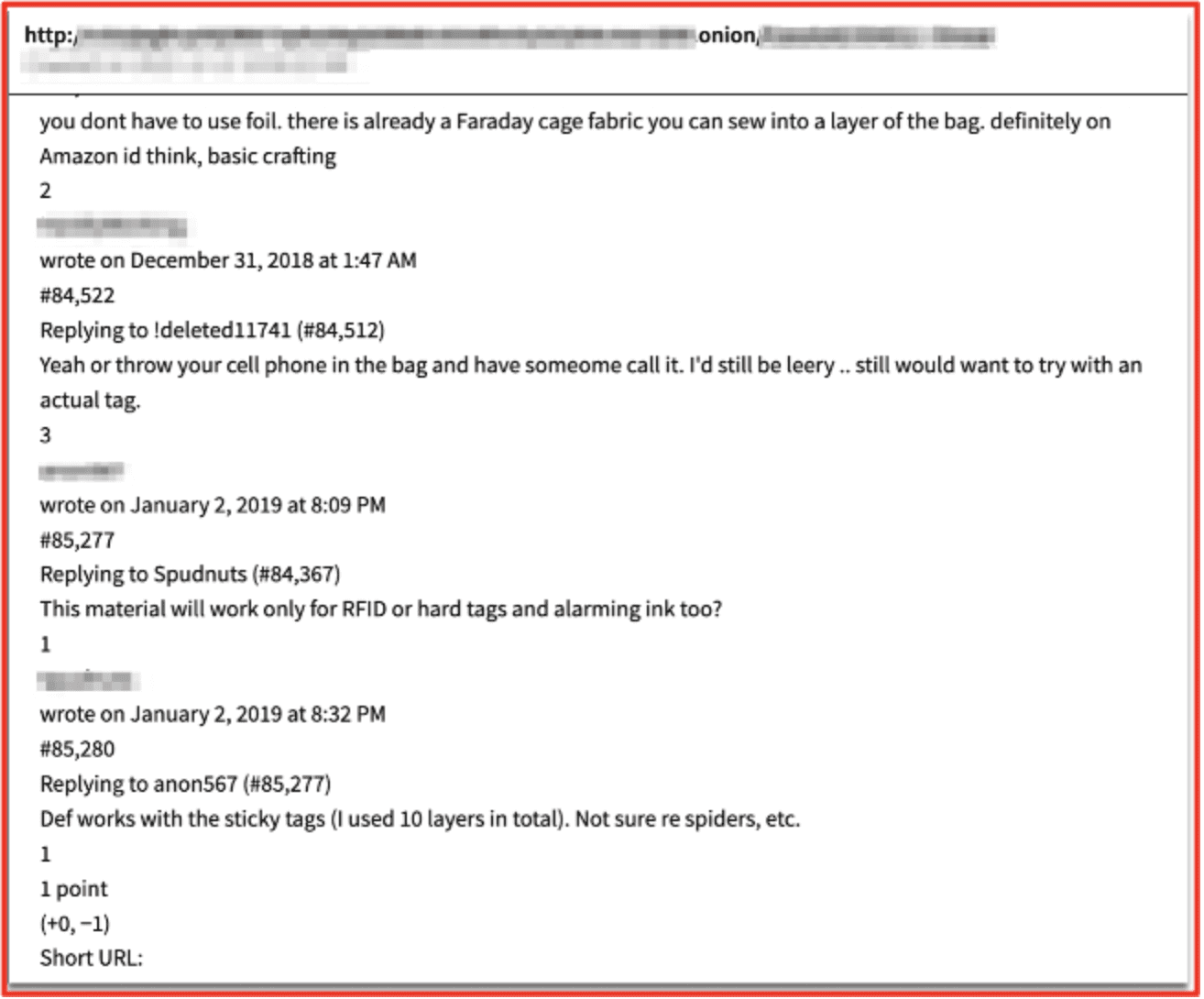
Darknet Threat Actors Discuss Bypassing Physical Security Measures for Theft
One of the oldest forms of retailer fraud and commerce crime is physical theft of goods from a store. During this research, DarkOwl analysts also uncovered conversations where threat actors revealed methods to bypass loss prevention physical security measures utilized in-stores, such as electronic article surveillance (EAS) ink-tags and RFID (radio-frequency identification) disruption.
Figure 11: Source DarkOwl Vision
Retailers at the Epicenter of Consumer Phishing Attacks and Identity Theft
Fake/Spoofed Websites and Sellers
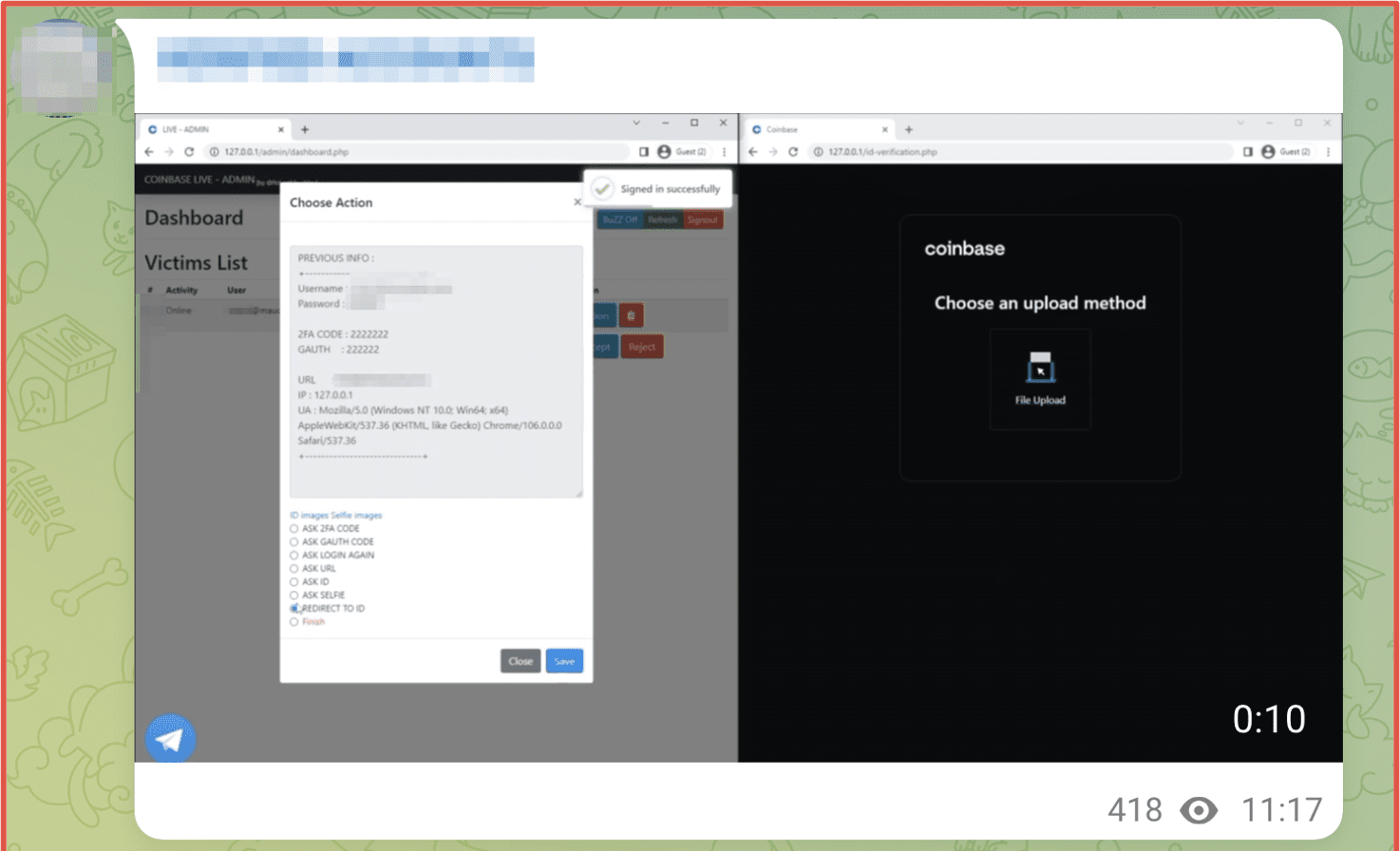
Oftentimes, a retailer’s brand and reputation will be exploited by threat actors so that they can carry out elaborate scams with advanced phishing and social engineering attacks – mainly with the intention to commit identity theft. Criminals lure victims to malicious sites – with links often delivered via phishing emails claiming to be a reputable, popular store – and typically advertise a promotion or deal to entice the consumer to click. Phishing emails have become increasingly more sophisticated as their delivery mechanisms are designed to evade spam filters using techniques such as URI fragmentation and domain hop architecture.
From our Darknet Glossary, “spoofing” is a method used by cybercriminals in which they falsify the origins of network communication to mislead or misdirect the recipient into thinking they are interacting with a known and trusted source. These websites look legitimate and very similar to the real retailer’s site. Some can also have malware that a customer can unknowingly download.
Spoofing and tricking unsuspecting customers into buying from fraudulent sites is often accomplished by typo-squatting, whereby fraudsters impersonate legitimate sites and services and trick people into using them by changing the spelling of the site ever so slightly so that most don’t notice the difference.
Fraudulent websites can damage the reputation of a commercial retailer and take away sales from customers who would have bought products from the legitimate business. Spoofed websites resulting in unhappy customers hurts trust in the brand, potentially impacting future sales and revenue.
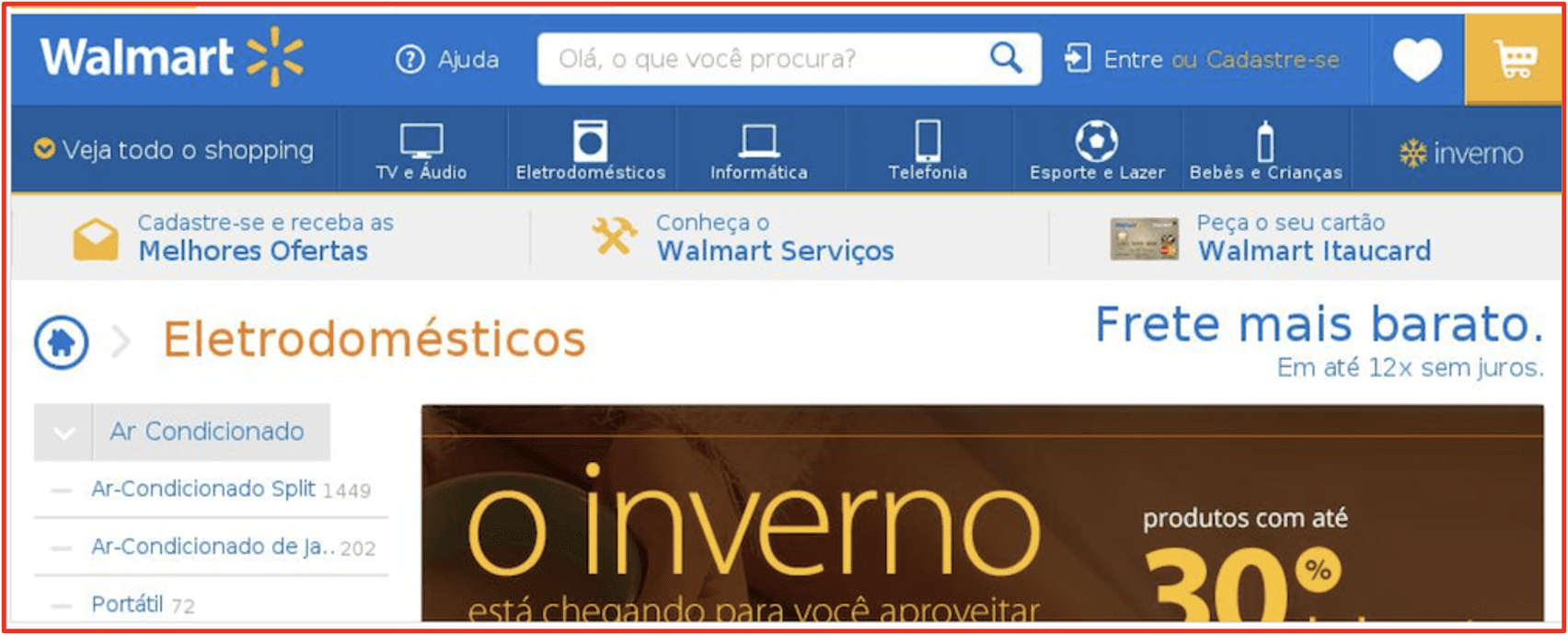
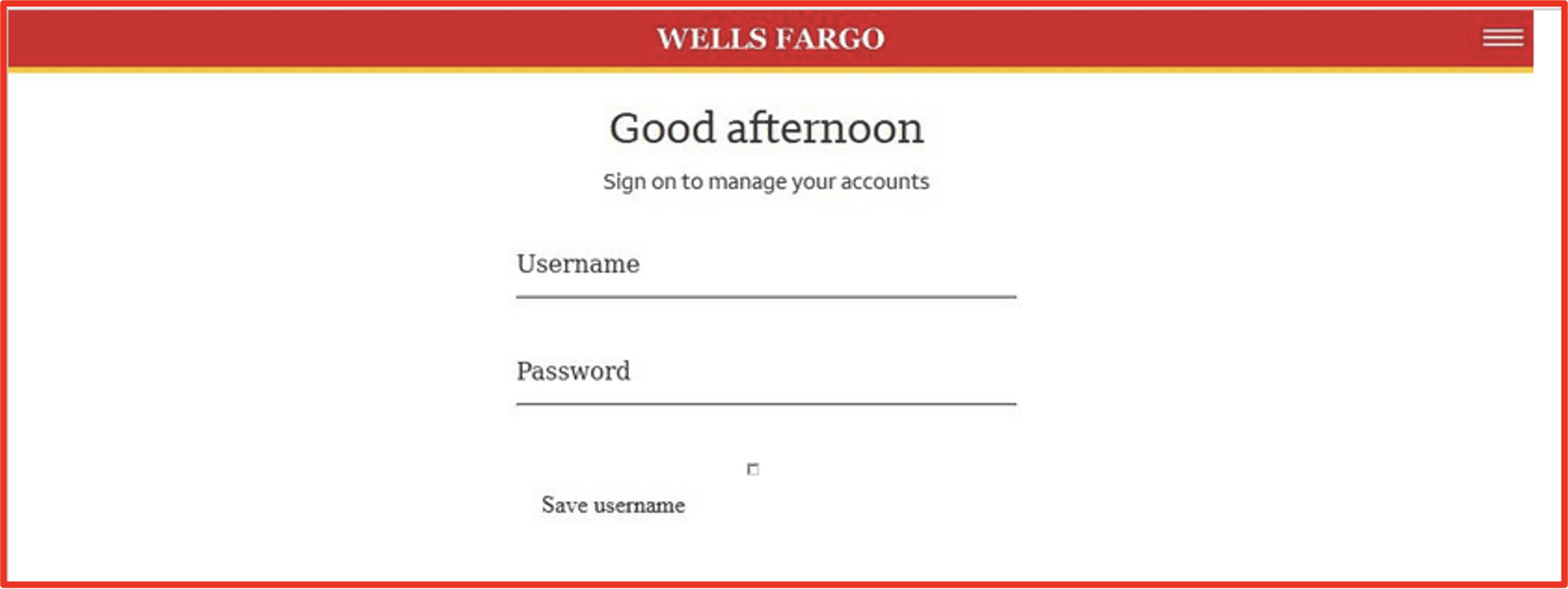
The figures below demonstrate sites that have been verified as phishing domains, e.g. Brazilian Wal-Mart and Well Fargo client login page which harvest banking authentication credentials.
Figure 12: Wal-Mart phishing site deployed in Brazil, Source: phishtank.org
Figure 13: A verified phish website for Wells Fargo Bank Source: phishtank.org
Offers to build fake websites and all the tools to facilitate complex phishing campaigns are readily available for sale on the darknet.
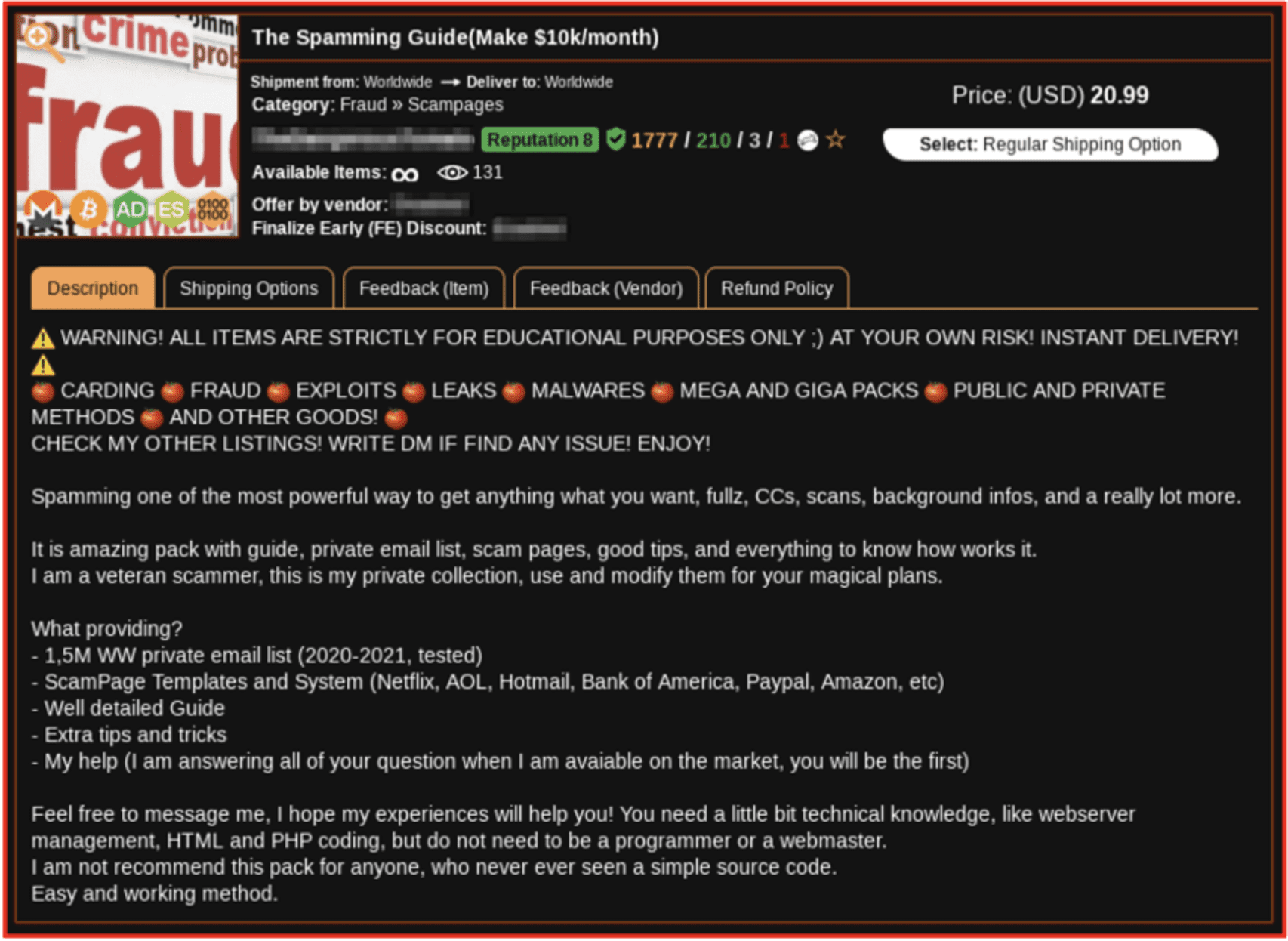
DarkOwl analysts observed “custom made websites” available for sale on a darknet marketplace ranging from $50 – $300 USD. Likewise, guides on “how to phish” and create fake e-commerce websites are on offer on darknet marketplaces for as little as $5 – $10 USD with advertised financial profit of $10K USD per month.
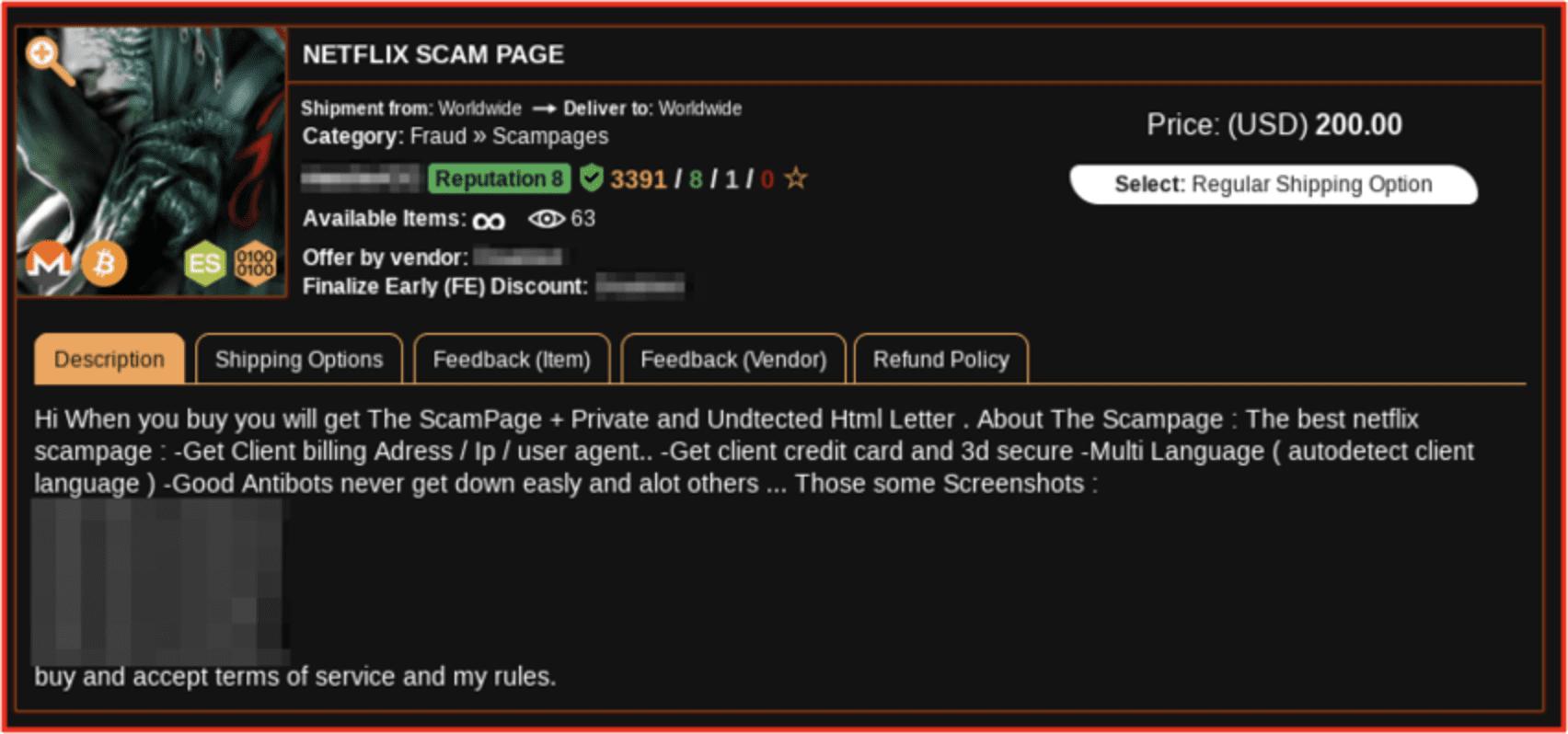
The most popular exploited retailers are Uber, Amazon, and Netflix and phishing kits often sold in conjunction with “lead lists” containing thousands of private email addresses and phone numbers that can be utilized for sending spam in large volumes.
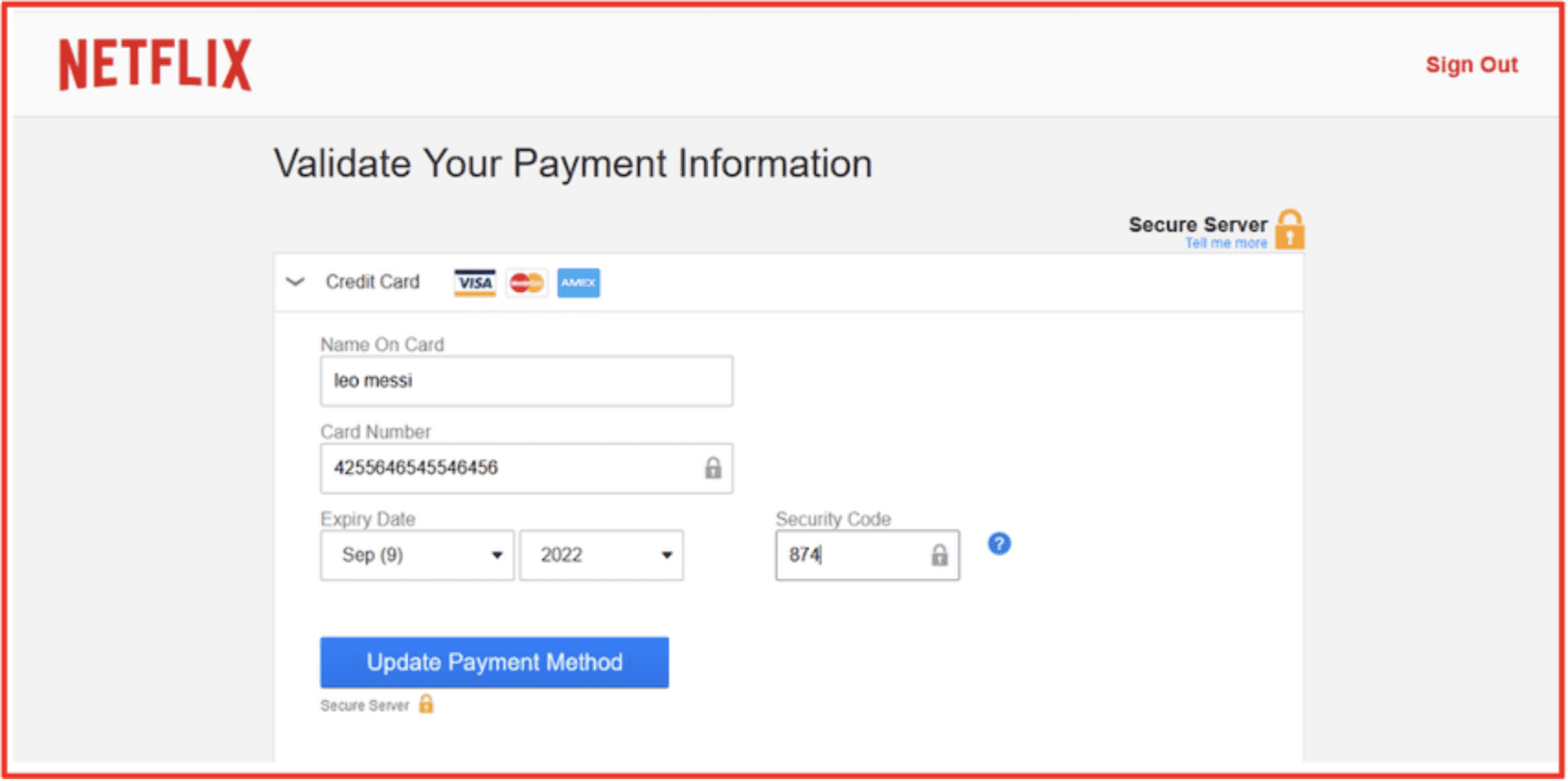
Figure 14: Netflix “scampage” website for sale Source: Kerberos Market,Tor Anonymous Browser
Figure 15: Netflix Payment Validation Phishing Site Sample Provided as Proof by Threat Actor
Figure 16: Advertisement for Phishing Kit Guide, Source Kerberos Market, Tor Anonymous Network
Falsifying the Authentication of Scam Pages through Website Certificates
DarkOwl analysts have also noticed website certificates such as SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates for sale in darknet fraud communities. Giving a spoofed website an authentic SSL/TLS certificates helps threat actors with their detection-evasion measures and makes the phishing/scam website to look more authentic.
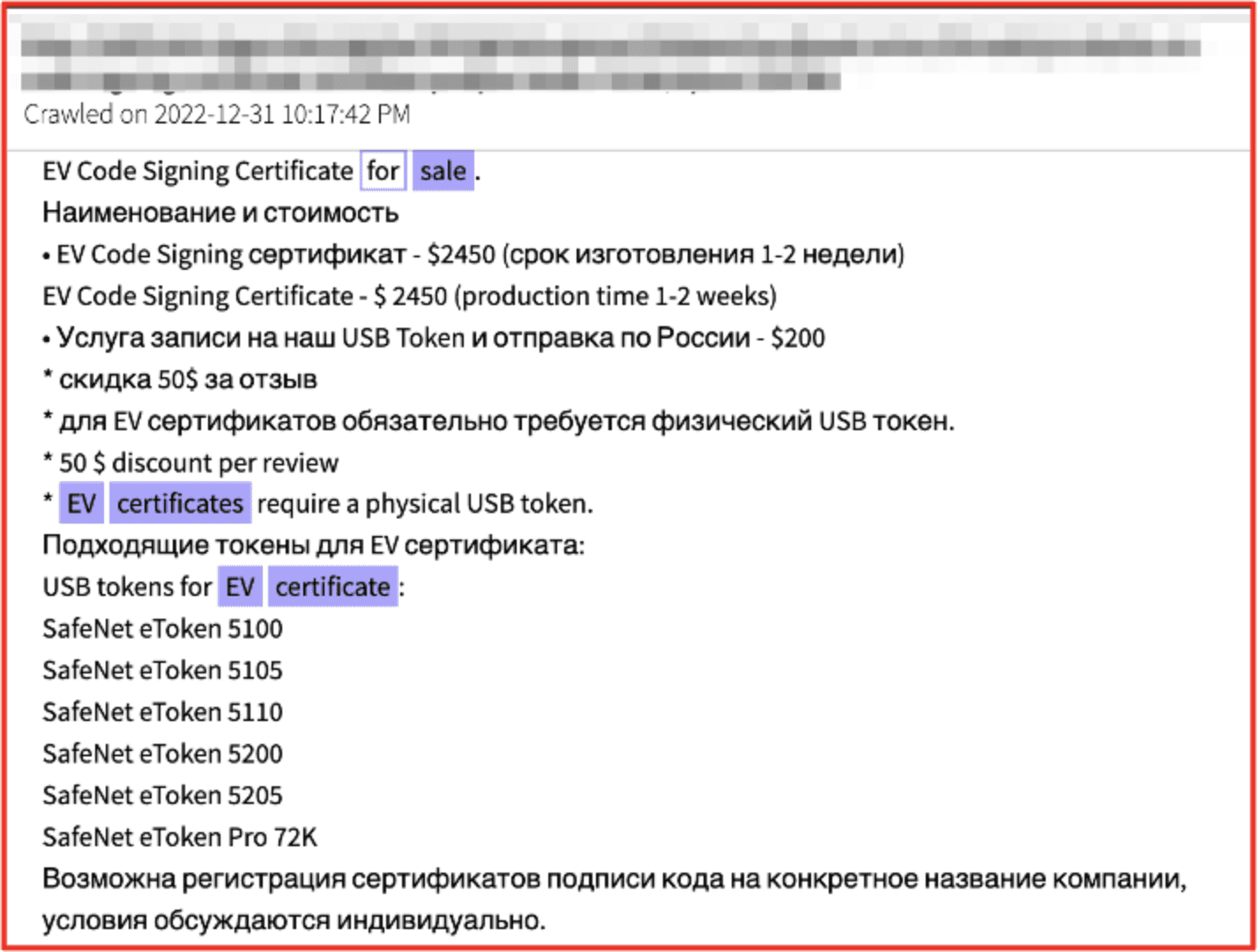
Certificates provide machines a unique identity and communicate trust to visitors of the website and search engines alike. This way hackers and threat actors avoid getting flagged as not trustworthy. DarkOwl also found Russian-based threat actors offering Extended Validation (EV) certificates, widely regarded as the most trustworthy kind of machine identity, for sale on the darknet for upwards of $2400 USD.
Figure 17: EV Certificates for sale on the darknet, Source DarkOwl Vision
[FIGURE TRANSLATED]
EV Code Signing Certificate for sale.
Name and cost
• EV Code Signing certificate – $2450 (production time 1-2 weeks)
EV Code Signing Certificate – $ 2450 (production time 1-2 weeks)
• Recording service to our USB Token and shipping across Russia – $200
* $50 discount per review
* A physical USB token is required for EV certificates.
* * 50 $ discount per review
* EV certificates require a physical USB token.
Suitable tokens for an EV certificate:
USB tokens for EV certificate:
SafeNet eToken 5100
SafeNet eToken 5105
SafeNet eToken 5110
SafeNet eToken 5200
SafeNet eToken 5205
SafeNet eToken Pro 72K
It is possible to register code signing certificates for a specific company name, the conditions are discussed individually.
Fake Delivery and Shipping Notifications – via Email and SMS Phishing Campaigns
Fraudsters and scammers will use lead lists to send large volumes of fake delivery and/or shipping notifications – appearing to come from trusted retail and delivery sources – indicating that there has been an issue with the delivery, it has been delayed, or a fee need to be paid for the package to be delivered.
Usually, the notification includes a link to a fraudulent site prompting users to enter their financial information and PII (which can be leveraged by actors later) or to pay a fee to release the shipment. Such phishing campaigns using retail commerce providers occurs via both email and SMS delivery.
Gift Card, Rewards Programs, and Retail Promotion Fraud
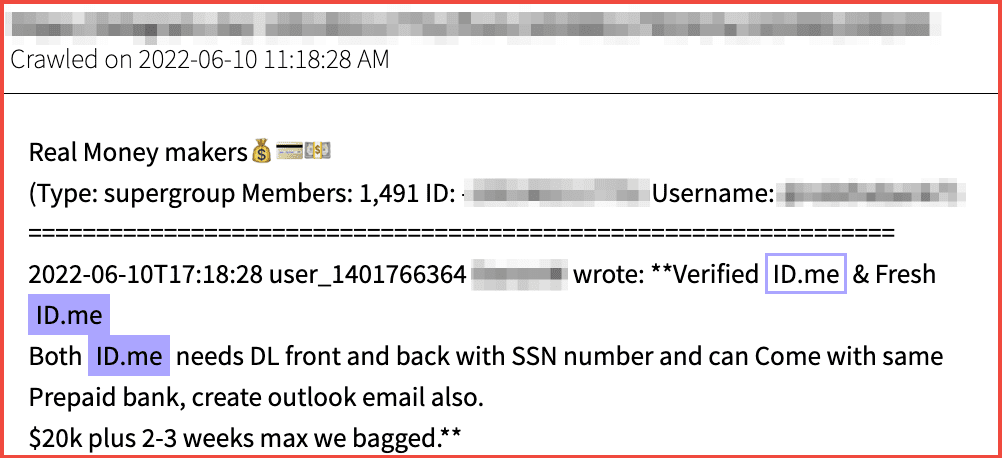
Gift card fraud is a lesser-known form of retail fraud, yet popular amongst darknet threat actors. Gift card fraud can occur via insider threats, i.e. employees steal legitimate gift cards, as well as externally, i.e. consumers redeem stolen or counterfeit gift cards.
Fraudsters easily utilize gift cards and vouchers for illicit purchases because these forms of payment have less security protection than traditional credit cards.
Figure 18: Source Telegram, Channel Redacted
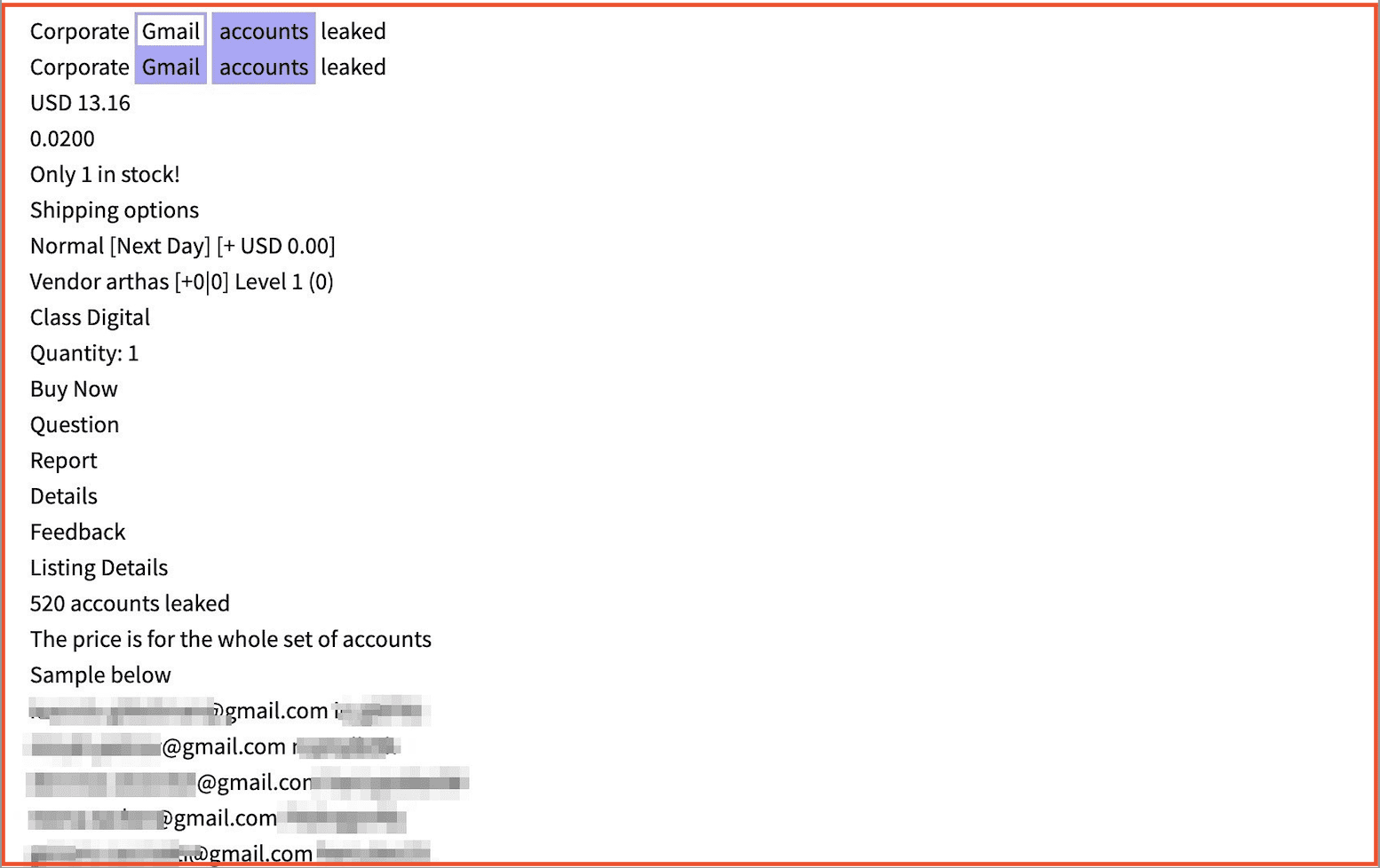
Loyalty programs and customer rewards are also stolen and/or counterfeited for resale. DarkOwl analysts have observed numerous prominent retailers mentioned in darknet fraud advertisements, such as Macy’s, Nordstrom, Kohl’s Cash, AMC Theatres, Office Depot, Bath and Body, Top Golf, DSW, Target, Costco, American Eagle, Southwest Airlines, Marcus Theatres, and numerous restaurant and coffee chains. Most gift card and reward program fraud on offer in the darknet are US-based retailers.
Figure 19: Fraud Vendor Shop, Source: Deep Web
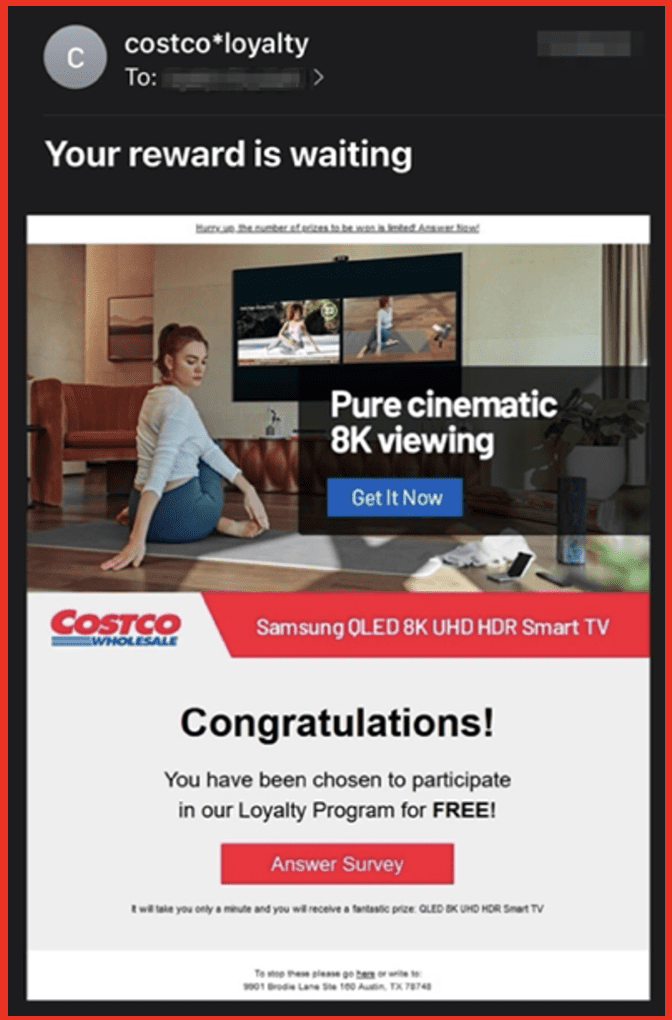
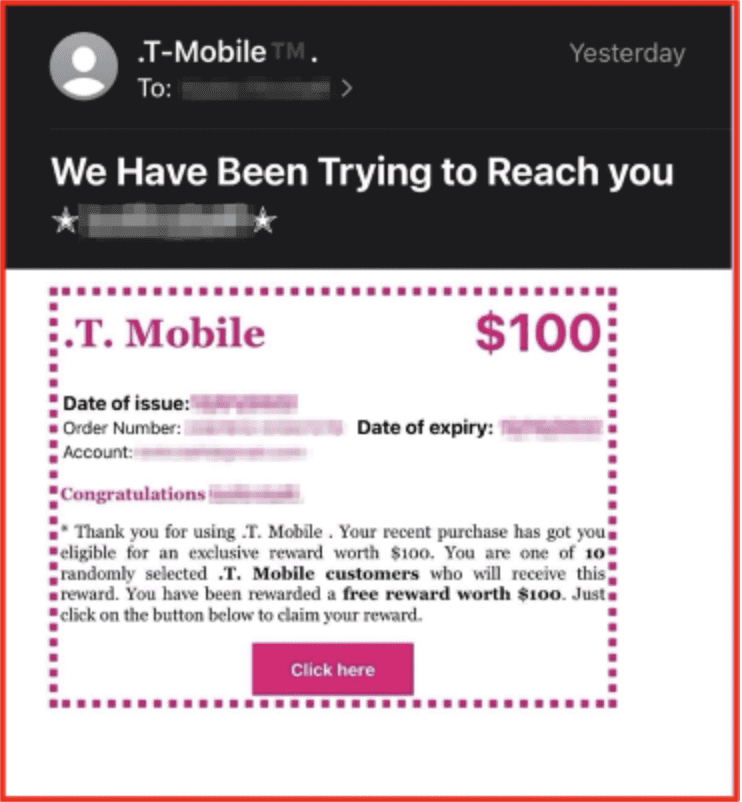
Phishing emails disguised as reward program promotions also lure customers to join fake loyalty programs and enter their personal information, which is systematically harvested, stored, organized by retailer into “logs,” and resold in mass in various darknet data brokerage communities across Tor and Telegram.
Figures 20 & 21: Examples of Phishing reward program promotions, Source DarkOwl Analysts
Final Thoughts
Cyber criminals and those involved in retail fraud have become more convincing, sophisticated, and organized with every holiday season. Retail fraud obviously harms commercial retailers fiscally, but also impacts the retailer’s reputation, trust in the brand, and customer loyalty overtime.
The darknet and darknet-adjacent chat applications play an important role in the evolution and proliferation of such virtual and physical theft techniques and tactics. The darknet provides and interconnected web of fraud methods that can be learned, shared, and constantly updated to outsmart legitimate retailers and trick their consumers.
Retailers can benefit from a regular darknet monitoring service for indications of the most up-to-date methods and malware used for retail fraud, to employ effective detection and countermeasures, and setup recognition education programs for their employees and stakeholders.
Interested in learning how darknet data plays a vital role in preventing, catching and remediating retail fraud? Contact us.